- New and Changed Information
- Index
- Preface
- Overview
- Configuring AAA
- Configuring RADIUS
- Configuring TACACS+
- Configuring User Accounts and RBAC
- Configuring 802.1X
- Configuring IP ACLs
- Configuring MAC ACLs
- Configuring VLAN ACLs
- Configuring Port Security
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection
- Configuring Source Guard
- Configuring Keychain Management
- Configuring Traffic Storm Control
- Information About TACACS+
- Licensing Requirements for TACACS+
- Prerequisites for TACACS+
- Guidelines and Limitations
- Configuring TACACS+
- TACACS+ Server Configuration Process
- Enabling TACACS+
- Adding a TACACS+ Server Host
- Copying a TACACS+ Server Host
- Deleting a TACACS+ Server Host
- Configuring a Global TACACS+ Key
- Configuring a Key for a Specific TACACS+ Server
- Adding a TACACS+ Server Group
- Adding a TACACS+ Server Host to a TACACS+ Server Group
- Deleting a TACACS+ Server Host from a TACACS+ Server Group
- Deleting a TACACS+ Server Group
- Specifying a TACACS+ Server at Login
- Configuring the Global TACACS+ Timeout Interval
- Configuring the Timeout Interval for a Server
- Configuring TCP Ports
- Configuring Periodic TACACS+ Server Monitoring
- Configuring the Dead-Time Interval
- Disabling TACACS+
- Displaying TACACS+ Statistics
- Where to Go Next
- Field Descriptions for TACACS+ Server Groups and Servers
- Additional References
- Feature History for TACACS+
Configuring TACACS+
This chapter describes how to configure the Terminal Access Controller Access Control System Plus (TACACS+) protocol on Cisco NX-OS devices.
This chapter includes the following sections:
•![]() Licensing Requirements for TACACS+
Licensing Requirements for TACACS+
•![]() Displaying TACACS+ Statistics
Displaying TACACS+ Statistics
•![]() Field Descriptions for TACACS+ Server Groups and Servers
Field Descriptions for TACACS+ Server Groups and Servers
Information About TACACS+
The TACACS+ security protocol provides centralized validation of users attempting to gain access to a Cisco NX-OS device. TACACS+ services are maintained in a database on a TACACS+ daemon running, typically, on a UNIX or Windows NT workstation. You must have access to and must configure a TACACS+ server before the configured TACACS+ features on your NX-OS device are available.
TACACS+ provides for separate authentication, authorization, and accounting facilities. TACACS+ allows for a single access control server (the TACACS+ daemon) to provide each service—authentication, authorization, and accounting—independently. Each service can be tied into its own database to take advantage of other services available on that server or on the network, depending on the capabilities of the daemon.
The TACACS+ client/server protocol uses TCP (TCP port 49) for transport requirements. Cisco NX-OS devices provide centralized authentication using the TACACS+ protocol.
This section includes the following topics:
•![]() TACACS+ Operation for User Login
TACACS+ Operation for User Login
•![]() Default TACACS+ Server Encryption Type and Secret Key
Default TACACS+ Server Encryption Type and Secret Key
TACACS+ Advantages
TACACS+ has the following advantages over RADIUS authentication:
•![]() Provides independent AAA facilities. For example, the Cisco NX-OS device can authorize access without authenticating.
Provides independent AAA facilities. For example, the Cisco NX-OS device can authorize access without authenticating.
•![]() Uses the TCP transport protocol to send data between the AAA client and server, making reliable transfers with a connection-oriented protocol.
Uses the TCP transport protocol to send data between the AAA client and server, making reliable transfers with a connection-oriented protocol.
•![]() Encrypts the entire protocol payload between the switch and the AAA server to ensure higher data confidentiality. The RADIUS protocol only encrypts passwords.
Encrypts the entire protocol payload between the switch and the AAA server to ensure higher data confidentiality. The RADIUS protocol only encrypts passwords.
TACACS+ Operation for User Login
When a user attempts a Password Authentication Protocol (PAP) login to a Cisco NX-OS device using TACACS+, the following actions occur:
1. ![]() When the Cisco NX-OS device establishes a connection, it contacts the TACACS+ daemon to obtain the username and password.
When the Cisco NX-OS device establishes a connection, it contacts the TACACS+ daemon to obtain the username and password.

Note ![]() TACACS+ allows an arbitrary conversation between the daemon and the user until the daemon receives enough information to authenticate the user. This action is usually done by prompting for a username and password combination, but may include prompts for other items, such as mother's maiden name.
TACACS+ allows an arbitrary conversation between the daemon and the user until the daemon receives enough information to authenticate the user. This action is usually done by prompting for a username and password combination, but may include prompts for other items, such as mother's maiden name.
2. ![]() The Cisco NX-OS device will eventually receive one of the following responses from the TACACS+ daemon:
The Cisco NX-OS device will eventually receive one of the following responses from the TACACS+ daemon:
a. ![]() ACCEPT—User authentication succeeds and service begins. If the Cisco NX-OS device requires user authorization, authorization begins.
ACCEPT—User authentication succeeds and service begins. If the Cisco NX-OS device requires user authorization, authorization begins.
b. ![]() REJECT—User authentication failed. The TACACS+ daemon either denies further access to the user or prompts the user to retry the login sequence.
REJECT—User authentication failed. The TACACS+ daemon either denies further access to the user or prompts the user to retry the login sequence.
c. ![]() ERROR—An error occurred at some time during authentication either at the daemon or in the network connection between the daemon and the Cisco NX-OS device. If the Cisco NX-OS device receives an ERROR response, the Cisco NX-OS device tries to use an alternative method for authenticating the user.
ERROR—An error occurred at some time during authentication either at the daemon or in the network connection between the daemon and the Cisco NX-OS device. If the Cisco NX-OS device receives an ERROR response, the Cisco NX-OS device tries to use an alternative method for authenticating the user.
After authentication, the user also undergoes an additional authorization phase if authorization has been enabled on the Cisco NX-OS device. Users must first successfully complete TACACS+ authentication before proceeding to TACACS+ authorization.
3. ![]() If TACACS+ authorization is required, the Cisco NX-OS device again contacts the TACACS+ daemon and it returns an ACCEPT or REJECT authorization response. An ACCEPT response contains attributes that are used to direct the EXEC or NETWORK session for that user and determines the services that the user can access.
If TACACS+ authorization is required, the Cisco NX-OS device again contacts the TACACS+ daemon and it returns an ACCEPT or REJECT authorization response. An ACCEPT response contains attributes that are used to direct the EXEC or NETWORK session for that user and determines the services that the user can access.
Services include the following:
•![]() Telnet, rlogin, Point-to-Point Protocol (PPP), Serial Line Internet Protocol (SLIP), or EXEC services
Telnet, rlogin, Point-to-Point Protocol (PPP), Serial Line Internet Protocol (SLIP), or EXEC services
•![]() Connection parameters, including the host or client IP address (IPv4 or IPv6), access list, and user timeouts
Connection parameters, including the host or client IP address (IPv4 or IPv6), access list, and user timeouts
Default TACACS+ Server Encryption Type and Secret Key
You must configure the TACACS+ secret key to authenticate the switch to the TACACS+ server. A secret key is a secret text string shared between the Cisco NX-OS device and the TACACS+ server host. The length of the key is restricted to 63 characters and can include any printable ASCII characters (white spaces are not allowed). You can configure a global secret key for all TACACS+ server configurations on the Cisco NX-OS device to use.
You can override the global secret key assignment by explicitly using the key option when configuring and individual TACACS+ server.
TACACS+ Server Monitoring
An unresponsive TACACS+ server can delay the processing of AAA requests. A Cisco NX-OS device can periodically monitor an TACACS+ server to check whether it is responding (or alive) to save time in processing AAA requests. The Cisco NX-OS device marks unresponsive TACACS+ servers as dead and does not send AAA requests to any dead TACACS+ servers. A Cisco NX-OS device periodically monitors dead TACACS+ servers and brings them to the alive state once they are responding. This process verifies that a TACACS+ server is in a working state before real AAA requests are sent its way. Whenever an TACACS+ server changes to the dead or alive state, a Simple Network Management Protocol (SNMP) trap is generated and the Cisco NX-OS device displays an error message that a failure is taking place before it can impact performance. See Figure 4-1.
Figure 4-1 TACACS+ Server States
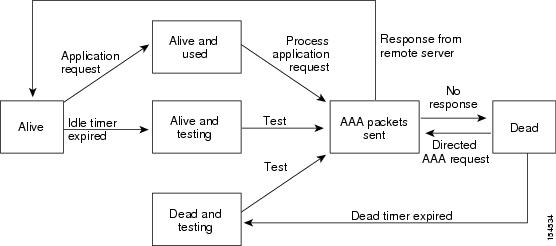

Note ![]() The monitoring interval for alive servers and dead servers are different and can be configured by the user. The TACACS+ server monitoring is performed by sending a test authentication request to the TACACS+ server.
The monitoring interval for alive servers and dead servers are different and can be configured by the user. The TACACS+ server monitoring is performed by sending a test authentication request to the TACACS+ server.
Vendor-Specific Attributes
The Internet Engineering Task Force (IETF) draft standard specifies a method for communicating vendor-specific attributes (VSAs) between the network access server and the TACACS+ server. The IETF uses attribute 26. VSAs allow vendors to support their own extended attributes that are not suitable for general use.
This section includes the following topics:
•![]() Cisco TACACS+ Privilege Levels
Cisco TACACS+ Privilege Levels
Cisco VSA Format
The Cisco TACACS+ implementation supports one vendor-specific option using the format recommended in the IETF specification. The Cisco vendor ID is 9, and the supported option is vendor type 1, which is named cisco-av-pair. The value is a string with the following format:
protocol : attribute separator value *
The protocol is a Cisco attribute for a particular type of authorization, separator is = (equal sign) for mandatory attributes, and * (asterisk) indicates optional attributes.
When you use TACACS+ servers for authentication on a Cisco NX-OS device, the TACACS+ protocol directs the TACACS+ server to return user attributes, such as authorization information, along with authentication results. This authorization information is specified through VSAs.
The following VSA protocol options are supported by the Cisco NX-OS software:
•![]() Shell—Protocol used in access-accept packets to provide user profile information.
Shell—Protocol used in access-accept packets to provide user profile information.
•![]() Accounting—Protocol used in accounting-request packets. If a value contains any white spaces, you should enclose the value within double quotation marks.
Accounting—Protocol used in accounting-request packets. If a value contains any white spaces, you should enclose the value within double quotation marks.
The Cisco NX-OS software supports the following attributes:
•![]() roles—Lists all the roles to which the user belongs. The value field is a string that lists the role names delimited by white space. For example, if the user belongs to roles network-operator and vdc-admin, the value field would be "network-operator vdc-admin." This subattribute, which the TACACS+ server sends in the VSA portion of the Access-Accept frames, can only be used with the shell protocol value. The following examples show the roles attribute as supported by Cisco ACS:
roles—Lists all the roles to which the user belongs. The value field is a string that lists the role names delimited by white space. For example, if the user belongs to roles network-operator and vdc-admin, the value field would be "network-operator vdc-admin." This subattribute, which the TACACS+ server sends in the VSA portion of the Access-Accept frames, can only be used with the shell protocol value. The following examples show the roles attribute as supported by Cisco ACS:
shell:roles="network-operator vdc-admin"
shell:roles*"network-operator vdc-admin"

Note ![]() When you specify a VSA as shell:roles*"network-operator vdc-admin", this VSA is flagged as an optional attribute and other Cisco devices ignore this attribute.
When you specify a VSA as shell:roles*"network-operator vdc-admin", this VSA is flagged as an optional attribute and other Cisco devices ignore this attribute.
•![]() accountinginfo—Stores accounting information in addition to the attributes covered by a standard TACACS+ accounting protocol. This attribute is sent only in the VSA portion of the Account-Request frames from the TACACS+ client on the switch. It can be used only with the accounting protocol data units (PDUs).
accountinginfo—Stores accounting information in addition to the attributes covered by a standard TACACS+ accounting protocol. This attribute is sent only in the VSA portion of the Account-Request frames from the TACACS+ client on the switch. It can be used only with the accounting protocol data units (PDUs).
Cisco TACACS+ Privilege Levels
TACACS+ servers support privilege levels for specifying the permissions that users have when logging into a Cisco NX-OS device. For the maximum privilege level 15, the Cisco NX-OS software applies the network-admin role in the default VDC or the vdc-admin role for nondefault VDCs. All other privilege levels are translated to the vdc-operator role. For more information on user roles, see Chapter 5, "Configuring RBAC."

Note ![]() If you specify a user role in the cisco-av-pair, that takes precedence over the privilege level.
If you specify a user role in the cisco-av-pair, that takes precedence over the privilege level.
Virtualization Support
TACACS+ configuration and operation are local to the virtual device context (VDC). For more information on VDCs, see the Cisco DCNM Virtual Device Context Configuration Guide, Release 4.1.
The Cisco NX-OS device uses virtual routing and forwarding instances (VRFs) to access the TACACS+ servers. For more information on VRFs, see the Cisco DCNM Unicast Routing Configuration Guide, Release 4.1.
Licensing Requirements for TACACS+
The following table shows the licensing requirements for this feature:
Prerequisites for TACACS+
TACACS+ has the following prerequisites:
•![]() Obtain the IPv4 or IPv6 addresses or hostnames for the TACACS+ servers.
Obtain the IPv4 or IPv6 addresses or hostnames for the TACACS+ servers.
•![]() Obtain the secret keys from the TACACS+ servers, if any.
Obtain the secret keys from the TACACS+ servers, if any.
•![]() Ensure that the Cisco NX-OS device is configured as a TACACS+ client of the AAA servers.
Ensure that the Cisco NX-OS device is configured as a TACACS+ client of the AAA servers.
•![]() Ensure that the logging level for TACACS+ in the Cisco NX-OS software is set to 5 using the command-line interface (CLI).
Ensure that the logging level for TACACS+ in the Cisco NX-OS software is set to 5 using the command-line interface (CLI).
switch# configure terminal
switch(config)# logging level tacacs+ 5
Guidelines and Limitations
TACACS+ has the following guidelines and limitations:
•![]() You can configure a maximum of 64 TACACS+ servers on the Cisco NX-OS device.
You can configure a maximum of 64 TACACS+ servers on the Cisco NX-OS device.
•![]() If you have a user account configured on the local Cisco NX-OS device that has the same name as a remote user account on an AAA server, the Cisco NX-OS software applies the user roles for the local user account to the remote user, not the user roles configured on the AAA server.
If you have a user account configured on the local Cisco NX-OS device that has the same name as a remote user account on an AAA server, the Cisco NX-OS software applies the user roles for the local user account to the remote user, not the user roles configured on the AAA server.
Configuring TACACS+
This section includes the following topics:
•![]() TACACS+ Server Configuration Process
TACACS+ Server Configuration Process
•![]() Copying a TACACS+ Server Host
Copying a TACACS+ Server Host
•![]() Deleting a TACACS+ Server Host
Deleting a TACACS+ Server Host
•![]() Configuring a Global TACACS+ Key
Configuring a Global TACACS+ Key
•![]() Configuring a Key for a Specific TACACS+ Server
Configuring a Key for a Specific TACACS+ Server
•![]() Adding a TACACS+ Server Group
Adding a TACACS+ Server Group
•![]() Adding a TACACS+ Server Host to a TACACS+ Server Group
Adding a TACACS+ Server Host to a TACACS+ Server Group
•![]() Deleting a TACACS+ Server Host from a TACACS+ Server Group
Deleting a TACACS+ Server Host from a TACACS+ Server Group
•![]() Deleting a TACACS+ Server Group
Deleting a TACACS+ Server Group
•![]() Specifying a TACACS+ Server at Login
Specifying a TACACS+ Server at Login
•![]() Configuring the Global TACACS+ Timeout Interval
Configuring the Global TACACS+ Timeout Interval
•![]() Configuring the Timeout Interval for a Server
Configuring the Timeout Interval for a Server
•![]() Configuring Periodic TACACS+ Server Monitoring
Configuring Periodic TACACS+ Server Monitoring
•![]() Configuring the Dead-Time Interval
Configuring the Dead-Time Interval
TACACS+ Server Configuration Process
To configure TACACS+ servers, follow these steps:
Step 1 ![]() Enable TACACS+ (see the "Enabling TACACS+" section).
Enable TACACS+ (see the "Enabling TACACS+" section).
Step 2 ![]() Establish the TACACS+ server connections to the Cisco NX-OS device (see the "Adding a TACACS+ Server Host" section).
Establish the TACACS+ server connections to the Cisco NX-OS device (see the "Adding a TACACS+ Server Host" section).
Step 3 ![]() Configure the secret keys for the TACACS+ servers (see the "Configuring a Global TACACS+ Key" section and the "Configuring a Key for a Specific TACACS+ Server" section).
Configure the secret keys for the TACACS+ servers (see the "Configuring a Global TACACS+ Key" section and the "Configuring a Key for a Specific TACACS+ Server" section).
Step 4 ![]() If needed, configure TACACS+ server groups with subsets of the TACACS+ servers for AAA authentication methods (see the "Adding a TACACS+ Server Group" section and the "Configuring AAA" section on page 2-7).
If needed, configure TACACS+ server groups with subsets of the TACACS+ servers for AAA authentication methods (see the "Adding a TACACS+ Server Group" section and the "Configuring AAA" section on page 2-7).
Step 5 ![]() If needed, configure any of the following optional parameters:
If needed, configure any of the following optional parameters:
•![]() Dead-time interval (see the "Configuring the Dead-Time Interval" section).
Dead-time interval (see the "Configuring the Dead-Time Interval" section).
•![]() TACACS+ server specification allowed at user login (see the "Specifying a TACACS+ Server at Login" section).
TACACS+ server specification allowed at user login (see the "Specifying a TACACS+ Server at Login" section).
•![]() Timeout interval (see the "Configuring the Global TACACS+ Timeout Interval" section).
Timeout interval (see the "Configuring the Global TACACS+ Timeout Interval" section).
•![]() TCP port (see the "Configuring TCP Ports" section).
TCP port (see the "Configuring TCP Ports" section).
Step 6 ![]() If needed, configure periodic TACACS+ server monitoring (see the "Configuring Periodic TACACS+ Server Monitoring" section).
If needed, configure periodic TACACS+ server monitoring (see the "Configuring Periodic TACACS+ Server Monitoring" section).
Figure 4-2 shows the AAA Server Groups pane.
Figure 4-2 Server Groups Pane

Figure 4-3 shows the Server Details tab.
Figure 4-3 Server Details Tab

Enabling TACACS+
By default, the TACACS+ feature is disabled on the device. You must explicitly enable the TACACS+ feature to access the configuration and verification commands for authentication.
DETAILED STEPS
To enable TACACS+, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, click the device.
From the Summary pane, click the device.
Step 3 ![]() From the menu bar, choose Server Groups > Enable TACACS.
From the menu bar, choose Server Groups > Enable TACACS.
Step 4 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Adding a TACACS+ Server Host
To access a remote TACACS+ server, you must add the TACACS+ server hosts and configure the IP address or the hostname for the TACACS+ server on the device. You can add up to 64 TACACS+ servers.

Note ![]() By default, when you configure a TACACS+ server IP address or hostname the Cisco NX-OS device, the TACACS+ server is added to the default TACACS+ server group. You can also add the TACACS+ server to another TACACS+ server group. For information about creating TACACS+ server groups, see the"Adding a TACACS+ Server Group" section and the "Adding a TACACS+ Server Host to a TACACS+ Server Group" section).
By default, when you configure a TACACS+ server IP address or hostname the Cisco NX-OS device, the TACACS+ server is added to the default TACACS+ server group. You can also add the TACACS+ server to another TACACS+ server group. For information about creating TACACS+ server groups, see the"Adding a TACACS+ Server Group" section and the "Adding a TACACS+ Server Host to a TACACS+ Server Group" section).
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
Obtain the IPv4 or IPv6 addresses or the hostnames for the remote TACACS+ servers.
DETAILED STEPS
To add a TACACS+ server host, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Click Default TACACS Server Group.
Click Default TACACS Server Group.
Step 4 ![]() From the menu bar, choose Server Groups > Add Server.
From the menu bar, choose Server Groups > Add Server.
The Server Details appears in the Details pane.
Step 5 ![]() In the Server field, enter the TACACS+ server IPv4 address, IPv6 address, or hostname in the Server field.
In the Server field, enter the TACACS+ server IPv4 address, IPv6 address, or hostname in the Server field.
Step 6 ![]() From the Server drop-down list, choose either the IPv4 address, IPv6 address, or hostname as the correct server identifier type.
From the Server drop-down list, choose either the IPv4 address, IPv6 address, or hostname as the correct server identifier type.

Note ![]() If the server identifier format matches the identifier type selected, DCNM outlines the Server field in yellow to indicate that it is correct. If the server identifier format does not match the identifier type, DCNM outlines the Server field in red to indicate an error. Change the address or the address type to correct this problem.
If the server identifier format matches the identifier type selected, DCNM outlines the Server field in yellow to indicate that it is correct. If the server identifier format does not match the identifier type, DCNM outlines the Server field in red to indicate an error. Change the address or the address type to correct this problem.
Step 7 ![]() (Optional) In the Authentication Port field, enter a new TCP port number or clear it to disable authentication.
(Optional) In the Authentication Port field, enter a new TCP port number or clear it to disable authentication.
The default authentication TCP port is 49.
Step 8 ![]() (Optional) In the Test area, you can enter a username, password, and idle time interval in minutes for periodic server host monitoring.
(Optional) In the Test area, you can enter a username, password, and idle time interval in minutes for periodic server host monitoring.
The default username is test, the default password is test, and the default idle time interval is 0 minutes, which disables periodic monitoring.
Step 9 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Copying a TACACS+ Server Host
You can copy the configuration of a TACACS+ server host from one TACACS+ server group to another server group, either on the same NX-OS device or on another NX-OS device.
BEFORE YOU BEGIN
Ensure that you have configured the server in the default TACACS+ server group (see the "Adding a TACACS+ Server Host" section).
Ensure that you have created the target TACACS+ server group (see the "Adding a TACACS+ Server Group" section).
DETAILED STEPS
To copy the configuration of a TACACS+ server host, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Double-click Default TACACS Server Group.
Double-click Default TACACS Server Group.
The list of configured TACACS+ server hosts appears.
Step 4 ![]() Click on the server host you want to copy.
Click on the server host you want to copy.
Step 5 ![]() From the menu bar, choose Actions > Copy.
From the menu bar, choose Actions > Copy.
Step 6 ![]() Click the destination server group.
Click the destination server group.

Note ![]() You can copy the server host configuration to a server group within the same device or in another device.
You can copy the server host configuration to a server group within the same device or in another device.
Step 7 ![]() From the menu bar, choose Actions > Paste.
From the menu bar, choose Actions > Paste.
The TACACS+ server host appears in the list of servers for the server group.
Step 8 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Deleting a TACACS+ Server Host
You can delete a TACACS+ server host from a server group.
DETAILED STEPS
To delete a TACACS+ server host, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Double-click the server group to display the list of server hosts.
Double-click the server group to display the list of server hosts.
Step 4 ![]() Click the TACACS+ server host to delete.
Click the TACACS+ server host to delete.
Step 5 ![]() From the menu bar, choose Server Groups > Delete Server and click Yes on the confirmation dialog.
From the menu bar, choose Server Groups > Delete Server and click Yes on the confirmation dialog.
The TACACS+ server host disappears from the list.
Step 6 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Configuring a Global TACACS+ Key
You can configure secret keys at the global level for all servers used by the device. A secret key is a shared secret text string between the device and the TACACS+ server hosts.
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
Obtain the secret key values for the remote TACACS+ servers.
DETAILED STEPS
To configure a global secret key, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Click Default TACACS Server Group.
Click Default TACACS Server Group.
Step 4 ![]() From the Details pane, click the Global TACACS Settings tab.
From the Details pane, click the Global TACACS Settings tab.
Step 5 ![]() In the Key field, enter the secret key.
In the Key field, enter the secret key.
Step 6 ![]() (Optional) Check Encrypt to encrypt the key.
(Optional) Check Encrypt to encrypt the key.
The default is clear text. The Cisco NX-OS software encrypts a clear text key before saving it to the running configuration.
Step 7 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Configuring a Key for a Specific TACACS+ Server
You can configure secret keys for a TACACS+ server. A secret key is a shared secret text string between the Cisco NX-OS device and the TACACS+ server host.
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
Configure one or more TACACS+ server hosts (see the "Adding a TACACS+ Server Host" section).
Obtain the secret key values for the remote TACACS+ servers.
DETAILED STEPS
To configure a TACACS+ server secret key, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Step 4 ![]() Click the desired TACACS+ server.
Click the desired TACACS+ server.
Step 5 ![]() From the Details pane, click the Server Details tab.
From the Details pane, click the Server Details tab.
Step 6 ![]() Check Override Defaults.
Check Override Defaults.
Step 7 ![]() In the Key field, enter the secret key.
In the Key field, enter the secret key.
The default is the global secret key.
Step 8 ![]() (Optional) Check Encrypt to encrypt the key.
(Optional) Check Encrypt to encrypt the key.
The default is clear text.
Step 9 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Adding a TACACS+ Server Group
You can reference one or more remote AAA servers to authenticate users using server groups. All members of a group must belong to the TACACS+ protocol. The servers are tried in the same order in which you configure them.
You can configure these server groups at any time but they only take effect when you apply them to an AAA service. For information on AAA services, see the "Remote AAA Services" section on page 2-2.
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
Configure one or more TACACS+ server hosts (see the "Adding a TACACS+ Server Host" section).
DETAILED STEPS
To add a TACACS+ server group, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, click the device.
From the Summary pane, click the device.
Step 3 ![]() From the menu bar, choose Server Groups > TACACS Server Group.
From the menu bar, choose Server Groups > TACACS Server Group.
A new line appears at the end of the server group list for the device and the Details tab appears in the Details pane.
Step 4 ![]() In the Server Group Name field, enter the name and press the Enter key.
In the Server Group Name field, enter the name and press the Enter key.
The server group name is a case-sensitive alphanumeric string with a maximum length of 127 characters.
Step 5 ![]() (Optional) In the Dead time(mins) field, enter the number of minutes for the dead-time interval.
(Optional) In the Dead time(mins) field, enter the number of minutes for the dead-time interval.
The default dead-time interval is 0 minutes.
Step 6 ![]() In the VRF Name field, click the down arrow to display the VRF Name dialog and click a VRF. Click OK.
In the VRF Name field, click the down arrow to display the VRF Name dialog and click a VRF. Click OK.
Step 7 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Adding a TACACS+ Server Host to a TACACS+ Server Group
You can add a TACACS+ server host to a TACACS+ server group.
BEFORE YOU BEGIN
Ensure that you have added the TACACS+ server host to the Default TACACS+ Server Group (see the "Adding a TACACS+ Server Host" section).
DETAILED STEPS
To add a TACACS+ server host to a TACACS+ server group, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Click a TACACS+ server group.
Click a TACACS+ server group.
Step 4 ![]() From the menu bar, choose Server Groups > Add Server.
From the menu bar, choose Server Groups > Add Server.
The Server Details appear in the Details pane.
Step 5 ![]() In the Server field, enter the TACACS+ server IPv4 address, IPv6 address, or hostname in the Server field.
In the Server field, enter the TACACS+ server IPv4 address, IPv6 address, or hostname in the Server field.
Step 6 ![]() From the Server drop-down list, choose either the IPv4 address, IPv6 address, or hostname as the correct server identifier type.
From the Server drop-down list, choose either the IPv4 address, IPv6 address, or hostname as the correct server identifier type.

Note ![]() If the server identifier format matches the identifier type selected, DCNM outlines the Server field in yellow to indicate that it is correct. If the server identifier format does not match the identifier type, DCNM outlines the Server field in red to indicate an error. Change the address or the address type to correct this problem.
If the server identifier format matches the identifier type selected, DCNM outlines the Server field in yellow to indicate that it is correct. If the server identifier format does not match the identifier type, DCNM outlines the Server field in red to indicate an error. Change the address or the address type to correct this problem.
Step 7 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Deleting a TACACS+ Server Host from a TACACS+ Server Group
You can delete a TACACS+ server host from a TACACS+ server group.
DETAILED STEPS
To delete a TACACS+ server host from a TACACS+ server group, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Double-click the server group to display the list of server hosts.
Double-click the server group to display the list of server hosts.
Step 4 ![]() Click the TACACS+ server host to delete.
Click the TACACS+ server host to delete.
Step 5 ![]() From the menu bar, choose Server Groups > Delete Server and click Yes on the confirmation dialog.
From the menu bar, choose Server Groups > Delete Server and click Yes on the confirmation dialog.
The TACACS+ server host disappears from the list.
Step 6 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Deleting a TACACS+ Server Group
You can delete a TACACS+ server group.
DETAILED STEPS
To delete a TACACS+ server group, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the list of server groups.
From the Summary pane, double-click the device to display the list of server groups.
Step 3 ![]() Click the TACACS+ server group to delete.
Click the TACACS+ server group to delete.
Step 4 ![]() From the menu bar, choose Server Groups > Delete Server Group and click Yes in the confirmation dialog.
From the menu bar, choose Server Groups > Delete Server Group and click Yes in the confirmation dialog.
The server group disappears from the server group list.
Step 5 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Specifying a TACACS+ Server at Login
You can configure the switch to allow the user to specify which TACACS+ server to send the authentication request by enabling the directed-request option. By default, a device forwards an authentication request based on the default AAA authentication method. If you enable this option, the user can log in as username@vrfname:hostname, where vrfname is the VRF to use and hostname is the name of a configured TACACS+ server.

Note ![]() If you enable the directed-request option, the device uses only the TACACS+ method for authentication and not the default local method.
If you enable the directed-request option, the device uses only the TACACS+ method for authentication and not the default local method.

Note ![]() User-specified logins are supported only for Telnet sessions.
User-specified logins are supported only for Telnet sessions.
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
DETAILED STEPS
To allow users to specify a TACACS+ server at login, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Click Default TACACS Server Group.
Click Default TACACS Server Group.
Step 4 ![]() From the Details pane, click the Global TACACS Settings tab.
From the Details pane, click the Global TACACS Settings tab.
Step 5 ![]() Check Direct Req.
Check Direct Req.
Step 6 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Configuring the Global TACACS+ Timeout Interval
You can set a global timeout interval that the device waits for responses from all TACACS+ servers before declaring a timeout failure. The timeout interval determines how long the device waits for responses from TACACS+ servers before declaring a timeout failure.
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
DETAILED STEPS
To configure the global TACACS+ timeout interval, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Click Default TACACS Server Group.
Click Default TACACS Server Group.
Step 4 ![]() From the Details pane, click the Global TACACS Settings tab.
From the Details pane, click the Global TACACS Settings tab.
Step 5 ![]() In the Time out(secs) field, enter the number of seconds for the timeout interval.
In the Time out(secs) field, enter the number of seconds for the timeout interval.
The default is 5 seconds.
Step 6 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Configuring the Timeout Interval for a Server
You can set a timeout interval that the device waits for responses from a TACACS+ server before declaring a timeout failure. The timeout interval determines how long the device waits for responses from a TACACS+ server before declaring a timeout failure.
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
Configure one or more TACACS+ server hosts (see the "Adding a TACACS+ Server Host" section).
DETAILED STEPS
To configure the timeout interval for a TACACS+ server, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Step 4 ![]() Click the desired TACACS+ server.
Click the desired TACACS+ server.
Step 5 ![]() From the Details pane, click the Server Details tab.
From the Details pane, click the Server Details tab.
Step 6 ![]() Check Override Defaults.
Check Override Defaults.
Step 7 ![]() In the Timeout(secs) field, enter the number of seconds for the timeout interval.
In the Timeout(secs) field, enter the number of seconds for the timeout interval.
The default is 5 seconds.
Step 8 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Configuring TCP Ports
You can configure another TCP port for the TACACS+ servers if there are conflicts with another application. By default, devices use port 49 for all TACACS+ requests.
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
Configure one or more TACACS+ server hosts (see the "Adding a TACACS+ Server Host" section).
DETAILED STEPS
To configure the authentication port for TACACS+ servers, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Step 4 ![]() Click the desired TACACS+ server.
Click the desired TACACS+ server.
Step 5 ![]() From the Details pane, click the Server Details tab.
From the Details pane, click the Server Details tab.
Step 6 ![]() In the Authentication Port field, enter a new TCP port number or clear it to disable authentication.
In the Authentication Port field, enter a new TCP port number or clear it to disable authentication.
The default authentication TCP port is 49.
Step 7 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Configuring Periodic TACACS+ Server Monitoring
You can monitor the availability of TACACS+ servers. These parameters include the username and password to use for the server and an idle timer. The idle timer specifies the interval in which a TACACS+ server receives no requests before the device sends out a test packet. You can configure this option to test servers periodically, or you can run a one-time only test.

Note ![]() To protect network security, we recommend that you use a username that is not the same as an existing username in the TACACS+ database.
To protect network security, we recommend that you use a username that is not the same as an existing username in the TACACS+ database.
The test idle timer specifies the interval in which a TACACS+ server receives no requests before the device sends out a test packet.

Note ![]() The default idle timer value is 0 minutes. When the idle time interval is 0 minutes, periodic TACACS+ server monitoring is not performed.
The default idle timer value is 0 minutes. When the idle time interval is 0 minutes, periodic TACACS+ server monitoring is not performed.
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
Configure one or more TACACS+ server hosts (see the "Adding a TACACS+ Server Host" section).
DETAILED STEPS
To configure periodic TACACS+ server monitoring, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Step 4 ![]() Click the desired TACACS+ server.
Click the desired TACACS+ server.
Step 5 ![]() From the Details pane, click the Server Details tab.
From the Details pane, click the Server Details tab.
Step 6 ![]() In the User Name field, enter a username.
In the User Name field, enter a username.
Step 7 ![]() In the Password field, enter a password.
In the Password field, enter a password.
Step 8 ![]() In the Idle Time field, enter the number of minutes for periodic monitoring.
In the Idle Time field, enter the number of minutes for periodic monitoring.
Step 9 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Configuring the Dead-Time Interval
You can configure the dead-time interval for all TACACS+ servers. The dead-time interval specifies the time that the device waits, after declaring a TACACS+ server is dead, before sending out a test packet to determine if the server is now alive.

Note ![]() When the dead-timer interval is 0 minutes, TACACS+ servers are not marked as dead even if they are not responding. You can configure the dead-timer per group (see the "Adding a TACACS+ Server Group" section).
When the dead-timer interval is 0 minutes, TACACS+ servers are not marked as dead even if they are not responding. You can configure the dead-timer per group (see the "Adding a TACACS+ Server Group" section).
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
DETAILED STEPS
To configure the dead-time interval, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Click Default TACACS Server Group.
Click Default TACACS Server Group.
Step 4 ![]() From the Details pane, click the Global TACACS Settings tab.
From the Details pane, click the Global TACACS Settings tab.
Step 5 ![]() In the Dead time(mins) field, enter the number of minutes.
In the Dead time(mins) field, enter the number of minutes.
The default is 0 minutes.
Step 6 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Disabling TACACS+
You can disable TACACS+.

DETAILED STEPS
To disable TACACS+, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, click the device.
From the Summary pane, click the device.
Step 3 ![]() From the menu bar, choose Server Groups > Disable TACACS.
From the menu bar, choose Server Groups > Disable TACACS.
Step 4 ![]() From the menu bar, choose File > Deploy to apply your changes to the device.
From the menu bar, choose File > Deploy to apply your changes to the device.
Displaying TACACS+ Statistics
You can display the statistics that the device maintains for TACACS+ activity.
BEFORE YOU BEGIN
Enable TACACS+ (see the "Enabling TACACS+" section).
Configure one or more TACACS+ server hosts (see the "Adding a TACACS+ Server Host" section).
DETAILED STEPS
To display TACACS+ server statistics, follow these steps:
Step 1 ![]() From the Feature Selector pane, choose Security > AAA > Server Groups.
From the Feature Selector pane, choose Security > AAA > Server Groups.
Step 2 ![]() From the Summary pane, double-click the device to display the server groups.
From the Summary pane, double-click the device to display the server groups.
Step 3 ![]() Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Double-click Default TACACS Server Group to display the list of TACACS+ servers.
Step 4 ![]() Click the desired TACACS+ server.
Click the desired TACACS+ server.
Step 5 ![]() From the Details pane, click the Statistics tab.
From the Details pane, click the Statistics tab.
Where to Go Next
You can now configure AAA authentication methods to include the TACACS+ server groups (see Chapter 2, "Configuring AAA").
Field Descriptions for TACACS+ Server Groups and Servers
This section includes the following topics:
•![]() Security: AAA: Server Groups: Summary Pane
Security: AAA: Server Groups: Summary Pane
•![]() Security: AAA: Server Groups: device: Default TACACS Server Group: Global TACACS Settings Tab
Security: AAA: Server Groups: device: Default TACACS Server Group: Global TACACS Settings Tab
•![]() Security: AAA: Server Groups: device: Default TACACS Server Group: server: Server Details Tab
Security: AAA: Server Groups: device: Default TACACS Server Group: server: Server Details Tab
•![]() Security: AAA: Server Groups: device: server group: Details Tab
Security: AAA: Server Groups: device: server group: Details Tab
Security: AAA: Server Groups: Summary Pane
Security: AAA: Server Groups: device: Default TACACS Server Group: Global TACACS Settings Tab
Security: AAA: Server Groups: device: Default TACACS Server Group: server: Server Details Tab
Security: AAA: Server Groups: device: server group: Details Tab
Additional References
For additional information related to implementing TACACS+, see the following sections:
•![]() MIBs
MIBs
Related Documents
|
|
|
|---|---|
NX-OS Licensing |
|
DCNM Licensing |
Cisco DCNM Fundamentals Configuration Guide, Release 4.1 |
VRF configuration |
Cisco DCNM Unicast Routing Configuration Guide, Release 4.1 |
Standards
|
|
|
|---|---|
No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature. |
— |
MIBs
|
|
|
|---|---|
• • |
To locate and download MIBs, go to the following URL: http://www.cisco.com/public/sw-center/enigmatic/cant/mibs.shtml |
Feature History for TACACS+
Table 4-5 lists the release history for this feature.
 Feedback
Feedback