Cisco TrustSec has
the following guidelines and limitations:
-
Traffic generated from any supervisor is tagged with device-SGT provided that a non-zero value is configured or downloaded
and SGT propagation is enabled on the egress interface. However, even if the SGACL enforcement is enabled on the corresponding
VRF or VLAN, this traffic would not be subject to SGACL enforcement, if the destination for this traffic is the next hop device.
-
Cisco TrustSec stops tagging traffic when Netflow is configured on the same interface which is used for tagging. Do not configure
Netflow on the same interface if the matrix does not specify that the Netflow is supported with SGT. The workaround for this
issue is to remove Netflow from the interface which is used for tagging and use a different interface to send the Netflow
(with no relation to the Cisco TrustSec).
-
The Cisco Nexus 7000 series switch does not support multiple SGACLs for the same source and destination pair. It is recommended
that the multi line single SGACL is used.
-
Cisco TrustSec MACSec—The following set of requirements must be used when deploying MACSec over SP-provided pseudowire connections.
These requirements help to ensure the right service, quality, or characteristics are ordered from the SP.
The Cisco Nexus 7000 series switch supports MACSec over Point-to-Point links, including those using DWDM, as well as non-PtP
links such as EoMPLS where the following conditions are met:
-
There is no re-ordering or buffering of packets on the MACSec link.
-
No additional frames can be injected to the MACSec link.
-
There must be end-to-end link event notification—if the edge device or any intermediate device loses a link then there must
be notifications sent so that the user is aware of the link failure as the service will be interrupted.
-
For MACsec links that have a bandwidth that is greater than or equal to 40G, multiple security associations (SCI/AN pairs)
are established with each SA protocol exchange.
-
Cisco TrustSec
SGT supports IPv4 addressing only.
-
Cisco TrustSec
SGT in-line tagging is not supported over OTV, VXLAN, FCoE, or Programmable
Fabric.
-
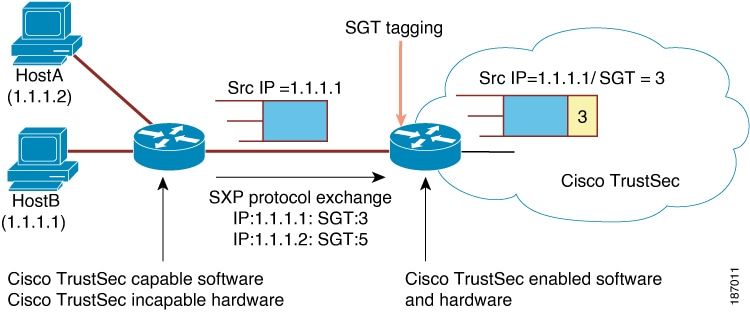
SXP cannot use
the management (mgmt 0) interface.
-
You cannot
enable Cisco TrustSec on interfaces in half-duplex mode.
-
If SGACL is
applied to the packets being routed through SVI, SGACL has to be enabled on all
the VLANs and the VRF instance involved.
-
You cannot
configure both Cisco TrustSec and 802.1X on an interface; you can configure
only one or the other. However, you must enable the 802.1X feature for Cisco
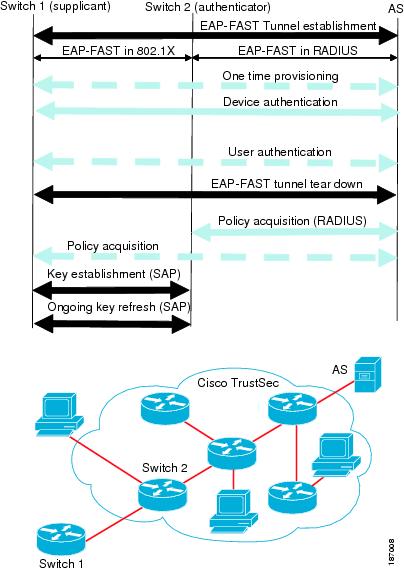
TrustSec to use EAP-FAST authentication.
-
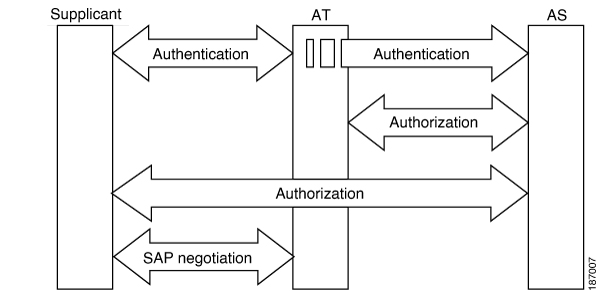
AAA authentication and authorization for Cisco TrustSec is only supported by the Cisco Secure ACS and Cisco ISE.
-
To download sgname tables or refresh the environment data, you must use the Cisco ISE Release 1.0 or a later release. The
Cisco Secure ACS does not support these features.
-
Cisco TrustSec supports 200,000 IP-SGT maps. This is subject to the FIB TCAM space availability on each of the modules. Note
that the CLI rollback is not supported when more than 100,000 IP-SGT mappings are manually configured. For more information,
see Cisco Nexus 7000 Series NX-OS Verified Scalability Guide.
-
The CISCO-TRUSTSEC-SXP-MIB does not provide an instance number. The object ctsxSxpConnInstance does not provide the instance number of the Cisco TrustSec SXP connection. Currently this number is not maintained and cannot
be displayed.
-
Reloading with Cisco TrustSec configuration on the Non-default VDC triggers a syslog message. When the Cisco TrustSec enforcement
is enabled on the VLANs, and if a VDC reload occurs, Cisco TrustSec attempts twice to disable the enforcement on the VLANs.
On the second attempt, the following syslog message appears:
CTS-2-RBACL_ENFORCEMENT_FAILED:Failed to disable RBACL enf on vdc reload
This syslog message can be ignored for the VDC reload because the VLANs are deleted on reload and Cisco TrustSec also deletes
the enforcement configurations for those VLANs.
-
The Cisco TrustSec configuration commands are not available. The no cts dev-id pswd dev-pswd command is currently not supported in NX-OS software. When the cts dev-id pass command is configured, the command configuration can be replaced using the same command, but it cannot be deleted.
-
When you change the Cisco TrustSec MACSec port mode from Cache Engine (CE) mode to FabricPath mode, CRC errors are displayed
in the Cisco TrustSec MACsec link until native VLAN tagging is disabled on the FabricPath core port. Such configuration changes
that occur on a Cisco TrustSec port should be flapped. However, this could cause possible traffic disruptions. In such circumstances,
to avoid the display of CRC errors and traffic disruptions, perform the following steps:
-
Disable the cache engine port while having the Cisco TrustSec MACsec enabled.
-
Change the
port mode to FabricPath mode.
-
Disable the
native VLAN tagging on the FabricPath core port.
-
Enable the
port.
-
The
subnet-to-SGT bindings are not expanded by default. To enable expansion, the
cts sxp
mapping network-mapcommand must be set to a non-zero value.
-
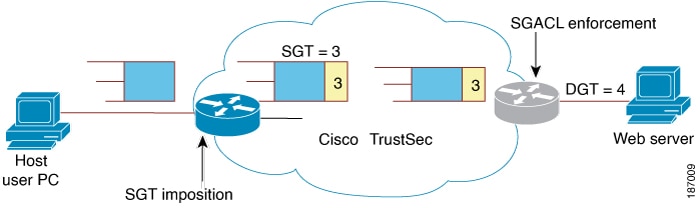
An SGT that is
associated with a longer prefix is always selected even if a corresponding SGT
binding exists. For example, consider the hosts 12.1.0.0/16 with the subnet-SGT
binding 10 and 12.1.1.1 with IP-SGT binding 20. SGT 20 is selected for the host
12.1.1.1 even though the parent prefix SGT is 10. Similarly, if VLAN 121 is
designated to the subnet 12.1.0.0/16 and configured with a VLAN-SGT binding of
30, host 12.1.1.1 will continue to have the SGT value of 20 and the host
12.1.1.2 will have an SGT value of 10, because the subnet-SGT binding is
considered a longer match than a VLAN-SGT mapping.
-
To enable the
monitoring mode, enable the
cts role-based
detailed-logging command. You can enable or disable logging at the ACE
level, as being done currently.
-
Monitoring at a
per-RBACL or per-ACE level is not supported.
-
The monitor mode
counter statistics and logging output might not match because the logging
output count is rate limited, while counter statistics are directly obtained
from the hardware.
-
When you enable
monitor
all by using CLI, ISE, or both, the monitoring for all SGT-DGT pairs is
turned on, independent of per-pair configuration.
-
When you disable
the monitor mode feature, the switch reverts to the default behavior. The
monitored SGACLs from ISE will not be installed. All the CLI-installed SGACLS
will begin to enforce or deny the policies as configured.
-
The traffic
hitting SGACL Access Control Entry (ACE) with the log option set is punted to
the supervisor, causing network congestion in the supervisor and the packets
originated from supervisor such as ping, OSPF hello, and SXP may fail leading
to control plane disruption. Therefore, we recommend that you enable log option
only for troubleshooting or validation purposes.
-
The following
guidelines and limitations are applicable for the SGACL Egress Policy Overwrite
feature:
-
If overlapping RBACL exists from both the sources (CLI and ISE) for an sgt-dgt pair, the respective RBACL is programmed in
to the hardware based on the configured priority. The RBACL is programmed as conventional or monitored based on the monitor
mode property.
-
If RBACL
exists only from a single source, irrespective of configured priority, the
RBACL is programmed as conventional or monitored based on the monitor mode
property.
-
Irrespective of the configured priority, RBACL always get
updated into the PSS. However, hardware programming is based on the priority
and monitor mode property.
-
SGACLs are
monitored when you enable monitor mode globally and set monitor all. However,
based on the install priority set by using the
cts role-based priority-static command, either the
SGACLs downloaded from ISE or the SGACLs configured by using CLI are monitored.
-
When SGACL
exists only from a single source, that is, either from ISE or CLI, the existing
SGACL is used irrespective of the configured install priority of SGACLs.
-
When you
set
monitor
all by using CLI, ISE, or both, the monitoring for all SGT-DGT pairs is
turned on, independent of per-pair configuration.
-
Based on the set priority, the monitoring is enabled for the SGACL configured by using CLI or SGACL downloaded from ISE.
-
When you
disable the monitor mode feature, the switch reverts to the default behavior.
The monitored SGACLs from ISE will not be installed. All the CLI-installed
SGACLS will begin to enforce or deny the policies as configured.
-
The following
guidelines and limitations are applicable for the SGACL Egress Policy Overwrite
feature:
-
Irrespective of whether SGT and DGT are known or unknown for a
given network traffic, or an SGACL policy exists for a given SGT and DGT, SGACL
policy enforcement disablement on an interface does bypass all SGACLs.
-
Per
Interface SGACL Bypass feature is configured on an L3 physical interface as
well as an L3 port-channel. However, port-channel member ports cannot be
configured for this feature.
-
SGACL
policy enforcement feature is removed from an interface when the IP address is
removed.
-
When an
L3 interface is converted to an L2 interface, the IP configuration is erased.
Thereby, the SGACL policy enforcement feature is also erased for the L2
interface.
-
When you
change a VRF, all L3 configurations are erased on an L3 interface. Thereby, the
SGACL policy enforcement feature is also erased for the L3 interface.
-
When you enable or disable the Cisco TrustSec SGT Caching feature, by default, Cisco TrustSec reprograms all the RBACLs to
add or remove the log option for all the ACEs. Due to this reprogramming, the previously known statistics are deleted for
a RBACL and they are not displayed in the show cts role-based counters command output.






 Feedback
Feedback