- Preface
- Product Overview
- Command-line Interfaces
- Configuring the Switch for the First Time
- Administering the Switch
- Configuring the Cisco IOS In Service Software Upgrade Process
- Configuring Interfaces
- Checking Port Status and Connectivity
- Configuring Supervisor Engine Redundancy Using RPR and SSO
- Configuring Cisco NSF with SSO Supervisor Engine Redundancy
- Environmental Monitoring and Power Management
- Configuring Power over Ethernet
- Configuring Energy Wise
- Configuring the Catalyst 4500 Series Switch with Cisco Network Assistant
- Configuring VLANs, VTP, and VMPS
- Configuring IP Unnumbered Interface
- Configuring Layer 2 Ethernet Interfaces
- Configuring SmartPort Macros
- Configuring STP and MST
- Configuring Flex Links and the MAC Address-Table Move Update Feature
- Configuring Resilient Ethernet Protocol
- Configuring Optional STP Features
- Configuring EtherChannels
- Configuring IGMP Snooping and Filtering
- Configuring IPv6 MLD Snooping
- Configuring 802.1Q and Layer 2 Protocol Tunneling
- Configuring CDP
- Configuring LLDP and LLDP-MED
- Configuring UDLD
- Configuring Unidirectional Ethernet
- Configuring Layer 3 Interfaces
- Configuring Cisco Express Forwarding
- Configuring Unicast Reverse Path Forwarding
- Configuring IP Multicast
- Configuring ANCP Client
- Configuring Policy-Based Routing
- Configuring VRF-lite
- Configuring Quality of Service
- Configuring Voice Interfaces
- Configuring Private VLANs
- Configuring 802.1X Port-Based Authentication
- Configuring the PPPoE Intermediate Agent
- Configuring Web-Based Authentication
- Configuring Port Security
- Configuring Control Plane Policing
- Configuring DHCP Snooping, IP Source Guard, and IPSG for Static Hosts
- Configuring Dynamic ARP Inspection
- Configuring Network Security with ACLs
- Port Unicast and Multicast Flood Blocking
- Configuring Storm Control
- Configuring SPAN and RSPAN
- Configuring System Message Logging
- Configuring OBFL
- Configuring SNMP
- Configuring NetFlow
- Configuring Ethernet CFM and OAM
- Configuring Y.1731 (AIS and RDI)
- Configuring Call Home
- Configuring Cisco IOS IP SLAs Operations
- Configuring RMON
- Performing Diagnostics
- Configuring WCCP Version 2 Services
- ROM Monitor
- Configuring MIB Support
- Index
- Acronyms
- Command List
- Ethernet CFM Overview
- Configuring Ethernet CFM
- Displaying Ethernet CFM Information
- Ethernet OAM Protocol Overview
- Setting Up and Configuring Ethernet OAM
- Displaying Ethernet OAM Protocol Information
- Ethernet CFM and Ethernet OAM Interaction
Configuring Ethernet CFM and OAM
Ethernet Operations, Administration, and Maintenance (OAM) is a protocol for installing, monitoring, and troubleshooting Ethernet networks to enhance management within the Ethernet infrastructure. The Catalyst 4500 series switch supports IEEE 802.1ag Connectivity Fault Management (CFM) and IEEE 802.3ah Ethernet OAM discovery, link monitoring, remote fault detection, and remote loopback. The Ethernet OAM manager controls the interaction between CFM and OAM.

Note ![]() For complete command and configuration information for CFM, see the Cisco IOS feature module at this URL:
For complete command and configuration information for CFM, see the Cisco IOS feature module at this URL:
http://www.cisco.com/en/US/docs/ios/cether/configuration/guide/ce_cfm.html
This chapter contains these sections:
•![]() Displaying Ethernet CFM Information
Displaying Ethernet CFM Information
•![]() Ethernet OAM Protocol Overview
Ethernet OAM Protocol Overview
•![]() Setting Up and Configuring Ethernet OAM
Setting Up and Configuring Ethernet OAM
•![]() Displaying Ethernet OAM Protocol Information
Displaying Ethernet OAM Protocol Information
•![]() Ethernet CFM and Ethernet OAM Interaction
Ethernet CFM and Ethernet OAM Interaction
Command List
This table lists the commands most commonly used with Ethernet CFM and OAM.
Ethernet CFM Overview
Ethernet CFM is an end-to-end per-service-instance (per VLAN) Ethernet layer OAM protocol. It includes proactive connectivity monitoring, fault verification, and fault isolation. End-to-end can be provider-edge-to provider-edge (PE-to-PE) device or customer-edge-to-customer-edge (CE-to-CE) device. Ethernet CFM, as specified by IEEE 802.1ag, is the standard for Layer 2 ping, Layer 2 traceroute, and end-to-end connectivity verification of the Ethernet network.
Unlike CFM, other metro-Ethernet OAM protocols are not end-to-end technologies. For example, IEEE 802.3ah OAM is a single-hop and per-physical-wire protocol and is not end-to-end or service aware.
These sections contain conceptual information about Ethernet CFM:
•![]() General Packet Forwarding Rules
General Packet Forwarding Rules
Definition List
CFM Domain
A CFM maintenance domain is a management space on a network that is owned and operated by a single entity and defined by a set of internal boundary ports. You assign a unique maintenance level (from 0 to 7) to define the domain hierarchy. The larger the domain, the higher the level. For example, as shown in Figure 55-1, a service-provider domain would be larger than an operator domain and might have a maintenance level of 6, while the operator domain maintenance level would be 3 or 4.
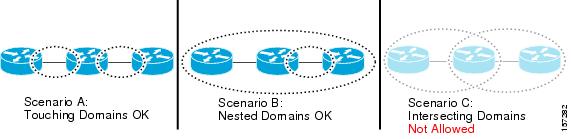
As shown in Figure 55-2, domains cannot intersect or overlap because that would require management by more than one entity, which is not allowed. Domains can touch or nest (if the outer domain has a higher maintenance level than the nested domain). Nesting domains can be useful when a service provider contracts with one or more operators to provide Ethernet service. Each operator has its own maintenance domain and the service provider domain is a superset of the operator domains. Maintenance levels of nesting domains should be communicated among the administrating organizations. CFM exchanges messages and performs operations on domains individually.
Figure 55-1 CFM Maintenance Domains

Figure 55-2 Allowed Domain Relationships
CFM Maintenance Points
Operating with a maintenance domain, a maintenance point demarcates an interface that participates in an CFM. Maintenance points drop all lower-level frames and forward all higher-level frames. There are two types of maintenance points:
•![]() Maintenance end points (MEPs) are points at the edge of the domain that define the boundary and confine CFM messages within the boundary. MEPs are inward facing by default. Inward facing means that they communicate through the relay function side, not the wire side (connected to the port), whereas MEPs that can be configured as outward facing communicate through the wire side, and not through the relay function side.
Maintenance end points (MEPs) are points at the edge of the domain that define the boundary and confine CFM messages within the boundary. MEPs are inward facing by default. Inward facing means that they communicate through the relay function side, not the wire side (connected to the port), whereas MEPs that can be configured as outward facing communicate through the wire side, and not through the relay function side.
An inward-facing MEP sends and receives CFM frames through the relay function. It drops all CFM frames at its level or lower that come from the wire side. For CFM frames from the relay side, it processes the frames at its level and drops frames at a lower level. The MEP transparently forwards all CFM frames at a higher level, whether they are received from the relay or wire side. CFM runs at the provider maintenance level (UPE-to-UPE), specifically with inward-facing MEPs at the user network interface (UNI).
An outward facing MEP (OFM) sends and receives CFM frames on the wire side. It drops all CFM frames at its level or lower that come from the relay function side. For CFM frames from the wire side, it processes the frames at its level and drops frames at a lower level. OFM transparently forwards all CFM frames at a higher level, whether they are received from the relay or wire side.
•![]() Maintenance intermediate points (MIPs) are inside a domain, not at the boundary, and respond to CFM only when triggered by traceroute and loopback messages. They forward CFM frames received from MEPs and other MIPs, drop all CFM frames at a lower level, and forward all CFM frames at a higher level, whether they are received from the relay or wire side.
Maintenance intermediate points (MIPs) are inside a domain, not at the boundary, and respond to CFM only when triggered by traceroute and loopback messages. They forward CFM frames received from MEPs and other MIPs, drop all CFM frames at a lower level, and forward all CFM frames at a higher level, whether they are received from the relay or wire side.
If a port on which the inward facing MEP is configured is blocked by Spanning-Tree Protocol (STP), the MEP cannot receive or transmit CFM messages. If a port on which the outward facing MEP is configured is blocked by STP, the OFM can only receive CFM messages from and transmit them towards the wire. If a port on which a MIP is configured is blocked by STP, the port cannot receive or respond to messages from the relay function side, but can receive CFM messages and respond to them from the wire side.
General Packet Forwarding Rules
Ethernet CFM frames should be forwarded or dropped based on the strict rules of hierarchical maintenance domains. MEPs and MIPs configured on bridge ports act as filters that confine CFM frames within the bounds of the correct domain(s) by dropping frames that do not belong to the correct Level.
Topics include:
Inward-Facing MEPs
An inward-facing MEP does the following:
•![]() Sends and receives CFM frames at its level through the relay function, not through the wire connected to the port on which the MEP is configured.
Sends and receives CFM frames at its level through the relay function, not through the wire connected to the port on which the MEP is configured.
•![]() Drops all CFM frames at its level (or lower level) that come from the wire side.
Drops all CFM frames at its level (or lower level) that come from the wire side.
•![]() Processes all CFM frames at its level that come from the direction of the relay function.
Processes all CFM frames at its level that come from the direction of the relay function.
A packet arriving on a wire at a port is coming from the wire side.
A packet arriving internally from the CPU or by the bridging action in hardware (or software) is coming from the relay function side.
•![]() Drops all CFM frames at a lower level that come from the direction of the relay function.
Drops all CFM frames at a lower level that come from the direction of the relay function.
•![]() Transparently forwards all CFM frames at a higher level, whether they come from the relay function or the wire side.
Transparently forwards all CFM frames at a higher level, whether they come from the relay function or the wire side.

Note ![]() A MEP of level L (where L != 7) requires a MIP of level M > L on the same port. So, CFM frames at a higher level than the MEP are cataloged by this MIP.
A MEP of level L (where L != 7) requires a MIP of level M > L on the same port. So, CFM frames at a higher level than the MEP are cataloged by this MIP.
•![]() If the port on which the MEP is configured is blocked by STP, the MEP can no longer transmit or receive CFM messages.
If the port on which the MEP is configured is blocked by STP, the MEP can no longer transmit or receive CFM messages.

Note ![]() On Catalyst 4500 Supervisor Engine 6-ME, outward MEPs are only supported on the supervisor uplink ports.
On Catalyst 4500 Supervisor Engine 6-ME, outward MEPs are only supported on the supervisor uplink ports.
Outward-Facing MEPs
An outward-facing MEP does the following:
•![]() Sends and receives CFM frames at its level through the wire connected to the port through which the MEP is configured.
Sends and receives CFM frames at its level through the wire connected to the port through which the MEP is configured.
•![]() Drops all CFM frames at its level (or lower level) that come from the relay function side.
Drops all CFM frames at its level (or lower level) that come from the relay function side.
•![]() Processes all CFM frames at its level coming from the direction of the wire.
Processes all CFM frames at its level coming from the direction of the wire.
•![]() Drops all CFM frames at a lower level coming from the direction of the wire.
Drops all CFM frames at a lower level coming from the direction of the wire.
•![]() Transparently forwards all CFM frames at a higher level, whether they come in from the relay function side or the wire side.
Transparently forwards all CFM frames at a higher level, whether they come in from the relay function side or the wire side.
A MEP of level L (where L != 7) requires a MIP of level M > L on the same port. So, CFM frames at a higher level than the MEP are catalogued by this MIP.
•![]() If the port on which the MEP is configured is blocked by STP, the MEP can still transmit and receive CFM messages through the wire.
If the port on which the MEP is configured is blocked by STP, the MEP can still transmit and receive CFM messages through the wire.
•![]() A MIP catalogues and forwards CFM frames at its level both through the wire and through the relay function.
A MIP catalogues and forwards CFM frames at its level both through the wire and through the relay function.
•![]() A MIP stops and drops all CFM frames at a lower level whether they come from the wire or relay function side.
A MIP stops and drops all CFM frames at a lower level whether they come from the wire or relay function side.
•![]() A MIP transparently forwards CFM frames at a higher level whether they come from the wire or relay function side.
A MIP transparently forwards CFM frames at a higher level whether they come from the wire or relay function side.
•![]() If the port on which the MIP is configured is blocked by STP, the MIP cab no longer receive or relay CFM messages towards the relay function side; however, it can still receive and respond to CFM messages from the wire.
If the port on which the MIP is configured is blocked by STP, the MIP cab no longer receive or relay CFM messages towards the relay function side; however, it can still receive and respond to CFM messages from the wire.
Transparent Ports
A transparent port has neither a MEP nor MIP configured, and forwards CFM frames like regular data traffic.
STP blocking applies to CFM frames on transparent ports just as it applies to ports with inward-facing MEPs; if the port is blocked by STP, CFM frames are dropped as they attempt to ingress or egress that port.
CFM Messages
CFM uses standard Ethernet frames distinguished by EtherType or (for multicast messages) by MAC address. All CFM messages are confined to a maintenance domain and to a service-provider VLAN (S-VLAN). Four CFM messages are supported:
•![]() Continuity Check (CC) messages—multicast heartbeat messages exchanged periodically between MEPs that allow MEPs to discover other MEPs within a domain and allow MIPs to discover MEPs. CC messages are confined to a domain or VLAN.
Continuity Check (CC) messages—multicast heartbeat messages exchanged periodically between MEPs that allow MEPs to discover other MEPs within a domain and allow MIPs to discover MEPs. CC messages are confined to a domain or VLAN.
•![]() Loopback messages—unicast frames transmitted by a MEP at administrator request to verify connectivity to a particular maintenance point, indicating whether a destination is reachable. A loopback message is similar to an Internet Control Message Protocol (ICMP) ping message.
Loopback messages—unicast frames transmitted by a MEP at administrator request to verify connectivity to a particular maintenance point, indicating whether a destination is reachable. A loopback message is similar to an Internet Control Message Protocol (ICMP) ping message.
•![]() Traceroute messages—multicast frames transmitted by a MEP at administrator request to track the path (hop-by-hop) to a destination MEP. Traceroute messages are similar in concept to UDP traceroute messages.
Traceroute messages—multicast frames transmitted by a MEP at administrator request to track the path (hop-by-hop) to a destination MEP. Traceroute messages are similar in concept to UDP traceroute messages.
•![]() AIS messages—described in Chapter 55 "Configuring Ethernet CFM and OAM."
AIS messages—described in Chapter 55 "Configuring Ethernet CFM and OAM."
Crosscheck Function
The crosscheck function verifies a post-provisioning timer-driven service between dynamically configured MEPs (using crosscheck messages) and expected MEPs (by configuration) for a service. It verifies that all endpoints of a multipoint service are operational. The crosscheck function is performed only one time and is initiated from the command-line interface (CLI).
SNMP Traps
The MEPs generate two types of SMNP traps: CC traps and crosscheck traps.
Supported CC traps include:
•![]() MEP up
MEP up
•![]() MEP down
MEP down
•![]() cross-connect (a service ID does not match the VLAN)
cross-connect (a service ID does not match the VLAN)
•![]() loop
loop
•![]() configuration error
configuration error
Supported crosscheck traps include:
•![]() service up
service up
•![]() MEP missing (an expected MEP is down)
MEP missing (an expected MEP is down)
•![]() unknown MEP
unknown MEP
IP SLAs Support for CFM
The Metro switch supports CFM with IP Service Level Agreements (SLAs), which gathers Ethernet layer network performance metrics. Available statistical measurements for the IP SLAs CFM operation include round-trip time, jitter (interpacket delay variance), and packet loss. You can schedule multiple IP SLA operations and use Simple Network Management Protocol (SNMP) trap notifications and syslog messages to monitor threshold violations proactively.
IP SLA integration with CFM gathers Ethernet layer statistical measurements by sending and receiving Ethernet data frames between CFM MEPs. Performance is measured between the source MEP and the destination MEP. Unlike other IP SLA operations that provide performance metrics for only the IP layer, IP SLAs with CFM provide performance metrics for Layer 2.
You can manually configure individual Ethernet ping or jitter operations. You can also configure an IP SLA automatic Ethernet operation that queries the CFM database for all MEPs in a given maintenance domain and VLAN. The operation then automatically creates individual Ethernet ping or jitter operations based on the discovered MEPs.
For more information about IP SLA operation with CFM, see the IP SLAs for Metro-Ethernet feature module at this URL:
http://www.cisco.com/en/US/docs/ios/12_2sr/12_2srb/feature/guide/sr_meth.html
Configuring Ethernet CFM
To configure Ethernet CFM you must prepare the network and configuring services. You can optionally configure and enable crosschecking. These sections are included:
•![]() Default Ethernet CFM Configuration
Default Ethernet CFM Configuration
•![]() Ethernet CFM Configuration Guidelines
Ethernet CFM Configuration Guidelines
•![]() Configuring the Ethernet CFM Service over VLANs
Configuring the Ethernet CFM Service over VLANs
•![]() Configuring Ethernet CFM Crosscheck for VLANs
Configuring Ethernet CFM Crosscheck for VLANs
•![]() Configuring IP SLAs CFM Operation
Configuring IP SLAs CFM Operation
•![]() Example: Switchport/VLAN CFM with an Inward-Facing MEP
Example: Switchport/VLAN CFM with an Inward-Facing MEP
Default Ethernet CFM Configuration
CFM is globally disabled.
CFM is enabled on all interfaces. A port can be configured as a flow point (MIP/MEP), a transparent port, or disabled (CFM disabled). By default, ports are transparent until configured as MEP, MIP, or disabled.
There are no MEPs or MIPs configured.
Ethernet CFM Configuration Guidelines
Here are some configuration guidelines and restrictions for CFM:
•![]() A MIP should be configured on a port before a MEP, unless the MEP is at level 7 or the MEP is an outward-facing MEP (OFM). Similarly, all the MEPs have to be removed before a MIP on a port.
A MIP should be configured on a port before a MEP, unless the MEP is at level 7 or the MEP is an outward-facing MEP (OFM). Similarly, all the MEPs have to be removed before a MIP on a port.
•![]() CFM Unicast packets (Loopback Messages and Traceroute Reply), are not allowed on an OFM on STP blocked ports. So, the blocked port cannot respond to ping and traceroute.
CFM Unicast packets (Loopback Messages and Traceroute Reply), are not allowed on an OFM on STP blocked ports. So, the blocked port cannot respond to ping and traceroute.
•![]() CFM is not supported and cannot be configured on routed ports.
CFM is not supported and cannot be configured on routed ports.
•![]() CFM is not supported and cannot be configured on dot1q-tunnel ports.
CFM is not supported and cannot be configured on dot1q-tunnel ports.
•![]() CFM is supported on EtherChannel port channels. You can configure an EtherChannel port channel as MEP or MIP. However, CFM is not supported on individual ports that belong to an EtherChannel and you cannot add a CFM port to an EtherChannel group.
CFM is supported on EtherChannel port channels. You can configure an EtherChannel port channel as MEP or MIP. However, CFM is not supported on individual ports that belong to an EtherChannel and you cannot add a CFM port to an EtherChannel group.
•![]() You cannot configure CFM on VLAN interfaces.
You cannot configure CFM on VLAN interfaces.
•![]() You cannot configure CFM on an EoMPLS port.
You cannot configure CFM on an EoMPLS port.
•![]() CFM is not supported and cannot be configured on a PVLAN isolated host port, community host port or promiscuous access port.
CFM is not supported and cannot be configured on a PVLAN isolated host port, community host port or promiscuous access port.
•![]() CFM is supported only on regular VLANs for inward-facing MEP on PVLAN trunks. Whereas OFM is supported on regular VLANs and isolated VLANs on PVLAN secondary trunk, similarly OFM is supported on regular VLANs and primary VLANs on promiscuous trunk ports.
CFM is supported only on regular VLANs for inward-facing MEP on PVLAN trunks. Whereas OFM is supported on regular VLANs and isolated VLANs on PVLAN secondary trunk, similarly OFM is supported on regular VLANs and primary VLANs on promiscuous trunk ports.
The CFM service on a PVLAN ends at the PVLAN trunk. The translation of CFM service from one PVLAN to another PVLAN is not supported between the PVLAN trunks.
Disabling CFM on a Port
When CFM is globally enabled, you might want to disable CFM selectively on a port (or port channel).

Note ![]() By default, CFM is globally disabled and enabled at every port.
By default, CFM is globally disabled and enabled at every port.
To configure the network for Ethernet CFM over VLANs, follow these steps:
Configuring the Ethernet CFM Service over VLANs
To configure the network for Ethernet CFM over VLANs, follow these steps:
Use the no versions of the commands to remove the configuration or return to the default configurations.
Configuring Ethernet CFM Crosscheck for VLANs
To configure Ethernet CFM crosscheck for VLANs, follow these steps:
Use the no form of each command to remove a configuration or to return to the default settings.
Configuring IP SLAs CFM Operation
You can manually configure an IP SLA's Ethernet ping or jitter echo operation, or you can configure
IP SLAs Ethernet operation with endpoint discovery. You can also configure multiple operation scheduling. For accurate one-way delay statistics, the clocks on the endpoint switches must be synchronized. You can configure the endpoint switches with Network Time Protocol (NTP) so that the switches are synchronized to the same clock source.

Note ![]() When you configure the Catalyst 4500 series switch for a class of service (CoS) probe, you must first globally enable QoS by entering the mls qos global configuration command.
When you configure the Catalyst 4500 series switch for a class of service (CoS) probe, you must first globally enable QoS by entering the mls qos global configuration command.
For detailed information about configuring IP SLAs operations, see the Cisco IOS IP SLAs Configuration Guide, Release 12.4T at this URL:
http://www.cisco.com/en/US/products/ps6441/products_installation_and_configuration_guides_list.html
For detailed information about IP SLAs commands, see the command reference at this URL:
http://www.cisco.com/en/US/docs/ios/ipsla/command/reference/sla_book.html
This section includes these procedures:
•![]() Manually Configuring an IP SLAs CFM Probe or Jitter Operation
Manually Configuring an IP SLAs CFM Probe or Jitter Operation
•![]() Configuring an IP SLAs Operation with Endpoint Discovery
Configuring an IP SLAs Operation with Endpoint Discovery
Manually Configuring an IP SLAs CFM Probe or Jitter Operation
To manually configure an IP SLAs Ethernet echo (ping) or jitter operation, follow these steps:
To remove an IP SLAs operation, enter the no ip sla operation-number global configuration command.
Configuring an IP SLAs Operation with Endpoint Discovery
To use IP SLAs to automatically discover the CFM endpoints for a domain and VLAN ID, follow these steps. You can configure ping or jitter operations to the discovered endpoints.
To remove an IP SLAs operation, enter the no ip sla operation-number global configuration command.
Example: Switchport/VLAN CFM with an Inward-Facing MEP
The following is an example of a VLAN-based CFM configuration between two switches. In this example, a Supervisor Engine II+10GE switch called g6-1 is connected to a Metro Ethernet Supervisor Engine 6-E switch called Switch. Gi 6/5 of g6-1 is connected to the gi 3/5 of the Switch through an ethernet cable.
Configuration on the Supervisor Engine II+10GE ("g6-1")
-----------------------------------------------------
!
ethernet cfm domain customer2 level 6
ethernet cfm domain PROVIDER2 level 5
service customerX vlan 102
ethernet cfm enable
!
!
vlan 102
!
interface GigabitEthernet6/2
switchport access vlan 102
ethernet cfm mip level 6
ethernet cfm mep level 5 mpid 2101 vlan 102
!
interface GigabitEthernet6/5
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 102
switchport mode trunk
ethernet cfm mip level 5
!
ethernet cfm cc enable level 5 vlan 102
!
Screen dumps from "g6-1"
-----------------------------------------------------
g6-1# show ethernet cfm main rem
Can only Ping/Traceroute to remote MEPs marked with *
-------------------------------------------------------------------------------
MPID Level Mac Address Vlan PortState InGressPort Age(sec) Service ID
-------------------------------------------------------------------------------
2111* 5 001b.d550.90fd 102 UP Gi6/5 6 customerX
Total Remote MEPs: 1
g6-1#
g6-1# show ethernet cfm main local
sh ethernet cfm main local
-------------------------------------------------------------------------------
MPID Level Type VLAN Port CC-Status MAC DomainName
-------------------------------------------------------------------------------
2101 5 MEP I 102 Gi6/2 Enabled 000a.4172.df3d PROVIDER2
-------------------------------------------------------------------------------
Level Type Port MAC
-------------------------------------------------------------------------------
6 MIP Gi6/2 000a.4172.df3d
5 MIP Gi6/5 000a.4172.df3d
g6-1#
Configuration on the Metro Ethernet Supervisor Engine 6-E Switch ("Switch")
-----------------------------------------------------
!
ethernet cfm domain customer2 level 6
ethernet cfm domain PROVIDER2 level 5
service customerX vlan 102
ethernet cfm enable
!
vlan 102
!
interface GigabitEthernet3/1
switchport mode trunk
ethernet cfm mip level 6
ethernet cfm mep level 5 mpid 2111 vlan 102
!
interface GigabitEthernet3/5
switchport mode trunk
ethernet cfm mip level 5
!
ethernet cfm cc enable level 5 vlan 102
!
Screen dumps on "Switch"
-----------------------------------------------------
Switch# show ethernet cfm main rem
Can only Ping/Traceroute to remote MEPs marked with *
MPID Level Mac Address Vlan PortState InGressPort Age(sec) Service ID
2101* 5 000a.4172.df3d 102 UP Gi3/5 1 customerX
Total Remote MEPs: 1
Switch# show ethernet cfm main local
MPID DomainName Level Type VLAN Port CC-Status MAC
2111 PROVIDER2 5 MEP 102 Gi3/1 Enabled 001b.d550.90fd
Level Type Port MAC
6 MIP Gi3/1 001b.d550.90fd
5 MIP Gi3/5 001b.d550.90fd
Displaying Ethernet CFM Information
To display Ethernet CFM information, you can use the privileged EXEC commands in Table 55-1.
To display IP SLAs Ethernet CFM information, you can use the privileged EXEC commands in Table 55-2.
Ethernet OAM Protocol Overview
The Ethernet OAM protocol for installing, monitoring, and troubleshooting Metro Ethernet networks and Ethernet WANs relies on an optional sublayer in the data link layer of the OSI model. Normal link operation does not require Ethernet OAM. You can implement Ethernet OAM on any full-duplex point-to-point or emulated point-to-point Ethernet link for a network or part of a network (specified interfaces).
OAM frames, called OAM protocol data units (OAM PDUs) use the slow protocol destination MAC address 0180.c200.0002. They are intercepted by the MAC sublayer and cannot propagate beyond a single hop within an Ethernet network. Ethernet OAM is a relatively slow protocol, with a maximum transmission rate of 10 frames per second, resulting in minor impact to normal operations. However, because the CPU must poll error counters frequently, when you enable link monitoring, the number of required CPU cycles is proportional to the number of interfaces that must be polled.
Ethernet OAM has two major components:
•![]() The OAM client establishes and manages Ethernet OAM on a link and enables and configures the OAM sublayer. During the OAM discovery phase, the OAM client monitors OAM PDUs received from the remote peer and enables OAM functionality. After the discovery phase, it manages the rules of response to OAM PDUs and the OAM remote loopback mode.
The OAM client establishes and manages Ethernet OAM on a link and enables and configures the OAM sublayer. During the OAM discovery phase, the OAM client monitors OAM PDUs received from the remote peer and enables OAM functionality. After the discovery phase, it manages the rules of response to OAM PDUs and the OAM remote loopback mode.
•![]() The OAM sublayer presents two standard IEEE 802.3 MAC service interfaces facing the superior and inferior MAC sublayers. It provides a dedicated interface for the OAM client to pass OAM control information and PDUs to and from the client. The sublayer includes these components:
The OAM sublayer presents two standard IEEE 802.3 MAC service interfaces facing the superior and inferior MAC sublayers. It provides a dedicated interface for the OAM client to pass OAM control information and PDUs to and from the client. The sublayer includes these components:
–![]() The control block provides the interface between the OAM client and other OAM sublayer internal blocks.
The control block provides the interface between the OAM client and other OAM sublayer internal blocks.
–![]() The multiplexer manages frames from the MAC client, the control block, and the parser and passes OAM PDUs from the control block and loopback frames from the parser to the subordinate layer.
The multiplexer manages frames from the MAC client, the control block, and the parser and passes OAM PDUs from the control block and loopback frames from the parser to the subordinate layer.
–![]() The parser classifies frames as OAM PDUs, MAC client frames, or loopback frames and sends them to the appropriate entity: OAM PDUs to the control block, MAC client frames to the superior sublayer, and loopback frames to the multiplexer.
The parser classifies frames as OAM PDUs, MAC client frames, or loopback frames and sends them to the appropriate entity: OAM PDUs to the control block, MAC client frames to the superior sublayer, and loopback frames to the multiplexer.
OAM Features
These OAM features are defined by IEEE 802.3ah:
•![]() Discovery identifies devices in the network and their OAM capabilities. It uses periodic OAM PDUs to advertise OAM mode, configuration, and capabilities; PDU configuration; and platform identity. An optional phase allows the local station to accept or reject the configuration of the peer OAM entity.
Discovery identifies devices in the network and their OAM capabilities. It uses periodic OAM PDUs to advertise OAM mode, configuration, and capabilities; PDU configuration; and platform identity. An optional phase allows the local station to accept or reject the configuration of the peer OAM entity.
•![]() Link monitoring detects and indicates link faults under a variety of conditions and uses the event notification OAM PDU to notify the remote OAM device when it detects problems on the link. Error events include when the number of symbol errors, the number of frame errors, the number of frame errors within a specified number of frames, or the number of error seconds within a specified period exceeding a configured threshold.
Link monitoring detects and indicates link faults under a variety of conditions and uses the event notification OAM PDU to notify the remote OAM device when it detects problems on the link. Error events include when the number of symbol errors, the number of frame errors, the number of frame errors within a specified number of frames, or the number of error seconds within a specified period exceeding a configured threshold.
•![]() Remote failure indication conveys a slowly deteriorating quality of an OAM entity to its peers by communicating these conditions: Link Fault means a loss of signal, Dying Gasp means an unrecoverable condition, and Critical Event means an unspecified vendor-specific critical event. The switch can receive and process but not generate Link Fault or Critical Event OAM PDUs. It can generate Dying Gasp OAM PDUs to show that Ethernet OAM is disabled, the interface is shut down, the interface enters the error-disabled state, or the switch is reloading. It can respond to, but not generate, Dying Gasp PDUs based on loss of power.
Remote failure indication conveys a slowly deteriorating quality of an OAM entity to its peers by communicating these conditions: Link Fault means a loss of signal, Dying Gasp means an unrecoverable condition, and Critical Event means an unspecified vendor-specific critical event. The switch can receive and process but not generate Link Fault or Critical Event OAM PDUs. It can generate Dying Gasp OAM PDUs to show that Ethernet OAM is disabled, the interface is shut down, the interface enters the error-disabled state, or the switch is reloading. It can respond to, but not generate, Dying Gasp PDUs based on loss of power.
•![]() Remote loopback mode ensures link quality with a remote peer during installation or troubleshooting. In this mode, when the switch receives a frame that is not an OAM PDU or a pause frame, it sends it back on the same port. The link appears to the user to be functioning. You can use the returned loopback acknowledgement to test delay, jitter, and throughput.
Remote loopback mode ensures link quality with a remote peer during installation or troubleshooting. In this mode, when the switch receives a frame that is not an OAM PDU or a pause frame, it sends it back on the same port. The link appears to the user to be functioning. You can use the returned loopback acknowledgement to test delay, jitter, and throughput.
OAM Messages
Ethernet OAM messages or PDUs are standard length, untagged Ethernet frames between 64 and 1518 bytes. They do not go beyond a single hop and have a maximum transmission rate of 10 OAM PDUs per second. Message types are information, event notification, loopback control, or vendor-specific OAM PDUs.
Setting Up and Configuring Ethernet OAM
This section includes this information:
•![]() Default Ethernet OAM Configuration
Default Ethernet OAM Configuration
•![]() Ethernet OAM Configuration Guidelines
Ethernet OAM Configuration Guidelines
•![]() Enabling Ethernet OAM on an Interface
Enabling Ethernet OAM on an Interface
•![]() Enabling Ethernet OAM Remote Loopback
Enabling Ethernet OAM Remote Loopback
•![]() Configuring Ethernet OAM Link Monitoring
Configuring Ethernet OAM Link Monitoring
•![]() Configuring Ethernet OAM Remote Failure Indications
Configuring Ethernet OAM Remote Failure Indications
•![]() Configuring Ethernet OAM Templates
Configuring Ethernet OAM Templates
Default Ethernet OAM Configuration
The default configuration is as follows:
•![]() Ethernet OAM is disabled on all interfaces.
Ethernet OAM is disabled on all interfaces.
•![]() When Ethernet OAM is enabled on an interface, link monitoring is automatically turned on.
When Ethernet OAM is enabled on an interface, link monitoring is automatically turned on.
•![]() Remote loopback is disabled.
Remote loopback is disabled.
•![]() No Ethernet OAM templates are configured.
No Ethernet OAM templates are configured.
Ethernet OAM Configuration Guidelines
Follow these guidelines when configuring Ethernet OAM:
•![]() The switch does not support monitoring of egress frames sent with cyclic redundancy code (CDC) errors. The ethernet oam link-monitor transmit crc interface-configuration or template-configuration commands are visible but are not supported on the switch. The commands are accepted but are not applied to an interface.
The switch does not support monitoring of egress frames sent with cyclic redundancy code (CDC) errors. The ethernet oam link-monitor transmit crc interface-configuration or template-configuration commands are visible but are not supported on the switch. The commands are accepted but are not applied to an interface.
•![]() For a remote failure indication, the switch does not generate Link Fault or Critical Event OAM PDUs. However, if these PDUs are received from a link partner, they are processed. The switch generates and receives Dying Gasp OAM PDUs when Ethernet OAM is disabled, the interface is shut down, the interface enters the error-disabled state, or the switch is reloading. It can respond to, but not generate, Dying Gasp PDUs based on loss of power.
For a remote failure indication, the switch does not generate Link Fault or Critical Event OAM PDUs. However, if these PDUs are received from a link partner, they are processed. The switch generates and receives Dying Gasp OAM PDUs when Ethernet OAM is disabled, the interface is shut down, the interface enters the error-disabled state, or the switch is reloading. It can respond to, but not generate, Dying Gasp PDUs based on loss of power.
•![]() The switch does not support Ethernet OAM loopback on ports that belong to an EtherChannel, ISL trunk, and promiscuous trunk.
The switch does not support Ethernet OAM loopback on ports that belong to an EtherChannel, ISL trunk, and promiscuous trunk.
Enabling Ethernet OAM on an Interface
To enable Ethernet OAM on an interface, follow these steps:
Enter the no ethernet oam interface configuration command to disable Ethernet OAM on the interface.
This example shows how to set basic OAM parameters on the switch:
Switch(config)# int gi1/3
Switch(config-if)# ethernet oam
Switch(config-if)# ethernet oam max-rate 9
Switch(config-if)# ethernet oam mode passive
Switch(config-if)# end
Switch# show ethernet oam status int gi1/2
GigabitEthernet1/2
General
-------
Admin state: enabled
Mode: passive
PDU max rate: 9 packets per second
PDU min rate: 1 packet per 1 second
Link timeout: 5 seconds
High threshold action: no action
Link fault action: no action
Dying gasp action: no action
Critical event action: no action
Link Monitoring
---------------
Status: supported (on)
Symbol Period Error
Window: 100 x 1048576 symbols
Low threshold: 1 error symbol(s)
High threshold: none
Frame Error
Window: 10 x 100 milliseconds
Low threshold: 1 error frame(s)
High threshold: none
Frame Period Error
Window: 1000 x 10000 frames
Low threshold: 1 error frame(s)
High threshold: none
Frame Seconds Error
Window: 100 x 100 milliseconds
Low threshold: 1 error second(s)
High threshold: none
Receive-Frame CRC Error
Window: 10 x 100 milliseconds
Low threshold: 10 error frame(s)
High threshold: none
Transmit-Frame CRC Error: Not Supported
Enabling Ethernet OAM Remote Loopback
You must enable Ethernet OAM remote loopback on an interface for the local OAM client to initiate OAM remote loopback operations. Changing this setting causes the local OAM client to exchange configuration information with its remote peer. Remote loopback is disabled by default.
Remote loopback has these limitations:
•![]() Only data packets are looped back.
Only data packets are looped back.
•![]() You cannot configure Ethernet OAM remote loopback on ISL ports or ports that belong to an EtherChannel.
You cannot configure Ethernet OAM remote loopback on ISL ports or ports that belong to an EtherChannel.
•![]() Remote loopback can be supported on a max of 16 ports.
Remote loopback can be supported on a max of 16 ports.
To enable Ethernet OAM remote loopback on an interface, follow these steps:
Use the no ethernet oam remote-loopback {supported | timeout} interface configuration command to disable remote loopback support or remove the timeout setting.
This example shows how to enable OAM Remote Loopback:
Switch(config)# int gi1/3
Switch(config-if)# ethernet oam
Switch(config-if)# ethernet oam remote-loopback supported
Switch(config-if)# end
Switch# show running int gi1/1
Building configuration...
Current configuration : 209 bytes
!
interface GigabitEthernet1/1
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 1,19
switchport mode trunk
ethernet oam remote-loopback supported
ethernet oam
end
Switch# ethernet oam remote-loopback start int gi1/1
This is a intrusive loopback.
Therefore, while you test Ethernet OAM MAC connectivity,
you will be unable to pass traffic across that link.
Proceed with Remote Loopback? [confirm]
Switch# ethernet oam remote-loopback stop int gi1/1
Switch#
*Apr 9 12:52:39.793: %ETHERNET_OAM-6-LOOPBACK: Interface Gi1/1 has exited the master loopback mode.
Configuring Ethernet OAM Link Monitoring
You can configure high and low thresholds for link-monitoring features. If no high threshold is configured, the default is none—no high threshold is set. If you do not set a low threshold, the default is a value lower than the high threshold.
Cisco does not generate link event PDUs for rxcrc and trxcrc errors because these are nonstandard.
To configure Ethernet OAM link monitoring on an interface, follow these steps:
The ethernet oam link-monitor transmit-crc {threshold {high {high-frames | none} | low {low-frames}} | window milliseconds} command is visible on the switch and you can enter it, but it is not supported. Enter the no form of the command to disable the configuration. Use the no form of each command to disable the threshold setting.
Symbol error counters are supported on the following line cards and supervisor cards:
•![]() Supervisor cards: WS-X4515, WS-X4516, WS-X4013+, WS-X4013+TS, WS-X4516-10GE, WS-X4013+10GE
Supervisor cards: WS-X4515, WS-X4516, WS-X4013+, WS-X4013+TS, WS-X4516-10GE, WS-X4013+10GE
•![]() Line cards: WS-X4148-RJ, WS-X4124-RJ, WS-X4232, WS-X4232-RJ-XX, WS-X4148-RJ21, WS-X4504-FX-MT, WS-X4224-RJ21-XX, WS-X4124-FX-MT, WS-X4232-L3
Line cards: WS-X4148-RJ, WS-X4124-RJ, WS-X4232, WS-X4232-RJ-XX, WS-X4148-RJ21, WS-X4504-FX-MT, WS-X4224-RJ21-XX, WS-X4124-FX-MT, WS-X4232-L3
The rest of the cards do not support symbol error counters.
Configuring Ethernet OAM Remote Failure Indications
You can configure an error-disable action to occur on an interface when the following occur:
•![]() crossing the high thresholds configured on the interface for link monitoring
crossing the high thresholds configured on the interface for link monitoring
•![]() on reception of Dying Gasp, executing shut on the interface
on reception of Dying Gasp, executing shut on the interface
•![]() on reception of Dying Gasp, executing reload command
on reception of Dying Gasp, executing reload command
•![]() on reception of Dying Gasp, executing no ethernet oam command on the interface
on reception of Dying Gasp, executing no ethernet oam command on the interface
To enable Ethernet OAM remote-failure indication actions on an interface, follow these steps:
This example shows how to configure Ethernet OAM remote-failure action on the switch interface:
Switch# conf t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# int gi1/1
Switch(config-if)# ethernet oam remote-failure dying-gasp action error
Switch(config-if)# ethernet oam link-monitor high-threshold action error
Switch(config-if)# end
Switch# show running-config int gi1/1
Building configuration...
Current configuration : 353 bytes
!
interface GigabitEthernet1/1
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 1,19
switchport mode trunk
ethernet oam remote-loopback supported
ethernet oam link-monitor high-threshold action error-disable-interface
ethernet oam remote-failure dying-gasp action error-disable-interface
ethernet oam
end
Switch# show ethernet oam status int gi1/1
GigabitEthernet1/1
General
-------
Admin state: enabled
Mode: active
PDU max rate: 10 packets per second
PDU min rate: 1 packet per 1 second
Link timeout: 5 seconds
High threshold action: error disable interface
Link fault action: no action
Dying gasp action: error disable interface
Critical event action: no action
Link Monitoring
---------------
Status: supported (on)
Symbol Period Error
Window: 100 x 1048576 symbols
Low threshold: 1 error symbol(s)
High threshold: none
Frame Error
Window: 10 x 100 milliseconds
Low threshold: 1 error frame(s)
High threshold: none
Frame Period Error
Window: 1000 x 10000 frames
Low threshold: 1 error frame(s)
High threshold: none
Frame Seconds Error
Window: 100 x 100 milliseconds
Low threshold: 1 error second(s)
High threshold: none
Receive-Frame CRC Error
Window: 10 x 100 milliseconds
Low threshold: 10 error frame(s)
High threshold: none
Transmit-Frame CRC Error: Not Supported
To enable Ethernet OAM failover action on an EtherChannel interface, follow these steps:
The switch does not generate Link Fault or Critical Event OAM PDUs. However, if these PDUs are received from a link partner, they are processed. The switch supports sending and receiving Dying Gasp OAM PDUs when Ethernet OAM is disabled, the interface is shut down, the interface enters the error-disabled state, or the switch is reloading. It can respond to but not generate Dying Gasp PDUs based on loss of power. Enter the no ethernet remote-failure {critical-event | dying-gasp | link-fault} action command to disable the remote failure indication action.
Configuring Ethernet OAM Templates
You can create a template for configuring a common set of options on multiple Ethernet OAM interfaces. The template can be configured to monitor frame errors, frame-period errors, frame-second errors, received CRS errors, and symbol-period errors and thresholds. You can also set the template to put the interface in error-disabled state if any high thresholds are exceeded. These steps are optional and can be performed in any sequence or repeated to configure different options.
To configure an Ethernet OAM template and to associate it with an interface, follow these steps:
The switch does not support monitoring egress frames with CRC errors. The ethernet oam link-monitor transmit-crc {threshold {high {high-frames | none} | low {low-frames}} | window milliseconds} command is visible on the switch and you can enter it, but it is not supported. Use the
no form of each command to remove the option from the template. Use the
no source-template template-name command to remove the source template association.
The following example illustrates how to configure an Ethernet OAM template and to associate it with an interface:
Switch# conf t
Switch(config)# template oam
Switch(config-template)# ethernet oam link-monitor receive-crc threshold high 1000
Switch(config-template)# ethernet oam link-monitor receive-crc threshold low 10
Switch(config-template)# ethernet oam link-monitor symbol-period threshold high 5000
Switch(config-template)# ethernet oam link-monitor symbol-period threshold low 5
Switch(config-template)# ethernet oam link-monitor frame threshold high 8000
Switch(config-template)# ethernet oam link-monitor frame threshold low 8
Switch(config-template)# ethernet oam link-monitor frame-period threshold hig 9000
Switch(config-template)# ethernet oam link-monitor frame-period threshold low 9
Switch(config-template)# ethernet oam link-monitor high action error-disable-interface
Switch(config-template)# exit
Switch(config)# int gi1/2
Switch(config-if)# source template oam
Switch(config-if)# end
Switch# show ethernet oam status int gi1/2
GigabitEthernet1/2
General
-------
Admin state: enabled
Mode: active
PDU max rate: 10 packets per second
PDU min rate: 1 packet per 1 second
Link timeout: 5 seconds
High threshold action: error disable interface
Link fault action: no action
Dying gasp action: no action
Critical event action: no action
Link Monitoring
---------------
Status: supported (on)
Symbol Period Error
Window: 100 x 1048576 symbols
Low threshold: 5 error symbol(s)
High threshold: 5000 error symbol(s)
Frame Error
Window: 10 x 100 milliseconds
Low threshold: 8 error frame(s)
High threshold: 8000 error frame(s)
Frame Period Error
Window: 1000 x 10000 frames
Low threshold: 9 error frame(s)
High threshold: 9000 error frame(s)
Frame Seconds Error
Window: 100 x 100 milliseconds
Low threshold: 1 error second(s)
High threshold: none
Receive-Frame CRC Error
Window: 10 x 100 milliseconds
Low threshold: 10 error frame(s)
High threshold: 1000 error frame(s)
Transmit-Frame CRC Error: Not Supported
Displaying Ethernet OAM Protocol Information
To display Ethernet OAM protocol information, you can use the privileged EXEC commands in Table 55-3.
These examples show how to apply these commands:
Switch# show ethernet oam discovery
GigabitEthernet1/1
Local client
------------
Administrative configurations:
Mode: active
Unidirection: not supported
Link monitor: supported (on)
Remote loopback: supported
MIB retrieval: not supported
Mtu size: 1500
Operational status:
Port status: operational
Loopback status: no loopback
PDU revision: 10
Remote client
-------------
MAC address: 000f.8f03.3591
Vendor(oui): 00000C(cisco)
Administrative configurations:
PDU revision: 2
Mode: active
Unidirection: not supported
Link monitor: supported
Remote loopback: supported
MIB retrieval: not supported
Mtu size: 1500
Switch# show ethernet oam statistics
GigabitEthernet1/1
Counters:
---------
Information OAMPDU Tx : 101163
Information OAMPDU Rx : 51296
Unique Event Notification OAMPDU Tx : 0
Unique Event Notification OAMPDU Rx : 0
Duplicate Event Notification OAMPDU TX : 0
Duplicate Event Notification OAMPDU RX : 0
Loopback Control OAMPDU Tx : 12
Loopback Control OAMPDU Rx : 0
Variable Request OAMPDU Tx : 0
Variable Request OAMPDU Rx : 0
Variable Response OAMPDU Tx : 0
Variable Response OAMPDU Rx : 0
Cisco OAMPDU Tx : 7
Cisco OAMPDU Rx : 8
Unsupported OAMPDU Tx : 0
Unsupported OAMPDU Rx : 0
Frames Lost due to OAM : 0
Local Faults:
-------------
0 Link Fault records
2 Dying Gasp records
Total dying gasps : 7
Time stamp : 1d01h
Total dying gasps : 6
Time stamp : 1d01h
0 Critical Event records
Remote Faults:
--------------
0 Link Fault records
2 Dying Gasp records
Total dying gasps : 8
Time stamp : 1d01h
Total dying gasps : 7
Time stamp : 1d01h
0 Critical Event records
Local event logs:
-----------------
0 Errored Symbol Period records
0 Errored Frame records
0 Errored Frame Period records
0 Errored Frame Second records
Remote event logs:
------------------
0 Errored Symbol Period records
0 Errored Frame records
0 Errored Frame Period records
0 Errored Frame Second records
Switch# show ethernet oam summary
Symbols: * - Master Loopback State, # - Slave Loopback State
& - Error Block State
Capability codes: L - Link Monitor, R - Remote Loopback
U - Unidirection, V - Variable Retrieval
Local Remote
Interface MAC Address OUI Mode Capability
Gi1/1 000f.8f03.3591 00000C active L R
Ethernet CFM and Ethernet OAM Interaction
You can also configure the OAM Manager infrastructure to interact between CFM and Ethernet OAM. When the Ethernet OAM protocol is running on an interface that has CFM MEPs configured, Ethernet OAM informs CFM of the state of the interface. Interaction is unidirectional from the Ethernet OAM to the CFM protocol, and the only information exchanged is the user network interface port status.
The Ethernet OAM protocol notifies CFM when these conditions occur:
•![]() Error thresholds are crossed at the local interface.
Error thresholds are crossed at the local interface.
CFM responds to the notification by sending a port status of Local_Excessive_Errors in the Port StatusType Length Value (TLV).
•![]() Ethernet OAM receives an OAM PDU from the remote side showing that an error threshold is exceeded on the remote endpoint.
Ethernet OAM receives an OAM PDU from the remote side showing that an error threshold is exceeded on the remote endpoint.
CFM responds to the notification by sending a port status of Remote_Excessive_Errors in the Port Status TLV.
•![]() The local port is set into loopback mode.
The local port is set into loopback mode.
CFM responds by sending a port status of Test in the Port Status TLV.
•![]() The remote port is set into loopback mode.
The remote port is set into loopback mode.
CFM responds by sending a port status of Test in the Port Status TLV.
For more information about CFM and interaction with Ethernet OAM, see the Ethernet Connectivity Fault Management feature module at this URL:
http://www.cisco.com/en/US/docs/ios/12_2sr/12_2sra/feature/guide/srethcfm.html
Ethernet OAM and CFM Configuration Example
These are configuration example of the interworking between Ethernet OAM and CFM in a sample service provider network. Such a hypothetical network would contain a provider-edge switch connected to a customer edge switch at each endpoint. You must configure CFM, E-LMI, and Ethernet OAM between the customer edge and the provider edge switch.
Customer-edge switch 1 (CE1) configuration:
Switch# config t
Switch(config)# interface GigabitEthernet1/1
Switch(config-if)# switchport trunk allowed vlan 10
Switch(config-if)# switchport mode trunk
Switch(config-if)# ethernet oam remote-loopback supported
Switch(config-if)# ethernet oam
Switch(config-if)# exit
Provider-edge switch 1 (PE1) configuration:
Switch# config t
Switch(config)# interface FastEthernet1/20
Switch(config-if)# switchport trunk encapsulation dot1q
Switch(config-if)# switchport mode trunk
Switch(config-if)# ethernet cfm mip level 7
Switch(config-if)# ethernet cfm mep level 4 mpid 100 vlan 100
Switch(config-if)# ethernet oam remote-loopback supported
Switch(config-if)# ethernet oamt
Provider-edge switch 2 (PE2) configuration:
Switch# config t
Switch(config)# interface GigabitEthernet1/20
Switch(config-if)# switchport mode trunk
Switch(config-if)# ethernet cfm mip level 7
Switch(config-if)# ethernet cfm mep level 4 mpid 101 vlan 10
Switch(config-if)# ethernet oam remote-loopback supported
Switch(config-if)# ethernet oam
Customer-edge switch 2 (CE2) configuration:
Switch# config t
Switch(config)# interface GigabitEthernet1/1
Switch(config-if)# switchport trunk allowed vlan 10
Switch(config-if)# switchport mode trunk
Switch(config-if)# ethernet oam remote-loopback supported
Switch(config-if)# ethernet oam
Switch(config-if)# exit
These output examples show provider-edge switch port status of the configuration. Port status shows as UP at both switches.
Switch PE1:
Switch# show ethernet cfm maintenance points remote
MPID Level Mac Address Vlan PortState InGressPort Age(sec) Service ID
101 * 4 0015.633f.6900 10 UP Gi1/1 27 blue
Switch PE2:
Switch# show ethernet cfm maintenance points remote
MPID Level Mac Address Vlan PortState InGressPort Age(sec) Service ID
100 * 4 0012.00a3.3780 10 UP Gi1/1 8 blue
Total Remote MEPs: 1
This example shows the output when you start remote loopback on CE1 (or PE1). The port state on the remote PE switch shows as Test and the remote CE switch enters into error-disable mode.
Switch# ethernet oam remote-loopback start interface gigabitethernet 1/1
This is a intrusive loopback.
Therefore, while you test Ethernet OAM MAC connectivity,
you will be unable to pass traffic across that link.
Proceed with Remote Loopback? [confirm]
Switch PE1:
Switch# show ethernet cfm maintenance points remote
MPID Level Mac Address Vlan PortState InGressPort Age(sec) Service ID
101 * 4 0015.633f.6900 10 UP Gi1/1 27 blue
Switch PE2:
Switch# show ethernet cfm maintenance points remote
MPID Level Mac Address Vlan PortState InGressPort Age(sec) Service ID
100 * 4 0012.00a3.3780 10 TEST Gi1/1 8 blue
Total Remote MEPs: 1
In addition, if you shut down the CE1 interface that connects to PE1, the remote PE2 port shows a PortState of Down.
 Feedback
Feedback