Hardware Requirements for a Single-Node Site
To install Security Manager in a single-node HA environment, you can configure a fault-tolerant storage array or use internal disks.
The following are the server hardware specifications for a single-node site:
-
Server which meets the basic processor and RAM requirements as described in the Installation Guide for Cisco Security Manager 4.29
-
Minimum of one Ethernet interface (two recommended)
-
Minimum of two physical drives (six recommended)
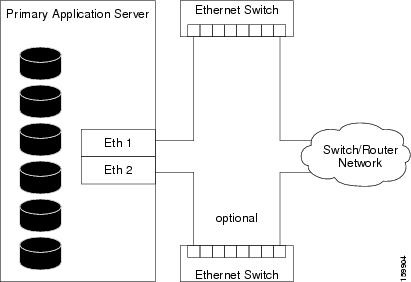
The figure shows using two Ethernet connections from the server to the switch/router network for redundancy. If an Ethernet port or switch fails, communication to the server is maintained. If this level of network redundancy is not required, you can use a single connection to the switch/router network (that is, Eth 2 and its associated Ethernet switch are optional).

 Feedback
Feedback