Feature Information
|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
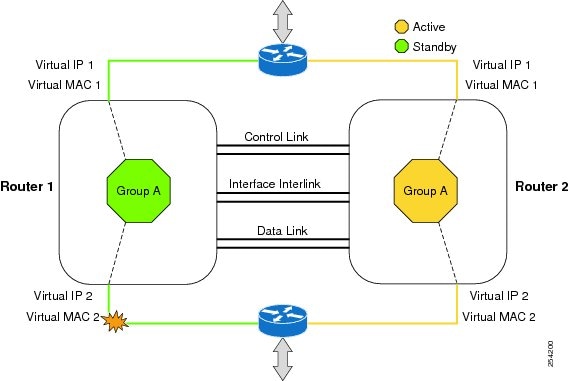
High Availability Support on Cisco Unified Border Element (CUBE) |
Baseline Functionality |
CUBE supports redundancy and failover capability on active and standby routers. |
|
IPv6 flows in High Availability |
Cisco IOS XE Dublin 17.12.1a |
The support for IPv6 flows in high availability is introduced. |






 Feedback
Feedback