- Preface
- Chapter 1: Overview
- Chapter 2: Getting Started
- Chapter 3: Configuring Security Solutions
- Chapter 4: Performing System Tasks
- Chapter 5: Adding and Using Maps
- Chapter 6: Monitoring Wireless Devices
- Chapter 7: Managing WCS User Accounts
- Chapter 8: Configuring Mobility Groups
- Chapter 9: Configuring Access Points
- Chapter 10: Configuring Controllers and Switches
- Chapter 11: Managing Clients
- Chapter 12: Using Templates
- Chapter 13: Mobility Services
- Chapter 14: Performing Maintenance Operations
- Chapter 15: Configuring Hybrid REAP
- Chapter 16: Alarms and Events
- Chapter 17: Running Reports
- Chapter 18: Administrative Tasks
- Chapter 19: Tools Menu
- Chapter 20: Virtual Domains
- Chapter 21: Google Earth Maps
- Appendix A: Troubleshooting and Best Practices
- Appendix B: WCS and End User Licenses
- Appendix C: Conversion of a WLSE Autonomous Deployment to a WCS Controller Deployment
- Index
Administrative Tasks
This chapter describes administrative tasks to perform with Cisco WCS. It contains the following sections:
•![]() Turning Password Rules On or Off
Turning Password Rules On or Off
•![]() Performing Data Management Tasks
Performing Data Management Tasks
Running Background Tasks
Choose Administration > Background Tasks to view several scheduled tasks. The Background Tasks page appears (see Figure 18-1).
Figure 18-1 Background Tasks Page

You can view the administrative and operating status, task interval, and time of day in which the task occurs. To execute a particular task, click the check box of the desired task and choose Execute Now from the Select a command drop-down list. The task executes based on what you have configured for the specific task.
Performing a Task
Follow these steps to perform a task (such as scheduling an automatic backup of the WCS database). Data collection tasks are data-set tasks that collect and organize information that may be useful for creating reports.

Note ![]() All tasks related to collecting data or any other background task would be handled in a similar manner.
All tasks related to collecting data or any other background task would be handled in a similar manner.
Step 1 ![]() Choose Administration > Background Tasks to display the Background Tasks page (see Figure 18-1). This page displays the following information:
Choose Administration > Background Tasks to display the Background Tasks page (see Figure 18-1). This page displays the following information:
•![]() Enabled—Whether the tasks have been enabled or disabled.
Enabled—Whether the tasks have been enabled or disabled.
•![]() Interval—Indicates the time period (in minutes) between task executions. You can set the interval from the task's data collection configuration page.
Interval—Indicates the time period (in minutes) between task executions. You can set the interval from the task's data collection configuration page.
•![]() Status—The present state of the task.
Status—The present state of the task.
•![]() Data Aggregation (Data Collection Tasks only)—If set to Yes, the data set combines data.
Data Aggregation (Data Collection Tasks only)—If set to Yes, the data set combines data.
•![]() Non-Aggregation Data Retain Period (Days) (Data Collection Tasks only)—The number of days that the non-aggregated data is retained. You can set the retention period from the task's data collection configuration page.
Non-Aggregation Data Retain Period (Days) (Data Collection Tasks only)—The number of days that the non-aggregated data is retained. You can set the retention period from the task's data collection configuration page.
•![]() Last Execution Time—The time and date when the task was last run.
Last Execution Time—The time and date when the task was last run.
•![]() Last Execution Status—The status after the last task was run.
Last Execution Status—The status after the last task was run.
Step 2 ![]() On this page, perform one of the following:
On this page, perform one of the following:
•![]() Execute the task now.
Execute the task now.
Click the check box of the task you want to execute. From the Select a command drop-down list, choose Execute Now, and click Go.
•![]() Enable the task.
Enable the task.
Click the check box of the task you want to enable. From the Select a command drop-down list, choose Enable Task, and click Go. The task changes from unavailable to active after enabling is complete.
•![]() Disable the task.
Disable the task.
Click the check box of the task you want to disable. From the Select a command drop-down list, choose Disable Task, and click Go. The task is grayed out after the disabling is complete.
•![]() View details of a task.
View details of a task.
Click a URL in the Data Collection Tasks or Other Background Tasks column to view a specific task. The details on that task appear. Data collections are data-set tasks that collect and organize a specific type of information useful for creating reports.
To go to a data set's configuration page, click the name of the data set in the Data Collection page. Each data set configuration page displays a table of the data set's executions. The table has following columns:
•![]() Executed task information including:
Executed task information including:
–![]() Last Execution Start Time—Indicates the date and time that the data-set task began running.
Last Execution Start Time—Indicates the date and time that the data-set task began running.
–![]() End Time—Indicates the date and time that the data-set task stopped running.
End Time—Indicates the date and time that the data-set task stopped running.
–![]() Elapsed Time (secs)—Indicates the amount of time (in seconds) it took to complete the task.
Elapsed Time (secs)—Indicates the amount of time (in seconds) it took to complete the task.
–![]() Result—Indicates the success or failure of the task.
Result—Indicates the success or failure of the task.
–![]() Additional Information—Provides any additional information regarding a specific task.
Additional Information—Provides any additional information regarding a specific task.
Each data set configuration page contains the following parameters and information under Collection Set Details:
•![]() Description—Provides a brief read-only description of the data set.
Description—Provides a brief read-only description of the data set.
•![]() Data Aggregation—Indicates whether or not data collected by the data set is aggregated.
Data Aggregation—Indicates whether or not data collected by the data set is aggregated.
•![]() Used By Report(s)—Displays names of the reports that use the data set.
Used By Report(s)—Displays names of the reports that use the data set.
–![]() CleanAir Air Quality—This data set is used for Worst Air Quality APs and Air Quality versus Time reports.
CleanAir Air Quality—This data set is used for Worst Air Quality APs and Air Quality versus Time reports.
–![]() Interferers—This data set us used for Worst Interferers reports.
Interferers—This data set us used for Worst Interferers reports.
•![]() Collection Status—Select the Enabled check box to enable data collection.
Collection Status—Select the Enabled check box to enable data collection.
•![]() Interval (min.)—Enter the time (in minutes) for the data set execution interval.
Interval (min.)—Enter the time (in minutes) for the data set execution interval.
Each data set configuration page contains the following parameters under Data Management:
•![]() Non-Aggregation Data Retain Period (Days)—Enter the number of days to retain non-aggregated data collected by the data set.
Non-Aggregation Data Retain Period (Days)—Enter the number of days to retain non-aggregated data collected by the data set.
•![]() Retain Aggregation Raw Data—Select the Enable check box to enable the retention of aggregated raw data.
Retain Aggregation Raw Data—Select the Enable check box to enable the retention of aggregated raw data.

Note ![]() The Aggregation Raw Data Retain Period setting is for polled raw data. To configure the retention period for aggregated trend data, go to Administration > Settings, then click Data Management from the left sidebar.
The Aggregation Raw Data Retain Period setting is for polled raw data. To configure the retention period for aggregated trend data, go to Administration > Settings, then click Data Management from the left sidebar.

Note ![]() See "WCS Historical Data" section for more information on aggregated and non-aggregated data.
See "WCS Historical Data" section for more information on aggregated and non-aggregated data.

Note ![]() For this example, performing a WCS server backup was selected as the task. The screens and fields to enter on the detailed screens vary based on the task you choose.
For this example, performing a WCS server backup was selected as the task. The screens and fields to enter on the detailed screens vary based on the task you choose.
Step 3 ![]() Select the Enabled check box to enable it.
Select the Enabled check box to enable it.
Step 4 ![]() Select the Report History Backup check box.
Select the Report History Backup check box.
Step 5 ![]() In the Max Backups to Keep text box, enter the maximum number of backup files to save on the server.
In the Max Backups to Keep text box, enter the maximum number of backup files to save on the server.
Range: 7 to 50
Default: 7

Note ![]() To prevent the WCS platform from running out of disk space, the server automatically deletes old backup files when the number of files exceeds the value entered for this text box.
To prevent the WCS platform from running out of disk space, the server automatically deletes old backup files when the number of files exceeds the value entered for this text box.
Step 6 ![]() In the Interval (Days) text box, enter the number of days between each backup. For example, 1 = a daily backup, 2 = a backup every other day, 7 = a weekly backup, and so on.
In the Interval (Days) text box, enter the number of days between each backup. For example, 1 = a daily backup, 2 = a backup every other day, 7 = a weekly backup, and so on.
Range: 1 to 360
Default: 7
Step 7 ![]() In the Time of Day text box, enter the back-up start time. It must be in this format: hh:mm AM/PM (for example: 03:00 AM). If no AM/PM notation is designated, the entered hour is always AM. If you want to specify 5PM, you could enter 17:00 or 5:00 PM. When the page is revisited after saving, the time is display as hh:mm (in this case 17:00), without the PM designation.
In the Time of Day text box, enter the back-up start time. It must be in this format: hh:mm AM/PM (for example: 03:00 AM). If no AM/PM notation is designated, the entered hour is always AM. If you want to specify 5PM, you could enter 17:00 or 5:00 PM. When the page is revisited after saving, the time is display as hh:mm (in this case 17:00), without the PM designation.

Note ![]() Backing up a large database affects the performance of the WCS server. Therefore, Cisco recommends that you schedule backups to run when the WCS server is idle (such as, in the middle of the night).
Backing up a large database affects the performance of the WCS server. Therefore, Cisco recommends that you schedule backups to run when the WCS server is idle (such as, in the middle of the night).
Step 8 ![]() Click Submit to save your settings. The backup file is saved as a .zip file in the ftp-install-dir/ftp-server/root/WCSBackup directory using this format: dd-mmm-yy_ hh-mm-ss.zip
Click Submit to save your settings. The backup file is saved as a .zip file in the ftp-install-dir/ftp-server/root/WCSBackup directory using this format: dd-mmm-yy_ hh-mm-ss.zip
(for example, 11-Nov-05_10-30-00.zip).
Configuration Sync
Configuration sync is a new task added in software release 5.1. It allows you to poll all configuration data from the controllers. Any audit (such as a network audit, security index calculation, or RRM audit) performed on the polled and database data is secondary to the configuration sync and can only be performed if this configuration sync task is enabled.
Each of the audits can be enabled separately and run independently of the other audits. If a particular audit requires an immediate run, it can be enabled when the Configuration Sync task is run.

Note ![]() If you plan to run the configuration sync task daily, you should enable all audits.
If you plan to run the configuration sync task daily, you should enable all audits.
Follow these steps to perform a configuration sync.
Step 1 ![]() Choose Administration > Background Tasks to display the Background Tasks page (see Figure 18-1).
Choose Administration > Background Tasks to display the Background Tasks page (see Figure 18-1).
Step 2 ![]() On this page, perform one of the following:
On this page, perform one of the following:
•![]() Execute the task now.
Execute the task now.
Click the Configuration Sync check box. From the Select a command drop-down list, choose Execute Now, and click Go. You see the status change in the Enabled column.
<OR>
•![]() Enable the task.
Enable the task.
Click the Configuration Sync check box. From the Select a command drop-down list, choose Enable Task, and click Go. The task converts from grayed out to active in the Enabled column.
<OR>
•![]() Disable the task.
Disable the task.
Click the Configuration Sync check box. From the Select a command drop-down list, choose Disable Task, and click Go. The task is grayed out in the Enabled column after the disabling is complete.
Step 3 ![]() To modify the task, click the Configuration Sync link in the Background Tasks column. The Task > Configuration Sync page appears (see Figure 18-2).
To modify the task, click the Configuration Sync link in the Background Tasks column. The Task > Configuration Sync page appears (see Figure 18-2).
Figure 18-2 Task > Configuration Sync

Step 4 ![]() In this page you can set the interval and time of day for the task and enable the secondary network audit, security index calculation, and RRM audits tasks.
In this page you can set the interval and time of day for the task and enable the secondary network audit, security index calculation, and RRM audits tasks.
Step 5 ![]() Click Submit.
Click Submit.
Controller License Status
Controller license status is available from release 6.0 or later. It resets the controller license file state so that WCS shows correct information.
Follow these steps to update the controller license status.
Step 1 ![]() Choose Administration > Background Tasks to display the Background Tasks page (see Figure 18-1).
Choose Administration > Background Tasks to display the Background Tasks page (see Figure 18-1).
Step 2 ![]() On this page, perform one of the following:
On this page, perform one of the following:
•![]() Execute the task now.
Execute the task now.
Click the Controller License Status check box. From the Select a command drop-down list, choose Execute Now, and click Go. You see the status change in the Enabled column.
<OR>
•![]() Enable the task.
Enable the task.
Click the Controller License Status check box. From the Select a command drop-down list, choose Enable Task, and click Go. The task converts from grayed out to active in the Enabled column.
<OR>
•![]() Disable the task.
Disable the task.
Click the Controller License Status check box. From the Select a command drop-down list, choose Disable Task, and click Go. The task converts from grayed out to active in the Enabled column after the disabling is complete.
Step 3 ![]() To modify the controller license reset task, click the Controller License Status link in the Background Tasks column. The Controller License Status page appears (see Figure 18-3).
To modify the controller license reset task, click the Controller License Status link in the Background Tasks column. The Controller License Status page appears (see Figure 18-3).
Figure 18-3 Controller License Status Page

This page shows when the latest license resynchronizations occurred. By default, it runs every 4 hours. From this page, you can disable this task or change the interval.
WCS Historical Data
There are two types of historical data in WCS, including:
•![]() Aggregated historical data—Numeric data that can be gathered as a whole and aggregated to minimum, maximum, or average. Client count is one example of aggregated historical data.
Aggregated historical data—Numeric data that can be gathered as a whole and aggregated to minimum, maximum, or average. Client count is one example of aggregated historical data.
Use the Administration > Settings > Data Management page to define the aggregated data retention period. Aggregation types include hourly, daily, and weekly.
The retention period for these aggregation types are defined as Default, Minimum, and Maximum (see Table 18-1).
|
|
|
|
|
|---|---|---|---|
Hourly |
31 days |
1 day |
31 days |
Daily |
90 days |
7 days |
365 days |
Weekly |
54 weeks |
2 weeks |
108 weeks |
•![]() Non-aggregated historical data—Numeric data that cannot be gathered as a whole (or aggregated). Client association history is one example of non-aggregated historical data.
Non-aggregated historical data—Numeric data that cannot be gathered as a whole (or aggregated). Client association history is one example of non-aggregated historical data.
You can define a non-aggregated retention period in each data collection task and other settings.
For example, you define the retention period for client association history in Administration > Settings > Client. By default, the retention period is 31 days or 1 million records. This retention period can be increased to 365 days.
Importing Tasks Into ACS
To import tasks into Cisco Secure ACS server, you must add WCS to an ACS server (or non-Cisco ACS server).
Adding WCS to an ACS Server
Follow these steps to add WCS to an ACS server.

Note ![]() The instructions and illustrations in this section pertain to ACS version 4.1 and may vary slightly for other versions or other vendor types. See the CiscoSecure ACS documentation or the documentation for the vendor you are using.
The instructions and illustrations in this section pertain to ACS version 4.1 and may vary slightly for other versions or other vendor types. See the CiscoSecure ACS documentation or the documentation for the vendor you are using.
Step 1 ![]() Click Add Entry on the Network Configuration page of the ACS server (see Figure 18-4).
Click Add Entry on the Network Configuration page of the ACS server (see Figure 18-4).
Figure 18-4 ACS Server Network Configuration Page
.

Step 2 ![]() In the AAA Client Hostname text box, enter the WCS hostname.
In the AAA Client Hostname text box, enter the WCS hostname.
Step 3 ![]() Enter the WCS IP address into the AAA Client IP Address text box.
Enter the WCS IP address into the AAA Client IP Address text box.
Step 4 ![]() In the Key text box, enter the shared secret that you wish to configure on both the WCS and ACS servers.
In the Key text box, enter the shared secret that you wish to configure on both the WCS and ACS servers.
Step 5 ![]() Choose TACACS+ in the Authenticate Using drop-down list.
Choose TACACS+ in the Authenticate Using drop-down list.
Step 6 ![]() Click Submit + Apply.
Click Submit + Apply.
Adding WCS as a TACACS+ Server
Follow these steps to add WCS to a TACACS+ server.
Step 1 ![]() Go to the TACACS+ (Cisco IOS) Interface Configuration page (see Figure 18-5).
Go to the TACACS+ (Cisco IOS) Interface Configuration page (see Figure 18-5).
Figure 18-5 TACACS+ Cisco IOS Interface Configuration Page

Step 2 ![]() In the New Services portion of the page, add Wireless-WCS in the Service column heading.
In the New Services portion of the page, add Wireless-WCS in the Service column heading.
Step 3 ![]() Enter HTTP in the Protocol column heading.
Enter HTTP in the Protocol column heading.

Note ![]() HTTP must be in uppercase.
HTTP must be in uppercase.
Step 4 ![]() Click the check box in front of these entries to enable the new service and protocol.
Click the check box in front of these entries to enable the new service and protocol.
Step 5 ![]() Click Submit.
Click Submit.
Adding WCS UserGroups into ACS for TACACS+
Follow these steps to add WCS UserGroups into an ACS Server for use with TACACS+ servers.
Step 1 ![]() Log into WCS.
Log into WCS.
Step 2 ![]() Choose Administration > AAA > Groups. The All Groups page appears (see Figure 18-6).
Choose Administration > AAA > Groups. The All Groups page appears (see Figure 18-6).
Figure 18-6 All Groups Page

Step 3 ![]() Click the Task List URL (the Export right-most column) of the User Group that you wish to add to ACS. The Export Task List page appears (see Figure 18-7).
Click the Task List URL (the Export right-most column) of the User Group that you wish to add to ACS. The Export Task List page appears (see Figure 18-7).
Figure 18-7 Export Task List Page

Step 4 ![]() Highlight the text inside of the TACACS+ Custom Attributes, go to your browser's menu, and choose Edit > Copy.
Highlight the text inside of the TACACS+ Custom Attributes, go to your browser's menu, and choose Edit > Copy.
Step 5 ![]() Log in to ACS.
Log in to ACS.
Step 6 ![]() Go to Group Setup. The Group Setup page appears (see Figure 18-8).
Go to Group Setup. The Group Setup page appears (see Figure 18-8).
Figure 18-8 Group Setup Page on ACS Server

Step 7 ![]() Choose which group to use and click Edit Settings. Wireless-WCS HTTP appears in the TACACS+ setting.
Choose which group to use and click Edit Settings. Wireless-WCS HTTP appears in the TACACS+ setting.
Step 8 ![]() Use your browser's Edit > Paste sequence to place the TACACS+ custom attributes from WCS into this text box.
Use your browser's Edit > Paste sequence to place the TACACS+ custom attributes from WCS into this text box.

Note ![]() When you upgrade WCS, any permissions on the TACACS+ or RADIUS server must be re-added.
When you upgrade WCS, any permissions on the TACACS+ or RADIUS server must be re-added.
Step 9 ![]() Click the check boxes to enable these attributes.
Click the check boxes to enable these attributes.
Step 10 ![]() Click Submit + Restart.
Click Submit + Restart.
You can now associate ACS users with this ACS group.

Note ![]() To enable TACACS+ in WCS, refer to the "Configuring TACACS+ Servers" section. For information on configuring ACS view server credentials, refer to the "Configuring ACS View Server Credentials" section. For information on adding WCS Virtual Domains into ACS for TACACS+, refer to the "Virtual Domain RADIUS and TACACS+ Attributes" section.
To enable TACACS+ in WCS, refer to the "Configuring TACACS+ Servers" section. For information on configuring ACS view server credentials, refer to the "Configuring ACS View Server Credentials" section. For information on adding WCS Virtual Domains into ACS for TACACS+, refer to the "Virtual Domain RADIUS and TACACS+ Attributes" section.
Adding WCS to ACS server for Use with RADIUS
Follow these steps to add WCS to an ACS server for use with RADIUS servers. If you have a non-Cisco ACS server, refer to the "Adding WCS to a Non-Cisco ACS Server for Use with RADIUS" section.
Step 1 ![]() Go to Network Configuration on the ACS server (see Figure 18-9).
Go to Network Configuration on the ACS server (see Figure 18-9).
Figure 18-9 Network Configuration Page on ACS Server

Step 2 ![]() Click Add Entry.
Click Add Entry.
Step 3 ![]() In the AAA Client Hostname text box, enter the WCS hostname.
In the AAA Client Hostname text box, enter the WCS hostname.
Step 4 ![]() In the AAA Client IP Address text box, enter the WCS IP address.
In the AAA Client IP Address text box, enter the WCS IP address.
Step 5 ![]() In the Key text box, enter the shared secret that you wish to configure on both the WCS and ACS servers.
In the Key text box, enter the shared secret that you wish to configure on both the WCS and ACS servers.
Step 6 ![]() Choose RADIUS (Cisco IOS/PIX 6.0) from the Authenticate Using drop-down list.
Choose RADIUS (Cisco IOS/PIX 6.0) from the Authenticate Using drop-down list.
Step 7 ![]() Click Submit + Apply.
Click Submit + Apply.
You can now associate ACS users with this ACS group.

Note ![]() To enable RADIUS in WCS, refer to the "Configuring RADIUS Servers" section. For information on configuring ACS view server credentials, refer to the "Configuring ACS View Server Credentials" section.
To enable RADIUS in WCS, refer to the "Configuring RADIUS Servers" section. For information on configuring ACS view server credentials, refer to the "Configuring ACS View Server Credentials" section.
Adding WCS UserGroups into ACS for RADIUS
Follow these steps to add WCS UserGroups into an ACS Server for use with RADIUS servers.
Step 1 ![]() Log into WCS.
Log into WCS.
Step 2 ![]() Choose Administration > AAA > Groups. The All Groups page appears (see Figure 18-10).
Choose Administration > AAA > Groups. The All Groups page appears (see Figure 18-10).
Figure 18-10 All Groups Page

Step 3 ![]() Click the Task List URL (the Export right-most column) of the User Group that you wish to add to ACS. The Export Task List page appears (see Figure 18-11).
Click the Task List URL (the Export right-most column) of the User Group that you wish to add to ACS. The Export Task List page appears (see Figure 18-11).
Figure 18-11 Export Task List Page

Step 4 ![]() Highlight the text inside of the RADIUS Custom Attributes, go to your browser's menu, and choose Edit > Copy.
Highlight the text inside of the RADIUS Custom Attributes, go to your browser's menu, and choose Edit > Copy.

Note ![]() When you upgrade WCS, any permissions on the TACACS+ or RADIUS server must be re-added.
When you upgrade WCS, any permissions on the TACACS+ or RADIUS server must be re-added.
Step 5 ![]() Log in to ACS.
Log in to ACS.
Step 6 ![]() Go to Group Setup. The Group Setup page appears (see Figure 18-12).
Go to Group Setup. The Group Setup page appears (see Figure 18-12).
Figure 18-12 Group Setup Page on ACS Server

Step 7 ![]() Choose which group to use and click Edit Settings. Find [009\001]cisco-av-pair under Cisco IOS/PIX 6.x RADIUS Attributes.
Choose which group to use and click Edit Settings. Find [009\001]cisco-av-pair under Cisco IOS/PIX 6.x RADIUS Attributes.
Step 8 ![]() Use your browser's Edit > Paste sequence to place the RADIUS custom attributes from WCS into this text box.
Use your browser's Edit > Paste sequence to place the RADIUS custom attributes from WCS into this text box.

Note ![]() When you upgrade WCS, any permissions on the TACACS+ or RADIUS server must be re-added.
When you upgrade WCS, any permissions on the TACACS+ or RADIUS server must be re-added.
Step 9 ![]() Click the check boxes to enable these attributes.
Click the check boxes to enable these attributes.
Step 10 ![]() Click Submit + Restart.
Click Submit + Restart.
You can now associate ACS users with this ACS group.

Note ![]() To enable RADIUS in WCS, refer to the "Configuring RADIUS Servers" section. For information on configuring ACS view server credentials, refer to the "Configuring ACS View Server Credentials" section.
To enable RADIUS in WCS, refer to the "Configuring RADIUS Servers" section. For information on configuring ACS view server credentials, refer to the "Configuring ACS View Server Credentials" section.
Adding WCS to a Non-Cisco ACS Server for Use with RADIUS
When you use a RADIUS server to log into WCS, the AAA server sends back an access=accept message with a usergroup and a list of available tasks, after the username and password were verified. The access=accept message comes back as a fragmented packet because of the large number of tasks in some user groups. You can look in the following file to see the tasks associated with a given user group: C:\Program Files\WCS5.0\webnms\webacs\WEB-INF\security\usergroup-map.xml. The tasks are passed back as a vendor specific attribute (VSA), and WCS requires authorization information using the VSA (IETF RADIUS attribute number 26). The VSA contains the WCS RADIUS task list information (refer to Figure 18-13).
Figure 18-13 Extracting Task List

The content of the VSA is as follows:
•![]() Type = 26 (IETF VSA number)
Type = 26 (IETF VSA number)
•![]() Vendor Id = 9 (Cisco vendor ID)
Vendor Id = 9 (Cisco vendor ID)
•![]() Vendor Type = 1 (Custom attributes)
Vendor Type = 1 (Custom attributes)
•![]() Vendor Data = The WCS task information (for example Wireless-WCS: task0 = Users and Group)
Vendor Data = The WCS task information (for example Wireless-WCS: task0 = Users and Group)
Each line from the WCS RADIUS task list should be sent in its own RADIUS VSA.
In the data portion of the access=access packet, the truncated output sometimes shows only one role sent back for an Admin user group login. The tasks associated with the role start with task0 and increment with task1, task2, and so on. Table 18-2 defines what these attributes in the access=access packet example signify.
0000 06 6d 0e 59 07 3d 6a 24 02 47 07 35 d2 12 a4 eb .m.Y.=j$G.5...
0010 a2 5a fa 84 38 20 e4 e2 3a 3a bc e5 1a 20 00 00 .Z..8..::..
0020 00 09 01 1a 57 69 72 65 6c 65 73 73 2d 57 43 53 ....Wireless-WCS
0030 3a 72 6f 6c 65 30 3d 41 64 6d 69 6e 1a 2b 00 00 :role0=Admin.+...
0040 00 09 01 25 57 69 72 65 6c 65 73 73 2d 57 43 53 ...%Wireless-WCS
0050 3a 74 61 73 6b 30 3d 55 73 65 72 73 20 61 6e 64 :task0=Users and
0060 20 47 72 6f 75 70 73 1a 27 00 00 00 09 01 21 57 Groups."....!W
0070 69 72 65 6c 65 73 73 2d 57 43 53 3a 74 61 73 6b Wireless-WCS:task
0080 31 3d 41 75 64 69 74 20 54 72 61 69 6c 73 xx xx 1=Audit Trails.*
To troubleshoot, perform the following steps:
•![]() Verify if the RADIUS packet is an access accept.
Verify if the RADIUS packet is an access accept.
•![]() Verify the task names for the user group in the access accept.
Verify the task names for the user group in the access accept.
•![]() Look at the different length fields in the RADIUS packet.
Look at the different length fields in the RADIUS packet.
Setting AAA Mode
Follow these steps to choose a AAA mode.
Step 1 ![]() Choose Administration > AAA.
Choose Administration > AAA.
Step 2 ![]() Choose AAA Mode from the left sidebar menu. The AAA Mode Setting page appears (see Figure 18-14).
Choose AAA Mode from the left sidebar menu. The AAA Mode Setting page appears (see Figure 18-14).
Figure 18-14 AAA Mode Settings Page

Step 3 ![]() Choose which AAA mode you want to use. Only one can be selected at a time.
Choose which AAA mode you want to use. Only one can be selected at a time.
Any changes to local user accounts are effective only when you are configured for local mode (the default). If you use remote authentication, changes to the credentials are made on a remote server. The two remote authentication types are RADIUS and TACACS+. RADIUS requires separate credentials for different locations (East and West Coast). TACACS+ is an effective and secure management framework with a built-in failover mechanism.
Step 4 ![]() Select the Enable Fallback to Local check box if you want the administrator to use the local database when the external AAA server is down.
Select the Enable Fallback to Local check box if you want the administrator to use the local database when the external AAA server is down.

Note ![]() This option is unavailable if Local was selected as a AAA mode type.
This option is unavailable if Local was selected as a AAA mode type.
Step 5 ![]() Click OK.
Click OK.
Auto Provisioning
Auto provisioning allows WCS to automatically configure a new or replace a current wireless LAN controller (WLC). The WCS auto provisioning feature can simplify deployments for customers with a large number of controllers.

Note ![]() For Auto Provisioning privileges, you must have Admin, Root, or SuperUser status.
For Auto Provisioning privileges, you must have Admin, Root, or SuperUser status.

Note ![]() To allow or disallow a user Auto Provisioning privileges, edit the permitted tasks using the Administration > AAA > Groups > group name > List of Tasks Permitted section of WCS. Select or unselect the check box to allow or disallow these privileges.
To allow or disallow a user Auto Provisioning privileges, edit the permitted tasks using the Administration > AAA > Groups > group name > List of Tasks Permitted section of WCS. Select or unselect the check box to allow or disallow these privileges.

Note ![]() As part of the initial configuration of a device, WCS sets the SNMP switch location attribute to a default value. When the device reboots, WCS verifies this attribute. If it has a default value, the device configuration is not erased and auto provisioning is not required for this device. If the SNMP switch location attribute is blank, the device configuration is considered to be erased or the device may be replaced. Auto provisioning is required for this device.
As part of the initial configuration of a device, WCS sets the SNMP switch location attribute to a default value. When the device reboots, WCS verifies this attribute. If it has a default value, the device configuration is not erased and auto provisioning is not required for this device. If the SNMP switch location attribute is blank, the device configuration is considered to be erased or the device may be replaced. Auto provisioning is required for this device.

Note ![]() A controller radio and b/g networks are initially disabled by the WCS downloaded startup configuration file. If desired, you may turn on those radio networks by using a template, which should be included as one of the automated templates.
A controller radio and b/g networks are initially disabled by the WCS downloaded startup configuration file. If desired, you may turn on those radio networks by using a template, which should be included as one of the automated templates.

Note ![]() To specify the Auto Provision filter contents, you can directlyenter the details in the application or import the details from a CSV file. The auto provisioning feature supports the 5500 and non-5500 series of controllers. The non-5500 series controllers have AP manager interface configuration information defined, whereas 5500 controllers do not have this information.
To specify the Auto Provision filter contents, you can directlyenter the details in the application or import the details from a CSV file. The auto provisioning feature supports the 5500 and non-5500 series of controllers. The non-5500 series controllers have AP manager interface configuration information defined, whereas 5500 controllers do not have this information.
To access the Auto Provisioning feature, choose Configure > Controller Auto Provisioning.
•![]() Auto Provisioning Device Management (Auto Provisioning Filter List)—Allows you to create and edit auto provisioning filters which define the list of allowable devices to be auto provisioned or auto monitored by WCS.
Auto Provisioning Device Management (Auto Provisioning Filter List)—Allows you to create and edit auto provisioning filters which define the list of allowable devices to be auto provisioned or auto monitored by WCS.
•![]() Auto Provisioning Setting (Auto Provisioning Primary Search Key Setting)—Provides the ability to set the matching criteria search order.
Auto Provisioning Setting (Auto Provisioning Primary Search Key Setting)—Provides the ability to set the matching criteria search order.
Auto Provisioning Device Management (Auto Provisioning Filter List)
This feature allows you to create and edit auto provisioning filters which define the list of allowable devices to be auto provisioned or auto monitored by WCS.
Filter parameters include:
•![]() Filter Name—Identifies the name of the filter.
Filter Name—Identifies the name of the filter.
•![]() Filter Enable—Indicates whether or not the filter is enabled.
Filter Enable—Indicates whether or not the filter is enabled.

Note ![]() Only enabled filters can participate in the Auto Provisioning process.
Only enabled filters can participate in the Auto Provisioning process.
•![]() Monitor Only—If selected, the WLC defined in this Filter is managed by WCS but not configured by WCS if the WLC contacts WCS during the auto provisioning process.
Monitor Only—If selected, the WLC defined in this Filter is managed by WCS but not configured by WCS if the WLC contacts WCS during the auto provisioning process.
•![]() Filter Mode—Indicates the search mode for this filter (Host Name, MAC Address, or Serial Number).
Filter Mode—Indicates the search mode for this filter (Host Name, MAC Address, or Serial Number).
•![]() Config Group Name—Indicates the Configuration Group name.
Config Group Name—Indicates the Configuration Group name.

Note ![]() All Config-Groups used by auto provision filters should not have any controller defined in them.
All Config-Groups used by auto provision filters should not have any controller defined in them.
Select a Command Options for Auto Provisioning
The Select a command drop-down list has the following options:
•![]() Add Filter—Allows you to add an Auto Provisioning filter. See "Auto Provisioning Filters > New Filter" for more information.
Add Filter—Allows you to add an Auto Provisioning filter. See "Auto Provisioning Filters > New Filter" for more information.
•![]() Delete Filter(s)—Allows you to delete the selected Auto Provisioning filter. See "Delete Filter(s)" for more information.
Delete Filter(s)—Allows you to delete the selected Auto Provisioning filter. See "Delete Filter(s)" for more information.
•![]() List Filter(s) Device Info—Allows you to view details for the selected Auto Provisioning filter. See "List Filter(s) Device Info" for more information.
List Filter(s) Device Info—Allows you to view details for the selected Auto Provisioning filter. See "List Filter(s) Device Info" for more information.
•![]() List All Filter(s) Device Info—Allows you to view details for all of the Auto Provisioning filter. See "List All Filter(s) Device Info" for more information.
List All Filter(s) Device Info—Allows you to view details for all of the Auto Provisioning filter. See "List All Filter(s) Device Info" for more information.
Auto Provisioning Filters > New Filter
To add an Auto Provisioning Filter, follow these steps:
Step 1 ![]() Choose Configure > Auto Provisioning. The Auto Provisioning Filter List page appears (see Figure 18-15).
Choose Configure > Auto Provisioning. The Auto Provisioning Filter List page appears (see Figure 18-15).
Figure 18-15 Auto Provisioning Filter List
Step 2 ![]() From the Select a command drop-down list, choose Add Filter.
From the Select a command drop-down list, choose Add Filter.
Step 3 ![]() Click Go.
Click Go.
Step 4 ![]() Click Go. The Auto Provisioning Filters > New Filter page appears (see Figure 18-16).
Click Go. The Auto Provisioning Filters > New Filter page appears (see Figure 18-16).
Figure 18-16 Auto Provisioning Filters > New Filter

Step 5 ![]() Configure the following information:
Configure the following information:
•![]() General
General
–![]() Enable Filter—Select check box to enable the new filter.
Enable Filter—Select check box to enable the new filter.

Note ![]() Only enabled filters can participate in the Auto Provisioning process.
Only enabled filters can participate in the Auto Provisioning process.
–![]() Filter Name—Enter a filter name.
Filter Name—Enter a filter name.
•![]() Filter Properties
Filter Properties
–![]() Monitor Only—If selected, the WLC defined in this Filter is managed by WCS but not configured by WCS if the WLC contacts WCS during the auto provisioning process.
Monitor Only—If selected, the WLC defined in this Filter is managed by WCS but not configured by WCS if the WLC contacts WCS during the auto provisioning process.
–![]() Filter Mode—From the drop-down list, choose Host Name, MAC Address, Serial Number to indicate the search mode for this filter.
Filter Mode—From the drop-down list, choose Host Name, MAC Address, Serial Number to indicate the search mode for this filter.
–![]() Config Group Name—From the drop-down list, choose a config group name.
Config Group Name—From the drop-down list, choose a config group name.
•![]() Filter Member Management - Add Member
Filter Member Management - Add Member
–![]() Input Type—From the drop-down list, choose Single Device or CSV File.
Input Type—From the drop-down list, choose Single Device or CSV File.
If Single Device is selected, enter the host name, enable LAG configuration (if applicable), and enter the following: management interface IP Address, management interface netmask, management interface gateway, AP manager interface IP address, AP manager interface netmask, AP manager interface gateway, and DHCP IP address.
If CSV File is selected, enter the CSV file or use the Browse button to navigate to the applicable CSV File.

Note ![]() You can choose the Download a sample CSV File link to download a sample CSV file to your computer and customize the various configurations.
You can choose the Download a sample CSV File link to download a sample CSV file to your computer and customize the various configurations.

Note ![]() Because MS-Excel can insert additional commas when you edit a CSV file, ensure that you edit the CSV file using a normal text editor application.
Because MS-Excel can insert additional commas when you edit a CSV file, ensure that you edit the CSV file using a normal text editor application.
A CSV file contains the following sections:
** The first part is the General Config section that contains parameters which are used to construct controller's startup config file.
** The first line in the CSV file must be keyword
"!!deviceId, LAG, managementIP, managementVlanId, managementNetmask, managementGateway, apManagerIP, apManagerVlanId, apManagerNetmask, apManagerGateway, dhcpServerIP"
deviceId—it can be Host name, Mac address, or Serial number.
LAG—controller's LAG configuration (true/false).
managementIP—controller's Management interface IP address.
managementVlanId—controller's Management interface VLAN Id (0=untagged).
managementNetmask—controller's Management interface Network mask.
managementGateway—controller's Management interface Gateway IP.
apManagerIP—controller's AP Manager Interface IP address, optional for 5500 series controller.
apManagerVlanId—controller's AP Manager Interface VLAN Id (0=untagged), optional for 5500 series controller.
apManagerNetmask—controller's AP Manager Interface Netmask, optional for 5500 series controller.
apManagerGateway—controller's AP Manager Interface Gateway, optional for 5500 series controller.
dhcpServerIP—controller's DHCP IP address.
** The second part is the Dynamic Interface section that contains dynamic interface parameters for a controller. This is an optional section.
** To configure a dynamic interface, the first eight parameters are mandatory and the last four parameters are optional.
"!!deviceId, interfaceName, vlanId, quarantineVlanId, interfaceIP, interfaceNetmask, gateway, primaryPort, secondaryPort, primaryDHCP, secondaryDHCP, aclName"
deviceId—this deviceId must be defined previously in section 1.
interfaceName—name of the dynamic interface.
vlanId—vlan ID used by this interface.
quarantineVlanId—quarantine vlan ID used by this interface.
interfaceIP—IP address of the dynamic interface.
interfaceNetmask—Network Mask of the dynamic interface.
gateway—Gateway IP address of the dynamic interface.
primaryPort—physical primary port number used by the dynamic interface.
secondaryPort—physical secondary port number used by the dynamic interface, this is an optional parameter.
primaryDHCP—the IP address of the primary DHCP used by the dynamic interface, this is an optional parameter.
secondaryDHCP—IP address of the secondary DHCP used by the dynamic interface, this is an optional parameter.
** The third part is the Device Specific Config section, contains other device specific configuration parameters which are optional during auto provisioning.
"!!deviceId, countryCode, mobilityGroupName, mobilityGroupMembers"
deviceId—this deviceId must be defined previously in section 1.
countryCode—country code for the controller, this is an optional parameter.
mobilityGroupName—default name of the mobility group this controller belongs to, this is an optional parameter. If this attribute is not specified then the existing default mobility group name will be used.
mobilityGroupMembers—IP addresses, Mac Addresses and mobility group name of the mobility group members of the controller, which are separated by semi colon, this is an optional parameter. Both IP address and Mac Address are required for a mobility group member, they are separated by forward slash. Mobility group name is an optional attribute in this field. If mobility group name is not present then the default mobility group name for this controller will be used.
•![]() If you select the Single Device option, specify the following options:
If you select the Single Device option, specify the following options:
–![]() Device Type—From the drop-down list, choose 5500 Controller or non-5500 Controller.
Device Type—From the drop-down list, choose 5500 Controller or non-5500 Controller.
–![]() Host Name
Host Name
–![]() LAG Configuration: Enabled or Disabled.
LAG Configuration: Enabled or Disabled.
–![]() Management Interface IP Address
Management Interface IP Address
–![]() Management Interface Netmask
Management Interface Netmask
–![]() Management Interface Gateway
Management Interface Gateway
–![]() AP Manager Interface IP Address
AP Manager Interface IP Address
–![]() AP Manager Interface Netmask
AP Manager Interface Netmask
–![]() AP Manager Interface Gateway
AP Manager Interface Gateway
–![]() DHCP IP Address
DHCP IP Address
Step 6 ![]() Click Submit.
Click Submit.

Note ![]() You can specify the Dynamic Interface configuration and Device Specific configuration details only when you input a CSV file. These two configurations cannot be performed using the GUI.
You can specify the Dynamic Interface configuration and Device Specific configuration details only when you input a CSV file. These two configurations cannot be performed using the GUI.
Editing a Current Auto Provisioning Filter
To edit a current Auto Provisioning filter, follow these steps:
Step 1 ![]() Choose Configure > Auto Provisioning.
Choose Configure > Auto Provisioning.
Step 2 ![]() Click the Filter Name of the filter you want to edit.
Click the Filter Name of the filter you want to edit.
Step 3 ![]() Make the necessary changes to the current filter parameters.
Make the necessary changes to the current filter parameters.

Note ![]() To view detailed information for a filter member, click the Device ID of the member you want to view.
To view detailed information for a filter member, click the Device ID of the member you want to view.
To delete a filter member. select the check box for the member you want to delete in the Filter Member Management - Delete Member section. When you click Submit, that member is deleted.
Step 4 ![]() Click Submit.
Click Submit.
Delete Filter(s)
To delete an Auto Provisioning Filter, follow these steps:
Step 1 ![]() Choose Configure > Auto Provisioning.
Choose Configure > Auto Provisioning.
Step 2 ![]() Select the check box of the filter you want to delete.
Select the check box of the filter you want to delete.
Step 3 ![]() From the Select a command drop-down list, choose Delete Filter(s).
From the Select a command drop-down list, choose Delete Filter(s).
Step 4 ![]() Click Go.
Click Go.
Step 5 ![]() Click OK to confirm the deletion.
Click OK to confirm the deletion.
List Filter(s) Device Info
To view details for an individual Auto Provisioning Filter, follow these steps:
Step 1 ![]() Choose Configure > Auto Provisioning.
Choose Configure > Auto Provisioning.
Step 2 ![]() Select the check box of the filter you want to view.
Select the check box of the filter you want to view.
Step 3 ![]() From the Select a command drop-down list, choose List Filter(s) Device Info.
From the Select a command drop-down list, choose List Filter(s) Device Info.
Step 4 ![]() Click Go. The Detailed Auto Provisioning Device Information page appears (see Figure 18-17).
Click Go. The Detailed Auto Provisioning Device Information page appears (see Figure 18-17).
Figure 18-17 Detailed Auto Provisioning Device Information

The following information is provided for the selected filter:
•![]() Filter Name—Indicates the filter name.
Filter Name—Indicates the filter name.
•![]() Device ID—Indicates the device ID.
Device ID—Indicates the device ID.
•![]() LAG—Indicates the controller LAG status as true or false.
LAG—Indicates the controller LAG status as true or false.
•![]() Management IP—Indicates the management interface IP address of the controller.
Management IP—Indicates the management interface IP address of the controller.
•![]() Management VlanId—Indicates the management VLAN Id of the controller.
Management VlanId—Indicates the management VLAN Id of the controller.
•![]() Management Netmask—Indicates the netmask mask of the management interface of the controller.
Management Netmask—Indicates the netmask mask of the management interface of the controller.
•![]() Management Gateway—Indicates the netmask gateway of the management interface of the controller.
Management Gateway—Indicates the netmask gateway of the management interface of the controller.
•![]() AP Mgr IP—Indicates the IP address of the access point manager.
AP Mgr IP—Indicates the IP address of the access point manager.
•![]() AP Mgr Vlan Id—Indicates the VLAN identifier of the access point manager.
AP Mgr Vlan Id—Indicates the VLAN identifier of the access point manager.
•![]() AP Mgr Netmask—Indicates the netmask mask of the access point manager.
AP Mgr Netmask—Indicates the netmask mask of the access point manager.
•![]() AP Mgr Gateway—Indicates the gateway IP address of the access point manager.
AP Mgr Gateway—Indicates the gateway IP address of the access point manager.
•![]() Status—Idle, Trap Received, Failed In Trap Processing, Failed In Applying Templates, Failed In Discovery Switch, Managed, Managed partially applied templates, or Unknown Error
Status—Idle, Trap Received, Failed In Trap Processing, Failed In Applying Templates, Failed In Discovery Switch, Managed, Managed partially applied templates, or Unknown Error
•![]() Country
Country
•![]() Mobility Grp—Indicates the name of the mobility group.
Mobility Grp—Indicates the name of the mobility group.
•![]() Mobility Grp Members
Mobility Grp Members
•![]() Timestamp—Indicates the date and time of the information.
Timestamp—Indicates the date and time of the information.
List All Filter(s) Device Info
To view details for all Auto Provisioning Filters, follow these steps:
Step 1 ![]() Choose Configure > Auto Provisioning.
Choose Configure > Auto Provisioning.
Step 2 ![]() From the Select a command drop-down list, choose List All Filter(s) Device Info.
From the Select a command drop-down list, choose List All Filter(s) Device Info.
Step 3 ![]() Click Go.
Click Go.
The following information is provided for the selected filter:
•![]() Filter Name—Indicates the filter name.
Filter Name—Indicates the filter name.
•![]() Device ID—Indicates the device ID.
Device ID—Indicates the device ID.
•![]() LAG—Indicates the controller LAG status as true or false.
LAG—Indicates the controller LAG status as true or false.
•![]() Management IP—Indicates the management interface IP address of the controller.
Management IP—Indicates the management interface IP address of the controller.
•![]() Management VlanId—Indicates the management VLAN Id of the controller.
Management VlanId—Indicates the management VLAN Id of the controller.
•![]() Management Netmask—Indicates the netmask mask of the management interface of the controller.
Management Netmask—Indicates the netmask mask of the management interface of the controller.
•![]() Management Gateway—Indicates the netmask gateway of the management interface of the controller.
Management Gateway—Indicates the netmask gateway of the management interface of the controller.
•![]() AP Mgr IP—Indicates the IP address of the access point manager.
AP Mgr IP—Indicates the IP address of the access point manager.
•![]() AP Mgr Vlan Id—Indicates the VLAN identifier of the access point manager.
AP Mgr Vlan Id—Indicates the VLAN identifier of the access point manager.
•![]() AP Mgr Netmask—Indicates the netmask mask of the access point manager.
AP Mgr Netmask—Indicates the netmask mask of the access point manager.
•![]() AP Mgr Gateway—Indicates the gateway IP address of the access point manager.
AP Mgr Gateway—Indicates the gateway IP address of the access point manager.
•![]() Status—Idle, Trap Received, Failed In Trap Processing, Failed In Applying Templates, Failed In Discovery Switch, Managed, Managed partially applied templates, or Unknown Error
Status—Idle, Trap Received, Failed In Trap Processing, Failed In Applying Templates, Failed In Discovery Switch, Managed, Managed partially applied templates, or Unknown Error
•![]() Country
Country
•![]() Mobility Grp
Mobility Grp
•![]() Mobility Grp Members
Mobility Grp Members
•![]() Timestamp—Indicates the date and time of the information.
Timestamp—Indicates the date and time of the information.
Export Filter(s)
To export an Auto Provisioning Filter, follow these steps:
Step 1 ![]() Choose Configure > Auto Provisioning.
Choose Configure > Auto Provisioning.
Step 2 ![]() Select the check box of the filter(s) you want to export.
Select the check box of the filter(s) you want to export.
Step 3 ![]() From the Select a command drop-down list, choose Export Filter(s) Config (CSV).
From the Select a command drop-down list, choose Export Filter(s) Config (CSV).
Step 4 ![]() Click Go.
Click Go.
Step 5 ![]() In the File Download dialog box that appears, click Save to save the file to a location on the computer.
In the File Download dialog box that appears, click Save to save the file to a location on the computer.
Export All Filter(s)
To export all Auto Provisioning Filters, follow these steps:
Step 1 ![]() Choose Configure > Auto Provisioning.
Choose Configure > Auto Provisioning.
Step 2 ![]() From the Select a command drop-down list, choose Export All Filter(s) Config (CSV).
From the Select a command drop-down list, choose Export All Filter(s) Config (CSV).
Step 3 ![]() Click Go.
Click Go.
Step 4 ![]() In the File Download dialog box that appears, click Save to save the file to a location on the computer.
In the File Download dialog box that appears, click Save to save the file to a location on the computer.
Auto Provisioning Setting (Auto Provisioning Primary Search Key Setting)
The Primary Search Key Setting enables you to set the matching criteria search order.
To indicate the Search Key Order, follow these steps:
Step 1 ![]() Choose Configure > Auto Provisioning.
Choose Configure > Auto Provisioning.
Step 2 ![]() From the left sidebar menu, choose Auto Provisioning Setting.
From the left sidebar menu, choose Auto Provisioning Setting.
Step 3 ![]() Click to highlight the applicable search key.
Click to highlight the applicable search key.
Step 4 ![]() Use the Move Up or Move Down buttons to move the search key to a higher or lower priority.
Use the Move Up or Move Down buttons to move the search key to a higher or lower priority.
Step 5 ![]() Click Save to confirm or Cancel to cancel the changes.
Click Save to confirm or Cancel to cancel the changes.
Turning Password Rules On or Off
You have the ability to customize the various password rules to meet your criteria. Follow these steps to customize the password rules.
Step 1 ![]() Choose Administration > AAA.
Choose Administration > AAA.
Step 2 ![]() From the left sidebar menu, choose Local Password Policy. The password rules are displayed individually, and each has a check box in front of it.
From the left sidebar menu, choose Local Password Policy. The password rules are displayed individually, and each has a check box in front of it.
Step 3 ![]() Click the check boxes to enable the rules you want. The rules are as follows:
Click the check boxes to enable the rules you want. The rules are as follows:

Note ![]() All rules are on by default.
All rules are on by default.
•![]() Password minimum length is 8 characters (the length configurable).
Password minimum length is 8 characters (the length configurable).
•![]() Password cannot contain username or the reverse of the username.
Password cannot contain username or the reverse of the username.
•![]() Password cannot be cisco or ocsic (Cisco reversed).
Password cannot be cisco or ocsic (Cisco reversed).
•![]() Root password cannot be public.
Root password cannot be public.
•![]() No character can be repeated more than three times consecutively in the password.
No character can be repeated more than three times consecutively in the password.
•![]() Password must contain characters from three of the character classes: uppercase, lowercase, digits, and special characters.
Password must contain characters from three of the character classes: uppercase, lowercase, digits, and special characters.
•![]() Password cannot be reused within n number of the previous passwords used. By default it is 10 times.
Password cannot be reused within n number of the previous passwords used. By default it is 10 times.
•![]() Password cannot be changed at an interval of less than 24 hours from last change.
Password cannot be changed at an interval of less than 24 hours from last change.
•![]() Set the account to be lockout after x number of failed login attempts. By default it is 5 attempts.
Set the account to be lockout after x number of failed login attempts. By default it is 5 attempts.
•![]() Set if the account should be disabled after 30 days of inactivity.
Set if the account should be disabled after 30 days of inactivity.
•![]() Set the number of days after when the password should expire. By default it is 60 days.
Set the number of days after when the password should expire. By default it is 60 days.
•![]() Enforce password change on first login
Enforce password change on first login
Click Save to configure the Local Password Policy rules.
Configuring TACACS+ Servers
This section describes how to add and delete TACACS+ servers. TACACS+ servers provide an effective and secure management framework with built-in failover mechanisms. If you want to make configuration changes, you must be authenticated.

Note ![]() In order to activate TACACS+ servers, you must enable them as described in the "Importing Tasks Into ACS" section.
In order to activate TACACS+ servers, you must enable them as described in the "Importing Tasks Into ACS" section.
Step 1 ![]() Choose Administration > AAA.
Choose Administration > AAA.
Step 2 ![]() From the left sidebar menu, choose TACACS+. The TACACS+ page appears (see Figure 18-18).
From the left sidebar menu, choose TACACS+. The TACACS+ page appears (see Figure 18-18).
Figure 18-18 TACACS+ Page

Step 3 ![]() The TACACS+ page shows the TACACS+ server's IP address, port, retransmit rate, and authentication type (Password Authentication Protocol (PAP)) or Challenge Handshake Authentication Protocol (CHAP). The TACACS+ servers are tried based on how they were configured.
The TACACS+ page shows the TACACS+ server's IP address, port, retransmit rate, and authentication type (Password Authentication Protocol (PAP)) or Challenge Handshake Authentication Protocol (CHAP). The TACACS+ servers are tried based on how they were configured.

Note ![]() If you need to change the order of how TACACS+ servers are tried, delete any irrelevant TACACS+ servers and re-add the desired ones in the preferred order.
If you need to change the order of how TACACS+ servers are tried, delete any irrelevant TACACS+ servers and re-add the desired ones in the preferred order.
Step 4 ![]() Use the drop-down list in the upper right-hand corner to add or delete TACACS+ servers. You can click an IP address if you want to make changes to the information.
Use the drop-down list in the upper right-hand corner to add or delete TACACS+ servers. You can click an IP address if you want to make changes to the information.
Step 5 ![]() The current server address and port are displayed. Use the drop-down list to choose either ASCII or hex shared secret format.
The current server address and port are displayed. Use the drop-down list to choose either ASCII or hex shared secret format.
Step 6 ![]() Enter the TACACS+ shared secret used by your specified server.
Enter the TACACS+ shared secret used by your specified server.
Step 7 ![]() Re-enter the shared secret in the Confirm Shared Secret text box.
Re-enter the shared secret in the Confirm Shared Secret text box.
Step 8 ![]() Specify the time in seconds after which the TACACS+ authentication request times out and a retransmission is attempted by the controller.
Specify the time in seconds after which the TACACS+ authentication request times out and a retransmission is attempted by the controller.
Step 9 ![]() Specify the number of retries that will be attempted.
Specify the number of retries that will be attempted.
Step 10 ![]() In the Authentication Type drop-down list, choose a protocol: PAP or CHAP.
In the Authentication Type drop-down list, choose a protocol: PAP or CHAP.
Step 11 ![]() Click Submit.
Click Submit.

Note ![]() See the "Configuring ACS 5.x" section for more information on Configuring ACS 5.x.
See the "Configuring ACS 5.x" section for more information on Configuring ACS 5.x.
Configuring RADIUS Servers
This section describes how to add and delete RADIUS servers. You must enable RADIUS servers and have a template set up for them in order to make configuration changes.

Note ![]() In order to activate RADIUS servers, you must enable them as described in the "Importing Tasks Into ACS" section.
In order to activate RADIUS servers, you must enable them as described in the "Importing Tasks Into ACS" section.
Step 1 ![]() Choose Administration > AAA.
Choose Administration > AAA.
Step 2 ![]() From the left sidebar menu, choose RADIUS. The RADIUS page appears (see Figure 18-19).
From the left sidebar menu, choose RADIUS. The RADIUS page appears (see Figure 18-19).
Figure 18-19 RADIUS Page
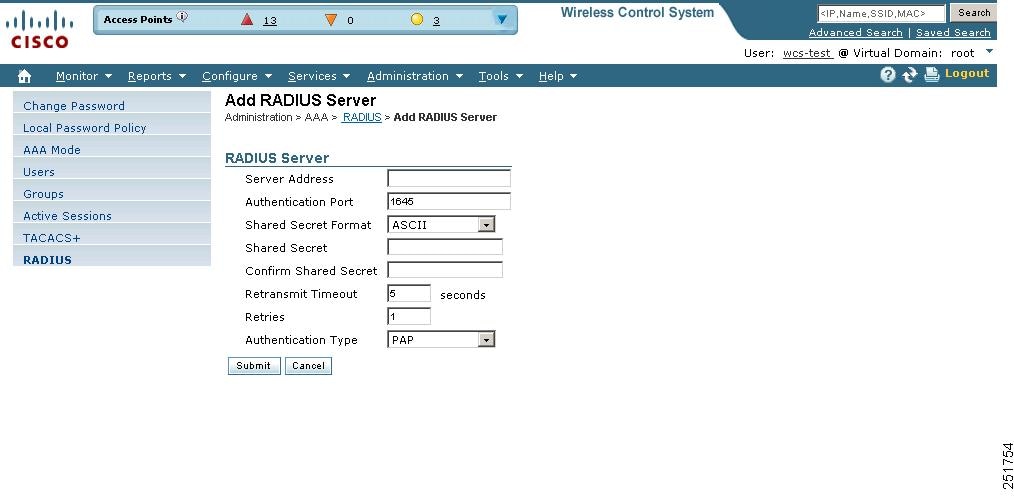
Step 3 ![]() The RADIUS page shows the server address, authentication port, retransmit timeout value, and authentication type for each RADIUS server that is configured. The RADIUS servers are tried based on how they were configured.
The RADIUS page shows the server address, authentication port, retransmit timeout value, and authentication type for each RADIUS server that is configured. The RADIUS servers are tried based on how they were configured.

Note ![]() If you need to change the order of how RADIUS servers are tried, delete any irrelevant RADIUS servers, and re-add the desired ones in the preferred order.
If you need to change the order of how RADIUS servers are tried, delete any irrelevant RADIUS servers, and re-add the desired ones in the preferred order.
Step 4 ![]() Use the drop-down list in the upper right-hand corner to add or delete RADIUS servers. You can click an IP address if you want to make changes to the information.
Use the drop-down list in the upper right-hand corner to add or delete RADIUS servers. You can click an IP address if you want to make changes to the information.
Step 5 ![]() The current authentication port appears. Use the drop-down list to choose either ASCII or hex shared secret format.
The current authentication port appears. Use the drop-down list to choose either ASCII or hex shared secret format.
Step 6 ![]() Enter the RADIUS shared secret used by your specified server.
Enter the RADIUS shared secret used by your specified server.
Step 7 ![]() Re-enter the shared secret in the Confirm Shared Secret text box.
Re-enter the shared secret in the Confirm Shared Secret text box.
Step 8 ![]() Specify the time in seconds after which the RADIUS authentication request times out and a retransmission is attempted by the controller.
Specify the time in seconds after which the RADIUS authentication request times out and a retransmission is attempted by the controller.
Step 9 ![]() Specify the number of retries that will be attempted.
Specify the number of retries that will be attempted.
Step 10 ![]() In the Authentication Type drop-down list, choose a protocol: PAP or CHAP.
In the Authentication Type drop-down list, choose a protocol: PAP or CHAP.
Step 11 ![]() Click Submit.
Click Submit.
Establishing Logging Options
Use Administration > Logging to access the Administer Logging Options page. This logging function is related only to WCS logging and not syslog information. The logging for controller syslog information can be done on the Controller > Management > Syslog page.
Follow the steps below to enable e-mail logging. The settings you establish are stored and are used by the e-mail server.
Step 1 ![]() Choose Administration > Logging. The Logging Options menu appears (see Figure 18-20).
Choose Administration > Logging. The Logging Options menu appears (see Figure 18-20).
Figure 18-20 Logging Options Page

Step 2 ![]() Choose a message level option of Trace, Information, or Error.
Choose a message level option of Trace, Information, or Error.
Step 3 ![]() Click the check boxes within the Enable Log Module portion of the page to enable various administration modules:
Click the check boxes within the Enable Log Module portion of the page to enable various administration modules:
•![]() Message Level—Select the minimum level of the messages that will be logged including Error, Information, or Trace.
Message Level—Select the minimum level of the messages that will be logged including Error, Information, or Trace.
•![]() Enable Log Module—You can enable logging for the following administration modules:
Enable Log Module—You can enable logging for the following administration modules:
–![]() Status Polling—Used to log all background tasks.
Status Polling—Used to log all background tasks.
–![]() Object Manager—Captures logs related to managed devices and resource allocation.
Object Manager—Captures logs related to managed devices and resource allocation.
–![]() Configuration—Used to log controller configurations that you make from WCS.
Configuration—Used to log controller configurations that you make from WCS.

Note ![]() To get complete controller configuration logs, also enable the General log module.
To get complete controller configuration logs, also enable the General log module.

Note ![]() To get the configuration values that the WCS sends in logs to controllers, enable Trace Display Values (Administration > Settings > SNMP Settings > Trace Display Value).
To get the configuration values that the WCS sends in logs to controllers, enable Trace Display Values (Administration > Settings > SNMP Settings > Trace Display Value).
•![]() Monitor—Used for Alarms, Spectrum Intelligence, CCXV5, Clients/Tags, Client Radio Measurements, SSO, and Mesh.
Monitor—Used for Alarms, Spectrum Intelligence, CCXV5, Clients/Tags, Client Radio Measurements, SSO, and Mesh.
•![]() Fault Analysis—Used by the event and alert subsystem.
Fault Analysis—Used by the event and alert subsystem.
•![]() SNMP Mediation—Captures logs for all SNMP communication between WCS and controllers.
SNMP Mediation—Captures logs for all SNMP communication between WCS and controllers.
•![]() General—Contains logs that do not fall under other log module categories.
General—Contains logs that do not fall under other log module categories.

Note ![]() Cisco recommends that you enable this log module.
Cisco recommends that you enable this log module.
•![]() MSE/Location Servers—Used for MSE-related operations such as adding or deleting an MSE and changing parameters on the MSE. It also enables logging for MSE synchronization including NW designs and controllers.
MSE/Location Servers—Used for MSE-related operations such as adding or deleting an MSE and changing parameters on the MSE. It also enables logging for MSE synchronization including NW designs and controllers.
•![]() XML Mediation—Used to enable trace for the communication between MSE/LOC 2700 and WCS.
XML Mediation—Used to enable trace for the communication between MSE/LOC 2700 and WCS.
•![]() Asynchronous—Used for WCS notifications and for Simple Object Access Protocol (SOAP) messages that MSE generates.
Asynchronous—Used for WCS notifications and for Simple Object Access Protocol (SOAP) messages that MSE generates.
•![]() Navigator—Contains logs to debug issues when WCS does not respond to WCS Navigator's periodic polling through the Northbound Webservice API.
Navigator—Contains logs to debug issues when WCS does not respond to WCS Navigator's periodic polling through the Northbound Webservice API.
•![]() Reports—Used to log messages related to creating, saving, scheduling, and running reports. This module also contains a list of scheduled and saved reports.
Reports—Used to log messages related to creating, saving, scheduling, and running reports. This module also contains a list of scheduled and saved reports.
•![]() Database Administration—Contains logs to debug important database-related operations in WCS.
Database Administration—Contains logs to debug important database-related operations in WCS.

Note ![]() Some functions should be used only for short periods of time during debugging so that the performance is not degraded. For example, trace mode and SNMP meditation should be enabled only during debugging because a lot of log information is generated.
Some functions should be used only for short periods of time during debugging so that the performance is not degraded. For example, trace mode and SNMP meditation should be enabled only during debugging because a lot of log information is generated.
Step 4 ![]() In the Log File Settings portion, enter the following settings. These settings will be effective after restarting WCS.
In the Log File Settings portion, enter the following settings. These settings will be effective after restarting WCS.
•![]() Max. file size—Maximum number of MBs allowed per log file.
Max. file size—Maximum number of MBs allowed per log file.
•![]() Number of files—Maximum number of log files allowed.
Number of files—Maximum number of log files allowed.
•![]() File prefix—Log file prefix, which can include the characters "%g" to sequentially number of files.
File prefix—Log file prefix, which can include the characters "%g" to sequentially number of files.
Step 5 ![]() Click the Download Log File section to download log files to the local machine.
Click the Download Log File section to download log files to the local machine.

Note ![]() The logs.zip filename includes a prefix with the host name, date, and time so that you can easily identify the stored log file. Included in the zip file is an html file that documents the log files.
The logs.zip filename includes a prefix with the host name, date, and time so that you can easily identify the stored log file. Included in the zip file is an html file that documents the log files.
Step 6 ![]() Click Submit.
Click Submit.
Using Logging Options to Enhance Troubleshooting
The logging screen allows you to customize the amount of data WCS collects in order to debug an issue. For easily reproduced issues, follow these steps prior to contacting TAC. These steps may create a smoother troubleshooting session:
Step 1 ![]() Choose Administration > Logging.
Choose Administration > Logging.
Step 2 ![]() From the Message Level drop-down list, choose Trace.
From the Message Level drop-down list, choose Trace.
Step 3 ![]() Select each check box to enable all log modules.
Select each check box to enable all log modules.
Step 4 ![]() Reproduce the current problem.
Reproduce the current problem.
Step 5 ![]() Return to the Logging Options page.
Return to the Logging Options page.
Step 6 ![]() Click Download from the Download Log File section.
Click Download from the Download Log File section.
Step 7 ![]() After you have retrieved the logs, select Information from the Message Level drop-down list.
After you have retrieved the logs, select Information from the Message Level drop-down list.

Note ![]() Leaving the Message Level at Trace can adversely affect performance over a long period of time.
Leaving the Message Level at Trace can adversely affect performance over a long period of time.
Performing Data Management Tasks
Within the Settings page, you can indicates the data that you want to generate for reports and e-mails. Choose Administration > Settings in the left sidebar menu.
•![]() See the "Alarms" section to specify how to handle old alarms and how to display assigned and acknowledged alarms in the Alarm Summary page.
See the "Alarms" section to specify how to handle old alarms and how to display assigned and acknowledged alarms in the Alarm Summary page.
•![]() See "Audit" section to configure audit information.
See "Audit" section to configure audit information.
•![]() See the "Client" section to enable client troubleshooting on a diagnostic channel.
See the "Client" section to enable client troubleshooting on a diagnostic channel.
•![]() See the "CLI Session" section to establish a telnet or SSH session.
See the "CLI Session" section to establish a telnet or SSH session.
•![]() See the "Controller Upgrade Settings" section for information on controller upgrade settings.
See the "Controller Upgrade Settings" section for information on controller upgrade settings.
•![]() See the "Data Management" section to establish trends for hourly, daily, and weekly data periods.
See the "Data Management" section to establish trends for hourly, daily, and weekly data periods.
•![]() See the "Guest Account Settings" section to designate where the scheduled reports will reside and for how long.
See the "Guest Account Settings" section to designate where the scheduled reports will reside and for how long.
•![]() See the "Login Disclaimer" section to enter disclaimer information.
See the "Login Disclaimer" section to enter disclaimer information.
•![]() See the "Mail Server Configuration" section to set the primary and secondary SMTP server host and port.
See the "Mail Server Configuration" section to set the primary and secondary SMTP server host and port.
•![]() See the "Notification Receiver" section to configure parameters for notification support of guest access functionality.
See the "Notification Receiver" section to configure parameters for notification support of guest access functionality.
•![]() See the "Server Settings" section to turn FTP, TFTP, HTTP, or HTTPS on or off.
See the "Server Settings" section to turn FTP, TFTP, HTTP, or HTTPS on or off.
•![]() See the "Severity Configurations" section to configure the severity level for newly generated alarms.
See the "Severity Configurations" section to configure the severity level for newly generated alarms.
•![]() See the "SNMP Credentials" section to specify which credentials to use for tracing the rogue access points.
See the "SNMP Credentials" section to specify which credentials to use for tracing the rogue access points.
•![]() See the "SNMP Settings" section to configure global SNMP settings from WCS.
See the "SNMP Settings" section to configure global SNMP settings from WCS.
•![]() See the "Switch Port Trace" section to identify the switch port to which a rogue access point is connected.
See the "Switch Port Trace" section to identify the switch port to which a rogue access point is connected.
Alarms
This Alarms page enables you to handle old alarms and display assigned and acknowledged alarms in the Alarm Summary page.
To open this page, follow these steps:
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Alarms. The Administration > Settings > Alarms page appears (see Figure 18-21).
From the left sidebar menu, choose Alarms. The Administration > Settings > Alarms page appears (see Figure 18-21).
Figure 18-21 Settings > Alarms Page

Step 3 ![]() Add or modify the following Alarms parameters:
Add or modify the following Alarms parameters:
•![]() Alarm Cleanup Options
Alarm Cleanup Options
–![]() Delete active and cleared alarms after—Enter the number of days after which active and cleared alarms are deleted. This option can be disabled by clearing the check box.
Delete active and cleared alarms after—Enter the number of days after which active and cleared alarms are deleted. This option can be disabled by clearing the check box.
–![]() Delete cleared security alarms after—Enter the number of days after which Security, Rogue AP, and Adhoc Rogue alarms are deleted.
Delete cleared security alarms after—Enter the number of days after which Security, Rogue AP, and Adhoc Rogue alarms are deleted.
–![]() Delete cleared non-security alarms after—Enter the number of days after which non-security alarms are deleted. Non-security alarms include all alarms that do not fall under the Security, Rogue AP, or Adhoc Rogue categories.
Delete cleared non-security alarms after—Enter the number of days after which non-security alarms are deleted. Non-security alarms include all alarms that do not fall under the Security, Rogue AP, or Adhoc Rogue categories.

Note ![]() Data cleanup tasks run nightly to delete old alarms. In addition to the data cleanup task, WCS has an hourly task to check alarm table size. When the alarm table size exceeds 300 K, the task deletes the oldest cleared alarms until the alarm table size is within 300 K.
Data cleanup tasks run nightly to delete old alarms. In addition to the data cleanup task, WCS has an hourly task to check alarm table size. When the alarm table size exceeds 300 K, the task deletes the oldest cleared alarms until the alarm table size is within 300 K.

Note ![]() If you want to keep the cleared alarms for more than 7 days, then you can specify a value more than 7 days in the Delete cleared non-security alarms after text box until the alarm table size reaches 300 K.
If you want to keep the cleared alarms for more than 7 days, then you can specify a value more than 7 days in the Delete cleared non-security alarms after text box until the alarm table size reaches 300 K.
•![]() Alarm Display Options
Alarm Display Options

Note ![]() These preferences only apply to the Alarm Summary page. Quick searches or alarms for any entity display all alarms regardless of the acknowledged or assigned state.
These preferences only apply to the Alarm Summary page. Quick searches or alarms for any entity display all alarms regardless of the acknowledged or assigned state.
–![]() Hide acknowledged alarms—When the check box is selected, Acknowledged alarms do not appear on the Alarm Summary page. This option is enabled by default.
Hide acknowledged alarms—When the check box is selected, Acknowledged alarms do not appear on the Alarm Summary page. This option is enabled by default.

Note ![]() E-mails are not generated for acknowledged alarms regardless of severity change.
E-mails are not generated for acknowledged alarms regardless of severity change.
–![]() Hide assigned alarms—When the check box is selected, assigned alarms do not appear on the Alarm Summary page.
Hide assigned alarms—When the check box is selected, assigned alarms do not appear on the Alarm Summary page.
–![]() Add controller name to alarm messages—Select the check box to add the name of the controller to alarm messages.
Add controller name to alarm messages—Select the check box to add the name of the controller to alarm messages.
–![]() Add WCS address to email notifications—Select the check box to add the WCS address to email notifications.
Add WCS address to email notifications—Select the check box to add the WCS address to email notifications.
Step 4 ![]() Click Save.
Click Save.
Audit
You can choose between basic and template-based auditing. The default setting is Basic Audit.
•![]() Basic Audit—Audits the configuration objects in the WCS database against current WLC device values. Prior to the 5.1.0.0 version of WCS, this was the only audit mode available.
Basic Audit—Audits the configuration objects in the WCS database against current WLC device values. Prior to the 5.1.0.0 version of WCS, this was the only audit mode available.

Note ![]() Configuration objects refer to the device configuration stored in the WCS database.
Configuration objects refer to the device configuration stored in the WCS database.
•![]() Template-based Audit—Audits on the applied templates, config group templates (which have been selected for the background audit), and configuration audits (for which corresponding templates do not exist) against current WLC device values.
Template-based Audit—Audits on the applied templates, config group templates (which have been selected for the background audit), and configuration audits (for which corresponding templates do not exist) against current WLC device values.
Follow these steps to indicate the type of audit you want to perform.
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Audit. The Audit Setting page appears (see Figure 18-22).
From the left sidebar menu, choose Audit. The Audit Setting page appears (see Figure 18-22).
Figure 18-22 Audit Settings Page

Step 3 ![]() Select the radio button for either Basic or Template-Based Audit. A basic audit audits the device configuration in the WCS database against the current WLC configuration. A template-based audit audits the applied templates, config group templates, and configuration objects (for which corresponding templates do not exist) against current WLC configuration.
Select the radio button for either Basic or Template-Based Audit. A basic audit audits the device configuration in the WCS database against the current WLC configuration. A template-based audit audits the applied templates, config group templates, and configuration objects (for which corresponding templates do not exist) against current WLC configuration.
Step 4 ![]() Choose if you want the audit to run on all parameters or only on selected parameters. If you select the Selected Parameters radio button, you can access the Configure Audit Parameters configuration page. (See the "Configuring Audit Parameters" section below). The Select audit parameters URL appears.
Choose if you want the audit to run on all parameters or only on selected parameters. If you select the Selected Parameters radio button, you can access the Configure Audit Parameters configuration page. (See the "Configuring Audit Parameters" section below). The Select audit parameters URL appears.
The selected audit parameters are used during network and controller audits.
Step 5 ![]() Click Save.
Click Save.

Note ![]() These settings are in effect when the controller audit or network audit is performed.
These settings are in effect when the controller audit or network audit is performed.
Configuring Audit Parameters
To configure the audit parameters for a global audit, follow these steps:
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Audit.
From the left sidebar menu, choose Audit.
Step 3 ![]() Select the Selected Parameters radio button to display the Select Audit Parameters link.
Select the Selected Parameters radio button to display the Select Audit Parameters link.
Step 4 ![]() Click Save.
Click Save.
Step 5 ![]() Click Select Audit Parameters to choose the required parameters for the audit in the Audit Configuration > Parameter Selection page.
Click Select Audit Parameters to choose the required parameters for the audit in the Audit Configuration > Parameter Selection page.
Step 6 ![]() Select the parameters that you want audited from each of the tabs. The tabs include System, WLAN, Security, Wireless, and Selected Attributes.
Select the parameters that you want audited from each of the tabs. The tabs include System, WLAN, Security, Wireless, and Selected Attributes.
Step 7 ![]() When all desired audit parameters are selected, click Submit to confirm the parameters or click Cancel to close the page without saving any audit parameters.
When all desired audit parameters are selected, click Submit to confirm the parameters or click Cancel to close the page without saving any audit parameters.
Once you click Submit, the selected audit parameters display under the Selected Attributes tab.
A current Controller Audit Report can be accessed from the Configure > Controllers page by selecting an object from the Audit Status column.

Note ![]() You can audit a controller by selecting Audit Now from the Select a command drop-down list in the Configure > Controllers page or by clicking Audit Now directly from the Controller Audit report. See the "Viewing Audit Status (for Controllers)" section.
You can audit a controller by selecting Audit Now from the Select a command drop-down list in the Configure > Controllers page or by clicking Audit Now directly from the Controller Audit report. See the "Viewing Audit Status (for Controllers)" section.
Client
In the Administration > Settings > Client page, you can configure the following client processes to improve WCS performance and scalability.

Note ![]() See the "Client Troubleshooting" section for further information on client troubleshooting.
See the "Client Troubleshooting" section for further information on client troubleshooting.
•![]() Process Diagnostic Trap
Process Diagnostic Trap
•![]() Host Name Lookup
Host Name Lookup
•![]() Data Retention
Data Retention
•![]() Client Traps
Client Traps
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Client. The Client page appears (see Figure 18-23).
From the left sidebar menu, choose Client. The Client page appears (see Figure 18-23).
Figure 18-23 Administration > Settings > Client Page

Step 1 ![]() Click if you want to enable automatic client troubleshooting on a diagnostic channel. Automatic client troubleshooting is available only for CCXV5 clients.
Click if you want to enable automatic client troubleshooting on a diagnostic channel. Automatic client troubleshooting is available only for CCXV5 clients.

Note ![]() If the check box is selected, WCS processes the diagnostic association trap. If it is not selected, WCS raises the trap, but automated troubleshooting is not initiated.
If the check box is selected, WCS processes the diagnostic association trap. If it is not selected, WCS raises the trap, but automated troubleshooting is not initiated.

Note ![]() While processing the diagnostic association trap, the WCS invokes a series of tests on the client. The client is updated on all completed tasks. The automated troubleshooting report is placed in dist/acs/win/webnms/logs. When the test is complete, the location of the log is updated in client details pages:V5 tab:Automated Troubleshooting Report section. An export button allows you to export the logs.
While processing the diagnostic association trap, the WCS invokes a series of tests on the client. The client is updated on all completed tasks. The automated troubleshooting report is placed in dist/acs/win/webnms/logs. When the test is complete, the location of the log is updated in client details pages:V5 tab:Automated Troubleshooting Report section. An export button allows you to export the logs.
Step 2 ![]() Select the Lookup client host names for DNS server check box. DNS lookup can take a considerable amount of time. Therefore, you can enable or disable the DNS lookup for client host name. It is set to Disable by default. If you enable the check box, you need to enter the number of days that you want the host name to remain in the cache.
Select the Lookup client host names for DNS server check box. DNS lookup can take a considerable amount of time. Therefore, you can enable or disable the DNS lookup for client host name. It is set to Disable by default. If you enable the check box, you need to enter the number of days that you want the host name to remain in the cache.
Step 3 ![]() In the Data Retention section, enter or edit the following data retention parameters. Client association history can take a lot of database and disk space. This can be an problem for database backup and restore functions. You can configure the retaining duration of a client association history to help manage this potential issue.
In the Data Retention section, enter or edit the following data retention parameters. Client association history can take a lot of database and disk space. This can be an problem for database backup and restore functions. You can configure the retaining duration of a client association history to help manage this potential issue.
•![]() Client (days)—Enter the number of days that you want WCS to retain the data. The default is 7days. The valid range is 1 to 30 days.
Client (days)—Enter the number of days that you want WCS to retain the data. The default is 7days. The valid range is 1 to 30 days.
•![]() Client (records)—Enter the number of client records that you want WCS to retain.
Client (records)—Enter the number of client records that you want WCS to retain.
•![]() Client session history (days)
Client session history (days)
•![]() Client session history (records)
Client session history (records)
Step 4 ![]() In some deployments, WCS may receive large amounts of client association and disassociation traps. Saving these traps as events may cause a slight performance issue. In such cases, other events that may be useful may be aged out sooner than expected.
In some deployments, WCS may receive large amounts of client association and disassociation traps. Saving these traps as events may cause a slight performance issue. In such cases, other events that may be useful may be aged out sooner than expected.
To ensure that WCS does not save client association and disassociation traps as events, clear the Save client association and disassociation traps as events check box.
Step 5 ![]() If you click the Poll clients when client traps received check box, WCS polls clients to quickly identify client sessions. In a busy network, you may want to disable polling while the client traps are received.
If you click the Poll clients when client traps received check box, WCS polls clients to quickly identify client sessions. In a busy network, you may want to disable polling while the client traps are received.
Step 6 ![]() Click Save.
Click Save.
CLI Session
Many WCS features such as autonomous access point and controller CLI templates, along with migration templates require executing CLI commands on the autonomous access point or controller. These CLI commands can be executed by establishing telnet or SSH sessions. The CLI session page allows you to select the session protocol. SSH is the default.
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose CLI Session.
From the left sidebar menu, choose CLI Session.
Step 3 ![]() The default SSH is selected. To instead choose Telnet, select that radio button.
The default SSH is selected. To instead choose Telnet, select that radio button.
Step 4 ![]() select
select
Step 5 ![]() Click Save.
Click Save.
Controller Upgrade Settings
The Controller Upgrade Settings page allows you to auto-refresh after a controller upgrade. Follow these steps to perform an auto-refresh.
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Controller Upgrade Settings (see Figure 18-24).
From the left sidebar menu, choose Controller Upgrade Settings (see Figure 18-24).
Figure 18-24 Controller Upgrade Settings

Step 3 ![]() Select the Auto refresh After Upgrade check box to automatically restore the configuration whenever there is a change in the WLC image.
Select the Auto refresh After Upgrade check box to automatically restore the configuration whenever there is a change in the WLC image.
Step 4 ![]() Determine the action WCS will take when a save config trap is received. When this option is enabled, you can choose to retain or delete the extra configurations present on the device but not on WCS. The setting is applied to all controllers managed by WCS. If you select the Auto Refresh on Save Config Trap check box on the Configure > Controllers > Properties > Settings page, it overrides this global setting.
Determine the action WCS will take when a save config trap is received. When this option is enabled, you can choose to retain or delete the extra configurations present on the device but not on WCS. The setting is applied to all controllers managed by WCS. If you select the Auto Refresh on Save Config Trap check box on the Configure > Controllers > Properties > Settings page, it overrides this global setting.

Note ![]() It may take up to 3 minutes for the automatic refresh to occur.
It may take up to 3 minutes for the automatic refresh to occur.
Step 5 ![]() Click Save.
Click Save.
Data Management
Follow the steps below to set retention periods for aggregated data used in timed calculations and network audit calculations. You can configure retention periods on an hourly, daily, and weekly basis.
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Data Management. The Data Management page appears (see Figure 18-25).
From the left sidebar menu, choose Data Management. The Data Management page appears (see Figure 18-25).
Figure 18-25 Data Management Page

Step 3 ![]() Specify the number of days to keep the hourly data. The valid range is 1 to 31.
Specify the number of days to keep the hourly data. The valid range is 1 to 31.
Step 4 ![]() Specify the number of days to keep the daily data. The valid range is 7 to 365.
Specify the number of days to keep the daily data. The valid range is 7 to 365.
Step 5 ![]() Specify the number of weeks to keep the weekly data. The valid range is 2 to 108.
Specify the number of weeks to keep the weekly data. The valid range is 2 to 108.
Step 6 ![]() Specify the number of days to retain the audit data collected by the Network Audit background task before purging. The limit is 90 days, and the minimum cleanup interval is 7 days.
Specify the number of days to retain the audit data collected by the Network Audit background task before purging. The limit is 90 days, and the minimum cleanup interval is 7 days.

Note ![]() For the best interactive graph data views, change the default settings to the maximum possible: 90 days for daily aggregated data and 54 weeks for weekly aggregated data. You must also make the appropriate measures to increase RAM and CPU capacity to compensate for these adjustments.
For the best interactive graph data views, change the default settings to the maximum possible: 90 days for daily aggregated data and 54 weeks for weekly aggregated data. You must also make the appropriate measures to increase RAM and CPU capacity to compensate for these adjustments.
Step 7 ![]() Click Save.
Click Save.
Guest Account Settings
The Guest Account Settings page allows you to globally remove all expired templates. Follow these steps to configure guest account settings.
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Guest Account Settings (see Figure 18-26).
From the left sidebar menu, choose Guest Account Settings (see Figure 18-26).
Figure 18-26 Guest Account Settings Page

Step 3 ![]() When the Automatically remove expired guest accounts option is selected, the guest accounts whose lifetime has ended are deleted from WCS. If this option is not selected, the expired accounts are moved to the Expired state.
When the Automatically remove expired guest accounts option is selected, the guest accounts whose lifetime has ended are deleted from WCS. If this option is not selected, the expired accounts are moved to the Expired state.
Step 4 ![]() By default, WCS Lobby Ambassador can access all guest accounts irrespective of who created them. If you select the Search and List only guest accounts created by this lobby ambassador check box, the Lobby Ambassadors can search and access only the guest accounts that have been created by them.
By default, WCS Lobby Ambassador can access all guest accounts irrespective of who created them. If you select the Search and List only guest accounts created by this lobby ambassador check box, the Lobby Ambassadors can search and access only the guest accounts that have been created by them.
Step 5 ![]() Click Save.
Click Save.
Login Disclaimer
The Login Disclaimer page allows you to enter disclaimer text at the top of the Login page for all users.
To enter Login Disclaimer text, follow these steps:
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Login Disclaimer. The Login Disclaimer page appears (see Figure 18-27).
From the left sidebar menu, choose Login Disclaimer. The Login Disclaimer page appears (see Figure 18-27).
Figure 18-27 Login Disclaimer Page

Step 3 ![]() Enter your Login Disclaimer text in the available text box.
Enter your Login Disclaimer text in the available text box.
Step 4 ![]() Click Save.
Click Save.
Mail Server Configuration
You can configure global e-mail parameters for sending e-mails from WCS reports, alarm notifications, and so on. This mail server page enables you to configure e-mail parameters in one place. The Mail Server page enables you to set the primary and secondary SMTP server host and port, the sender's e-mail address, and the recipient's e-mail addresses. Follow these steps to configure global e-mail parameters.

Note ![]() You must configure the global SMTP server before setting global e-mail parameters.
You must configure the global SMTP server before setting global e-mail parameters.
Step 1 ![]() Choose Administration > Setting.
Choose Administration > Setting.
Step 2 ![]() From the left sidebar menu, choose Mail Server Configuration. The page in Figure 18-28 appears.
From the left sidebar menu, choose Mail Server Configuration. The page in Figure 18-28 appears.
Figure 18-28 Mail Server Configuration Page

Step 3 ![]() Enter the host name of the primary SMTP server.
Enter the host name of the primary SMTP server.
Step 4 ![]() Enter the username of the SMTP server.
Enter the username of the SMTP server.
Step 5 ![]() Provide a password for logging on to the SMTP server and confirm it.
Provide a password for logging on to the SMTP server and confirm it.

Note ![]() Both Username and Password are optional.
Both Username and Password are optional.
Step 6 ![]() Provide the same information for the secondary SMTP server (only if a secondary mail server is available).
Provide the same information for the secondary SMTP server (only if a secondary mail server is available).
Step 7 ![]() The From text box in the Sender and Receivers portion of the page is populated with WCS@<WCS server IP address>. You can change it to a different sender.
The From text box in the Sender and Receivers portion of the page is populated with WCS@<WCS server IP address>. You can change it to a different sender.
Step 8 ![]() Enter the recipient's e-mail addresses in the To text box. The e-mail address you provide serves as the default value for other functional areas, such as alarms or reports. Multiple e-mail addresses can be added and should be separated by commas.
Enter the recipient's e-mail addresses in the To text box. The e-mail address you provide serves as the default value for other functional areas, such as alarms or reports. Multiple e-mail addresses can be added and should be separated by commas.

Note ![]() Global changes you make to the recipient e-mail addresses in Step 7 are disregarded if e-mail notifications were set.
Global changes you make to the recipient e-mail addresses in Step 7 are disregarded if e-mail notifications were set.
You must indicate the primary SMTP mail server and fill the From address text boxes.
If you want all alarm categories applied to the provided recipient list, select the Apply recipient list to all alarm categories check box.
Step 9 ![]() If you click the "Configure email notification for individual alarm categories" link, you can specify the alarm categories and severity levels you want to enable. Email notifications are sent when an alarm occurs that matches categories and the severity levels you select.
If you click the "Configure email notification for individual alarm categories" link, you can specify the alarm categories and severity levels you want to enable. Email notifications are sent when an alarm occurs that matches categories and the severity levels you select.

Note ![]() You can set each alarm severity by clicking the alarm category, choosing Critical, Major, Minor, or Warning, and providing an email address.
You can set each alarm severity by clicking the alarm category, choosing Critical, Major, Minor, or Warning, and providing an email address.
Step 10 ![]() Click the Test button to send a test e-mail using the parameters you configured. The results of the test operation appear on the same screen. The test feature checks the connectivity to both primary and secondary mail servers by sending an e-mail with a "WCS test e-mail" subject line.
Click the Test button to send a test e-mail using the parameters you configured. The results of the test operation appear on the same screen. The test feature checks the connectivity to both primary and secondary mail servers by sending an e-mail with a "WCS test e-mail" subject line.
Step 11 ![]() If the test results were satisfactory, click Save.
If the test results were satisfactory, click Save.
Notification Receiver
The Notification Receiver page displays current notification receivers that support guest access. Alerts and events are sent as SNMPv2 notifications to configured notification receivers.
In this page, you can view current or add additional notification receivers.
•![]() Adding a Notification Receiver to WCS
Adding a Notification Receiver to WCS
•![]() Removing a Notification Receiver
Removing a Notification Receiver
To access the Notification Receiver page, follow these steps:
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Notification Receivers. All currently configured servers appear in this page. If you want to add one, choose Add Notification Receiver from the Select a command drop-down list, and click Go (see Figure 18-29).
From the left sidebar menu, choose Notification Receivers. All currently configured servers appear in this page. If you want to add one, choose Add Notification Receiver from the Select a command drop-down list, and click Go (see Figure 18-29).
Figure 18-29 Notification Receiver Page

Adding a Notification Receiver to WCS
Follow these steps to view current or add additional notification receivers:
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Notification Receivers. All currently configured servers appear on this page.
From the left sidebar menu, choose Notification Receivers. All currently configured servers appear on this page.
Step 3 ![]() From the Select a command drop-down list, click Add Notification Receiver.
From the Select a command drop-down list, click Add Notification Receiver.
Step 4 ![]() Click Go (see Figure 18-30).
Click Go (see Figure 18-30).
Figure 18-30 Notification Receiver Page

Step 5 ![]() Enter the server IP address and name.
Enter the server IP address and name.
Step 6 ![]() Choose the receiver type between basic North Bound and Guest Access.
Choose the receiver type between basic North Bound and Guest Access.
Step 7 ![]() Choose the notification type as UDP or TCP. The default is UDP.
Choose the notification type as UDP or TCP. The default is UDP.
Step 8 ![]() Enter the UDP parameters including Port Number and Community.
Enter the UDP parameters including Port Number and Community.

Note ![]() The receiver that you configure must be listening to UDP on the same port that is configured.
The receiver that you configure must be listening to UDP on the same port that is configured.
Step 9 ![]() If you have selected North Bound as the receiver type, specify the criteria and severity.
If you have selected North Bound as the receiver type, specify the criteria and severity.

Note ![]() Alarms for only selected category will be processed.
Alarms for only selected category will be processed.

Note ![]() Alarms with only selected severity matching the selected categories will be processed.
Alarms with only selected severity matching the selected categories will be processed.
Step 10 ![]() Click Save to confirm the Notification Receiver information.
Click Save to confirm the Notification Receiver information.

Note![]() •
•![]() By default only INFO level events will be processed for selected Category.
By default only INFO level events will be processed for selected Category.
•![]() Only SNMPV2 traps will be considered for northbound notification.
Only SNMPV2 traps will be considered for northbound notification.
•![]() You need to allow TCP port 7 which is required for keepalive between WCS and the receiver server.
You need to allow TCP port 7 which is required for keepalive between WCS and the receiver server.
Removing a Notification Receiver
To delete a notification receiver, follow these steps:
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Notification Receivers. All currently configured servers appear on this page.
From the left sidebar menu, choose Notification Receivers. All currently configured servers appear on this page.
Step 3 ![]() Select the check box(es) of the notification receiver(s) that you want to delete.
Select the check box(es) of the notification receiver(s) that you want to delete.
Step 4 ![]() From the Select a command drop-down list, click Remove Notification Receiver.
From the Select a command drop-down list, click Remove Notification Receiver.
Step 5 ![]() Click Go.
Click Go.
Step 6 ![]() Click OK to confirm the deletion.
Click OK to confirm the deletion.
The sample display from a northbound SNMP receiver that has received event traps from WCS is as follows:
Figure 18-31 Sample display from a northbound SNMP receiver

The sample output below shows the log file generated by WCS. This log file is located in the log file directory on the WCS server (/opt/WCS7.0.28.0/webnms/logs). The log output helps you troubleshoot when alarms are not being received by the northbound SNMP receiver.
06/04/10 08:30:58.559 INFO[com.cisco.wcslogger.services] : [NBNotificationService$NbOrderQueue][addNbAlarm]Adding into queue
06/04/10 08:30:58.560 INFO[com.cisco.wcslogger.services] : [NBNotificationService$NbOrderQueue][addNbAlarm]incrTotalNotifications2
06/04/10 08:30:58.560 INFO[com.cisco.wcslogger.services] : [NBNotificationService$NbOrderQueue][addNbAlarm]incrHandledInNotification2
06/04/10 08:30:58.560 INFO[com.cisco.wcslogger.services] : [NBNotificationService$NbOrderQueue][addNbAlarm]incrNonCongestedIn2
06/04/10 08:30:58.560 INFO[com.cisco.wcslogger.services] : [NBNotificationService][addNBAlert]Added into queue
06/04/10 08:30:58.561 INFO[com.cisco.wcslogger.services] : [NBNotificationService$NbOrderQueue][getNbAlarm]incrHandledOutNotification2
06/04/10 08:30:58.561 INFO[com.cisco.wcslogger.services] : [NBNotificationService][startNotifier]Processing the alertNoiseProfile_LradIf!00:17:df:a9:c8:30!0
06/04/10 08:30:58.561 INFO[com.cisco.wcslogger.notification] : [NbAlertToNmsAlertCorrelator][formVarBindList]Generating the varbind list for NB
06/04/10 08:30:58.562 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.2.1.1.3.0 variable value: 10 days, 20:22:17.26
06/04/10 08:30:58.562 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.6.3.1.1.4.1.0 variable value: 1.3.6.1.4.1.9.9.199991.0.1
06/04/10 08:30:58.562 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.2 variable value: 07:da:05:18:0c:30:0d:09:2d:07:00
06/04/10 08:30:58.563 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.3 variable value: 07:da:06:04:08:1e:3a:04:2d:07:00
06/04/10 08:30:58.563 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.4 variable value: NoiseProfile_LradIf!00:17:df:a9:c8:30!0
06/04/10 08:30:58.563 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.5 variable value: 2
06/04/10 08:30:58.563 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.6 variable value: Radio load threshold violation
06/04/10 08:30:58.563 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.7 variable value: 1
06/04/10 08:30:58.564 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.8 variable value: 172.19.29.112
06/04/10 08:30:58.564 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.9 variable value: AP 1250-LWAP-ANGN-170-CMR, Interface 802.11b/g/n
06/04/10 08:30:58.564 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.10 variable value: Noise changed to acceptable level on '802.11b/g/n' interface of AP '1250-LWAP-ANGN-170-CMR', connected to Controller '172.19.29.112'.
06/04/10 08:30:58.564 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.11 variable value: 1
06/04/10 08:30:58.564 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.12 variable value:
06/04/10 08:30:58.565 INFO[com.cisco.wcslogger.notification] : [NBUtil][printVarBind]Variable OID: 1.3.6.1.4.1.9.9.199991.1.1.2.1.14 variable value:
06/04/10 08:30:58.573 INFO[com.cisco.wcslogger.notification] : [NBUtil][sendTrap]OSS list size with reachability status as up1
06/04/10 08:30:58.573 INFO[com.cisco.wcslogger.notification] : [NBUtil][sendTrap]Sending UDP Notification for receiver:172.19.27.85 on port:162
MIB to WCS alert/event mapping
Table 18-3 summarizes the Cisco-WCS-Notification-MIB to WCS alert/event mapping.
Report
Follow these steps to indicate where the scheduled reports will reside and for how many days:
Step 1 ![]() Choose Administration > Setting.
Choose Administration > Setting.
Step 2 ![]() From the left sidebar menu, choose Report. The Report page appears (see Figure 18-32).
From the left sidebar menu, choose Report. The Report page appears (see Figure 18-32).
Figure 18-32 Report Page

Step 3 ![]() Enter the path for saving report data files on a local PC. You can edit the existing default path.
Enter the path for saving report data files on a local PC. You can edit the existing default path.
Step 4 ![]() Specify the number of days to retain report data files.
Specify the number of days to retain report data files.
Step 5 ![]() Click Save.
Click Save.
Server Settings
Follow these steps to turn TFTP, FTP, HTTP, or HTTPS on or off:
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Server Setting. The Server Setting page appears (see Figure 18-33).
From the left sidebar menu, choose Server Setting. The Server Setting page appears (see Figure 18-33).
Figure 18-33 Server Settings Page

Step 3 ![]() If you want to modify the FTP and TFTP directories or the HTTP and HTTPS ports that were established during installation, enter the port number (or port number and root where required) that you want to modify and click Enable or Disable.
If you want to modify the FTP and TFTP directories or the HTTP and HTTPS ports that were established during installation, enter the port number (or port number and root where required) that you want to modify and click Enable or Disable.
The changes are reflected after a restart.
Severity Configurations
You can change the severity level for newly generated alarms.

Note ![]() Existing alarms remain unchanged.
Existing alarms remain unchanged.
To change the severity level of newly generated alarms, follow these steps:
Step 1 ![]() Choose Administration > Setting.
Choose Administration > Setting.
Step 2 ![]() Choose Severity Configuration from the left sidebar menu. The Severity Configuration page appears (see Figure 18-34).
Choose Severity Configuration from the left sidebar menu. The Severity Configuration page appears (see Figure 18-34).
Figure 18-34 Severity Configuration Page

Step 3 ![]() Choose the check box of the alarm condition whose severity level you want to change.
Choose the check box of the alarm condition whose severity level you want to change.
Step 4 ![]() From the Configure Severity Level drop-down list, choose the new severity level (Critical, Major, Minor, Warning, Informational, Reset to Default).
From the Configure Severity Level drop-down list, choose the new severity level (Critical, Major, Minor, Warning, Informational, Reset to Default).
Step 5 ![]() Click Go.
Click Go.
Step 6 ![]() Click OK to confirm the change.
Click OK to confirm the change.
SNMP Credentials
The SNMP Credentials page allows you to specify credentials to use for tracing the rogue access points. Use this option when you cannot find a specific entry using a number-based entry. When a switch credential is not added to WCS, you can use SNMP credentials on this page to connect to the switch.
To configure SNMP credentials, follow these steps:
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose SNMP Credentials.
From the left sidebar menu, choose SNMP Credentials.
Step 3 ![]() Perform one of the following:
Perform one of the following:
•![]() To add a new SNMP entry, select Add SNMP Entries from the Select a command drop-down list, and click Go. The Credentials Details page appears.
To add a new SNMP entry, select Add SNMP Entries from the Select a command drop-down list, and click Go. The Credentials Details page appears.
•![]() To modify an existing SNMP credential, click the Network Address link. The SNMP Credential Details page appears (see Figure 18-35). An SNMP credential is defined per network so only network addresses are allowed. 0.0.0.0 is the SNMP credential default and is used when no specific SNMP credential is defined. The default community string is private for both read and write. You should update the pre-populated SNMP credential with your own SNMP information.
To modify an existing SNMP credential, click the Network Address link. The SNMP Credential Details page appears (see Figure 18-35). An SNMP credential is defined per network so only network addresses are allowed. 0.0.0.0 is the SNMP credential default and is used when no specific SNMP credential is defined. The default community string is private for both read and write. You should update the pre-populated SNMP credential with your own SNMP information.
Figure 18-35 SNMP Credential Details Page

Step 4 ![]() Choose one of the following:
Choose one of the following:
If you want to add SNMP credentials or use commas to separate multiple SNMP credentials, leave the Add Format Type drop-down list at SNMP Credential Info.
If you want to add multiple SNMP credentials by importing a CSV file, choose File from the Add Format Type drop-down list. The CSV file allows you to generate your own import file and add the devices you want.
Step 5 ![]() If you chose SNMP Credential Info, enter the network address of the SNMP credential you want to add. If you want to add multiple SNMP credentials, use commas between network addresses. Make sure that SNMP credentials are correct so that switch port tracing executes as expected.
If you chose SNMP Credential Info, enter the network address of the SNMP credential you want to add. If you want to add multiple SNMP credentials, use commas between network addresses. Make sure that SNMP credentials are correct so that switch port tracing executes as expected.
During SPT, if WCS finds switches and connects to them, WCS saves the switches internally. These switches are displayed in Configure > Ethernet Switches. When you update the SNMP credentials, the automatically added switches get deleted.
Step 6 ![]() If you chose File, click Browse to find the location of the CSV file you want to import. The first row of the CSV file is used to describe the columns included. The IP address column is mandatory.
If you chose File, click Browse to find the location of the CSV file you want to import. The first row of the CSV file is used to describe the columns included. The IP address column is mandatory.
Sample File:
ip_address,snmpv1_community,snmpv2_community,snmpv3_user_name,snmpv3_auth_type,snmpv3_auth _password,snmpv3_privacy_type,snmpv3_privacy_password,network_mask 209.165.200.224,private,private,user1,HMAC-MD5,12345,DES,12345,255.255.255.224 209.165.200.225,private,private,user1,HMAC-MD5,password3,DES,password4,255.255.255.224 209.165.200.226,private,private,user1,HMAC-MD5,12345,DES,12345,255.255.255.224
The CSV file can contain the following fields:
•![]() ip_address: IP address
ip_address: IP address
•![]() network_mask: Network mask
network_mask: Network mask
•![]() snmpv1_community: SNMP V1 community
snmpv1_community: SNMP V1 community
•![]() snmpv2_community: SNMP V2 community
snmpv2_community: SNMP V2 community
•![]() snmpv3_user_name: SNMP V3 user name
snmpv3_user_name: SNMP V3 user name
•![]() snmpv3_auth_type: SNMP V3 authorization type. Can be None or HMAC-MD5 or HMAC-SHA
snmpv3_auth_type: SNMP V3 authorization type. Can be None or HMAC-MD5 or HMAC-SHA
•![]() snmpv3_auth_password: SNMP V3 authorization password
snmpv3_auth_password: SNMP V3 authorization password
•![]() snmpv3_privacy_type: SNMP V3 privacy type. Can be None or DES or CFB-AES-128
snmpv3_privacy_type: SNMP V3 privacy type. Can be None or DES or CFB-AES-128
•![]() snmpv3_privacy_password: SNMP V3 privacy password snmp_retries:SNMP retries
snmpv3_privacy_password: SNMP V3 privacy password snmp_retries:SNMP retries
•![]() snmp_timeout: SNMP timeout
snmp_timeout: SNMP timeout
Step 7 ![]() In the Retries parameter, enter the number of times an attempt is made to discover the switch.
In the Retries parameter, enter the number of times an attempt is made to discover the switch.

Note ![]() Enter SNMP parameters for write access, if available. With read-only access parameters, the switch is added but you will not be able to modify its configuration in WCS. Device connectivity tests use the SNMP retries and timeout parameters configured in Administration > Settings > SNMP Settings.
Enter SNMP parameters for write access, if available. With read-only access parameters, the switch is added but you will not be able to modify its configuration in WCS. Device connectivity tests use the SNMP retries and timeout parameters configured in Administration > Settings > SNMP Settings.
Step 8 ![]() Enter the session timeout value in seconds. This value is the maximum amount of time allowed for a client before it must reauthenticate.
Enter the session timeout value in seconds. This value is the maximum amount of time allowed for a client before it must reauthenticate.
Step 9 ![]() If SNMP v1 or v2 with default community is configured, the network is open to easy attacks because default communities are well known. SNMP v1 or v2 with a non-default community is more secure than a default community, but SNMP v3 with Auth and Privacy type and no default user is the most secure SNMP connection.
If SNMP v1 or v2 with default community is configured, the network is open to easy attacks because default communities are well known. SNMP v1 or v2 with a non-default community is more secure than a default community, but SNMP v3 with Auth and Privacy type and no default user is the most secure SNMP connection.
Step 10 ![]() Click OK.
Click OK.
If WCS can use the SNMP credential listed to access the switch, the switch is added for later use and will appear on the Configure > Ethernet Switches page.

Note ![]() If you manually added switches through the Configure > Ethernet Switches page, switch port tracing will use the credentials from that page, not the ones listed on the SNMP Credentials page. If the manually added switch credentials have changed, you need to update them from the Configure > Ethernet page.
If you manually added switches through the Configure > Ethernet Switches page, switch port tracing will use the credentials from that page, not the ones listed on the SNMP Credentials page. If the manually added switch credentials have changed, you need to update them from the Configure > Ethernet page.
SNMP Settings
The SNMP Settings page allows you to configure global SNMP settings from WCS.

Note ![]() Any changes you make on this screen globally effect WCS. The changes are saved across restarts as well as across backups and restores.
Any changes you make on this screen globally effect WCS. The changes are saved across restarts as well as across backups and restores.
Follow these steps to configure global SNMP settings:
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose SNMP Settings. The SNMP Settings page appears (see Figure 18-36).
From the left sidebar menu, choose SNMP Settings. The SNMP Settings page appears (see Figure 18-36).
Figure 18-36 SNMP Settings Page

Step 3 ![]() If Trace Display Values is selected, mediation trace-level logging shows data values fetched from the controller using SNMP. If unselected, the values do not appear.
If Trace Display Values is selected, mediation trace-level logging shows data values fetched from the controller using SNMP. If unselected, the values do not appear.

Note ![]() The default is unselected for security reasons.
The default is unselected for security reasons.
Step 4 ![]() For the Backoff Algorithm, choose either Exponential or Constant Timeout from the drop-down list. If you choose Exponential (the default value), each SNMP try waits twice as long as the previous try, starting with the specified timeout for the first try. If you choose Constant Timeout, each SNMP try waits the same, specified amount of time.
For the Backoff Algorithm, choose either Exponential or Constant Timeout from the drop-down list. If you choose Exponential (the default value), each SNMP try waits twice as long as the previous try, starting with the specified timeout for the first try. If you choose Constant Timeout, each SNMP try waits the same, specified amount of time.

Note ![]() Constant Timeout is useful on unreliable networks (such as satellite networks) where the desired number of retries is large. Because it does not double the timeout per try, it does not take as long to timeout with a high number of retries.
Constant Timeout is useful on unreliable networks (such as satellite networks) where the desired number of retries is large. Because it does not double the timeout per try, it does not take as long to timeout with a high number of retries.
Step 5 ![]() Determine if you want to use reachability parameters. If selected, the WCS defaults to the global Reachability Retries and Timeout that you configure. If unselected, WCS always uses the timeout and retries specified per-controller or per-IOS access point. The default is selected.
Determine if you want to use reachability parameters. If selected, the WCS defaults to the global Reachability Retries and Timeout that you configure. If unselected, WCS always uses the timeout and retries specified per-controller or per-IOS access point. The default is selected.

Note ![]() Adjust this setting downward if switch port tracing is taking a long time to complete.
Adjust this setting downward if switch port tracing is taking a long time to complete.
Step 6 ![]() For the Reachability Retries parameter, enter the number of global retries used for determining device reachability. The default number is 2. This parameter is only available if the Use Reachability Parameters check box is selected.
For the Reachability Retries parameter, enter the number of global retries used for determining device reachability. The default number is 2. This parameter is only available if the Use Reachability Parameters check box is selected.

Note ![]() Adjust this setting downward if switch port tracing is taking a long time to complete.
Adjust this setting downward if switch port tracing is taking a long time to complete.
Step 7 ![]() For the Reachability Timeout parameter, enter a global timeout used for determining device reachability. The default number is 2. This parameter is only available if the Use Reachability Parameters check box is selected.
For the Reachability Timeout parameter, enter a global timeout used for determining device reachability. The default number is 2. This parameter is only available if the Use Reachability Parameters check box is selected.
Step 8 ![]() At the Maximum VarBinds per PDU parameter, enter a number to indicate the largest number of SNMP variable bindings allowed in a request or response PDU. The default is 100.
At the Maximum VarBinds per PDU parameter, enter a number to indicate the largest number of SNMP variable bindings allowed in a request or response PDU. The default is 100.

Note ![]() For customers who have issues with PDU fragmentation in their network, this number can be reduced to 50, which typically eliminates the fragmentation.
For customers who have issues with PDU fragmentation in their network, this number can be reduced to 50, which typically eliminates the fragmentation.
Step 9 ![]() Click Save to confirm these settings.
Click Save to confirm these settings.
Switch Port Trace
The Switch Port Trace page allows you to run a trace on detected rogue access points on the wire.
To correctly trace and contain rogue access points, you must correctly provide the following information.
•![]() Reporting APs—A rogue access point has to be reported by one or more managed access points.
Reporting APs—A rogue access point has to be reported by one or more managed access points.
•![]() AP CDP Neighbor—Access point CDP neighbor information is required to determine the seed switches.
AP CDP Neighbor—Access point CDP neighbor information is required to determine the seed switches.
•![]() Switch IP address and SNMP credentials—All switches to be traced must have a management IP address and SNMP management enabled. You can add network address based entries instead of only adding individual switches. The correct write community string must be specified to enable/disable switch ports. For tracing, read community strings are sufficient.
Switch IP address and SNMP credentials—All switches to be traced must have a management IP address and SNMP management enabled. You can add network address based entries instead of only adding individual switches. The correct write community string must be specified to enable/disable switch ports. For tracing, read community strings are sufficient.
•![]() Switch port configuration—Trunking switch ports must be correctly configured. Switch port security must be turned off.
Switch port configuration—Trunking switch ports must be correctly configured. Switch port security must be turned off.
•![]() Only Cisco Ethernet switches are supported.
Only Cisco Ethernet switches are supported.
•![]() Switch VLAN settings must be properly configured.
Switch VLAN settings must be properly configured.
•![]() CDP protocol must be enabled on all switches.
CDP protocol must be enabled on all switches.
•![]() An Ethernet connection must exist between the rogue access point and the Cisco switch.
An Ethernet connection must exist between the rogue access point and the Cisco switch.
•![]() You should have some traffic between rogue access points and the Ethernet switch.
You should have some traffic between rogue access points and the Ethernet switch.
•![]() The rogue access point must be connected to a switch within the max hop limit. The default hop count is 2, and the maximum is 10.
The rogue access point must be connected to a switch within the max hop limit. The default hop count is 2, and the maximum is 10.
•![]() If SNMPv3 is chosen, use the context option and create one for each VLAN, in addition to the one for the main group (which is required for non-VLAN-based MIBs).
If SNMPv3 is chosen, use the context option and create one for each VLAN, in addition to the one for the main group (which is required for non-VLAN-based MIBs).
Follow these steps to specify options for switch port tracing.
Step 1 ![]() Choose Administration > Settings.
Choose Administration > Settings.
Step 2 ![]() From the left sidebar menu, choose Switch Port Trace (see Figure 18-37).
From the left sidebar menu, choose Switch Port Trace (see Figure 18-37).
Figure 18-37 Switch Port Trace Page

Step 3 ![]() Configure the following basic settings as needed:
Configure the following basic settings as needed:
•![]() MAC address +1/-1 search—Select the check box to enable.
MAC address +1/-1 search—Select the check box to enable.
This search involves the MAC address +1/-1 convention where the wired-side MAC address of the rogue access point is obtained by adding or subtracting the radio MAC address by one.
•![]() Rogue client MAC address search—Select the check box to enable.
Rogue client MAC address search—Select the check box to enable.
When a rogue access point client exists, the MAC address of the client is added to the searchable MAC address list.
•![]() Vendor (OUI) search—Select the check box to enable. OUI refers to Organizational Unique Identifier search which searches the first 3 bytes in a MAC address.
Vendor (OUI) search—Select the check box to enable. OUI refers to Organizational Unique Identifier search which searches the first 3 bytes in a MAC address.
•![]() Exclude switch trunk ports—Select the check box to exclude switch trunk ports from the switch port trace.
Exclude switch trunk ports—Select the check box to exclude switch trunk ports from the switch port trace.

Note ![]() When more than one port is traced for a given MAC address, additional checks are performed to improve accuracy. These checks include: trunk port, non-AP CDP neighbors present on the port, and whether or not the MAC address is the only one on this port.
When more than one port is traced for a given MAC address, additional checks are performed to improve accuracy. These checks include: trunk port, non-AP CDP neighbors present on the port, and whether or not the MAC address is the only one on this port.
•![]() Exclude device list—Select the check box to exclude additional devices from the trace. Enter into the device list text box each device that you want to exclude from the switch port trace. Separate each device names with commas.
Exclude device list—Select the check box to exclude additional devices from the trace. Enter into the device list text box each device that you want to exclude from the switch port trace. Separate each device names with commas.
•![]() Max hop count—Enter the maximum number of hops for this trace. Keep in mind that the greater the hop count, the longer the switch port trace will take to perform.
Max hop count—Enter the maximum number of hops for this trace. Keep in mind that the greater the hop count, the longer the switch port trace will take to perform.
•![]() Exclude vendor list—Enter in the vendor list text box any vendors that you want to exclude from the switch port trace. Separate vendor names with commas. The vendor list is not case sensitive.
Exclude vendor list—Enter in the vendor list text box any vendors that you want to exclude from the switch port trace. Separate vendor names with commas. The vendor list is not case sensitive.
Step 4 ![]() Configure the following advanced settings as needed:
Configure the following advanced settings as needed:
•![]() TraceRogueAP task max thread—Switch port tracing uses multiple threads to trace rogue access points. This field indicates the maximum number of rogue access points that can be traced on parallel threads.
TraceRogueAP task max thread—Switch port tracing uses multiple threads to trace rogue access points. This field indicates the maximum number of rogue access points that can be traced on parallel threads.
•![]() TraceRogueAP max queue size—Switch port tracing maintains a queue to trace rogue access points. Whenever you select a rogue access point for tracing, it is queued for processing. This field indicates the maximum number of entries that you can store in the queue.
TraceRogueAP max queue size—Switch port tracing maintains a queue to trace rogue access points. Whenever you select a rogue access point for tracing, it is queued for processing. This field indicates the maximum number of entries that you can store in the queue.
•![]() SwitchTask max thread—Switch port tracing uses multiple threads to query switch devices. This field indicates the maximum number of switch devices that you can query on parallel threads.
SwitchTask max thread—Switch port tracing uses multiple threads to query switch devices. This field indicates the maximum number of switch devices that you can query on parallel threads.

Note ![]() The default value for these parameters should be good for normal operations. These parameters directly impact the performance of switch port tracing and WCS. Unless required, Cisco does not recommend that you alter these parameters.
The default value for these parameters should be good for normal operations. These parameters directly impact the performance of switch port tracing and WCS. Unless required, Cisco does not recommend that you alter these parameters.
•![]() Select CDP device capabilities—Select the check box to enable.
Select CDP device capabilities—Select the check box to enable.

Note ![]() WCS uses CDP to discover neighbors during tracing. When the neighbors are verified, WCS uses the CDP capabilities field to determine whether or not the neighbor device is a valid switch. If the neighbor device is not a valid switch, it is not traced.
WCS uses CDP to discover neighbors during tracing. When the neighbors are verified, WCS uses the CDP capabilities field to determine whether or not the neighbor device is a valid switch. If the neighbor device is not a valid switch, it is not traced.
Step 5 ![]() Click Save to confirm changes made. Click Reset to return the page to the original settings. Click Factory Reset to return settings to the factory defaults.
Click Save to confirm changes made. Click Reset to return the page to the original settings. Click Factory Reset to return settings to the factory defaults.
High Availability
To ensure continued operation in case of failure, WCS now provides a high availability (or failover framework). When an active (primary) WCS fails, a secondary WCS takes over operations (in less than two minutes) for the failed primary WCS and continues to provide service. Upon failover, a peer of the failed primary WCS is activated on the secondary WCS using the local database and files, and the secondary WCS runs a fully functional WCS. While the secondary host is in failover mode, the database and file backups of other primary WCSs continue uninterrupted.
To activate and use high availability, you must buy a high availability license. The license is deployed on each primary WCS that is supported by a secondary WCS. After the license is validated, you must configure parameters on the WCS administration interface (see the "Configuring High Availability" section).
Failover Scenario
When a failure of a primary WCS is automatically detected, the following events take place:

Note ![]() One physical secondary WCS can back many primary WCSs.
One physical secondary WCS can back many primary WCSs.
1. ![]() The primary WCS is confirmed as non-functioning (hardware crash, network crash, or the like) by the health monitor on the secondary WCS.
The primary WCS is confirmed as non-functioning (hardware crash, network crash, or the like) by the health monitor on the secondary WCS.
2. ![]() If automatic failover has been enabled, WCS is started on the secondary as described in Step 3. If automatic failover is disabled, an email is sent to the administrator asking if they want to manually start failover.
If automatic failover has been enabled, WCS is started on the secondary as described in Step 3. If automatic failover is disabled, an email is sent to the administrator asking if they want to manually start failover.
3. ![]() The secondary WCS instance is started immediately (using the configuration already in place) and uses the corresponding database of the primary. After a successful failover, the client should point to the newly activated WCS (the secondary WCS). The secondary WCS updates all controllers with its own address as the trap destination.
The secondary WCS instance is started immediately (using the configuration already in place) and uses the corresponding database of the primary. After a successful failover, the client should point to the newly activated WCS (the secondary WCS). The secondary WCS updates all controllers with its own address as the trap destination.

Note ![]() The redirecting of web traffic to the secondary WCS does not occur automatically. You must use your infrastructure tools to properly configure this redirection.
The redirecting of web traffic to the secondary WCS does not occur automatically. You must use your infrastructure tools to properly configure this redirection.
MSEs that were served from the primary WCS are now served by the secondary WCS. Any Navigators in the network start monitoring the secondary WCS.
4. ![]() The result of the failover operation is indicated as an event in the Health Monitor UI, or a critical alarm is sent to the administrator and to other WCS instances.
The result of the failover operation is indicated as an event in the Health Monitor UI, or a critical alarm is sent to the administrator and to other WCS instances.
Prerequisites and Limitations
Before initiating failover, you must consider the following prerequisites and limitations:
•![]() You must have the extra hardware identical to the primary WCS to run a stand-by instance of WCS.
You must have the extra hardware identical to the primary WCS to run a stand-by instance of WCS.
•![]() This design is based on the software-based WCS and does not accommodate appliance-based WCS.
This design is based on the software-based WCS and does not accommodate appliance-based WCS.
•![]() The presence of Navigator is considered so that multi-WCS deployments are accommodated.
The presence of Navigator is considered so that multi-WCS deployments are accommodated.
•![]() A reliable high-speed wired network must exist between the primary WCS and its backup WCS.
A reliable high-speed wired network must exist between the primary WCS and its backup WCS.
•![]() The primary and secondary WCS must be running the same WCS software release.
The primary and secondary WCS must be running the same WCS software release.
•![]() WCS supports both Windows- or Linux-based platforms. However, for this failover design, all WCSs in the primary-secondary group must run on the same operating system (either Windows or Linux).
WCS supports both Windows- or Linux-based platforms. However, for this failover design, all WCSs in the primary-secondary group must run on the same operating system (either Windows or Linux).
•![]() Failover should be considered temporary. The failed primary WCS should be restored to normal as soon as possible, and failback will be re-initiated. The longer it takes to restore the failed primary WCS, the longer the other WCSs sharing that secondary WCS must run without failover support.
Failover should be considered temporary. The failed primary WCS should be restored to normal as soon as possible, and failback will be re-initiated. The longer it takes to restore the failed primary WCS, the longer the other WCSs sharing that secondary WCS must run without failover support.
•![]() The latest controller software must be used.
The latest controller software must be used.
•![]() The primary and secondary host are not required to share the same subnet. They can be geographically separated.
The primary and secondary host are not required to share the same subnet. They can be geographically separated.
•![]() If a secondary host fails for any reason, all the primary instances are affected, and they run in stand-alone mode without any failover support.
If a secondary host fails for any reason, all the primary instances are affected, and they run in stand-alone mode without any failover support.
•![]() The ports over which the primary and secondary WCSs communicate must be open (not blocked with network firewalls, application fireways, gateways, and so on). The tomcat port is configurable during installation, and its default port is 8082. You should reserve solid database ports from 1315 to 1319.
The ports over which the primary and secondary WCSs communicate must be open (not blocked with network firewalls, application fireways, gateways, and so on). The tomcat port is configurable during installation, and its default port is 8082. You should reserve solid database ports from 1315 to 1319.
•![]() Any access control lists imposed between the primary and secondary WCS must allow traffic to go between the primary and secondary WCSs.
Any access control lists imposed between the primary and secondary WCS must allow traffic to go between the primary and secondary WCSs.
•![]() In a 2:1 high availability scenario, the secondary WCS must be a high-end PC with more memory than the two primary PCs.
In a 2:1 high availability scenario, the secondary WCS must be a high-end PC with more memory than the two primary PCs.
Configuring High Availability

Note ![]() When database transaction logs grow to 1/3 of the database partition disk space, set the database to "Standalone" mode to prevent transaction logs from keep growing. But it requires a complete netcopy next time when the database synchronization occurs.
When database transaction logs grow to 1/3 of the database partition disk space, set the database to "Standalone" mode to prevent transaction logs from keep growing. But it requires a complete netcopy next time when the database synchronization occurs.
Follow these steps to configure high availability on the primary WCS. See the "Installing WCS for Windows" section to see the installation steps.

Note ![]() Before you configure high availability, you must configure a mail server. See the "Mail Server Configuration" section for steps on configuring a mail server.
Before you configure high availability, you must configure a mail server. See the "Mail Server Configuration" section for steps on configuring a mail server.
Step 1 ![]() Choose Administration > High Availability.
Choose Administration > High Availability.
Step 2 ![]() Choose HA Configuration from the left sidebar menu. The High Availability Configuration page appears (see Figure 18-38).
Choose HA Configuration from the left sidebar menu. The High Availability Configuration page appears (see Figure 18-38).
Figure 18-38 High Availability Configuration Page

The current status of high availability is shown in the upper portion of the page.
Step 3 ![]() Enter the IP address or hostname of the secondary WCS.
Enter the IP address or hostname of the secondary WCS.
Step 4 ![]() Enter the authentication key specified during the installation of the secondary WCS.
Enter the authentication key specified during the installation of the secondary WCS.
Step 5 ![]() The default admin email address that you configured in Administration > Settings > Email Server is automatically supplied. You can make any necessary changes. Any changes you make to these email addresses must also be entered in the Secondary SMTP Server section of the Administration > Settings > Mail Server page.
The default admin email address that you configured in Administration > Settings > Email Server is automatically supplied. You can make any necessary changes. Any changes you make to these email addresses must also be entered in the Secondary SMTP Server section of the Administration > Settings > Mail Server page.

Note ![]() You must enter an email address when configuring high availability. WCS tests the email server configuration, and if the test fails (because the mail server cannot connect), WCS does not allow the high availability configuration.
You must enter an email address when configuring high availability. WCS tests the email server configuration, and if the test fails (because the mail server cannot connect), WCS does not allow the high availability configuration.
Step 6 ![]() Choose either a manual or automatic failover option. If you choose manual, you can trigger the failover operation with a button in the secondary HealthMonitor GUI or with the URL specified in the email which the administrator receives upon failure of the primary WCS. If you choose automatic, the secondary WCS initiates a failover on its own when a failure is detected on the primary.
Choose either a manual or automatic failover option. If you choose manual, you can trigger the failover operation with a button in the secondary HealthMonitor GUI or with the URL specified in the email which the administrator receives upon failure of the primary WCS. If you choose automatic, the secondary WCS initiates a failover on its own when a failure is detected on the primary.
Step 7 ![]() Click Save Only to retain the configuration but not enable high availability at the current time, or click Save & Enable to enable high availability.
Click Save Only to retain the configuration but not enable high availability at the current time, or click Save & Enable to enable high availability.
At this point, the secondary is either reachable with the database, and files are synchronized between health monitors, or the secondary is unreachable, and an error is returned because secondary installation did not occur.
From the WCS GUI (Administration > High Availability) after high availability has been enabled, you can perform the following functions:
•![]() Update—Use the Update function to make changes to the Report Repository path (Administration > Settings > Report) or FTP/TFTP root directory (Administration > Settings > Server Settings) and to appropriately synchronize the files.
Update—Use the Update function to make changes to the Report Repository path (Administration > Settings > Report) or FTP/TFTP root directory (Administration > Settings > Server Settings) and to appropriately synchronize the files.
•![]() Disable—Use the Disable function to break the connection between the primary and secondary WCSs. The database and files stop synchronizing.
Disable—Use the Disable function to break the connection between the primary and secondary WCSs. The database and files stop synchronizing.
•![]() Delete—Use the Delete operation to decommission the primary WCS from the secondary WCS.
Delete—Use the Delete operation to decommission the primary WCS from the secondary WCS.
•![]() Cancel—User the Cancel operation to cancel any modifications you made to the high availability configuration. You are returned to the High Availability Status page after you choose Cancel.
Cancel—User the Cancel operation to cancel any modifications you made to the high availability configuration. You are returned to the High Availability Status page after you choose Cancel.
Deploying High Availability
Follow these steps to deploy high availability on an existing WCS installation.
Step 1 ![]() Identify and prepare the hardware to run the secondary WCS.
Identify and prepare the hardware to run the secondary WCS.
Step 2 ![]() Ensure that network connectivity between the primary and secondary WCS is functioning, and all necessary ports are open.
Ensure that network connectivity between the primary and secondary WCS is functioning, and all necessary ports are open.
Step 3 ![]() Install the secondary WCS with the same version of WCS that is installed on the primary. See the "Installing WCS for Windows" section.
Install the secondary WCS with the same version of WCS that is installed on the primary. See the "Installing WCS for Windows" section.
Step 4 ![]() Start the secondary WCS as a standby server. In this mode, the WCS application does not start. At the same time, the Health Monitor is started on the secondary WCS.
Start the secondary WCS as a standby server. In this mode, the WCS application does not start. At the same time, the Health Monitor is started on the secondary WCS.
Step 5 ![]() On every primary WCS that needs to use this secondary WCS, stop the WCS.
On every primary WCS that needs to use this secondary WCS, stop the WCS.
Step 6 ![]() On the primary host, install the new version of WCS and perform all necessary upgrade steps.
On the primary host, install the new version of WCS and perform all necessary upgrade steps.
Step 7 ![]() Start the primary WCS (as a primary). See the "Starting WCS" section. The Health Monitor also starts.
Start the primary WCS (as a primary). See the "Starting WCS" section. The Health Monitor also starts.
Step 8 ![]() Configure the high availability parameters described in the "Configuring High Availability" section.
Configure the high availability parameters described in the "Configuring High Availability" section.
Step 9 ![]() Click Activate to activate high availability on the primary. WCS primary first copies its database to the secondary WCS and then connects to the secondary. The following files are copied over from the primary to the secondary WCS:
Click Activate to activate high availability on the primary. WCS primary first copies its database to the secondary WCS and then connects to the secondary. The following files are copied over from the primary to the secondary WCS:
•![]() DB password file
DB password file
•![]() all auto provisioning startup config files
all auto provisioning startup config files
•![]() all domain maps
all domain maps
•![]() all history reports which are generated by scheduled report tasks
all history reports which are generated by scheduled report tasks
High availability deployment is complete. Use https://<wcsip>:8082 to access the HealthMonitor UI. Within the HealthMonitor UI, use the authentication key to login.
You can change the authentication key in WCS using the command prompt. To change the authentication key, change the path to WCS installation directory then to "bin" and enter hmadmin - authkey key.
To view the current status of the health monitor, enter hmadmin [-options] status.
Adding a New Primary WCS
Follow these steps to add a new primary WCS to an existing setup. This new primary WCS uses the existing secondary as the failover server.
Step 1 ![]() Ensure that network connectivity between the new primary and secondary is functioning and that all necessary ports are open.
Ensure that network connectivity between the new primary and secondary is functioning and that all necessary ports are open.
Step 2 ![]() Make sure that the same WCS release that is loaded on the other primary WCS and secondary WCS is loaded on the new primary WCS.
Make sure that the same WCS release that is loaded on the other primary WCS and secondary WCS is loaded on the new primary WCS.
Step 3 ![]() Install the correct version of WCS on the primary WCS.
Install the correct version of WCS on the primary WCS.
Step 4 ![]() Upgrade the primary WCS. The Health Monitor also starts.
Upgrade the primary WCS. The Health Monitor also starts.
Step 5 ![]() Follow the steps in the "Configuring High Availability" section.
Follow the steps in the "Configuring High Availability" section.
Step 6 ![]() After the primary WCS connects to the secondary, the Health Monitor on the primary connects to the secondary Health Monitor. They mutually acknowledge each other and start the monitoring.
After the primary WCS connects to the secondary, the Health Monitor on the primary connects to the secondary Health Monitor. They mutually acknowledge each other and start the monitoring.
High availability deployment is now complete.
Removing a Primary WCS
When a primary WCS instance is removed from a group, you must disable the peer database instance on the secondary WCS and remove the Health Monitor for that primary. (To remove the primary WCS from high availability, use the Remove button on the High Availability configuration page.) The secondary WCS disables the database instance and removes the uninstalled primary WCS from its Health Monitor.
Setting User Preferences
This page contains user-specific settings you may want to adjust.
Step 1 ![]() Choose Administration > User Preferences. The User Preferences Page appears (see Figure 18-39).
Choose Administration > User Preferences. The User Preferences Page appears (see Figure 18-39).
Figure 18-39 User Preferences Page

Step 2 ![]() Use the Items Per List Page drop-down list to configure the number of entries shown on a given list page (such as alarms, events, AP list, etc.).
Use the Items Per List Page drop-down list to configure the number of entries shown on a given list page (such as alarms, events, AP list, etc.).
Step 3 ![]() If you want the maps and alarms page to automatically refresh when a new alarm is raised by WCS, click the check box in the Alarms portion of the page.
If you want the maps and alarms page to automatically refresh when a new alarm is raised by WCS, click the check box in the Alarms portion of the page.
Step 4 ![]() Use the drop-down list to indicate how often you want the alarm count refreshed in the Alarm summary page on the left panel. If you instead want to specify how often to reset, use the drop-down list to choose a time interval.
Use the drop-down list to indicate how often you want the alarm count refreshed in the Alarm summary page on the left panel. If you instead want to specify how often to reset, use the drop-down list to choose a time interval.
Step 5 ![]() Use the Alarm Category to display in Alarm Summary drop-down list to decide which alarm categories to display in the Alarm Summary page.
Use the Alarm Category to display in Alarm Summary drop-down list to decide which alarm categories to display in the Alarm Summary page.
Step 6 ![]() If you do not want the alarm acknowledge warning message to appear, click the Disable Alarm Acknowledge Warning Message check box.
If you do not want the alarm acknowledge warning message to appear, click the Disable Alarm Acknowledge Warning Message check box.
Step 7 ![]() Specify how often you want the home page refreshed by clicking the Refresh home page check box and choosing a time interval from the Refresh home page every drop-down list.
Specify how often you want the home page refreshed by clicking the Refresh home page check box and choosing a time interval from the Refresh home page every drop-down list.
Step 8 ![]() Click Save.
Click Save.
Accessing the License Center
The License Center allows you to manage WCS, wireless LAN controllers, and MSE licenses. To view the License Center page, choose Administration > License Center (see Figure 18-40).

Note ![]() Although WCS and MSE licenses can be fully managed from the License Center, WLC licenses can only be viewed. You must use WLC or CLM to manage WLC licenses.
Although WCS and MSE licenses can be fully managed from the License Center, WLC licenses can only be viewed. You must use WLC or CLM to manage WLC licenses.
Figure 18-40 License Center

WCS License Information
The WCS Licenses portion of the License Center page displays the following:
•![]() Feature—The type of license, either Base or PLUS. A Base license supports standard WCS capabilities, which includes wireless client data access, rogue access point containment functions, Cisco WLAN Solution monitoring and control, and client and rogue access point location to the nearest access point. Cisco WCS PLUS license supports Cisco WCS Base license features and the following capabilities: mobility services enablement and high availability.
Feature—The type of license, either Base or PLUS. A Base license supports standard WCS capabilities, which includes wireless client data access, rogue access point containment functions, Cisco WLAN Solution monitoring and control, and client and rogue access point location to the nearest access point. Cisco WCS PLUS license supports Cisco WCS Base license features and the following capabilities: mobility services enablement and high availability.

Note ![]() To upgrade to a PLUS license, you must purchase upgrade licenses with the total count meeting or exceeding your Base license.
To upgrade to a PLUS license, you must purchase upgrade licenses with the total count meeting or exceeding your Base license.

Note ![]() An older Cisco WCS Location license is forward-compatible and is equivalent to a PLUS license. When upgrading to this release, older Location licenses appear as PLUS licenses. Older Enterprise SKUs which generated Location licenses are also forward-compatible and become PLUS licenses when loaded. The process to provision a Cisco WCS PLUS license is the same as provisioning a current Cisco WCS license.
An older Cisco WCS Location license is forward-compatible and is equivalent to a PLUS license. When upgrading to this release, older Location licenses appear as PLUS licenses. Older Enterprise SKUs which generated Location licenses are also forward-compatible and become PLUS licenses when loaded. The process to provision a Cisco WCS PLUS license is the same as provisioning a current Cisco WCS license.
•![]() Host—The WCS host name.
Host—The WCS host name.

Note ![]() The host name provides a link to the WCS License Files section.
The host name provides a link to the WCS License Files section.
•![]() AP Limit—The total number of licensed access points.
AP Limit—The total number of licensed access points.
•![]() AP Count—The current number of access points using licenses.
AP Count—The current number of access points using licenses.

Note ![]() AP count includes both associated and unassociated access points. When you are near the AP limit, you can delete any unassociated access points to increase available license capacity. For a demo license, you can click the "If you do not have a Product Authorization Key (PAK), please click here for available licenses" link and choose Wireless Control System Trial License.
AP count includes both associated and unassociated access points. When you are near the AP limit, you can delete any unassociated access points to increase available license capacity. For a demo license, you can click the "If you do not have a Product Authorization Key (PAK), please click here for available licenses" link and choose Wireless Control System Trial License.
•![]() % Used—The percentage of access points licensed across WCS. If the percentage drops to 75%, the value appears in red. At this level, a message also appears indicating that both associated and unassociated access points are part of the AP count.
% Used—The percentage of access points licensed across WCS. If the percentage drops to 75%, the value appears in red. At this level, a message also appears indicating that both associated and unassociated access points are part of the AP count.
•![]() Type—Permanent if all licenses are permanent. If any licenses are evaluations (or demos), it shows the number of days remaining on the license that has the fewest number of days until expiration.
Type—Permanent if all licenses are permanent. If any licenses are evaluations (or demos), it shows the number of days remaining on the license that has the fewest number of days until expiration.

Note ![]() To add a new license for WCS, go to the Product License Registration link
To add a new license for WCS, go to the Product License Registration link
(https://tools.cisco.com/SWIFT/Licensing/PrivateRegistrationServlet)
and provide your Product Authorization Key (PAK) and host name.
See the Cisco Wireless Control System Licensing and Ordering Guide at this location:
http://www.cisco.com/en/US/prod/collateral/wireless/ps5755/ps6301/ps6305/product_data_sheet0900aecd804b4646.html#wp9000156.
It covers selecting the correct SKU, ordering the SKU, installing the software, registering the PAK certificate, and installing the license file on the server.
See the "WCS Licenses" section for more information on licensing enforcement, PAK certificates, license types, and installing and managing WCS licenses.
Controller License Information
The Controller Licensing portion of the License Center page provides the following information for both WPLUS and Base licenses:
•![]() Controller Count—The current number of licensed controllers.
Controller Count—The current number of licensed controllers.

Note ![]() Only 5500 series controllers are included in the count.
Only 5500 series controllers are included in the count.

Note ![]() Clicking the number in this column is the same as choosing Summary > Controller from the left sidebar menu, except that it is sorted by the feature you click. This page provides a summary of active controllers.
Clicking the number in this column is the same as choosing Summary > Controller from the left sidebar menu, except that it is sorted by the feature you click. This page provides a summary of active controllers.
•![]() AP Limit—The total number of licensed access points.
AP Limit—The total number of licensed access points.
•![]() Type—The four different types of licenses are as follows:
Type—The four different types of licenses are as follows:

Note ![]() For any controllers with a type other than Permanent, the least number of days left to expiration is shown.
For any controllers with a type other than Permanent, the least number of days left to expiration is shown.
–![]() Permanent—Licenses are node-locked and have no usage period associated with them. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Upon installation of these licenses, you have the necessary permissions across different versions.
Permanent—Licenses are node-locked and have no usage period associated with them. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Upon installation of these licenses, you have the necessary permissions across different versions.
–![]() Evaluation—Licenses are non-node-locked and are valid only for a limited period. They are used only when no permanent, extension, or grace period licenses exist. Before using an evaluation license, you must accept an End User License Agreement (EULA). Even though they are non-node-locked, their usage is recorded on the device. The number of days remaining on the evaluation license that has the fewest number of days until expiration is shown.
Evaluation—Licenses are non-node-locked and are valid only for a limited period. They are used only when no permanent, extension, or grace period licenses exist. Before using an evaluation license, you must accept an End User License Agreement (EULA). Even though they are non-node-locked, their usage is recorded on the device. The number of days remaining on the evaluation license that has the fewest number of days until expiration is shown.
–![]() Extension—Licenses are node-locked and metered. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Before using an extension license, you must accept a EULA during installation.
Extension—Licenses are node-locked and metered. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Before using an extension license, you must accept a EULA during installation.
–![]() Grace Period—Licenses are node-locked and metered. These licenses are issued by Cisco's licensing portal as part of the permission ticket to rehost a license. They are installed on the device as part of the rehost operation, and you must accept a EULA as part of the rehost operation.
Grace Period—Licenses are node-locked and metered. These licenses are issued by Cisco's licensing portal as part of the permission ticket to rehost a license. They are installed on the device as part of the rehost operation, and you must accept a EULA as part of the rehost operation.
If you need to revoke a license from one controller and install it on another, it is called rehosting. You might want to rehost a license in order to change the purpose of a controller. See Performing System Tasks of the Cisco Wireless LAN Controller Configuration Guide for information on rehosting a license.

Note ![]() The licensing status is updated periodically. To initiate an immediate update, go to Administration > Background Tasks and run the Controller License Status task.
The licensing status is updated periodically. To initiate an immediate update, go to Administration > Background Tasks and run the Controller License Status task.
If your network contains various Cisco licensed devices, you might want to consider using the Cisco License Manager (CLM) to manage all of the licenses using a single application. CLM is a secure client/server application that manages Cisco software licenses network wide. You can download the CLM software and access user documentation at this URL: http://www.cisco.com/go/clm. You can either register a PAK certificate with CLM or with the licensing portal found at https://tools.cisco.com/SWIFT/Licensing/PrivateRegistrationServlet.
MSE License Information
The MSE Licenses portion of the License Center page provides the following information:
•![]() Type—The four different types of licenses are as follows:
Type—The four different types of licenses are as follows:
–![]() Permanent—Licenses are node-locked and have no usage period associated with them. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Upon installation of these licenses, you have the necessary permissions across different versions.
Permanent—Licenses are node-locked and have no usage period associated with them. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Upon installation of these licenses, you have the necessary permissions across different versions.
–![]() Evaluation—Licenses are non-node-locked and are valid only for a limited time period. They are used only when no permanent, extension, or grace period licenses exist. Before using an evaluation license, you must accept an End User License Agreement (EULA). Even though they are non-node-locked, their usage is recorded on the device. The number of days remaining on the evaluation license which has the fewest number of days until expiration is shown.
Evaluation—Licenses are non-node-locked and are valid only for a limited time period. They are used only when no permanent, extension, or grace period licenses exist. Before using an evaluation license, you must accept an End User License Agreement (EULA). Even though they are non-node-locked, their usage is recorded on the device. The number of days remaining on the evaluation license which has the fewest number of days until expiration is shown.
–![]() Extension—Licenses are node-locked and metered. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Before using an extension license, you must accept a EULA during installation.
Extension—Licenses are node-locked and metered. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Before using an extension license, you must accept a EULA during installation.
•![]() Tag Elements
Tag Elements

Note ![]() In some cases, you may need to delete a license manually from an MSE before you can apply a tag license from the system manager. To get rid of a tag license, you must uninstall and reinstall MSE.
In some cases, you may need to delete a license manually from an MSE before you can apply a tag license from the system manager. To get rid of a tag license, you must uninstall and reinstall MSE.
–![]() Limit—The total number of tag elements with licenses.
Limit—The total number of tag elements with licenses.
–![]() Count—The number of tag elements currently licensed across MSEs.
Count—The number of tag elements currently licensed across MSEs.
–![]() % Used—The percentage of tag elements licensed across MSEs.
% Used—The percentage of tag elements licensed across MSEs.
•![]() Client Elements
Client Elements
–![]() Limit—The total number of client elements with licenses.
Limit—The total number of client elements with licenses.
–![]() Count—The number of client elements currently licensed across MSEs.
Count—The number of client elements currently licensed across MSEs.
–![]() % Used—The percentage of client elements licensed across MSEs.
% Used—The percentage of client elements licensed across MSEs.
•![]() Monitor Mode APs
Monitor Mode APs
–![]() Limit—The total number of CAM access points licensed across MSEs.
Limit—The total number of CAM access points licensed across MSEs.
–![]() Count—The number of CAM access points currently licensed across MSEs.
Count—The number of CAM access points currently licensed across MSEs.
–![]() % Used—The percentage of CAM access points licensed across MSEs.
% Used—The percentage of CAM access points licensed across MSEs.
Controller
If you want to see more details about controller licensing, choose the Summary > Controller option from the left sidebar menu. The License Center page appears (see Figure 18-41). All currently active licenses on the controller are summarized.
Figure 18-41 License Center (Edit View) Page

All licensed controllers and their information in the bulleted list below are displayed. If you want to change how the controller results are displayed, click Edit View. In the Edit View page, highlight License Status, and click Hide to remove the column from the display.
Above the Controller Summary list is a series of filters that allow you to filter the list by Controller Name, Feature, Type, or Greater Than Percent Used. For example, if you enter 50, the list shows any WLCs that have more than 50% of its licenses used.

Note ![]() You can also use the Advanced Search link to sort the list of controllers.
You can also use the Advanced Search link to sort the list of controllers.
•![]() Controller Name—Provides a link to the Files > Controller Files page.
Controller Name—Provides a link to the Files > Controller Files page.
•![]() Controller IP—The IP address of the controller.
Controller IP—The IP address of the controller.
•![]() Model—The controller model type.
Model—The controller model type.
•![]() Feature—The type of license, either Base or WPLUS. The Base license supports the standard software set, and the WPLUS license supports the premium Wireless Plus (WPLUS) software set. The WPLUS software set provides the standard feature set as well as added functionality for OfficeExtend access points, CAPWAP data encryptions, and enterprise wireless mesh.
Feature—The type of license, either Base or WPLUS. The Base license supports the standard software set, and the WPLUS license supports the premium Wireless Plus (WPLUS) software set. The WPLUS software set provides the standard feature set as well as added functionality for OfficeExtend access points, CAPWAP data encryptions, and enterprise wireless mesh.
•![]() AP Limit—The maximum capacity of access points allowed to join this controller.
AP Limit—The maximum capacity of access points allowed to join this controller.
•![]() AP Count—The current number of access points using licenses.
AP Count—The current number of access points using licenses.
•![]() % Used—The percentage of licensed access points that are being used. If the percentage is greater than 75%, the bar appears red to indicate that the limit is being approached.
% Used—The percentage of licensed access points that are being used. If the percentage is greater than 75%, the bar appears red to indicate that the limit is being approached.
•![]() Type—The four different types of licenses are as follows:
Type—The four different types of licenses are as follows:

Note ![]() For any controllers with a type other than Permanent, the least number of days left to expiration is shown.
For any controllers with a type other than Permanent, the least number of days left to expiration is shown.
–![]() Permanent—Licenses are node-locked and have no usage period associated with them. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Upon installation of these licenses, you have the necessary permissions across different versions.
Permanent—Licenses are node-locked and have no usage period associated with them. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Upon installation of these licenses, you have the necessary permissions across different versions.
–![]() Evaluation—Licenses are non-node-locked and are valid only for a limited time period. They are used only when no permanent, extension, or grace period licenses exist. Before using an evaluation license, you must accept an End User License Agreement (EULA). Even though they are non-node-locked, their usage is recorded on the device. The number of days remaining on the evaluation license which has the fewest number of days until expiration is shown.
Evaluation—Licenses are non-node-locked and are valid only for a limited time period. They are used only when no permanent, extension, or grace period licenses exist. Before using an evaluation license, you must accept an End User License Agreement (EULA). Even though they are non-node-locked, their usage is recorded on the device. The number of days remaining on the evaluation license which has the fewest number of days until expiration is shown.
–![]() Extension—Licenses are node-locked and metered. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Before using an extension license, you must accept a EULA during installation.
Extension—Licenses are node-locked and metered. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Before using an extension license, you must accept a EULA during installation.

Note ![]() If a license shows as expired, the controller does not stop functioning. Only upon a reboot will the controller with the expired license become inactive.
If a license shows as expired, the controller does not stop functioning. Only upon a reboot will the controller with the expired license become inactive.
•![]() Status—In Use, Not in Use, Inactive, or EULA Not Accepted.
Status—In Use, Not in Use, Inactive, or EULA Not Accepted.
MSE
If you want to see more details about MSE licensing, choose Summary > MSE from the left sidebar menu. The License Center page appears (see Figure 18-42).
Figure 18-42 License Center Page

All licensed MSEs are listed in the following columns.
•![]() MSE Name—Provides a link to the MSE license file list page.
MSE Name—Provides a link to the MSE license file list page.
•![]() Type—Specifies the type of MSE.
Type—Specifies the type of MSE.

Note ![]() Under wIPS Monitor Mode APs, an active link takes you to a list of licensed access points. You cannot access a list of licensed clients or tags.
Under wIPS Monitor Mode APs, an active link takes you to a list of licensed access points. You cannot access a list of licensed clients or tags.
•![]() Limit—Displays the total number of client elements licensed across MSEs.
Limit—Displays the total number of client elements licensed across MSEs.
•![]() Count—Displays the number of client elements that are currently licensed across MSEs.
Count—Displays the number of client elements that are currently licensed across MSEs.
•![]() Unlicensed Count—Displays the number of client elements that are not licensed.
Unlicensed Count—Displays the number of client elements that are not licensed.
•![]() % Used—Displays the percentage of clients used across all MSEs.
% Used—Displays the percentage of clients used across all MSEs.
•![]() License Type—The four different types of licenses are as follows:
License Type—The four different types of licenses are as follows:
–![]() Permanent—Licenses are node-locked and have no usage period associated with them. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Upon installation of these licenses, you have the necessary permissions across different versions.
Permanent—Licenses are node-locked and have no usage period associated with them. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Upon installation of these licenses, you have the necessary permissions across different versions.
–![]() Evaluation—Licenses are non-node-locked and are valid only for a limited time period. They are used only when no permanent, extension, or grace period licenses exist. Before using an evaluation license, you must accept an End User License Agreement (EULA). Even though they are non-node-locked, their usage is recorded on the device. The number of days remaining on the evaluation license which has the fewest number of days until expiration is shown.
Evaluation—Licenses are non-node-locked and are valid only for a limited time period. They are used only when no permanent, extension, or grace period licenses exist. Before using an evaluation license, you must accept an End User License Agreement (EULA). Even though they are non-node-locked, their usage is recorded on the device. The number of days remaining on the evaluation license which has the fewest number of days until expiration is shown.
–![]() Extension—Licenses are node-locked and metered. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Before using an extension license, you must accept a EULA during installation.
Extension—Licenses are node-locked and metered. They are issued by Cisco's licensing portal and must be installed using management interfaces on the device. Before using an extension license, you must accept a EULA during installation.
•![]() Status
Status
–![]() Active—License is installed and being used by a feature.
Active—License is installed and being used by a feature.
–![]() Inactive—License is installed but not being used by a feature.
Inactive—License is installed but not being used by a feature.
–![]() Expired—License has expired.
Expired—License has expired.
–![]() Corrupted—License is corrupted.
Corrupted—License is corrupted.
Managing Individual Licenses
Managing Controller Licenses
Choose Files > Controller Files from the left sidebar menu to monitor the controller licenses.

Note ![]() WCS does not directly manage controller licenses. It simply monitors the licenses. You can manage the licenses using CLI, WebUI, or Cisco License Manager (CM) at:
WCS does not directly manage controller licenses. It simply monitors the licenses. You can manage the licenses using CLI, WebUI, or Cisco License Manager (CM) at:
https://tools.cisco.com/SWIFT/Licensing/PrivateRegistrationServlet.
The page displays the following information:
•![]() Controller Name
Controller Name
•![]() Controller IP
Controller IP
•![]() Feature—The feature options are wplus-ap-count, wplus, base-ap-count, and base. Two are active at any one time for an enable feature level of WPLUS or Base and the AP count (base-ap-count or wplus-ap-count), which determines the number of access points that the controller supports (12, 25, 50, 100, or 250). For every physical license installed, two license files show up in the controller as a feature level license and an ap-count license. For example, if you install a WPlus 500 license on the controller, you see a wplus or wplus-ap-count feature.
Feature—The feature options are wplus-ap-count, wplus, base-ap-count, and base. Two are active at any one time for an enable feature level of WPLUS or Base and the AP count (base-ap-count or wplus-ap-count), which determines the number of access points that the controller supports (12, 25, 50, 100, or 250). For every physical license installed, two license files show up in the controller as a feature level license and an ap-count license. For example, if you install a WPlus 500 license on the controller, you see a wplus or wplus-ap-count feature.

Note ![]() You can have both a WPLUS and Base license, but only one can be active at a time.
You can have both a WPLUS and Base license, but only one can be active at a time.
•![]() AP Limit—The number of access points that the controller supports.
AP Limit—The number of access points that the controller supports.
•![]() EULA Status—Whether the End User License Agreement has been accepted or not.
EULA Status—Whether the End User License Agreement has been accepted or not.
•![]() Comments—Any user-entered comments about the license when it is installed.
Comments—Any user-entered comments about the license when it is installed.
•![]() Type—Permanent, evaluation, or extension.
Type—Permanent, evaluation, or extension.

Note ![]() For any controllers with a type other than Permanent, the number of days left to expiration is shown. A license is not in use does not incur the reduction in count until it is in use.
For any controllers with a type other than Permanent, the number of days left to expiration is shown. A license is not in use does not incur the reduction in count until it is in use.
•![]() Status —The status can be described as follows:
Status —The status can be described as follows:
–![]() Inactive—The license level is being used, but this license is not in use.
Inactive—The license level is being used, but this license is not in use.
–![]() Not In Use—The license level is not being used, and this license is currently unrecognized.
Not In Use—The license level is not being used, and this license is currently unrecognized.
–![]() Expired in Use—The license is being used, but it is expired and will not be used upon next reboot.
Expired in Use—The license is being used, but it is expired and will not be used upon next reboot.
–![]() Expired Not in Use—The license has expired and can no longer be used.
Expired Not in Use—The license has expired and can no longer be used.
–![]() Count Consumed—The ap-count license is In Use.
Count Consumed—The ap-count license is In Use.
All licensed controllers and their information are displayed. If you want to change how the controller results are displayed, click Edit View. In the Edit View page, use the Show and Hide buttons to determine how the columns appear.
Above the Controller Summary list is a series of filters that allow you to sort the list by Controller Name, Feature, or Type.
Managing WCS Licenses
Follow these steps to manage WCS licenses. For information on deciding on a license, types of licenses, installing a license, and backing up and restoring WCS licenses, refer to the "WCS Licenses" section.
Step 1 ![]() Choose Administration > License Center to access the License Center page. It provides information about the WCS licenses, the controller license, and elements of MSE licenses.
Choose Administration > License Center to access the License Center page. It provides information about the WCS licenses, the controller license, and elements of MSE licenses.
For WCS licenses, the following is displayed:
•![]() Feature
Feature
•![]() Host name
Host name
•![]() AP Limit
AP Limit
•![]() AP Count (for specified number of access points)
AP Count (for specified number of access points)
•![]() Capacity of licenses currently used
Capacity of licenses currently used
•![]() Type
Type
For controller licensing, the following is displayed:
•![]() Feature
Feature
•![]() Controller Count
Controller Count
•![]() AP Limit
AP Limit
•![]() Type
Type
For tag elements, client elements, and wIPS Monitor Mode APs within MSE, the following is displayed:
•![]() Limit
Limit
•![]() Count
Count
•![]() % Used
% Used
Step 2 ![]() Choose Files > WCS Files from the left sidebar menu to see the following:
Choose Files > WCS Files from the left sidebar menu to see the following:
•![]() Product Activation Key (PAK)
Product Activation Key (PAK)
•![]() the feature
the feature
•![]() the access point limit
the access point limit
•![]() type
type
You can click the check box of the desired license and either add or delete it.
Managing MSE Licenses
To manage MSE license, choose Files > MSE Files from the left sidebar menu. The page displays the MSE licenses found and includes the following information:
•![]() MSE License File
MSE License File
•![]() MSE Name
MSE Name
•![]() Element Type
Element Type
•![]() Limit
Limit
•![]() License Type
License Type

Note ![]() Evaluation extension and tag licenses are not displayed on this page.
Evaluation extension and tag licenses are not displayed on this page.
With full WCS support, the complete functionality of CLM is embedded within WCS. You therefore have a single point of management for devices and their licenses.
If you need to search for a particular license file, you can choose an element type from the drop-down box, and click Go. For example, if you choose Client, and click Go, all license files with client licenses are returned.
Configuring ACS 5.x
This section provides instructions for configuring ACS 5.x to work with WCS.
Creating Network Devices and AAA Clients
To create Network Devices and AAA Clients, perform the following steps:
Step 1 ![]() Choose Network Resources > Network Devices and AAA Clients.
Choose Network Resources > Network Devices and AAA Clients.
Figure 18-43 Network Devices Page

Step 2 ![]() Enter IP Address.
Enter IP Address.
Adding Groups
To add groups, perform the following steps:
Step 1 ![]() Choose Users and Identity Stores > Identity Groups.
Choose Users and Identity Stores > Identity Groups.
Figure 18-44 Identify Groups Page

Step 2 ![]() Create a Group
Create a Group
Adding Users
To add users, perform the following steps:
Step 1 ![]() Choose Users and Identity Stores > Internal Identity Stores > Users.
Choose Users and Identity Stores > Internal Identity Stores > Users.
Figure 18-45 Internal Users Page

Step 2 ![]() Add a user, and then map to group to that user.
Add a user, and then map to group to that user.
Creating Policy Elements or Authorization Profiles
Creating Policy Elements or Authorization Profiles for RADIUS
To create policy elements or authorization profiles for RADIUS, perform the following steps:
Step 1 ![]() Choose Policy Elements > Authorization and Permissions > Network Access > Authorization Profiles.
Choose Policy Elements > Authorization and Permissions > Network Access > Authorization Profiles.
Step 2 ![]() Click Create.
Click Create.
Step 3 ![]() Enter Name and Description.
Enter Name and Description.
Step 4 ![]() Click the RADIUS Attributes tab.
Click the RADIUS Attributes tab.
Step 5 ![]() Add RADIUS Attributes one by one (see Figure 18-46).
Add RADIUS Attributes one by one (see Figure 18-46).
Figure 18-46 Authorization Profiles Page

Step 6 ![]() Click Submit.
Click Submit.
Creating Policy Elements or Authorization Profiles For TACACS
To create policy elements or authorization profiles for RADIUS, perform the following steps:
Step 1 ![]() Choose Policy Elements > Authorization and Permissions > Device Administration > Shell Profiles.
Choose Policy Elements > Authorization and Permissions > Device Administration > Shell Profiles.
Step 2 ![]() Click Create.
Click Create.
Step 3 ![]() Enter Name and Description.
Enter Name and Description.
Step 4 ![]() Click the Custom Attributes tab.
Click the Custom Attributes tab.
Step 5 ![]() Add the TACACS Attributes one by one (see Figure 18-47).
Add the TACACS Attributes one by one (see Figure 18-47).
Figure 18-47 Shell Profiles Page

Step 6 ![]() Click Submit.
Click Submit.
Creating Authorization Rules
This section provides instructions for configuring authorization for RADIUS and TACACS.
Creating Service Selection Rules for RADIUS
To create service selection rules for RADIUS, perform the following steps:
Step 1 ![]() Choose Access Policies > Access Services > Service Selection Rules.
Choose Access Policies > Access Services > Service Selection Rules.
Step 2 ![]() Click Create.
Click Create.
Step 3 ![]() Select the protocol as Radius and service as Default Network Access (see Figure 18-48).
Select the protocol as Radius and service as Default Network Access (see Figure 18-48).
Figure 18-48 Service Selection Page

Step 4 ![]() Click OK.
Click OK.
Creating Service Selection Rules for TACACS
To create service selection rules for TACACS, perform the following steps:
Step 1 ![]() Choose Access Policies > Access Services > Service Selection Rules.
Choose Access Policies > Access Services > Service Selection Rules.
Step 2 ![]() Click Create.
Click Create.
Step 3 ![]() Select the protocol as TACACS and Service as Default Device Admin (see Figure 18-49).
Select the protocol as TACACS and Service as Default Device Admin (see Figure 18-49).
Figure 18-49 Service Selection Page

Step 4 ![]() Click OK.
Click OK.
Configuring Access Services
This section provides instructions for configuring access services for RADIUS and TACACS.
Configuring Access Services for RADIUS
To configure access services for RADIUS, perform the following steps:
Step 1 ![]() Choose Access Policies > Access Services > Default Network Access.
Choose Access Policies > Access Services > Default Network Access.
Step 2 ![]() In the General tab, select the Policy Structure you want to use. By default all the three will be selected. Similarly, in Allowed Protocols, select the protocols you want to use.
In the General tab, select the Policy Structure you want to use. By default all the three will be selected. Similarly, in Allowed Protocols, select the protocols you want to use.

Note ![]() You can retain the defaults for identity and group mapping.
You can retain the defaults for identity and group mapping.
Step 3 ![]() To create an authorization rule for RADIUS, choose Access Policies > Access Services > Default Network Access > Authorization.
To create an authorization rule for RADIUS, choose Access Policies > Access Services > Default Network Access > Authorization.
Step 4 ![]() Click Create.
Click Create.
Step 5 ![]() In Location, select All Locations or you can create a rule based on the location.
In Location, select All Locations or you can create a rule based on the location.
Step 6 ![]() In Group, select the group that you created earlier.
In Group, select the group that you created earlier.
Step 7 ![]() In Device Type, select All Device Types or you can create a rule based on the Device Type.
In Device Type, select All Device Types or you can create a rule based on the Device Type.
Step 8 ![]() In Authorization Profile, select the authorization profile created for RADIUS.
In Authorization Profile, select the authorization profile created for RADIUS.
Figure 18-50 Authorization Page

Step 9 ![]() Click OK.
Click OK.
Step 10 ![]() Click Save.
Click Save.
Configuring Access Services for TACACS
To configure access services for TACACS, perform the following steps:
Step 1 ![]() Choose Access Policies > Access Services > Default Device Admin.
Choose Access Policies > Access Services > Default Device Admin.
Step 2 ![]() In the General tab, select the Policy Structure you want to use. By default all the three will be selected. Similarly, in Allowed Protocols, select the protocols you want to use.
In the General tab, select the Policy Structure you want to use. By default all the three will be selected. Similarly, in Allowed Protocols, select the protocols you want to use.

Note ![]() You can retain the defaults for identity and group mapping.
You can retain the defaults for identity and group mapping.
Step 3 ![]() To create an authorization rule for TACACS, choose Access Policies > Access Services > Default Device Admin > Authorization.
To create an authorization rule for TACACS, choose Access Policies > Access Services > Default Device Admin > Authorization.
Step 4 ![]() Click Create.
Click Create.
Step 5 ![]() In Location, select All Locations or you can create a rule based on the location.
In Location, select All Locations or you can create a rule based on the location.
Step 6 ![]() In Group, select the group that you created earlier.
In Group, select the group that you created earlier.
Step 7 ![]() In Device Type, select All Device Types or you can create a rule based on the Device Type.
In Device Type, select All Device Types or you can create a rule based on the Device Type.
Step 8 ![]() In Shell Profile, select the shell profile created for TACACS.
In Shell Profile, select the shell profile created for TACACS.
Figure 18-51 Authorization Page

Step 9 ![]() Click OK.
Click OK.
Step 10 ![]() Click Save.
Click Save.
 Feedback
Feedback