|
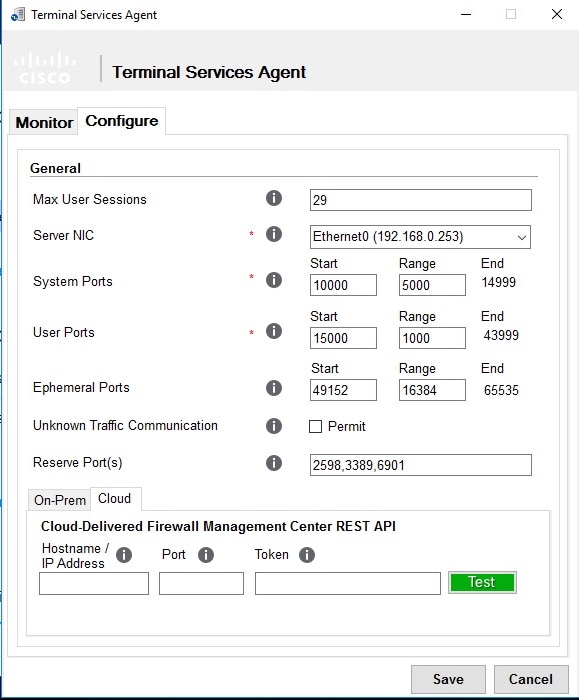
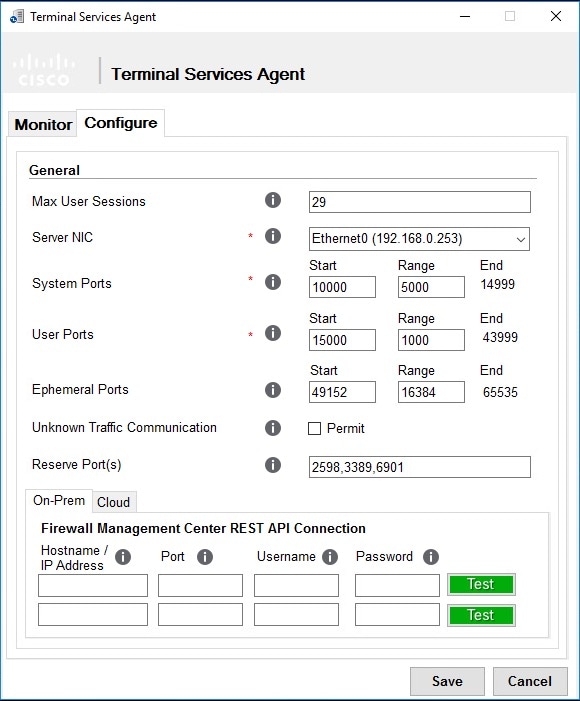
Max User Sessions
|
The maximum number of user sessions you want the TS Agent to monitor. A single user can run several user sessions at a time.
This version of the TS Agent supports 29 user sessions by default, up to a maximum of 199 user sessions.
|
29 (the maximum supported value in this version of the TS Agent)
|
|
Server NIC
|
The TS Agent supports using a single network interface controller (NIC) for port translation and server-system communications.
If two or more valid NICs are present on your server, the TS Agent performs port translation only on the address you specify
during configuration.
The TS Agent automatically populates this field with the IPv4 address and/or IPv6 address for each NIC on the server where
the TS Agent is installed. A valid NIC must have a single IPv4 or IPv6 address, or one of each type; a valid NIC cannot have
multiple addresses of the same type.
|
Note
|
If the server's IP address changes, you are prompted to save the configuration and reboot the server to make the change effective.
|
|
Note
|
You must disable router advertisement messages on any devices connected to your server. If router advertisements are enabled,
the devices may assign multiple IPv6 addresses to NICs on your server and invalidate the NICs for use with the TS Agent.
|
|
Ethernet 2 (192.0.2.1) (a NIC on your server)
|
|
System Ports
|
The port range you use for system processes. The TS Agent ignores this activity. Configure a Start port to indicate where you want to begin the range. Configure a Range value to indicate the number of ports you want to designate for each individual system process.
Cisco recommends a Range value of 5000 or more. If you notice the TS Agent frequently runs out of ports for system processes, increase your Range value.
|
Note
|
If a system process requires a port that falls outside your designated System Ports, add the port to the Exclude Port(s) field. If you do not identify a port used by system processes in the System Ports range or exclude it, system processes might fail.
|
The TS Agent automatically populates the End value using the following formula:
( [Start value] + [Range value] ) - 1
If your entries cause the End value to exceed the Start value of User Ports, you must adjust your Start and Range values.
|
Start set to 10000 and Range set to 5000
|
|
User Ports
|
The port range you want to designate for users. Configure a Start port to indicate where you want to begin the range. Configure a Range value to indicate the number of ports you want to designate for TCP or UDP connections in each individual user session.
|
Note
|
ICMP traffic is passed without being port mapped.
|
Cisco recommends a Range value of 1000 or more. If you notice the TS Agent frequently runs out of ports for user traffic, increase your Range value.
|
Note
|
When the number of ports used exceeds the value of Range, user traffic is blocked.
|
The TS Agent automatically populates the End value using the following formula:
[Start value] + ( [Range value] * [Max User Sessions value] ) - 1
If your entries cause the End value to exceed 65535, you must adjust your Start and Range values.
|
Start set to
15000 and
Range set to
1000
|
|
Ephemeral Ports
|
Enter a range of ephemeral ports (also referred to as dynamic ports) to allow the TS Agent to monitor.
|
Start set to
49152 and
Range set to
16384
|
|
Unknown Traffic Communication
|
Check Permit to allow the TS Agent to permit traffic over System ports; however, the TS Agent does not track port usage. System ports
are used by the Local System account or other local user accounts. (A local user account exists only on the TS Agent server;
it has no corresponding Active Directory account.) You can choose this option to permit the following types of traffic:
-
Permit traffic run by the Local System account (such as Server Message Block (SMB)) instead of being blocked. The
Cloud-delivered Firewall Management Center or On-Prem Firewall Management CenterFMC identifies this traffic as coming from the Unknown user because the user does not exist in Active Directory.
Enabling this option also enables you to successfully test the connection with the
Cloud-delivered Firewall Management Center or On-Prem Firewall Management CenterFMC if you log in to the TS Agent server using a local system account.
-
When a user or system session exhausts all available ports in its range, the TS Agent allows the traffic over ephemeral ports.
This option enables the traffic; the
Cloud-delivered Firewall Management Center or On-Prem Firewall Management CenterFMC identifies the traffic as coming from the Unknown user.
This is especially useful when System ports are needed for keeping system healthy, such as domain controller updates, authentications,
Windows Management Interface (WMI) queries, and so on.
Uncheck to block traffic on system ports.
|
n/a
|
|
Reserve Port(s)
|
The port(s) you want the TS Agent to ignore. Enter the ports you want to exclude as a comma-separated list.
The TS Agent automatically populates Reserve Port(s) with default port values for the Citrix MA Client (2598), Citrix Provisioning (6910), and Windows Terminal Server (3389). If you do not exclude the proper ports, applications requiring those ports might fail.
If you're using Citrix Provisioning and you're upgrading from an earlier TS Agent version, you must enter 6910 in this field.
The value you specify in the TS Agent Reserve Port(s) field must match one of the Citrix Provisioning First and Last UDP port numbers ports.
|
Caution
|
Failure to specify the correct port will cause clients to fail to boot.
|
|
Note
|
If a process on your server is using or listening in on a port that is not in your System Ports range, you must manually exclude that port using the Reserve Port(s) field.
|
|
Note
|
If there is a client application installed on your server and the application is configured to bind to a socket using a specific
port number, you must use the Reserve Port(s) field to exclude that port from translation.
|
|
Typically one of the following:
-
2598,3389 (the Citrix MA Client and Windows Terminal Server ports)
-
2598,3389, 6910 (the Citrix MA Client, Windows Terminal Server, and Citrix Provisioning ports)
|

 to do that.
to do that.
 )
) Feedback
Feedback