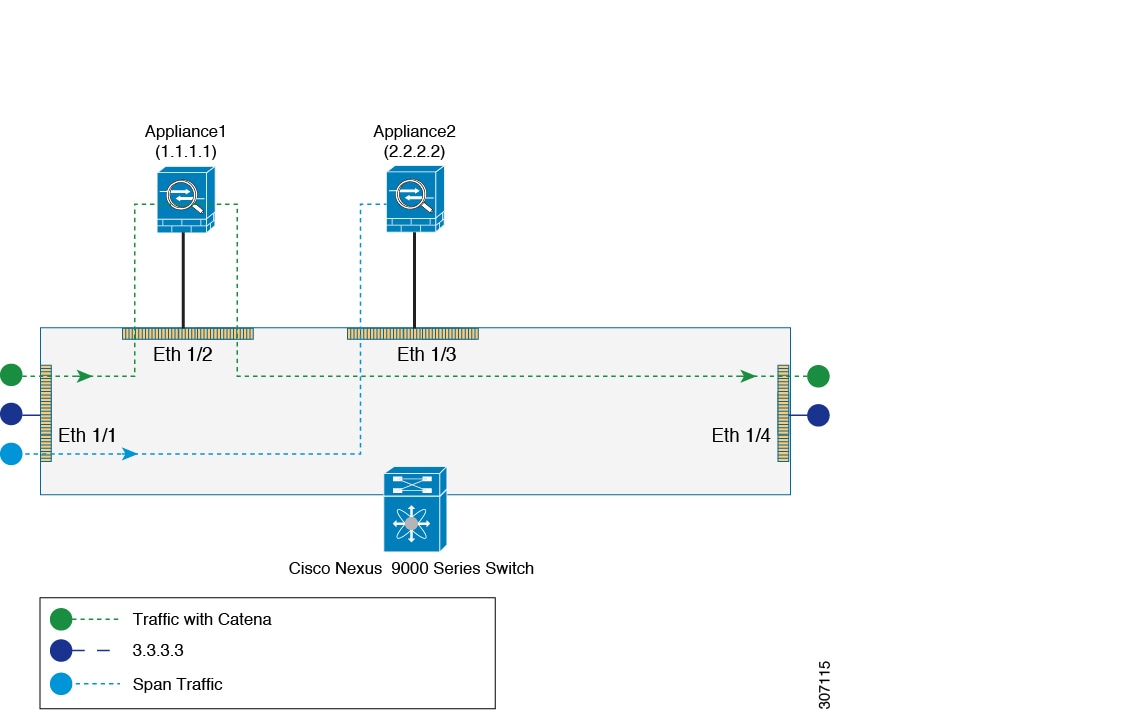
Enabling Chaining using Deployment Modes
You can create multiple chains, each comprising multiple functions and services; configure each chain to run on multiple devices; and apply network policies to these elements. You can create chains using the following deployment modes:
-
Transparent mode
-
Routed mode
-
Mixed mode, including both Transparent and Routed mode in the same chain




 Feedback
Feedback