Access Control Policy (Syslog: ACPolicy)
The access control policy associated with the intrusion policy where the intrusion, preprocessor, or decoder rule that generated
the event is enabled.
Access Control Rule (Syslog: AccessControlRuleName)
The access control rule that invoked the intrusion policy that generated the event. Default Action indicates that the intrusion policy where the rule is enabled is not associated with a specific access control rule but,
instead, is configured as the default action of the access control policy.
This field is empty (or, for syslog messages, omitted) if there is:
-
No associated rule/default action: Intrusion inspection was associated with neither an access control rule nor the default
action, for example, if the packet was examined by the intrusion policy specified to handle packets that must pass before
the system can determine which rule to apply. (This policy is specified in the Advanced tab of the access control policy.)
-
No associated connection event: The connection event logged for the session has been purged from the database, for example,
if connection events have higher turnover than intrusion events.
Application Protocol (Syslog: ApplicationProtocol)
The application protocol, if available, which represents communications between hosts detected in the traffic that triggered
the intrusion event.
Application Protocol Category and Tag
Criteria that characterize the application to help you understand the application's function.
Application Risk
The risk associated with detected applications in the traffic that triggered the intrusion event: Very High, High, Medium,
Low, and Very Low. Each type of application detected in a connection has an associated risk; this field displays the highest
risk of those.
Business Relevance
The business relevance associated with detected applications in the traffic that triggered the intrusion event: Very High,
High, Medium, Low, and Very Low. Each type of application detected in a connection has an associated business relevance; this
field displays the lowest (least relevant) of those.
Classification (Syslog: Classification)
The classification where the rule that generated the event belongs.
See a list of possible classification values in Intrusion Event Details.
When searching this field, enter the classification number, or all or part of the classification name or description for the
rule that generated the events you want to view. You can also enter a comma-separated list of numbers, names, or descriptions.
Finally, if you add a custom classification, you can also search using all or part of its name or description.
Client (Syslog: Client)
The client application, if available, which represents software running on the monitored host detected in the traffic that
triggered the intrusion event.
Client Category and Tag
Criteria that characterize the application to help you understand the application's function.
Connection Counter (Syslog Only)
A counter that distinguishes one connection from another simultaneous connection. This field has no significance on its own.
The following fields collectively uniquely identify the connection event
associated with a particular intrusion event: DeviceUUID, First
Packet Time, Connection Instance ID, and Connection Counter.
Connection Instance ID (Syslog Only)
The Snort instance that processed the connection event. This field has no significance on its own.
The following fields collectively uniquely identify the connection event
associated with a particular intrusion event: DeviceUUID, First
Packet Time, Connection Instance ID, and Connection Counter.
Count
The number of events that match the information that appears in each row. Note that the Count field appears only after you
apply a constraint that creates two or more identical rows. This field is not searchable.
CVE ID
This field is a search field only.
Search by the identification number associated with the vulnerability in MITRE’s Common Vulnerabilities and Exposures (CVE)
database (https://cve.mitre.org/).
Destination Continent
The continent of the receiving host involved in the intrusion event.
Destination Country
The country of the receiving host involved in the intrusion event.
Destination Host Criticality
The destination host criticality (value of the Host Criticality attribute for that corresponding host) when the event is generated.
Keep in mind that this field is not updated when the criticality of the host changes. However, new events will have the new
criticality value.
Destination Port / ICMP Code (Syslog: DstPort, ICMPCode)
The port number for the host receiving the traffic. For ICMP traffic, where there is no port number, this field displays the
ICMP code.
Device
The managed device where the access control policy was deployed.
DeviceUUID (Syslog Only)
The unique identifier of the firewall device that generated an event.
The following fields collectively uniquely identify the connection event associated with a particular intrusion event: DeviceUUID,
First Packet Time, Connection Instance ID, and Connection Counter.
Domain
The domain of the device that detected the intrusion. This field is only present if you have ever configured the management center for multitenancy.
Egress Interface (Syslog: EgressInterface)
The egress interface of the packet that triggered the event. This interface column is not populated for a passive interface.
Egress Security Zone (Syslog: EgressZone)
The egress security zone of the packet that triggered the event. This security zone field is not populated in a passive deployment.
Egress Virtual Router
In networks using virtual routing, the name of the virtual router through which traffic exited the network.
Email Attachments
The MIME attachment file name that was extracted from the MIME Content-Disposition header. To display attachment file names,
you must enable the SMTP preprocessor Log MIME Attachment Names option. Multiple attachment file names are supported.
Email Headers
This field is a search field only.
The data that was extracted from the email header.
To associate email headers with intrusion events for SMTP traffic, you must enable the SMTP preprocessor Log Headers option.
Email Recipient
The address of the email recipient that was extracted from the SMTP RCPT TO command. To display a value for this field, you
must enable the SMTP preprocessor Log To Addresses option. Multiple recipient addresses are supported.
Email Sender
The address of the email sender that was extracted from the SMTP MAIL FROM command. To display a value for this field, you
must enable the SMTP preprocessor Log From Address option. Multiple sender addresses are supported.
First Packet Time (Syslog Only)
The time the system encountered the first packet.
The following fields collectively uniquely identify the connection event
associated with a particular intrusion event: DeviceUUID, First
Packet Time, Connection Instance ID, and Connection Counter.
Generator
The component that generated the event.
See also information about the following intrusion event fields: GID, Message, and Snort ID.
GID (Syslog Only)
Generator ID; the ID of the component that generated the event.
See also information about the following intrusion event fields: Generator, Message, and Snort ID.
HTTP Hostname
The host name, if present, that was extracted from the HTTP request Host header. Note that request packets do not always include
the host name.
To associate host names with intrusion events for HTTP client traffic, you must enable the HTTP Inspect preprocessor Log Hostname option.
In table views, this column displays the first fifty characters of the extracted host name. You can hover your pointer over
the displayed portion of an abbreviated host name to display the complete name, up to 256 bytes. You can also display the
complete host name, up to 256 bytes, in the packet view.
HTTP Response Code (Syslog: HTTPResponse)
The HTTP status code sent in response to a client's HTTP request over the connection that triggered the event.
HTTP URI
The normalized URI, if present, associated with the HTTP request packet that triggered the intrusion event. Note that request
packets do not always include a URI.
To associate URIs with intrusion events for HTTP traffic, you must enable the HTTP Inspect preprocessor Log URI option.
To see the associated HTTP URI in intrusion events triggered by HTTP responses, you should configure HTTP server ports in
the Perform Stream Reassembly on Both Ports option; note, however, that this increases resource demands for traffic reassembly.
This column displays the first fifty characters of the extracted URI. You can hover your pointer over the displayed portion
of an abbreviated URI to display the complete URI, up to 2048 bytes. You can also display the complete URI, up to 2048 bytes,
in the packet view.
Impact
The impact level in this field indicates the correlation between intrusion data, network discovery data, and vulnerability
information.
When searching this field, do not specify impact icon colors or partial strings. For example, do not use blue, level 1, or 0. Valid case-insensitive values are:
-
Impact 0, Impact Level 0
-
Impact 1, Impact Level 1
-
Impact 2, Impact Level 2
-
Impact 3, Impact Level 3
-
Impact 4, Impact Level 4
Because no operating system information is available for hosts added to the network map from NetFlow data, the system cannot
assign Vulnerable (impact level 1: red) impact levels for intrusion events involving those hosts. In such cases, use the host
input feature to manually set the operating system identity for the hosts.
Ingress Interface (Syslog: IngressInterface)
The ingress interface of the packet that triggered the event. Only this interface column is populated for a passive interface.
Ingress Security Zone (Syslog: IngressZone)
The ingress security zone or tunnel zone of the packet that triggered the event. Only this security zone field is populated in a passive deployment.
Ingress Virtual Router
In networks using virtual routing, the name of the virtual router through which traffic entered the network.
Inline Result (Syslog: InlineResult)
In workflow and table views, this field displays one of the following:
Table 1. Inline Result Field Contents in Workflow and Table Views
|
This Icon
|
Indicates
|
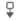 |
The system dropped the packet that triggered the rule.
|
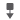 |
IPS would have dropped the packet if you enabled the Drop when Inline intrusion policy option (in an inline deployment), or if a Drop and Generate rule generated the event while the system was
pruning.
|
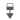 |
IPS may have transmitted or delivered the packet to the destination, but the connection that contained this packet is now
blocked.
|
|
No icon (blank)
|
The triggered rule was not set to Drop and Generate Events
|
The following table lists the possible reasons for the inline results — Would have dropped and Partially dropped.
|
Inline Result
|
Reason
|
Detailed Reason
|
|
Would Have Dropped
|
Interface in Passive or Tap mode
|
You have configured the interfaces in inline tap or passive mode.
|
|
Intrusion Policy in "Detection" Inspection Mode
|
You have set the inspection mode in the intrusion policy to Detection.
|
|
Connection Timed Out
|
The Snort inspection engine has suspended the inspection as the TCP/IP connection timed out.
|
|
Partially Dropped
|
Connection Closed (0x01)
|
While creating a new flow, if the allocated flows are more than the allowed number of flows, the Snort inspection engine prunes
the least recently used flows.
|
|
Connection Closed (0x02)
|
When reloading the Snort inspection engine causes a memory adjustment, the engine prunes the least recently used flows.
|
|
Connection Closed (0x04)
|
When the Snort inspection engine is gracefully shutting down, the engine purges all the active flows.
|
In a passive deployment, the system does not drop packets, including when an inline interface is in tap mode, regardless of
the rule state or the inline drop behavior of the intrusion policy.
When searching this field, enter either of the following:
-
dropped to specify whether the packet is dropped in an inline deployment.
-
would have dropped to specify whether the packet would have dropped if the intrusion policy had been set to drop packets in an inline deployment.
-
partially dropped to specify whether the packet is transmitted or delivered to the destination, but the connection that contained this packet
is now blocked.
Intrusion Policy (Syslog: IntrusionPolicy)
The intrusion policy where the intrusion, preprocessor, or decoder rule that generated the event was enabled. You can choose
an intrusion policy as the default action for an access control policy, or you can associate an intrusion policy with an access
control rule.
IOC (Syslog: NumIOC)
Whether the traffic that triggered the intrusion event also triggered an indication of compromise (IOC) for a host involved
in the connection.
When searching this field, specify triggered or n/a.
Message (Syslog: Message)
The explanatory text for the event. For rule-based intrusion events, the event message is pulled from the rule. For decoder-
and preprocessor-based events, the event message is hard coded.
The Generator and Snort IDs (GID and SID) and the SID version (Revision) are appended in parentheses to the end of each message
in the format of numbers separated by colons (GID:SID:version). For example (1:36330:2).
MITRE
A count of techniques that you can click to bring up a modal, which shows the full list of MITRE tactics and techniques within
that hierarchy.
MPLS Label (Syslog: MPLS_Label)
The Multiprotocol Label Switching label associated with the packet that triggered the intrusion event.
Network Analysis Policy (Syslog: NAPPolicy)
The network analysis policy, if any, associated with the generation of the event.
This field displays the first fifty characters of the extracted URI. You can hover your pointer over the displayed portion
of an abbreviated URI to display the complete URI, up to 2048 bytes. You can also display the complete URI, up to 2048 bytes,
in the packet view.
Original Client IP
The original client IP address that was extracted from an X-Forwarded-For (XFF), True-Client-IP, or custom-defined HTTP header.
To display a value for this field, you must enable the HTTP preprocessor Extract Original Client IP Address option in the network analysis policy. Optionally, in the same area of the network analysis policy, you can also specify
up to six custom client IP headers, as well as set the priority order in which the system selects the value for the Original
Client IP event field.
Priority (Syslog: Priority)
The event priority as determined by the Talos Intelligence Group. The priority corresponds to either the value of the priority keyword or the value for the classtype keyword. For other intrusion events, the priority is determined by the decoder or preprocessor. Valid values are high, medium,
and low.
Protocol (Syslog: Protocol)
In the Secure Firewall Management Center web interface, this field is a search field only.
The name or number of the transport protocol used in the connection as listed in http://www.iana.org/assignments/protocol-numbers. This is the protocol associated with the source and destination port/ICMP column.
Reviewed By
The name of the user who reviewed the event. When searching this field, you can enter unreviewed to search for events that have not been reviewed.
Revision (Syslog Only)
The version of the signature that was used to generate the event.
See also information about the following intrusion event fields: Generator, GID, Message, SID, and Snort ID.
Rule Group
A count of non-MITRE rule groups that you can click to bring up a modal, which shows the full list of rule groups.
Security Context (Syslog: Context)
The metadata identifying the virtual firewall group through which the traffic passed. The system only populates this field
for ASA FirePOWER in multiple context mode.
SID (Syslog Only)
The signature ID (also known as the Snort ID) of the rule that generated the event.
See also information about the following intrusion event fields: Generator, GID, Message, Revision, and Snort ID.
Snort ID
This field is a search field only.
(For the syslog field, see SID.)
When performing your search: Specify the Snort ID (SID) of the rule that generated the event or, optionally, specify the combination Generator ID (GID) and SID of the rule,
where the GID and SID are separated with a colon (:) in the format GID:SID. You can specify any of the values in the following
table:
Table 2. Snort ID Search Values
|
Value
|
Example
|
|
a single SID
|
10000
|
|
a SID range
|
10000-11000
|
|
greater than a SID
|
>10000
|
|
greater than or equal to a SID
|
>=10000
|
|
less than a SID
|
<10000
|
|
less than or equal to a SID
|
<=10000
|
|
a comma-separated list of SIDs
|
10000,11000,12000
|
|
a single GID:SID combination
|
1:10000
|
|
a comma-separated list of GID:SID combinations
|
1:10000,1:11000,1:12000
|
|
a comma-separated list of SIDs and GID:SID combinations
|
10000,1:11000,12000
|
The SID of the events you are viewing is listed in the Message column. For more information, see the description in this section
for the Message field.
Source Continent
The continent of the sending host involved in the intrusion event.
Source Country
The country of the sending host involved in the intrusion event.
Source Host Criticality
The source host criticality (value of the Host Criticality attribute for that corresponding host) when the event is generated.
Keep in mind that this field is not updated when the criticality of the host changes. However, new events will have the new
criticality value.
Source Port / ICMP Type (Syslog: SrcPort, ICMPType)
The port number on the sending host. For ICMP traffic, where there is no port number, this field displays the ICMP type.
Source User (Syslog: User)
The username associated with the IP address of the host that initiated the connection, which may or may not be the source
host of the exploit. This user value is typically known only for users on your network.
If applicable, the username is preceded by <realm>\.
SSL Actual Action (Syslog: SSLActualAction)
In the Secure Firewall Management Center web interface, this field is a search field only.
The action the system applied to encrypted traffic:
- Block/Block with reset
-
Represents blocked encrypted connections.
- Decrypt (Resign)
-
Represents an outgoing connection decrypted using a re-signed server certificate.
- Decrypt (Replace Key)
-
Represents an outgoing connection decrypted using a self-signed server certificate with a substituted public key.
- Decrypt (Known Key)
-
Represents an incoming connection decrypted using a known private key.
- Default Action
-
Indicates the connection was handled by the default action.
- Do not Decrypt
-
Represents a connection the system did not decrypt.
Field values are displayed in the SSL Status field on the search workflow pages.
SSL Certificate Information
This field is a search field only.
The information stored on the public key certificate used to encrypt traffic, including:
-
Subject/Issuer Common Name
-
Subject/Issuer Organization
-
Subject/Issuer Organization Unit
-
Not Valid Before/After
-
Serial Number
-
Certificate Fingerprint
-
Public Key Fingerprint
SSL Failure Reason
This field is a search field only.
The reason the system failed to decrypt encrypted traffic:
-
Unknown
-
No Match
-
Success
-
Uncached Session
-
Unknown Cipher Suite
-
Unsupported Cipher Suite
-
Unsupported SSL Version
-
SSL Compression Used
-
Session Undecryptable in Passive Mode
-
Handshake Error
-
Decryption Error
-
Pending Server Name Category Lookup
-
Pending Common Name Category Lookup
-
Internal Error
-
Network Parameters Unavailable
-
Invalid Server Certificate Handle
-
Server Certificate Fingerprint Unavailable
-
Cannot Cache Subject DN
-
Cannot Cache Issuer DN
-
Unknown SSL Version
-
External Certificate List Unavailable
-
External Certificate Fingerprint Unavailable
-
Internal Certificate List Invalid
-
Internal Certificate List Unavailable
-
Internal Certificate Unavailable
-
Internal Certificate Fingerprint Unavailable
-
Server Certificate Validation Unavailable
-
Server Certificate Validation Failure
-
Invalid Action
Field values are displayed in the SSL Status field on the search workflow pages.
SSL Status
The action associated with the SSL Actual Action (SSL rule, default action, or undecryptable traffic action) that logged the encrypted connection.
If the system fails to decrypt an encrypted connection, it displays the SSL Actual Action (undecryptable traffic action) taken, as well as the SSL Failure Reason. For example, if the system detects traffic encrypted with an unknown cipher suite and allows it without further inspection,
this field displays Do Not Decrypt (Unknown Cipher Suite).
Click the Lock icon to view certificate details.
When searching this field, enter one or more of the SSL Actual Action and SSL Failure Reason values to view encrypted traffic the system handled or failed to decrypt.
SSL Subject/Issuer Country
This field is a search field only.
A two-character ISO 3166-1 alpha-2 country code for the subject or issuer country associated with the encryption certificate.
Time
The date and time of the event. This field is not searchable.
VLAN ID (Syslog: VLAN_ID)
The innermost VLAN ID associated with the packet that triggered the intrusion event.
Web Application (Syslog: WebApplication)
The web application, which represents the content or requested URL for HTTP traffic detected in the traffic that triggered
the intrusion event.
If the system detects an application protocol of HTTP but cannot detect a specific web application, the system supplies a
generic web browsing designation instead.
Web Application Category and Tag
Criteria that characterize the application to help you understand the application's function.

 )
) )
) )
) )
) )
)

 Feedback
Feedback