Introduction to Correlation Policies and Rules
You can use the correlation feature to respond in real time to threats to your network, using correlation policies.
A correlation policy violation occurs when the activity on your network triggers either a correlation rule or compliance allow list within an active correlation policy.
Correlation Rules
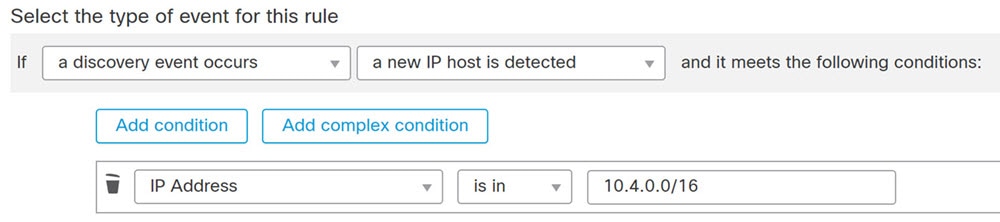
When a correlation rule in an active correlation policy triggers, the system generates a correlation event. Correlation rules can trigger when:
-
The system generates a specific type of event (connection, intrusion, malware, discovery, user activity, and so on).
-
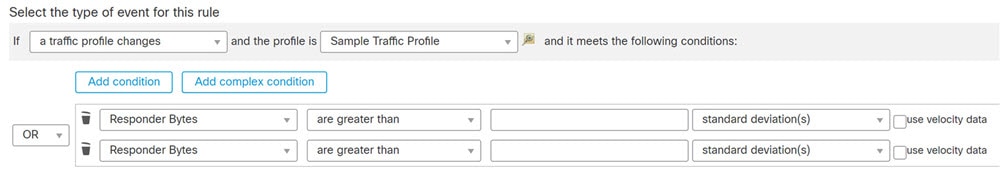
Your network traffic deviates from its normal profile.
You can constrain correlation rules in the following ways:
-
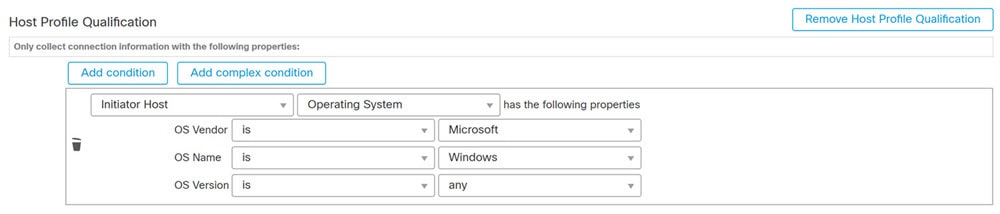
Add a host profile qualification to constrain the rule using information from the host profile of a host involved in the triggering event.
-
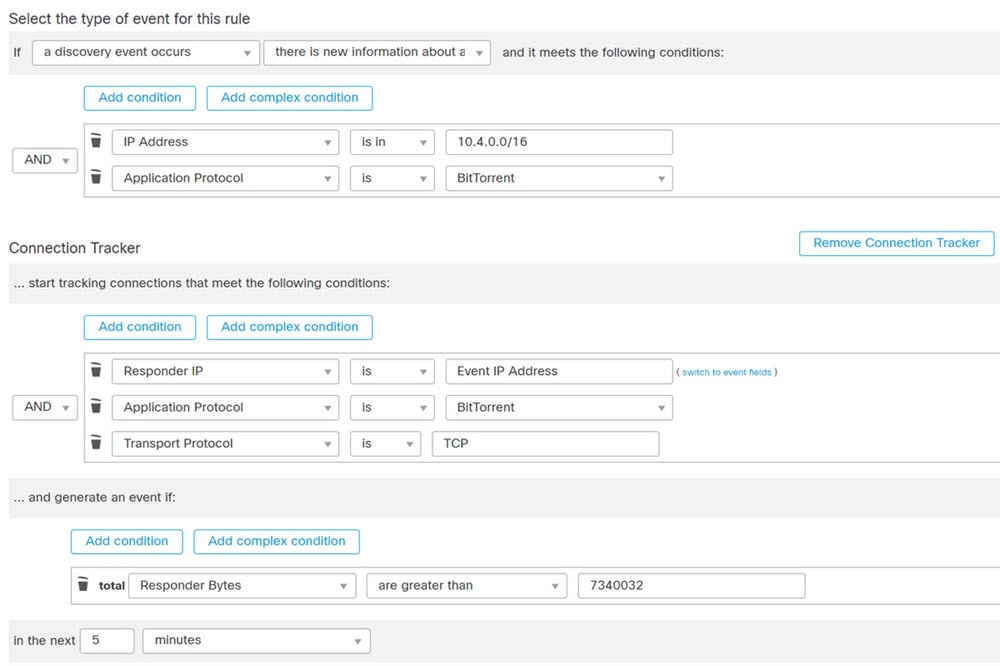
Add a connection tracker to a correlation rule so that after the rule’s initial criteria are met, the system begins tracking certain connections. Then, a correlation event is generated only if the tracked connections meet additional criteria.
-
Add a user qualification to a correlation rule to track certain users or groups of users. For example, you can constrain a correlation rule so that it triggers only for a particular user's traffic, or traffic from a specific department.
-
Add snooze periods. When a correlation rule triggers, a snooze period causes that rule not to trigger again for a specified interval. After the snooze period elapses, the rule can trigger again and start a new snooze period.
-
Add inactive periods. During inactive periods, correlation rules do not trigger.
Although you can configure correlation rules without licensing your deployment, rules that use unlicensed components do not trigger.
Compliance Allow Lists
A compliance allow list specifies which operating systems, applications (web and client), and protocols are allowed on hosts on your network. When a host violates an allow list used in an active correlation policy, the system generates an allow list event.
Correlation Responses
Responses to correlation policy violations include simple alerts and various remediations (such as scanning a host). You can associate each correlation rule or allow list with a single response or group of responses.
If network traffic triggers multiple rules or allow lists, the system launches all the responses associated with each rule and allow list.
Correlation and Multitenancy
In a multidomain deployment, you can create correlation policies at any domain level, using whatever rules, allow lists, and responses are available at that level. Higher-level domain administrators can perform correlation within or across domains:
-
Constraining a correlation rule by domain matches events reported by that domain's descendants.
-
Higher-level domain administrators can create compliance allow lists that evaluate hosts across domains. You can target different subnets in different domains in the same allow list.
 Note |
The system builds a separate network map for each leaf domain. Using literal configurations (such as IP addresses, VLAN tags, and usernames) to constrain cross-domain correlation rules can have unexpected results. |
 )
)
 )
) )
)









 Feedback
Feedback