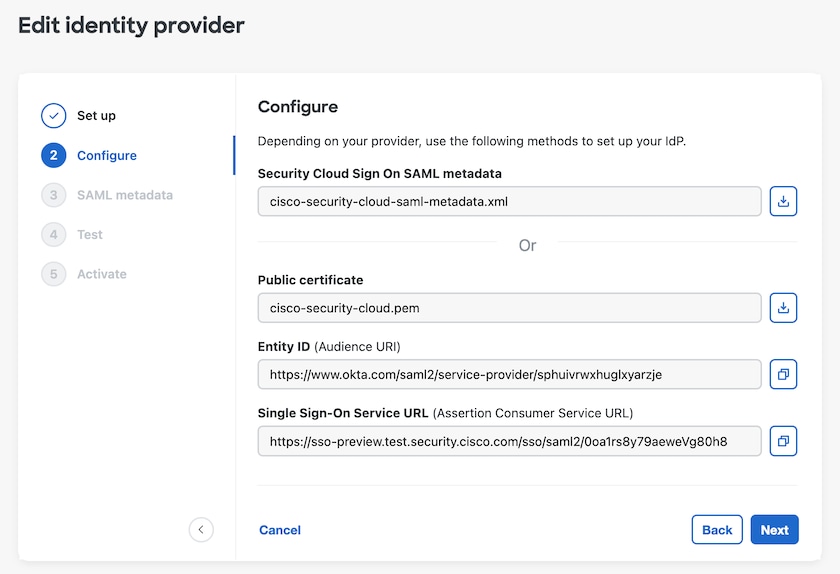
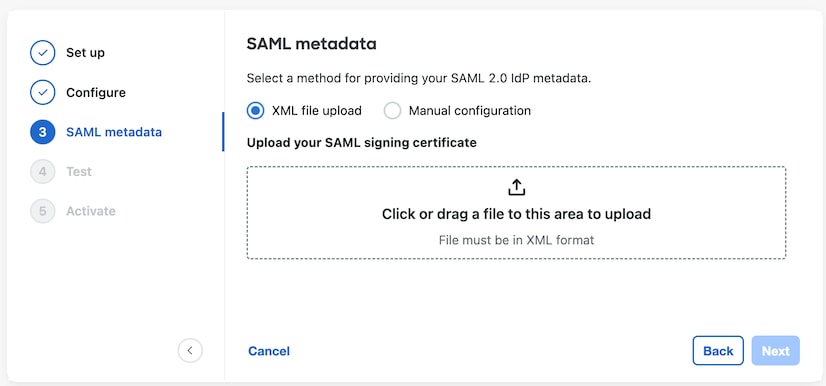
Prerequisites
Integrating your identity provider with Security Cloud Sign On requires the following:
-
The ability to create and configure SAML applications in your identity provider's management portal





 Feedback
Feedback