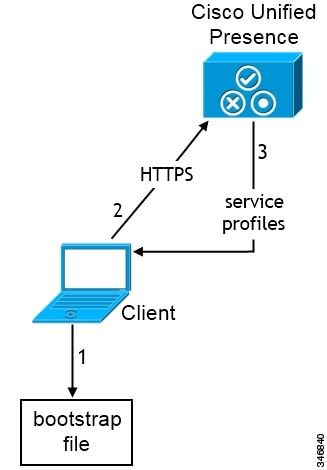
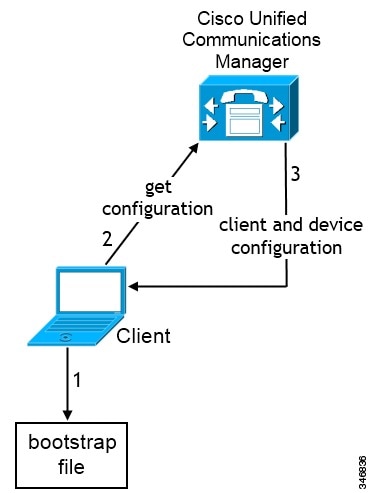
To enable users to launch Cisco Jabber without manually entering service discovery information, create and distribute a configuration URL to users.
You can provide a configuration URL link to users by emailing
the link to the user directly, or by posting the link to a website.
Include the following parameters in the URL:
-
ServicesDomain—Required. Every configuration URL must include the domain of the IM and presence server that Cisco Jabber needs for service discovery.
-
VoiceServiceDomain—Required only if you deploy a hybrid cloud-based architecture where the domain of the IM and presence server differs from
the domain of the voice server. Set this parameter to ensure that Cisco Jabber can discover voice services.
-
ServiceDiscoveryExcludedServices—Optional. You can exclude any of the following services from the service discovery process:
-
Webex—When you set this value, the client:
-
CUCM—When you set this value, the client:
-
CUP—When you set this value, the client:
You can specify multiple, comma-separated values to exclude multiple services.
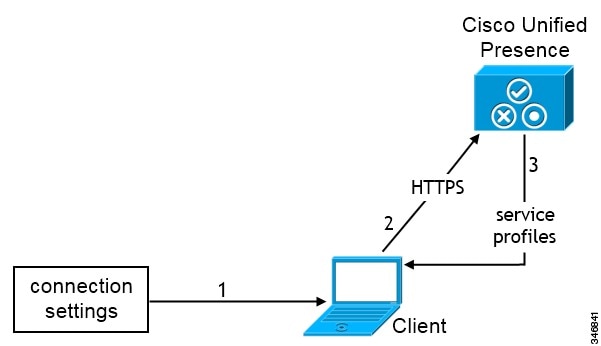
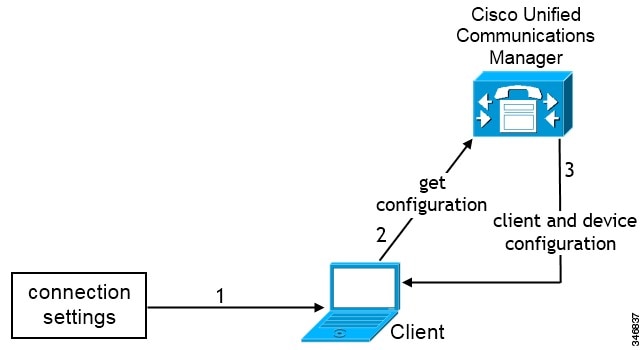
If you exclude all three services, the client does not perform service discovery and prompts the user to manually enter connection
settings.
-
ServicesDomainSsoEmailPrompt—Optional. Specifies whether the user is shown the email prompt for the purposes of determining their home cluster.
-
EnablePRTEncryption—Optional. Specifies that the PRT file is encrypted. Applies to Cisco Jabber for Mac.
-
PRTCertificateName—Optional. Specifies the name of the certificate. Applies to Cisco Jabber for Mac.
-
InvalidCertificateBehavior—Optional. Specifies the client behavior for invalid certificates.
-
PRTCertificateUrl—Specifies the name of a certificate with a public key in the trusted root certificate store. Applies to Cisco Jabber mobile
clients.
-
Telephony_Enabled—Specifies whether the user has phone capability or not. The default is true.
-
ForceLaunchBrowser—Used to force user to use the external browser. Applies to Cisco Jabber mobile clients.

Note
|
ForceLaunchBrowser is used for client certificate deployments and for devices with Android OS below 5.0.
|
-
IP_Mode—Specifies the network IP protocol for the Jabber client.
-
IPv4-Only—Jabber will only attempt to make IPv4 connections.
-
IPv6-Only—Jabber will only attempt to make IPv6 connections.
-
Two Stacks (Default)—Jabber can connect with either IPv4 or IPv6.

Note
|
The parameters are case sensitive.
|
Examples


 Feedback
Feedback