LDAP Synchronization Overview
Lightweight Directory Access Protocol (LDAP) synchronization helps you to provision and configure end users for your system. During LDAP synchronization, the system imports a list of users and associated user data from an external LDAP directory into the Cisco Unified Communications Manager database. In addition, you can configure a regular synchronization schedule to pick up any changes in your employee data.
User ID and Directory URI
-
User ID—You must specify a value for the user ID on Cisco Unified Communications Manager. This value is required for the default IM address scheme and for users to sign in. The default value is
sAMAccountName.
Important
If the attribute for the user ID is other than
sAMAccountNameand you are using the default IM address scheme in Cisco Unified Communications Manager IM and Presence Service, you must specify the attribute as the value for the parameter in your client configuration file as follows:The CDI parameter is UserAccountName.<UserAccountName>attribute-name</UserAccountName>If you do not specify the attribute in your configuration, and the attribute is other than
sAMAccountName, the client cannot resolve contacts in your directory. As a result, users do not get presence and cannot send or receive instant messages.
-
Directory URI—You should specify a value for the directory URI if you plan to: -
Enable URI dialing in Cisco Jabber.
-
Use the directory URI address scheme on Cisco Unified Communications Manager IM and Presence Service version 10 and higher.
-
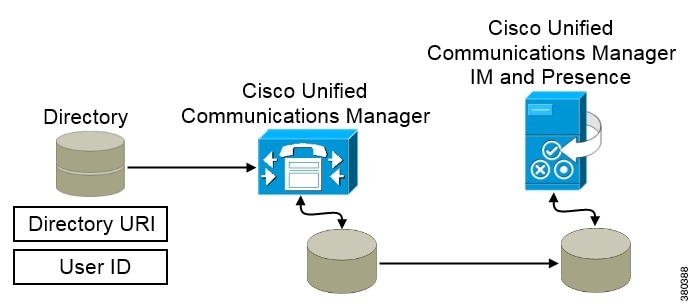
When Cisco Unified Communications Manager synchronizes with the directory source, it retrieves the values for the directory URI and user ID and populates them in the end user configuration table in the Cisco Unified Communications Manager database.
The Cisco Unified Communications Manager database then synchronizes with the Cisco Unified Communications Manager IM and Presence Service database. As a result, the values for the directory URI and user ID are populated in the end user configuration table in the Cisco Unified Communications Manager IM and Presence Service database.
 Feedback
Feedback