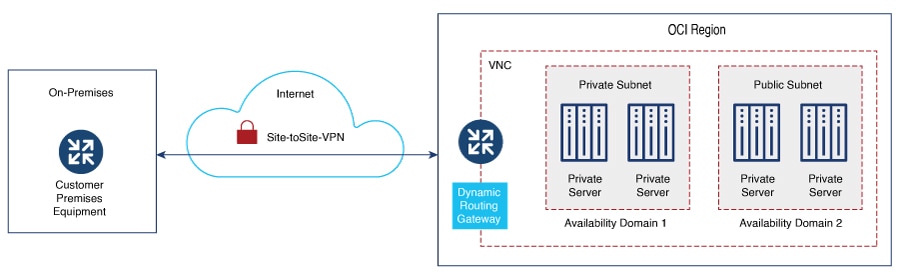
Installing Controller on Oracle Cloud Infrastructure
Cisco Catalyst Wireless Controller for Cloud on Oracle Cloud Infrastructure
The IOS XE based Cisco Catalyst Wireless Controller for Cloud (C9800-CL) sets the standard for Infrastructure as a Service (IaaS) secure wireless network services with Oracle Cloud Infrastructure (OCI). C9800-CL combines the advantages and flexibility of an OCI public cloud with the customization and feature-richness that customers usually experience on-prem deployments.
Scalability
C9800-CL scales up to x Access Points and y clients with features like Zero Touch AP provisioning, High Availability, Application Visibility and Control, and more. Here, x and y values depend on the capacity of the instance.
The following are the scale values for small, medium, and large instances:Small: 1000 APs and 10,000 clients
Medium: 3000 APs and 32,000 clients
Large: 6000 APs and 64,000 clients
OCI Compute Instances
OCI Compute service helps you provision and control the compute hosts, referred to as instances. You can create instances according to your specific compute and application needs.
When you create an instance, you can
-
securely connect to it from your own computer
-
reboot it
-
connect and disconnect storage volumes, and
-
shut it down permanently when it is no longer needed.
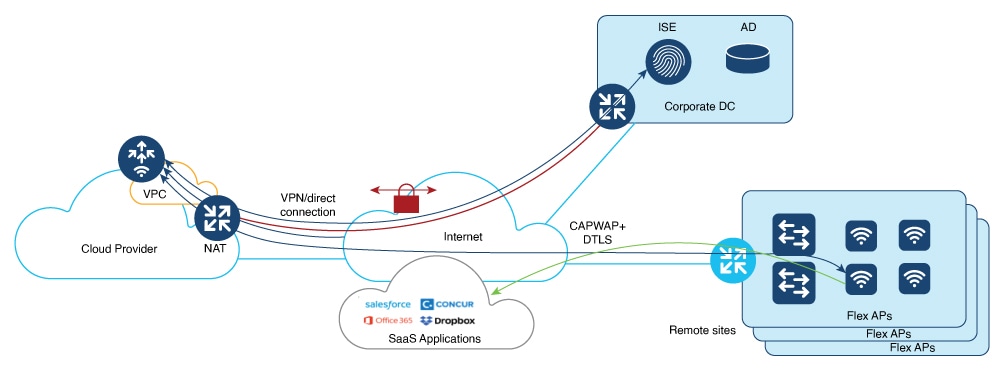
Supported Cloud Deployment Scenarios
The Cisco Catalyst Wireless Controller for Cloud supports the following deployment scenario:
-
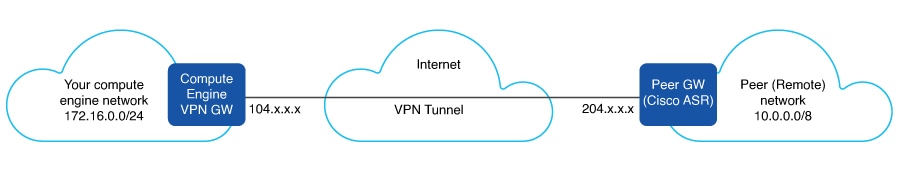
Virtual Private Network (VPN) between the AP locations and the Public Cloud
-
Connect directly to the Public IP of the controller in the cloud

 Feedback
Feedback