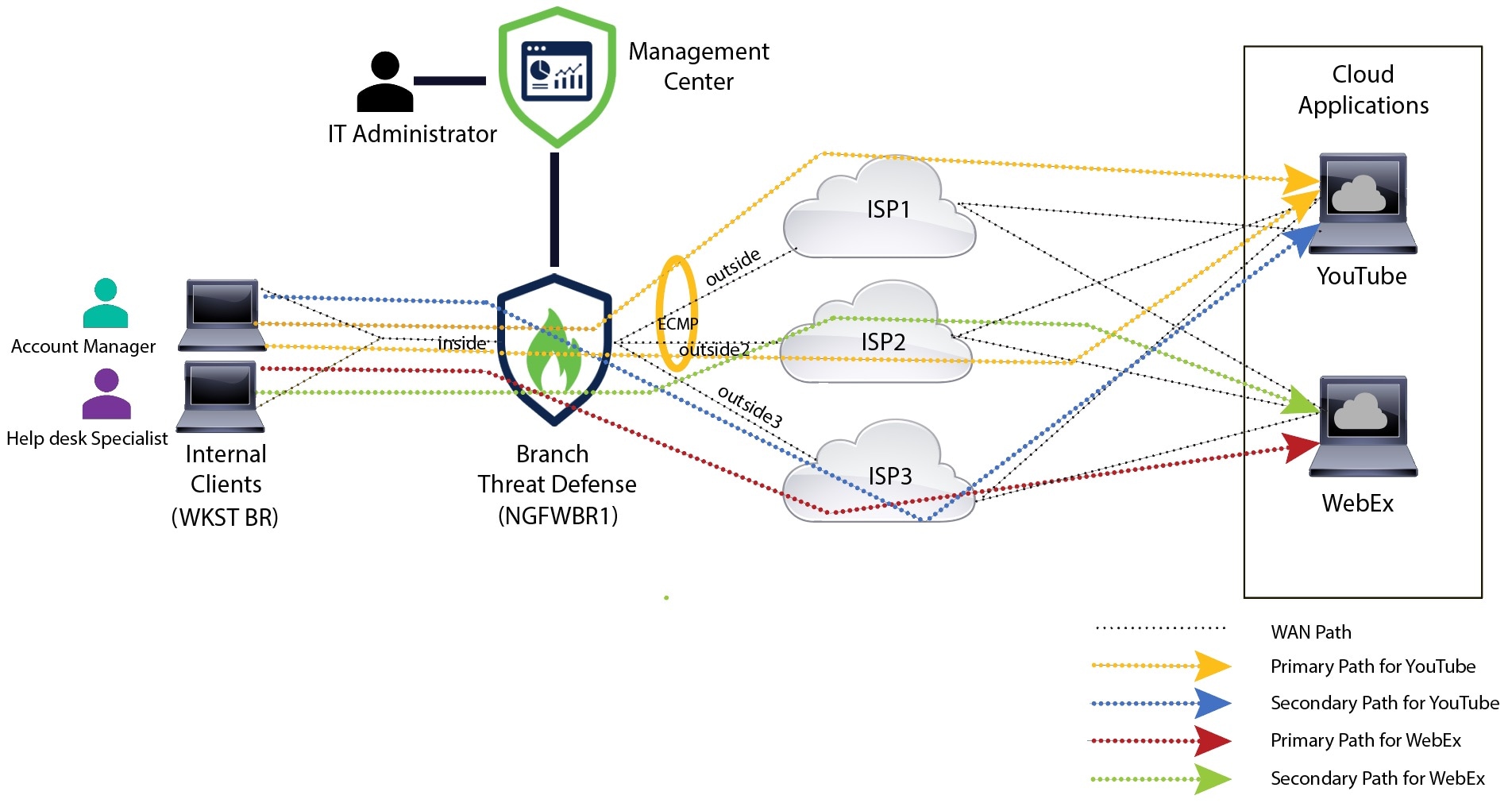
部署后,使用以下 CLI 监控和排除与 Cisco Secure Firewall Threat Defense 上策略型路由相关的问题。
|
如何...
|
CLI 命令
|
|
登录 Cisco Secure Firewall Threat Defense Lina CLI
|
system support diagnostic-cli
|
| 查看在部署期间从管理中心推送到威胁防御的预定义网络服务对象 |
|
|
查看与配置的应用相关的特定网络服务对象 (NSG)
|
-
show object id YouTube
-
show object id WebEx
|
|
验证推送到 Cisco Secure Firewall 的网络服务组 (NSG)
|
show run object-group network-service
|
|
查看与策略型路由关联的路由映射
|
show run route-map
|
|
验证接口配置详细信息,例如接口名称和接口优先级
|
show run interface
|
| 验证受信任的 DNS 服务器配置 |
show dns
|
| 确定流量所采用的路径 |
debug policy-route
|
重要
|
运行调试命令时要谨慎,尤其是在生产环境中,因为它可能会根据流量产生冗长的输出。
|
|
|
停止调试路由
|
undebug all
|
要查看预定义的网络服务对象,请使用以下命令:
ngfwbr1# show object network-service
object network-service "ADrive" dynamic
description Online file storage and backup.
app-id 17
domain adrive.com (bid=0) ip (hitcnt=0)
object network-service "Amazon" dynamic
description Online retailer of books and most other goods.
app-id 24
domain amazon.com (bid=0) ip (hitcnt=0)
domain amazon.jobs (bid=0) ip (hitcnt=0)
domain amazon.in (bid=0) ip (hitcnt=0)
.
.
.
output snipped
.
.
.
object network-service "Logitech" dynamic
description Company develops Computer peripherals and accessories.
app-id 4671
domain logitech.com (bid=0) ip (hitcnt=0)
object network-service "Lenovo" dynamic
description Company manufactures/markets computers, software and related services.
app-id 4672
domain lenovo.com (bid=0) ip (hitcnt=0)
domain lenovo.com.cn (bid=0) ip (hitcnt=0)
domain lenovomm.com (bid=0) ip (hitcnt=0)
ngfwbr1#
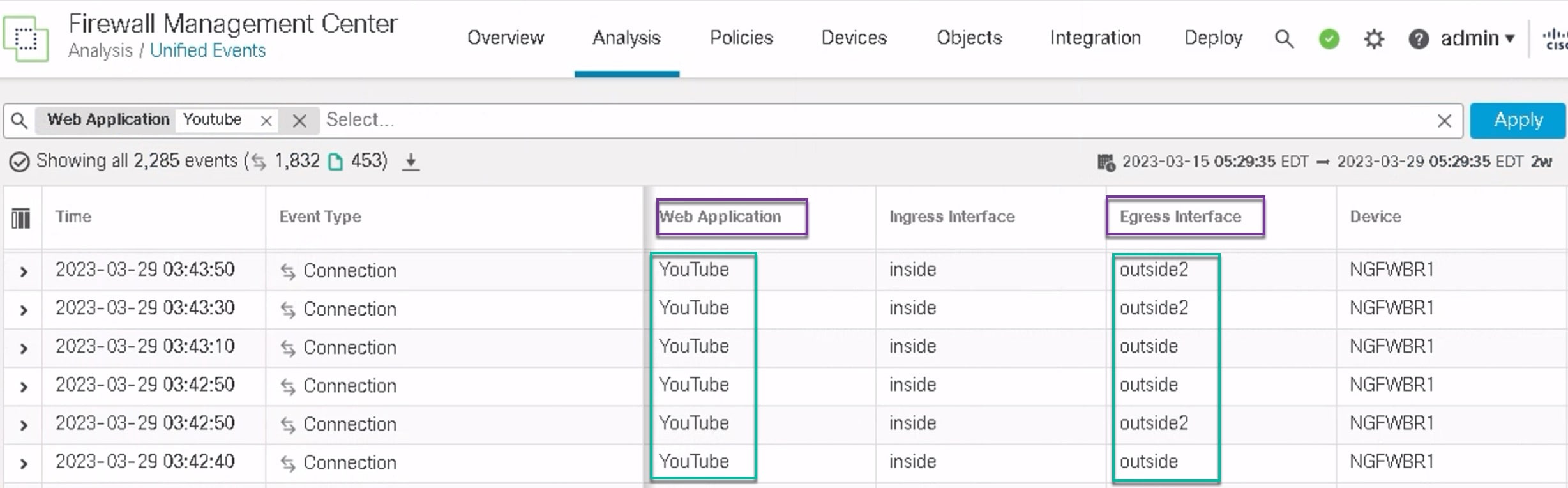
要查看特定网络服务对象(例如 YouTube 和 WebEx),请使用以下命令:
ngfwbr1# show object id YouTube
object network-service "YouTube" dynamic
description A video-sharing website on which users can upload, share, and view videos.
app-id 929
domain youtubei.googleapis.com (bid=592729) ip (hitcnt=0)
domain yt3.ggpht.com (bid=709809) ip (hitcnt=102)
domain youtube.com (bid=830871) ip (hitcnt=101)
domain ytimg.com (bid=1035543) ip (hitcnt=93)
domain googlevideo.com (bid=1148165) ip (hitcnt=466)
domain youtu.be (bid=1247981) ip (hitcnt=0)
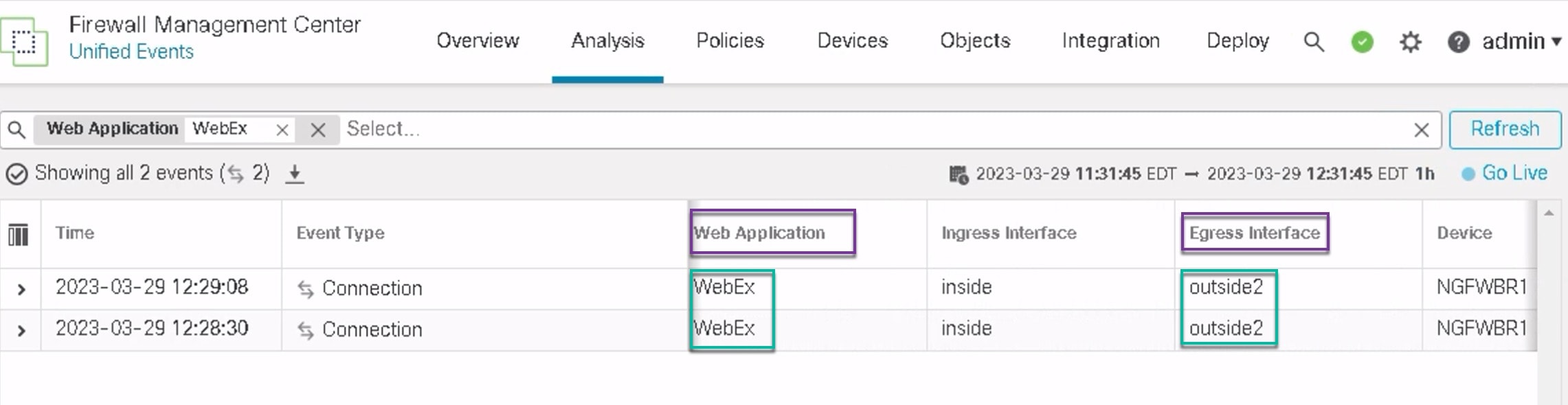
ngfwbr1# show object id WebEx
object network-service "WebEx" dynamic
description Cisco's online meeting and web conferencing application.
app-id 905
domain files-prod-us-east-2.webexcontent.com (bid=182837) ip (hitcnt=0)
domain webex.com (bid=290507) ip (hitcnt=30)
domain avatar-prod-us-east-2.webexcontent.com (bid=452667) ip (hitcnt=0)
ngfwbr1#
要验证 NSG 是否已推送到威胁防御,请使用以下命令:
ngfwbr1# show run object-group network-service
object-group network-service FMC_NSG_292057776181
network-service-member "WebEx"
object-group network-service FMC_NSG_292057776200
network-service-member "YouTube"
ngfwbr1#
要验证与 PBR 关联的路由映射,请使用以下命令:
ngfwbr1# show run route-map
!
route-map FMC_GENERATED_PBR_1678091359817 permit 5
match ip address DIA_Collaboration
set interface outside3 outside2
!
route-map FMC_GENERATED_PBR_1678091359817 permit 10
match ip address DIA_SocialMedia
set adaptive-interface cost outside outside2 outside3
!
ngfwbr1#
要验证接口配置和接口优先级详细信息,请使用以下命令:
ngfwbr1# show run interface
!
interface GigabitEthernet0/0
nameif outside
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
zone-member ECMP-WAN
ip address 198.18.128.81 255.255.192.0
policy-route cost 10
!
interface GigabitEthernet0/1
nameif inside
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 198.19.11.4 255.255.255.0
policy-route route-map FMC_GENERATED_PBR_1678091359817
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
nameif outside2
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
zone-member ECMP-WAN
ip address 198.19.40.4 255.255.255.0
policy-route cost 10
!
interface GigabitEthernet0/4
nameif outside3
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 198.19.30.4 255.255.255.0
policy-route cost 20
!
interface Management0/0
management-only
nameif diagnostic
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
no ip address
ngfwbr1#
要验证受信任的 DNS 配置,请使用以下命令:
ngfwbr1# show dns
DNS Trusted Source enabled for DHCP Server Configured
DNS Trusted Source enabled for DHCP Client Learned
DNS Trusted Source enabled for DHCP Relay Learned
DNS Trusted Source enabled for DNS Server Configured
DNS Trusted Source not enabled for Trust-any
DNS Trusted Source: Type: IPs : Interface : Idle/Timeout (sec)
DNS Server Configured: 198.19.10.100: <ifc-not-specified> : N/A
Trusted Source Configured: 198.19.10.100: <ifc-not-specified> : N/A
DNS snooping IP cache: 0 in use, 37 most used
Address Idle(sec) Timeout(sec) Hit-count Branch(es)
ngfwbr1#
要调试策略路由,请使用以下命令:
ngfwbr1# debug policy-route
debug policy-route enabled at level 1
ngfwbr1# pbr: policy based route lookup called for 198.19.11.225/58119 to 198.19.10.100/53 proto 17 sub_proto 0 received on interface inside, NSGs, nsg_id=none
pbr: no route policy found; skip to normal route lookup
.
output-snipped
.
pbr: policy based route lookup called for 198.19.11.225/61482 to 63.140.48.151/443 proto 6 sub_proto 0 received on interface inside , NSGs, nsg_id=1
pbr: First matching rule from ACL(2)
pbr: route map FMC_GENERATED_PBR_1678091359817, sequence 5, permit; proceed with policy routing
pbr: evaluating interface outside3
pbr: policy based routing applied; egress_ifc = outside3 : next_hop = 198.19.30.63
ngfwbr1#
上面的调试示例适用于 WebEx 流量。请注意,在 PBR 将路由路径更改为 outside2 接口之前,流量将通过 outside3 接口进行路由。
要停止调试过程,请使用以下命令:
ngfwbr1# undebug all



 )
) )
)
 反馈
反馈