VNFM Upgrade Operations
The information provided in this section is applicable only when you upgrade your software to release 6.2 and beyond.
 Important |
If you're upgrading to any releases prior to 6.2, follow the upgrade instructions in the Upgrading the Ultra Services Platform Deployment chapter of this guide. |
 Caution |
Upgrade/redeployment operations are disruptive as they involve terminating VMs for the various components that comprise the deployment. When upgrading UAS software roles, all related data is lost. As such, it is strongly recommended that you backup all files related to the deployment including configuration files, logs, and images before performing the upgrade or redeployment. Refer to Backing Up Deployment Information for more information. |
 Important |
The process described in this section is supported only with Ultra M deployments based on OSP 10 and that leverage the Hyper-Converged architecture. |
Limitations
The following limitations exist with the VNFM upgrade feature:
-
This functionality is only available after upgrading to the 6.2 release.
-
The rolling VNFM patch upgrade process can only be used to upgrade to new releases that have a compatible database schema. As new releases become available, Cisco will provide information as to whether or not this functionality can be used to perform the upgrade.
-
For Ultra M deployments, AutoDeploy and AutoIT must be upgraded before using this functionality. Upgrading these products will terminate the VNF deployment.
-
For stand-alone AutoVNF deployments, AutoVNF must be upgraded before using this functionality. Upgrading these products will terminate the VNF deployment.
-
Make sure there are no additional operations running while performing an upgrade/rolling upgrade process.
-
Upgrade/rolling upgrade procedure should be done only in a maintenance window.
Feature Description
 Important |
In 6.2, this feature was not fully qualified and was made available only for testing purposes. In 6.3 and later releases, this functionality is fully qualified. For more information, contact your Cisco Accounts representative. |
With this release, the ESC-based VNFM can optionally be upgraded as part of a rolling patch upgrade process in order to preserve the operational state of the VNF and UAS deployments.
 Important |
The VNFM upgrade process is supported for Ultra M deployments that leverage the Hyper-Converged architecture and for stand-alone AutoVNF deployments. |
VNFM Upgrade Workflow
This section describes the sequence in which the rolling patch upgrade of VNFM occurs.
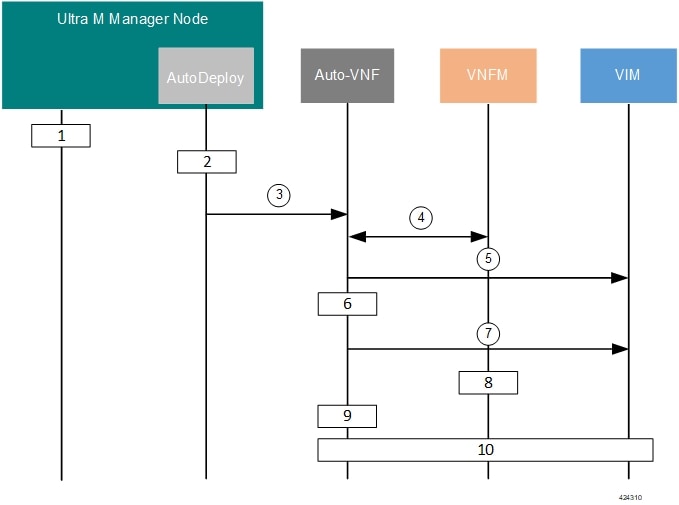
Figure 1 illustrates the VNFM upgrade process for Ultra M deployments. For stand-alone AutoVNF deployments, the upgrade software image is uploaded to the onboarding server (step 1) and the upgrade command is executed from AutoVNF (step 3).
-
Onboard the new USP ISO containing the VNFM upgrade image to the Ultra M Manager node.
-
Update the deployment network service descriptor (NSD) to identify the new package and onboard it.
nsd nsd_name_including_vnfm_vnfd vnf-package [ previous_package_desriptor_name upgrade_package_descriptor_name ]Package information is defined in the VNF package descriptor (vnf-packaged) as follows:
<---SNIP---> vnf-packaged <upgrade_package_descriptor_name> location <package_url> validate-signature false configuration staros external-url /home/ubuntu/system.cfg <---SNIP--->The package must then be referenced in the virtual descriptor unit (VDU) pertaining to the UEM:
<---SNIP---> vdu esc vdu-type cisco-esc login-credential esc_login netconf-credential esc_netconf image vnf-package vnf-rack vnf-rack1 vnf-package primary <upgrade_package_descriptor_name> vnf-package secondary <previous_package_descriptor_name> … <---SNIP--->
Important
The secondary image is used as a fallback in the event an issue is encountered through the upgrade process. If no secondary image is specified, the upgrade process will stop and generate an error log.
-
The rolling upgrade request is triggered through AutoDeploy which initiates the process with AutoVNF.
-
AutoVNF determines which VNFM VM is active and which is standby by communicating with each of the VMs over the management interface.
-
AutoVNF triggers the shutdown of the standby VNFM via the VIM.
-
AutoVNF waits until the VIM confirms that the standby VNFM VM has been completely terminated.
-
AutoVNF initiates the deployment of a new VNFM VM via the VIM using the upgrade image. The VNFM VM is deployed in standby mode.
-
The standby VNFM VM synchronizes data with the active VNFM VM.
-
AutoVNF waits until the VIM confirms that the new VM has been deployed and is in standby mode. If it detects that there is an issue with the VM, AutoVNF re-initiates the VNFM VM with the previous image. If no issues are detected, AutoVNF proceeds with the upgrade process.
-
Repeat the steps 4 to 7 for the VNFM VM that is currently active.
Initiating the VNFM Upgrade
VNFM upgrades are initiated through a remote procedure call (RPC) executed from the ConfD command line interface (CLI) or via a NETCONF API.
Via the CLI
To perform an upgrade using the CLI, log in to AutoDeploy (Ultra M deployments) or AutoVNF (stand-alone AutoVNF deployments) as the ConfD CLI admin user and execute the following command:
update-sw nsd-id <nsd_name> rolling { true | false } vnfd <vnfd_name> vnf-package <pkg_id> NOTES:
-
<nsd_name> and <vnfd_name> are the names of the network service descriptor (NSD) file and VNF descriptor (VNFD) (respectively) in which the VNF component (VNFC) for the VNFM VNF component is defined.
-
If the rolling false operator is used, the upgrade terminates the entire deployment. In this scenario, the vnfd<vnfd_name> operator should not be included in the command. If it is included, a transaction ID for the upgrade is generated and failed. The AutoVNF upstart log reflects this status.
-
<pkg_id> is the name of the USP ISO containing the upgraded VNFM VM image.
-
Ensure that the upgrade package is defined as a VNF package descriptor within the NSD and that it is specified as the primary package in the VNFM VDU configuration.
-
Ensure that the current (pre-upgrade) package is specified as the secondary package in the VNFM VDU configuration in order to provide rollback support in the event of errors.
Via the NETCONF API
Operation: nsd:update-sw
Namespace: xmlns:nsd="http://www.cisco.com/usp/nfv/usp-nsds"
Parameters:
|
Parameter Name |
Required |
Type |
Description |
|---|---|---|---|
|
nsd |
M |
string |
NSD name |
|
rolling |
M |
boolean |
Specifies if the rolling is enabled (true) /disabled (false) |
|
vnfd |
M |
string |
VNFD name, mandatory in case of rolling upgrade |
|
package |
M |
string |
Package descriptor name that should be used to update the vnfd instance mentioned by “vnfd” |
NOTES:
-
If the rolling false operator is used, the upgrade terminates the entire deployment. In this scenario, the vnfd<vnfd_name> operator should not be included in the command. If it is included, a transaction ID for the upgrade is generated and failed. The AutoVNF upstart log reflects this status.
-
Ensure that the upgrade package is defined as a VNF package descriptor within the NSD and that it is specified as the primary package in the VNFM VDU configuration.
-
Ensure that the current (pre-upgrade) package is specified as the secondary package in the VNFM VDU configuration in order to provide rollback support in the event of errors.
Example RPC
<nc:rpc message-id="urn:uuid:bac690a2-08af-4c9f-8765-3c907d6e12ba" <nsd xmlns="http://www.cisco.com/usp/nfv/usp-nsds">
<nsd-id>fremont-autovnf</nsd-id>
<vim-identity>vim1</vim-identity>
<vnfd xmlns="http://www.cisco.com/usp/nfv/usp-nsds">
<vnfd-id>esc</vnfd-id>
<vnf-type>esc</vnf-type>
<version>6.0</version>
<configuration>
<boot-time>1800</boot-time>
<set-vim-instance-name>true</set-vim-instance-name>
</configuration>
<external-connection-point>
<vnfc>esc</vnfc>
<connection-point>eth0</connection-point>
</external-connection-point>
<high-availability>true</high-availability>
<vnfc>
<vnfc-id>esc</vnfc-id>
<health-check>
<enabled>false</enabled>
</health-check>
<vdu>
<vdu-id>esc</vdu-id>
</vdu>
<connection-point>
<connection-point-id>eth0</connection-point-id>
<virtual-link>
<service-vl>mgmt</service-vl>
</virtual-link>
</connection-point>
<connection-point>
<connection-point-id>eth1</connection-point-id>
<virtual-link>
<service-vl>orch</service-vl>
</virtual-link>
</connection-point>
</vnfc>
</vnfd>
</nsd>
<vim xmlns="http://www.cisco.com/usp/nfv/usp-uas-common">
<vim-id>vim1</vim-id>
<api-version>v2</api-version>
<auth-url>http://172.21.201.218:5000/v2.0</auth-url>
<user>vim-admin-creds</user>
<tenant>abcxyz</tenant>
</vim>
<secure-token xmlns="http://www.cisco.com/usp/nfv/usp-secure-token">
<secure-id>vim-admin-creds</secure-id>
<user>abcxyz</user>
<password>******</password>
</secure-token>
<vdu xmlns="http://www.cisco.com/usp/nfv/usp-uas-common">
<vdu-id>esc</vdu-id>
<vdu-type>cisco-esc</vdu-type>
<flavor>
<vcpus>2</vcpus>
<ram>4096</ram>
<root-disk>40</root-disk>
<ephemeral-disk>0</ephemeral-disk>
<swap-disk>0</swap-disk>
</flavor>
<login-credential>esc_login</login-credential>
<netconf-credential>esc_netconf</netconf-credential>
<image>
<vnf-package>usp_throttle</vnf-package>
</image>
<vnf-rack>abcxyz-vnf-rack</vnf-rack>
<vnf-package>
<primary>usp_6_2t</primary>
<secondary>usp_throttle</secondary>
</vnf-package>
<volume/>
</vdu>
<secure-token xmlns="http://www.cisco.com/usp/nfv/usp-secure-token">
<secure-id>esc_login</secure-id>
<user>admin</user>
<password>******</password>
</secure-token>
<secure-token xmlns="http://www.cisco.com/usp/nfv/usp-secure-token">
<secure-id>esc_netconf</secure-id>
<user>admin</user>
<password>******</password>
</secure-token>
<vnf-packaged xmlns="http://www.cisco.com/usp/nfv/usp-uas-common">
<vnf-package-id>usp_throttle</vnf-package-id>
<location>http://192.168.200.61:5000/isos/fremont-autovnf_usp_throttle</location>
<validate-signature>false</validate-signature>
<configuration>
<name>staros</name>
<external-url>http://192.168.200.61:5000/isos/fremont-autovnf_usp_throttle_staros</external-url>
</configuration>
</vnf-packaged>
</config>




 Feedback
Feedback