Cisco ISE-PIC Terminology
This guide uses the following terms when discussing Cisco ISE-PIC:
|
Term |
Definition |
|---|---|
|
GUI |
Graphic user interface. GUI refers to any of the screens and tabs in the software installation of ISE-PIC. |
|
NIC |
Network interface card. |
|
Node |
An individual physical or virtual Cisco ISE-PIC appliance. |
|
PAN |
The main node in your ISE-PIC deployment is the primary administration node (PAN) and this is the node from which you can perform all available actions. In ISE-PIC, you can install up to two nodes. If you install the second node, it is referred to as the secondary administration node (secondary PAN). |
|
Parser |
The ISE-PIC backend component that receives syslog messages and breaks that input up into parts that can then be managed, mapped and published to ISE-PIC. The parser goes through each line of information of a syslog message as it arrives, looking for key information. For example, if a parser is configured to look for “mac=”, the parser then parses each line while looking for that phrase. The parser is set up to then communicate the defined information to ISE once it has found the key phrase that was configured. |
|
Primary node |
The main node in your ISE-PIC deployment is the primary administration node (PAN) and this is the node from which you can perform all available actions. In ISE-PIC, you can install up to two nodes. If you install the second node, it is referred to as the secondary administration node (secondary PAN). |
|
Probe |
Probes are mechanisms that collect data from a given source. Probe is a generic term that describes any mechanism, but does not specifically describe how the data is collected or what is collected. For example, an Active Directory (AD) probe helps ISE-PIC collect data from AD while a syslog probe collects data from a parser that reads syslog messages. |
|
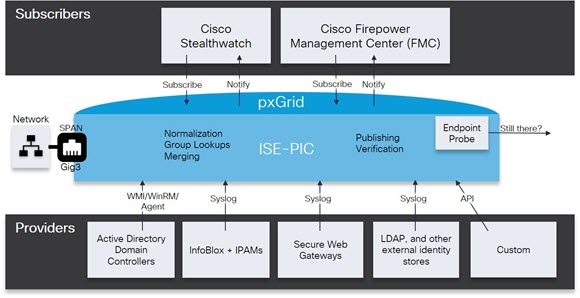
Provider |
Clients or sources from which ISE-PIC receives, maps and publishes user identity information. |
|
Secondary node |
The main node in your ISE-PIC deployment is the primary administration node (PAN) and this is the node from which you can perform all available actions. In ISE-PIC, you can install up to two nodes. If you install the second node, it is referred to as the secondary administration node (secondary PAN). |
|
Subscriber |
Systems that subscribe to the ISE-PIC services in order to receive user identity information. |

 Feedback
Feedback