Reports
Security posture reports allow you to export industrial network data from the traffic captured and processed by Cisco Cyber Vision.
That way, you can show off striking information like sensitive entrance points, acknowledged vulnerabilities for status reports, etc.
You must install the reports extension to be able to use this page. You can do so by importing the reports extension file through the Admin Extension page in Cisco Cyber Vision. The extension file is available on cisco.com.

Security posture reports allow you to create reports from a preset, that is a a set of data, present by default in Cisco Cyber Vision, or a custom one.
Reports are exportable in docx and pdf formats.
You can costumize the report by adding a logo, such as the company's one. By default, the report will be generated with Cisco's logo.
The table of content menu allows you to set which content will appear in the report.
Create a report
Procedure
|
Step 1 |
Click Create and run a report.  |
|
Step 2 |
Give the report a name and optionally add a description. 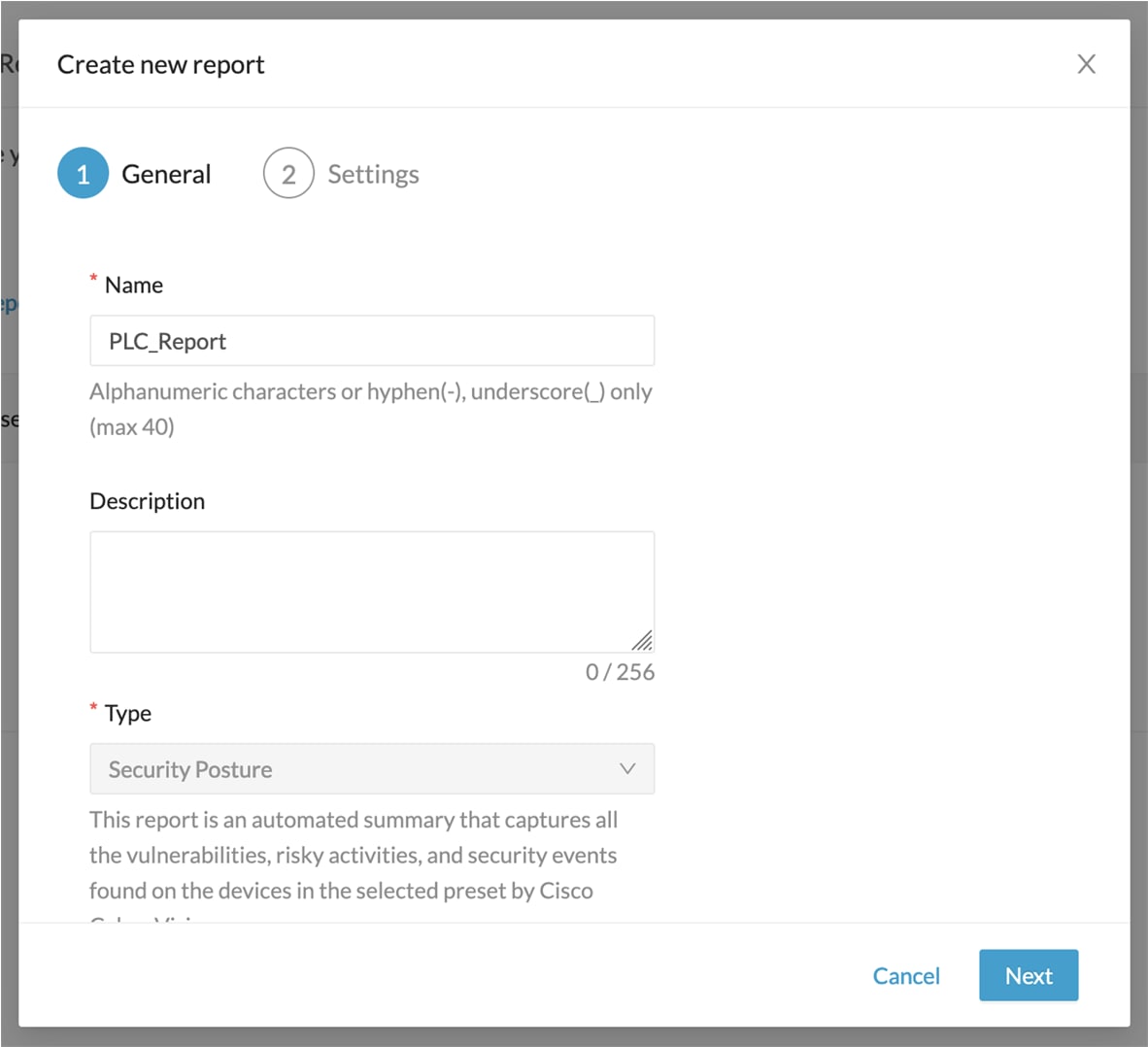 |
|
Step 3 |
Optionally, add a logo. It will appear on the report. |
|
Step 4 |
Select the format(s) you want the report to be generated to.  |
|
Step 5 |
Click Next. |
|
Step 6 |
Select a preset from the dropdown menu. |
|
Step 7 |
Under table of content, select the content you want to appear in the report.  |
|
Step 8 |
Click Save and run. The new report appears in the list with the status Processing. It should eventually turn to Success after a few moment once the report is generated.  |
|
Step 9 |
To download the report, click the name of the report in the list to open its right side panel or the format button(s). 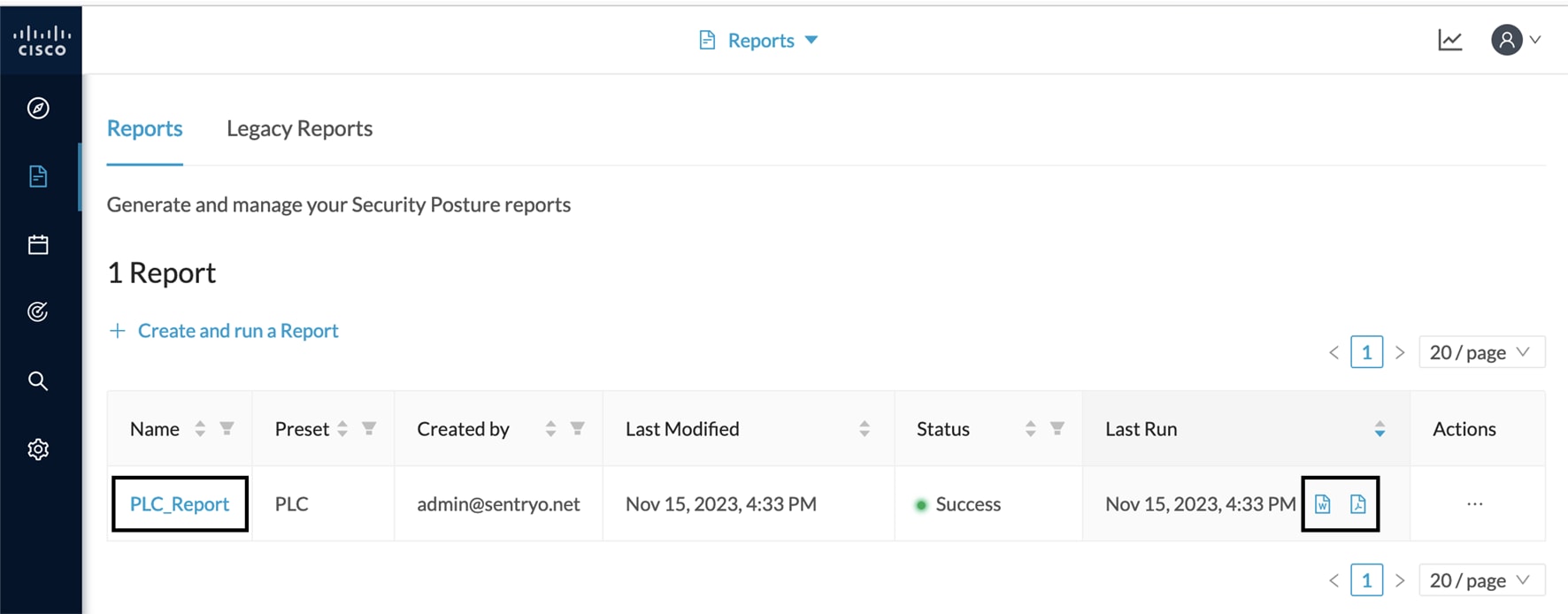 |
|
Step 10 |
On the right side panel, click the links to download the latest reports. You will find older ones under the Previous Reports menu. 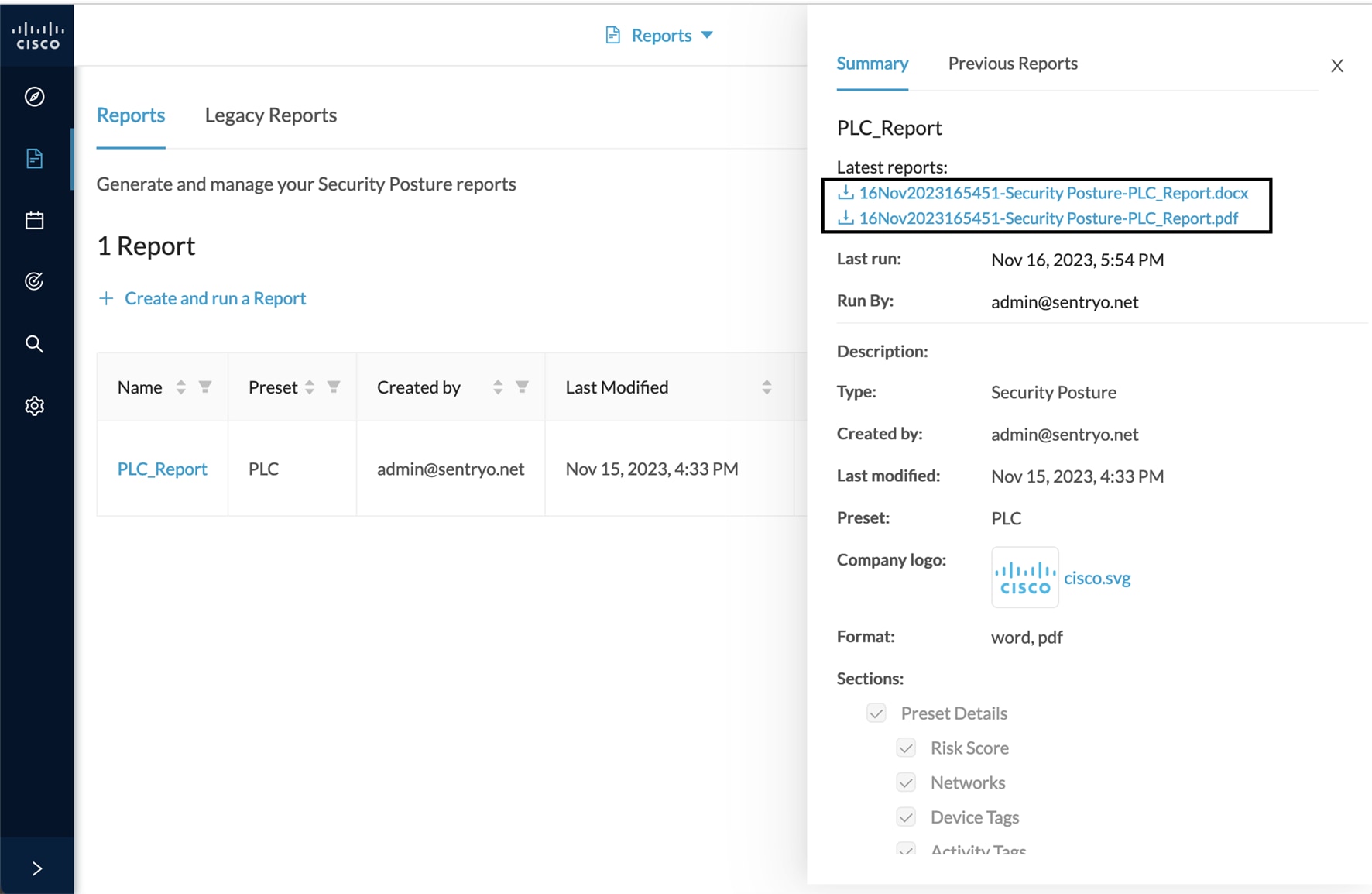 |
|
Step 11 |
To generate a new report click Run Again under Actions.  |


 Feedback
Feedback