- Preface
- 1 Overview of Access Point Features
- 2 Using the Web-Browser Interface
- 3 Using the Command-Line Interface
- 4 Configuring the Access Point for the First Time
- 5 Administrating the Access Point
- 6 Configuring Radio Settings
- 7 Configuring Multiple SSIDs
- 8 Configuring Spanning Tree Protocol
- 9 Configuring an Access Point as a Local Authenticator
- 10 Configuring WLAN Authentication and Encryption
- 11 Configuring Authentication Types
- 12 Configuring Other Services
- 13 Configuring RADIUS and TACACS+ Servers
- 14 Configuring VLANs
- 15 Configuring QoS
- 16 Configuring Filters
- 17 Configuring CDP
- 18 Configuring SNMP
- 19 Configuring Repeater and Standby Access Points and Workgroup Bridge Mode
- 20 Managing Firmware and Configurations
- 21 Configuring SCEP
- 22 Configuring LLDP
- 23 Configuring L2TPv3 Over UDP/IP
- 24 Configuring Ethernet over GRE
- 25 Configuring System Message Logging
- 26 Troubleshooting
- 27 Miscellaneous AP-Specific Configurations
- APPENDIX A Protocol Filters
- APPENDIX B Supported MIBs
- APPENDIX C Error and Event Messages
- Understanding Repeater Access Points
- Configuring a Repeater Access Point
- Aligning Antennas
- Understanding Hot Standby
- Configuring a Hot Standby Access Point
- Understanding Workgroup Bridge Mode
- Workgroup Bridge VLAN Tagging
- Configuring Workgroup Bridge Mode
- Using Workgroup Bridges in a Lightweight Environment
- Configuring Workgroup Bridges for High-Speed Roaming
- Configuring Transparent Transporting of PROFINET Traffic
Configuring Repeater and Standby Access Points and Workgroup Bridge Mode
This chapter describes how to configure your access point as a repeater, as a hot standby unit, or as a workgroup bridge.
Understanding Repeater Access Points
A repeater access point is not connected to the wired LAN; it is placed within radio range of an access point connected to the wired LAN to extend the range of your infrastructure or to overcome an obstacle that blocks radio communication. You can configure either the 2.4 GHz radio or the 5 GHz radio as a repeater. In access points with two radios, only one radio can be a repeater; the other radio must be shut down or be configured as a root, scanner, or spectrum radio.
The repeater forwards traffic between wireless users and the wired LAN by sending packets to either another repeater or to an access point connected to the wired LAN. The data is sent through the route that provides the best performance for the client. When you configure an access point as a repeater, the access point’s Ethernet port does not forward traffic.
You can set up a chain of several repeater access points, but throughput for client devices at the end of the repeater chain will be quite low. Because each repeater must receive and then re-transmit each packet on the same channel, throughput is cut in half for each repeater you add to the chain.
A repeater access point associates to the access point with which it has the best connectivity. However, you can specify the access point to which the repeater associates. Setting up a static, specific association between a repeater and a root access point improves repeater performance.
To set up repeaters, you must enable Aironet extensions on both the parent (root) access point and the repeater access points. Aironet extensions, which are enabled by default, improve the access point's ability to understand the capabilities of Cisco Aironet client devices associated with the access point. Disabling Aironet extensions sometimes improves the interoperability between the access point and non-Cisco client devices. Non-Cisco client devices might have difficulty communicating with repeater access points and the root access point to which repeaters are associated.
To use an SSID between an access point and a repeater, the Infrastructure SSID option has to be enabled on the SSID to allow AP to repeater communication.
The infrastructure SSID must be assigned to the native VLAN. If more than one VLAN is created on an access point or wireless bridge, an infrastructure SSID cannot be assigned to a non-native VLAN. The following message appears when the infrastructure SSID is configured on non-native VLAN:

Note![]() Access points create a virtual interface for each radio interface, and so repeater access points associate to the root access point twice: once for the actual interface and once for the virtual interface.
Access points create a virtual interface for each radio interface, and so repeater access points associate to the root access point twice: once for the actual interface and once for the virtual interface.

Note![]() You cannot set a radio to act as a repeater and support other SSIDs at the same time. The repeater radio can only repeat the native VLAN. You cannot set a radio as a repeater, and then map to that radio an SSID that is mapped to a VLAN other than the native VLAN. However, the other radio can be configured to support several SSIDs and several VLANs.
You cannot set a radio to act as a repeater and support other SSIDs at the same time. The repeater radio can only repeat the native VLAN. You cannot set a radio as a repeater, and then map to that radio an SSID that is mapped to a VLAN other than the native VLAN. However, the other radio can be configured to support several SSIDs and several VLANs.
Figure 19-1 shows an access point acting as a repeater.
Figure 19-1 Access Point as a Repeater

Configuring a Repeater Access Point
This section provides instructions for setting up an access point as a repeater and includes these sections:
- Default Configuration
- Guidelines for Repeaters
- Setting Up a Repeater
- Verifying Repeater Operation
- Aligning Antennas
- Setting Up a Repeater As a EAP-FAST Client
- Setting Up a Repeater As a WPA2 Client
Default Configuration
Access points are configured as root units by default. Table 19-1 shows the default values for settings that control the access point’s role in the wireless LAN.
|
|
|
|---|---|
Guidelines for Repeaters
Follow these guidelines when configuring repeater access points:
- Use repeaters to serve client devices that do not require high throughput. Repeaters extend the coverage area of your wireless LAN, but they drastically reduce throughput.
- Use repeaters when most if not all client devices that associate with the repeaters are Cisco Aironet clients. When non-Cisco clients are expected, verify that these clients support the Aironet IE extension, as this option is required on the SSID to allow for the communication between an AP and a repeater.
- Make sure that the data rates configured on the repeater access point match the data rates on the parent access point. For instructions on configuring data rates, see the e “Configuring Radio Data Rates” section.
- The SSID configured on the repeater radio must be mapped to the native VLAN.

Note![]() Repeater access points running Cisco IOS software cannot associate to parent access points that do not run Cisco IOS software.
Repeater access points running Cisco IOS software cannot associate to parent access points that do not run Cisco IOS software.

Note![]() Repeater access points do not support wireless domain services (WDS). Do not configure a repeater access point as a WDS candidate, and do not configure a WDS access point to fall back to repeater mode in case of Ethernet failure. Repeaters can join a WDS infrastructure and act as WDS clients whenever needed.
Repeater access points do not support wireless domain services (WDS). Do not configure a repeater access point as a WDS candidate, and do not configure a WDS access point to fall back to repeater mode in case of Ethernet failure. Repeaters can join a WDS infrastructure and act as WDS clients whenever needed.

Note![]() If multiple BSSIDs are configured on a root access point that is designated as the parent of a repeater, the parent MAC address might change if a BSSID on the parent is added or deleted. If you use multiple BSSIDs on your wireless LAN and a repeater on your wireless LAN is configured to associate to a specific parent, check the association status of the repeater when you add or delete BSSIDs on the parent access point. If necessary, reconfigure the disassociated device to use the BSSID’s new MAC address.
If multiple BSSIDs are configured on a root access point that is designated as the parent of a repeater, the parent MAC address might change if a BSSID on the parent is added or deleted. If you use multiple BSSIDs on your wireless LAN and a repeater on your wireless LAN is configured to associate to a specific parent, check the association status of the repeater when you add or delete BSSIDs on the parent access point. If necessary, reconfigure the disassociated device to use the BSSID’s new MAC address.
Setting Up a Repeater
Beginning in Privileged Exec mode, follow these steps to configure an access point as a repeater:
The following example shows how to set up a repeater access point with three potential parents, designated 1 to 3:
This example shows how to remove a parent, here parent 2, from the parent list:
This example shows how to set a timeout of 60 seconds for the parent list:
This example shows how to disable the timeout value for the parent list:
Aligning Antennas
When an access point is configured as a repeater, you can align its antenna with another remote antenna using the dot11 antenna-alignment CLI command.
The command invokes an alignment test. The radio disassociates from its parent, probes adjacent wireless devices, and records the MAC addresses and signal strengths of responses it receives. After the timeout, the radio reassociates with its parent.
Follow these steps to run an antenna alignment test:
|
|
|
|
|---|---|---|
dot11 dot11radio { 0 | 1 } antenna-alignment timeout timeout-in-seconds |
Use the show dot11 antenna-alignment command to list the MAC addresses and signal level for the last 10 devices that responded to the probe.
Verifying Repeater Operation
After you set up the repeater, if your repeater is functioning correctly, the repeater access point should appear associated with the root access point in the root access point's Association Table.
Setting Up a Repeater As a WPA2 Client
WPA key management uses a combination of encryption methods to protect communication between client devices and the access point. You can set up a repeater access point to authenticate to your network like other WPA2-enabled client devices.
Beginning in Privileged Exec mode, follow these steps to set up the repeater as a WPA2 client:
Setting Up a Repeater As a EAP-FAST Client
You can set up a repeater access point to authenticate to your network like other wireless client devices. After you provide a network username and password for the repeater access point, it can authenticate to your network, through the root AP, using user credentials.
Setting up a repeater as a EAP-FAST, or other 802.1x/EAP authentication-method client requires three major steps:
1.![]() Create an authentication username and password for the repeater on your authentication server.
Create an authentication username and password for the repeater on your authentication server.
2.![]() Configure the authentication method to be supported on the root access point to which the repeater associates. The access point to which the repeater associates is called the parent access point. See “Configuring Authentication Types,” for instructions on setting up authentication.
Configure the authentication method to be supported on the root access point to which the repeater associates. The access point to which the repeater associates is called the parent access point. See “Configuring Authentication Types,” for instructions on setting up authentication.

Note![]() On the repeater access point, you must enable the same cipher suite or WEP encryption method and WEP features that are enabled on the parent access point.
On the repeater access point, you must enable the same cipher suite or WEP encryption method and WEP features that are enabled on the parent access point.
3.![]() Configure the repeater to act as a 802.1x/EAP client for the chosen method. The following example shows EAP-FAST configuration:
Configure the repeater to act as a 802.1x/EAP client for the chosen method. The following example shows EAP-FAST configuration:
Understanding Hot Standby
Hot Standby mode designates an access point as a backup for another access point. The standby access point is placed near the access point it monitors, configured exactly the same as the monitored access point. The standby access point associates with the monitored access point as a client and sends IAPP queries to the monitored access point through both the Ethernet and the radio ports. If the monitored access point fails to respond, the standby access point comes online and takes the monitored access point’s place in the network.
Except for the IP address, the standby access point’s settings should be identical to the settings on the monitored access point. If the monitored access point goes offline and the standby access point takes its place in the network, matching settings ensures that client devices can switch easily to the standby access point.
The standby access point monitors another access point in a device-to-device relationship, not in an interface-to-interface relationship. For example, you cannot configure the standby access point’s 5-GHz radio to monitor the 5-GHz radio in access point alpha and the standby’s 2.4-GHz radio to monitor the 2.4-GHz radio in access point bravo. You also cannot configure one radio in a dual-radio access point as a standby radio and configure the other radio to serve client devices.
Hot standby mode is disabled by default.

Note![]() If the monitored access point malfunctions and the standby access point takes its place, repeat the hot standby setup on the standby access point when you repair or replace the monitored access point. The standby access point does not revert to standby mode automatically.
If the monitored access point malfunctions and the standby access point takes its place, repeat the hot standby setup on the standby access point when you repair or replace the monitored access point. The standby access point does not revert to standby mode automatically.

Note![]() The MAC address of the monitored access point might change if a BSSID on the monitored unit is added or deleted. If you use multiple BSSIDs on your wireless LAN, check the status of the standby unit when you add or delete BSSIDs on the monitored access point. If necessary, reconfigure the standby unit to use the BSSID’s new MAC address.
The MAC address of the monitored access point might change if a BSSID on the monitored unit is added or deleted. If you use multiple BSSIDs on your wireless LAN, check the status of the standby unit when you add or delete BSSIDs on the monitored access point. If necessary, reconfigure the standby unit to use the BSSID’s new MAC address.

Note![]() Hot standby is not supported on the BR1410 configured for AP mode.
Hot standby is not supported on the BR1410 configured for AP mode.
Configuring a Hot Standby Access Point
When you set up the standby access point, you must enter radio mac address of the access point that the standby unit will monitor. To monitor access points with two radios, you need both radios MAC addresses. Record the MAC address of the monitored access point before you configure the standby access point.
The standby access point also must duplicate several key settings on the monitored access point. These settings are:
- Primary SSID (as well as additional SSIDs configured on the monitored access point)
- Default IP Subnet Mask
- Default Gateway
- Data rates
- Security settings
- Authentication types and authentication servers
- Radios configuration and status
Check the monitored access point and record these settings before you set up the standby access point.

Note![]() Wireless client devices associated to the standby access point lose their connections during the hot standby setup process.
Wireless client devices associated to the standby access point lose their connections during the hot standby setup process.

Tip![]() To quickly duplicate the monitored access point’s settings on the standby access point, save the monitored access point configuration and load it on the standby access point. See “Working with Configuration Files,” for instructions on uploading and downloading configuration files.
To quickly duplicate the monitored access point’s settings on the standby access point, save the monitored access point configuration and load it on the standby access point. See “Working with Configuration Files,” for instructions on uploading and downloading configuration files.
Beginning in Privileged Exec mode, follow these steps to enable hot standby mode on an access point:
After you enable standby mode, configure the settings that you recorded from the monitored access point to match on the standby access point.
Verifying Standby Operation
Use this command to check the status of the standby access point:
This command displays the status of the standby access point. Table 19-2 lists the standby status messages that can appear.
Use this command to check the standby configuration:
This command displays the MAC address of the standby access point, the standby timeout, and the poll-frequency values. If no standby access point is configured, this message appears:
If a standby access point takes over for the monitored access point, you can use the show iapp statistics command to help determine the reason that the standby access point took over.
Understanding Workgroup Bridge Mode
You can configure access points as workgroup bridges, also termed as WGBs. In workgroup bridge (WGB) mode, the unit associates to another access point as a client and provides a network connection for the devices connected to its Ethernet port. For example, if you need to provide wireless connectivity for a group of network printers, you can connect the printers to a hub or to a switch, connect the hub or switch to the access point Ethernet port, and configure the access point as a workgroup bridge. The workgroup bridge associates to an access point on your network.
If your access point has two radios, either the 2.4-GHz radio or the 5-GHz radio can function in workgroup bridge mode. When you configure one radio interface as a workgroup bridge, the other radio remains up. However, both radios cannot be configured to operate simultaneously as a workgroup bridge. The other radio can either be disabled (shutdown), or be in root (access point or bridge), scanner, or spectrum mode.


Note![]() If multiple BSSIDs are configured on a root access point that is designated as the parent of a workgroup bridge, the parent MAC address might change if a BSSID on the parent is added or deleted. If you use multiple BSSIDs on your wireless LAN and a workgroup bridge on your wireless LAN is configured to associate to a specific parent, check the association status of the workgroup bridge when you add or delete BSSIDs on the parent access point. If necessary, reconfigure the workgroup bridge to use the BSSID’s new MAC address.
If multiple BSSIDs are configured on a root access point that is designated as the parent of a workgroup bridge, the parent MAC address might change if a BSSID on the parent is added or deleted. If you use multiple BSSIDs on your wireless LAN and a workgroup bridge on your wireless LAN is configured to associate to a specific parent, check the association status of the workgroup bridge when you add or delete BSSIDs on the parent access point. If necessary, reconfigure the workgroup bridge to use the BSSID’s new MAC address.

Note![]() Although it functions as a bridge, an access point in workgroup bridge mode has a limited radio range. Workgroup bridges do not support the distance setting, which enables you to configure wireless bridges to communicate across several kilometers.
Although it functions as a bridge, an access point in workgroup bridge mode has a limited radio range. Workgroup bridges do not support the distance setting, which enables you to configure wireless bridges to communicate across several kilometers.
Figure 19-2 shows an access point in workgroup bridge mode.
Figure 19-2 Access Point in Workgroup Bridge Mode

Treating Workgroup Bridges as Infrastructure Devices or as Client Devices
The access point to which a workgroup bridge associates can treat the workgroup bridge as an infrastructure device or as a simple client device. By default, access points and bridges treat workgroup bridges as client devices.
For increased reliability, you can configure access points and bridges to treat workgroup bridges not as client devices but as infrastructure devices, like access points or bridges. Treating a workgroup bridge as an infrastructure device means that the access point reliably delivers multicast packets, including Address Resolution Protocol (ARP) packets, to the workgroup bridge. You use the infrastructure-client configuration interface command to configure access points and bridges to treat workgroup bridges as infrastructure devices.
Configuring access points and bridges to treat a workgroup bridge as a client device allows more workgroup bridges to associate to the same access point, or to associate using an SSID that is not an infrastructure SSID. The performance cost of reliable multicast delivery—duplication of each multicast packet sent to each workgroup bridge—limits the number of infrastructure devices, including workgroup bridges, that can associate to an access point or bridge. To increase beyond 20 the number of workgroup bridges that can associate to the access point, the access point must reduce the delivery reliability of multicast packets to workgroup bridges. With reduced reliability, the access point cannot confirm whether multicast packets reach the intended workgroup bridge, so wired clients of workgroup bridges at the edge of the access point coverage area may not receive all multicast frames. When you treat workgroup bridges as client devices, you increase performance but reduce reliability. You use the no infrastructure client configuration interface command to configure access points and bridges to treat workgroup bridges as simple client devices. This is the default setting.
You should use a workgroup bridge as an infrastructure device if the devices connected to the workgroup bridge require network reliability equivalent to that of an access point or a bridge. You should use a workgroup bridge as a client device if these conditions are true:
- More than 20 workgroup bridges associate to the same access point or bridge
- The workgroup bridge associates using an SSID that is not an infrastructure SSID
- The workgroup bridge is mobile
Please notice that the (no) infrastructure client command is entered on the access point to which the workgroup bridge associates. This command determines whether the access point should add unicast copies of each multicast frames, sent in a reliable (unicast with acknowledgment) fashion to each workgroup bridge in the cell.
When infrastructure client is configured on the access point, each workgroup bridge potentially receives both the multicast initial frame and the unicast copy. Processing both frames (carrying the same upper layer content) creates processing inefficiency on the workgroup bridge. You can configure the workgroup bridge to consider the multicast frame and discard the unicast copy (default), or consider the unicast frame and discard the multicast original frame. To configure this behavior on the workgroup bridge radio, use the command station-role workgroup-bridge multicast mode {client | infrastructure}. The client option considers the multicast frame and discards the unicast copy. The infrastructure option echoes the Infrastructure Client configuration on the main access point, and sets the workgroup bridge to consider the unicast copies of multicast frames, and not process the multicast frames.
Configuring a Workgroup Bridge for Roaming
By default, workgroup bridges are expected to be static. Therefore, once they are associated to an access point SSID, they do not scan for other access points.
If your workgroup bridge is mobile, you can configure it to scan for a better radio connection to a parent access point or bridge. Use this command to configure the workgroup bridge as a mobile station:
When you enable this setting, the workgroup bridge scans for a new parent association when it encounters a poor Received Signal Strength Indicator (RSSI), excessive radio interference, or a high frame-loss percentage. Using these criteria, a workgroup bridge configured as a mobile station searches for a new parent association and roams to a new parent before it loses its current association. When the mobile station setting is disabled (the default setting) the workgroup bridge does not search for a new association until it loses its current association.
ap(config-if)# mobile station minimum-rate <data rate>
This is a configurable parameter to control when WGB triggers a new roaming event. If this cli is configured and if the current data rate is lower than the configured value, the new roaming process will be triggered. This will reduce unnecessary roaming and allows to have an expected rate value.
You can also configure the periodicity of scans. When the connection conditions deteriorate, the workgroup bridge scans for a better access point to connect to. If the scan does not allow the workgroup bridge to find a better connection point, use the mobile station period number-of-seconds command to determine the interval to the next scanning cycle.
Configuring a Workgroup Bridge for Limited Channel Scanning
In mobile environments such as railroads, a workgroup bridge instead of scanning all the channels will be restricted to scan only a set of limited channels in order to reduce the hand-off delay when the workgroup bridge roams from one access point to another. By limiting the number of channels the workgroup bridge scans to only those required, the mobile workgroup bridge achieves and maintains a continuous wireless LAN connection with fast and smooth roaming.
Configuring the Limited Channel Set
This limited channel set is configured using the mobile station scan <set of channels> CLI command to invoke scanning to all or specified channels. There is no limitation on the maximum number of channels that can be configured. The maximum number of channels that can be configured is restricted only by the number of channels a radio can support. When executed, the workgroup bridge only scans this limited channel set. This limited channel feature also affects the known channel list that the workgroup bridge receives from the access point to which it is currently associated. Channels are added to the known channel list only if they are also a part of the limited channel set.
The following example shows how the command is used. In the example, channels 1, 6, and 11 are specified to scan:
Use the no mobile station scan command to restore scanning to all the channels.
Ignoring the CCX Neighbor List
In addition, the workgroup bridge updates its known channel list using CCX reports such as the AP Adjacent report or Enhanced Neighbor List report. However, when a workgroup bridge is configured for limited channel scanning, it does not need to process the CCX reports to update its known channel list. Use the mobile station ignore neighbor-list command to disable processing of CCX neighbor list reports. This command is effective only if the workgroup bridge is configured for limited scanning channel scanning. The following example shows how this command is used
Configuring a Client VLAN
If the devices connected to the workgroup bridge’s Ethernet port should all be assigned to a particular VLAN, you can configure a VLAN for the connected devices. Enter this command on the workgroup bridge:
All the devices connected to the workgroup bridge’s Ethernet port are assigned to that VLAN.
Workgroup Bridge VLAN Tagging
The Workgroup-Bridge (WGB) VLAN tagging feature enables segregation of VLAN traffic based on the VLAN numbers for Unified WGB solution.
When this feature is enabled, the WGB removes the 802.1q header while sending the packet from a VLAN client to the wireless LAN controller (WLC). WGB gets the packet to a VLAN client without 802.1q header and WGB code has to be modified to add the 802.1q header while forwarding the frame to the switch behind WGB.
WGB updates the WLC with the wired-client VLAN information in the Internet Access Point Protocol (IAPP) Association message. WLC treats the WGB client as a VLAN-client and forwards the packet in the right VLAN interface based on the source-mac-address.
In the upstream direction, WGB removes the 802.1q header from the packet while sending to the WLC. In the downstream direction while forwarding the packet to the switch connecting the wired-client, the WLC sends the packet to WGB without the 802.1q tag and WGB adds a 4-byte 802.1q header based on the destination mac-address. (For detailed information on VLANs, refer to Chapter 14, “Configuring VLANs”.)
Enter this command to enable WGB VLAN tagging:
Configuring Workgroup Bridge Mode
Beginning in privileged EXEC mode, follow these steps to configure an access point as a workgroup bridge:
This example shows how to configure an access point as a workgroup bridge. In this example, the workgroup bridge uses the configured username and password to perform LEAP authentication, and the devices attached to its Ethernet port are assigned to VLAN 22:
This example shows how to set up a workgroup bridge with the parent access points, designated 1 and 2:
This example shows how to remove a parent, here parent 2, from the parent list:
This example shows how to set a timeout of 60 seconds for the parent list:
This example shows how to disable the timeout value for the parent list:
Using Workgroup Bridges in a Lightweight Environment
You can configure an access point to operate as a workgroup bridge so that it can provide wireless connectivity to a lightweight access point on behalf of clients that are connected by Ethernet to the workgroup bridge access point. A workgroup bridge connects to a wired network over a single wireless segment by learning the MAC address of its wired clients on the Ethernet interface and reporting them to the lightweight access point using Internet Access Point Protocol (IAPP) messaging. The workgroup bridge provides wireless access connectivity to wired clients by establishing a single connection to the lightweight access point. The lightweight access point treats the workgroup bridge as a wireless client.
Figure 19-3 Workgroup Bridge in a Lightweight Environment


Note![]() If the lightweight access point fails, the workgroup bridge attempts to associate to another access point.
If the lightweight access point fails, the workgroup bridge attempts to associate to another access point.
Guidelines for Using Workgroup Bridges in a Lightweight Environment
Follow these guidelines for using workgroup bridges on your lightweight network:
- The workgroup bridge can be any autonomous access point that supports the workgroup bridge mode and is running Cisco IOS Release JA or greater (on 32-MB access points) or Cisco IOS Release 12.3(8)JEB or greater (on 16-MB access points). These access points include the AP1040, AP1140, and AP1260. Cisco IOS Releases prior to 12.4(3g)JA and 12.3(8)JEB are not supported.

Note![]() If your access point has two radios, you can configure only one for workgroup bridge mode. This radio is used to connect to the lightweight access point. We recommend that you disable the second radio.
If your access point has two radios, you can configure only one for workgroup bridge mode. This radio is used to connect to the lightweight access point. We recommend that you disable the second radio.
Perform one of the following to enable the workgroup bridge mode on the workgroup bridge:
- On the workgroup bridge access point GUI, choose Workgroup Bridge for the role in radio network on the Network > Network Interfaces > Radio0-802.11N 2.4GHz / Radio1-802.11N 5GHz > Settings page.
Alternatively, on the WGB access point CLI radio configuration submode, enter this command: station-role workgroup-bridge - Only workgroup bridge in client mode (which is the default value) are supported. The lightweight access point will not relay multicast frames in a unicast fashion to associated workgroup bridges. Perform one of the following to enable client mode on the workgroup bridge:
–![]() On the radio configuration page, choose Disabled for the Reliable Multicast to workgroup bridge parameter.
On the radio configuration page, choose Disabled for the Reliable Multicast to workgroup bridge parameter.
–![]() From the radio configuration submode, enter this command: no infrastructure client.
From the radio configuration submode, enter this command: no infrastructure client.
–![]() Cisco Centralized Key Management (CCKM)
Cisco Centralized Key Management (CCKM)

Note![]() If a workgroup bridge associates to a web-authentication WLAN, the workgroup bridge is added to the exclusion list, and all of the workgroup bridge wired clients are deleted.
If a workgroup bridge associates to a web-authentication WLAN, the workgroup bridge is added to the exclusion list, and all of the workgroup bridge wired clients are deleted.
- In a mesh network, a workgroup bridge can associate to any mesh access point, regardless of whether it acts as a root access point or a mesh access point.
- Wired clients connected to the workgroup bridge are not authenticated for security. Instead, the workgroup bridge is authenticated against the access point to which it associates. Therefore, We recommend that you physically secure the wired side of the workgroup bridge.
- With Layer 3 roaming, if you connect a wired client into the workgroup bridge network after the workgroup bridge has roamed to another controller (for example, to a foreign controller), the wired client’s IP address displays only on the anchor controller, not on the foreign controller.
- When you delete a workgroup bridge record from the controller, all of the workgroup bridge wired clients’ records are also deleted.
- Wired clients connected to a workgroup bridge inherit the workgroup bridge’s QoS and AAA override attributes.
- These features are not supported for wired clients connected to a workgroup bridge:
- You do not need to configure anything on the controller to enable the workgroup bridge to communicate with the lightweight access point. However, to ensure proper communication, you should create a WLAN on the controller that matches the SSID and security method that was configured on the workgroup bridge.
Sample Workgroup Bridge Association Verification
To verify that the workgroup bridge is associated to an access point, enter this command on the workgroup bridge:
If a wired client does not send traffic for an extended period of time, the workgroup bridge removes the client from its bridge table, even if traffic is continuously being sent to the wired client. As a result, the traffic flow to the wired client fails. To avoid the traffic loss, prevent the wired client from being removed from the bridge table by configuring the aging-out timer on the workgroup bridge to a large value using the following IOS commands on the workgroup bridge:
where bridge-group-number is a value between 1 and 255, and seconds is a value between 10 and 1,000,000 seconds. We recommend configuring the seconds parameter to a value greater than the wired client’s idle period.
Enabling VideoStream Support on Workgroup Bridges
VideoStream improves the reliability of an IP multicast stream by converting the multicast frame, over the air, to a unicast frame. Cisco IOS Releases 15.2(2)JA and later provide VideoStream support for wired devices connected to workgroup bridges. For access points running release 15.2(2)JA and later, the workgroup bridge is added to the wireless LAN controller (WLC) multicast table, and the workgroup bridge converts the VideoStream unicast frame into an Ethernet multicast frame and sends it out to its wired clients.
Enter this command on the WLC to enable VideoStream for workgroup bridges:
Configuring Workgroup Bridges for High-Speed Roaming
Consider the wireless network deployments which involve high-speed roaming of a workgroup bridge AP, such as in high-speed rail coaches. As the coaches move, the workgroup bridge AP in the coach roams from one parent AP (or root AP) to the next one mounted along the railway track. Such a scenario can involve trains moving at about 100 km/h, with the parent APs placed about 200-300m apart along the track.
For such scenarios ensure that the following configurations are done.

Note![]() Configuring workgroup bridges for high-speed roaming scenarios is supported only on the Cisco Aironet 3600 and 3700 series, and the IW3700 series access points.
Configuring workgroup bridges for high-speed roaming scenarios is supported only on the Cisco Aironet 3600 and 3700 series, and the IW3700 series access points.
802.11v BSS Transition on the Wireless Controller
For high-speed roaming to work, on the wireless controller you must have 802.11v BSS Transition enabled. This allows for the workgroup bridge AP to request for and receive a neighbor list from the associated AP (i.e. the current parent AP). The workgroup bridge AP uses this list to identify the small set of channels on which it needs to scan to find the next parent AP.
Configuration on the WGB
To set how quickly a WGB detects that the current parent AP is suboptimal, while it is moving out of range, and that a roam needs to be initiated to discover the next parent AP, you can use the following command:
drssi roaming threshold value period value packet value neighlist-update-interval value
- DRSSI roaming threshold is the RSSI threshold value. APs with RSSI values above this threshold are not considered for associating with.
You are recommended to set the DRSSI roaming threshold to about 2 to 3 dBm below the average RSSI level in the middle point between two APs on the track. Note that a configured threshold of x, corresponding to -x dBm.
- Period controls how often the WGB decides to evaluate the quality of the link to the current parent. For example, if the train is moving very fast, you would like the WGB to evaluate the link quality more frequently. However if the speed is slow, the WGB can avoid frequent computations on evaluating the link quality.
- Packet is the threshold number of sample data packets from the current root AP that the WGB uses to keep track of the link quality with the AP. The WGB AP maintains a running average of the RSSI of the last received data packets from the root AP. If this running average falls below the threshold, the WGB initiates a roam. For example, if the train is moving very fast, a small number of samples can be used to decide when to switch.
- neighlist-update-interval is the time interval to update WGB neighbor list for roaming. It is used to trigger a periodic dot11v query to associated AP for that AP’s neighbor list. You can enter a value from 1 through 10000 in seconds. Default is 10 seconds.
As configured in the following example, a DRSSI roaming threshold value of 67, Period value of 1, and Packet value of 20 works well up to a speed of 100 km/h.
You can also set the workgroup bridge to scan only the neighbor list that is received from the last associated AP, using the following command:
drssi scan-only current-neighbor-list
You can also disable this above command so that the workgroup bridge ages out the neighbors list gradually - the age out factor is reduced by 1 for every roam. Default age is 2. To disable, use the command no drssi scan-only current-neighbor-list.

Note![]() You can configure roaming by using either the mobile station command, or the drssi command. Make sure that you do not configure both commands at the same time.
You can configure roaming by using either the mobile station command, or the drssi command. Make sure that you do not configure both commands at the same time.
Debug and Show commands
On the WGB, to view the current neighbor list table, use the following command:
show dot11 bss-trans neighbor-list
On the WGB, to enable debugging for 802.11v BSS transition:
debug dot11 dot11v {detail | errors | all}
Configuring Transparent Transporting of PROFINET Traffic
PROFINET is the PROFIBUS International (PI) open Industrial Ethernet Standard that uses TCP/IP and IT standards for automation control. PROFINET is particularly useful for industrial automation systems and process control networks. It emphasizes data exchange and defines communication paths to meet speed requirements.
PROFINET communication is scalable on three levels:
- Normal non-real-time communication uses TCP/IP and enables bus cycle times of approximately 100 ms. It is used for downloads, diagnostics, and management.
- Real-Time (RT): Real-time communication enables cycle times of approximately 10 ms. It is used to control traffic, time critical alarms and messaging. Real-time data are treated with a higher priority than TCP(UDP)/IP data. It uses the standard existing protocol components (using Ethernet with special frame etherType = 0x8892 and priority value in the VLAN tag) to achieve deterministic and cyclic data transfer.
- Isochronous Real-Time (IRT): Isochronous real-time communication enables cycle times of approximately 1 ms. The main focus of IRT is the ‘timing’ of the communication that requires precisely controlled communication. It is achieved using specialized hardware and the IEEE 1588-PTP protocol. IRT is out of the scope of this document.
PROFINET I/O is a modular communication framework for distributed automation applications. PROFINET I/O uses cyclic data transfer to exchange data, alarms, and diagnostic information with programmable controllers, input/output (I/O) devices, and other automation controllers (for example, motion controllers).
This feature implements the ability of transparent PROFINET RT traffic over wireless on the IW3700 Series. With this feature, PROFINET RT traffic, including PROFINET Class of Service (CoS) value, can be transparently relayed via Wi-Fi network.

Note![]() Both flexconnect mode and autonomous mode are supported for this feature.
Both flexconnect mode and autonomous mode are supported for this feature.
Figure 19-4 shows a topology of autonomous AP and WGB configuration.
Two vlans are configured on the autonomous AP. The native vlan (vlan 0) is used for the connection of autonomous AP. The PROFINET packets, between the IE Switch and autonomous AP, are transfered in vlan x. The wireless PROFINET traffic will be in the corresponding Access Category (AC) queue according to the CoS value. The WGB connects to the IO Device directly. The downstream is untagged, and the upstream uses vlan 0 to express the CoS priority.
Figure 19-4 Autonomous AP (root AP and WGB)
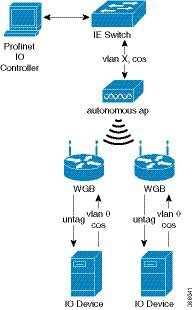
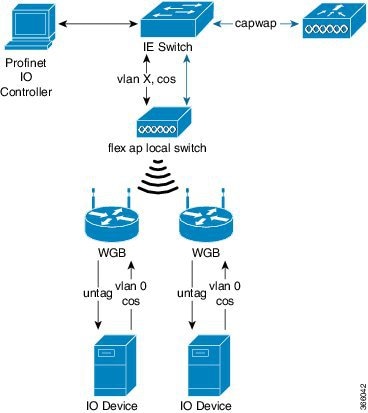
Figure 19-5 shows a topology of unified AP local switching configuration. The WLC communicates with the AP by capwap packets to exchange the control messages. The green lines and arrows are Profinet data flows. The black lines and arrows are capwap control packet flows.
Figure 19-5 Unified AP Local Switching
Configuration Examples
This section contains configuration examples for autonomous AP and WGB. In the following examples, native vlan 201 is used for control messages. Vlan 203 is used for Profinet.
Autonomous AP Configuration
Follow these steps to configure the autonomous AP:
Step 1![]() Create an ssid #Profinet in vlan 203.
Create an ssid #Profinet in vlan 203.
Step 2![]() Align the ssid #Profinet to dot11 5G.
Align the ssid #Profinet to dot11 5G.
WGB Configuration
Follow these steps to configure the WGB:
Step 1![]() Create the ssid #Profinet in the native vlan.
Create the ssid #Profinet in the native vlan.
Step 2![]() Align the ssid #Profinet to dot11.
Align the ssid #Profinet to dot11.
 Feedback
Feedback