Power On the Firewall
System power is controlled by a rocker power switch located on the rear of the firewall. The rocker power switch provides a soft notification that supports graceful shutdown of the system to reduce the risk of system software and data corruption.
 Note |
The first time you boot up the firewall, threat defense initialization can take approximately 15 to 30 minutes. |
Before you begin
It's important that you provide reliable power for your firewall (for example, using an uninterruptable power supply (UPS)). Loss of power without first shutting down can cause serious file system damage. There are many processes running in the background all the time, and losing power does not allow the graceful shutdown of your system.
Procedure
|
Step 1 |
Attach the power cord to the firewall, and connect it to an electrical outlet. |
|
Step 2 |
Turn the power on using the rocker power switch located on the rear of the chassis, adjacent to the power cord. 
|
|
Step 3 |
Check the Power LED on the back of the firewall; if it is solid green, the firewall is powered on. 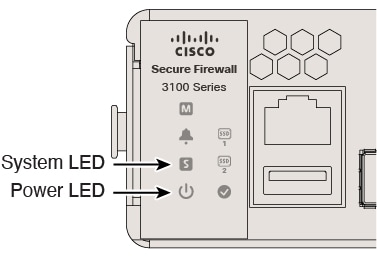
|
|
Step 4 |
Check the System LED on the back of the firewall; after it is solid green, the system has passed power-on diagnostics. |

 Feedback
Feedback