About the ASA
The ASA provides advanced stateful firewall and VPN concentrator functionality in one device, and with the included ASA FirePOWER module, next-generation firewall services including Next-Generation Intrusion Prevention System (NGIPS), Application Visibility and Control (AVC), URL filtering, and Advanced Malware Protection (AMP).
You can manage the ASA using one of the following managers:
-
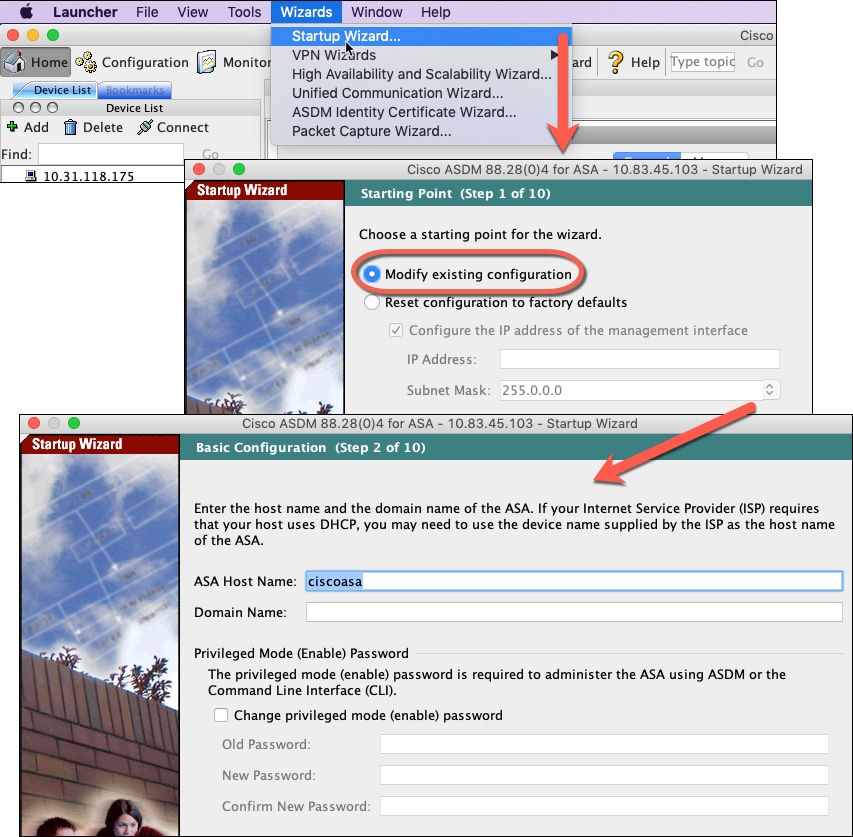
ASDM (covered in this guide)—A single device manager included on the device.
-
CLI
-
Cisco Defense Orchestrator—A simplified, cloud-based multi-device manager
-
Cisco Security Manager—A multi-device manager on a separate server.
You can manage the ASA FirePOWER module using one of the following managers:
-
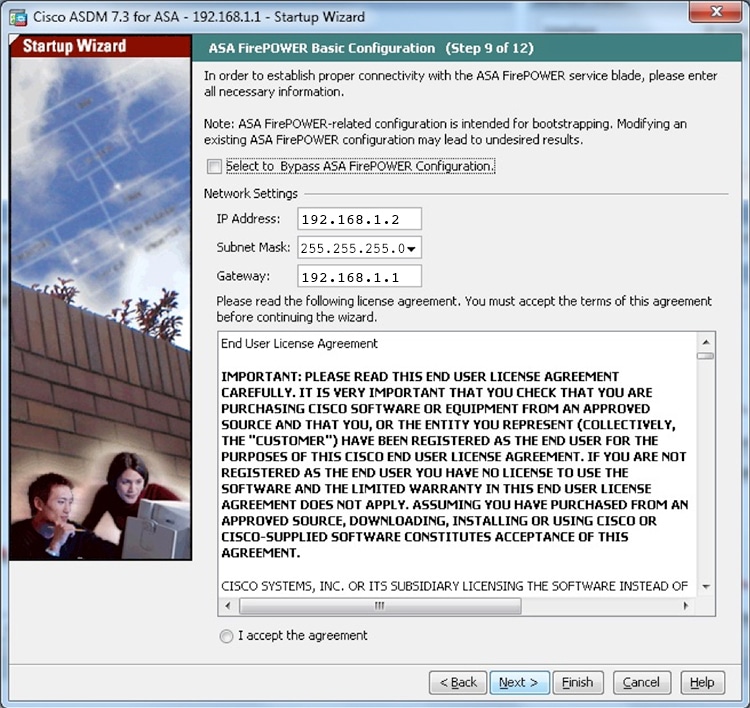
ASDM (Covered in this guide)—A single device manager included on the device.
-
Firepower Management Center (FMC)—A full-featured, multidevice manager on a separate server.
You can also access the FirePOWER CLI for troubleshooting purposes.





 Feedback
Feedback