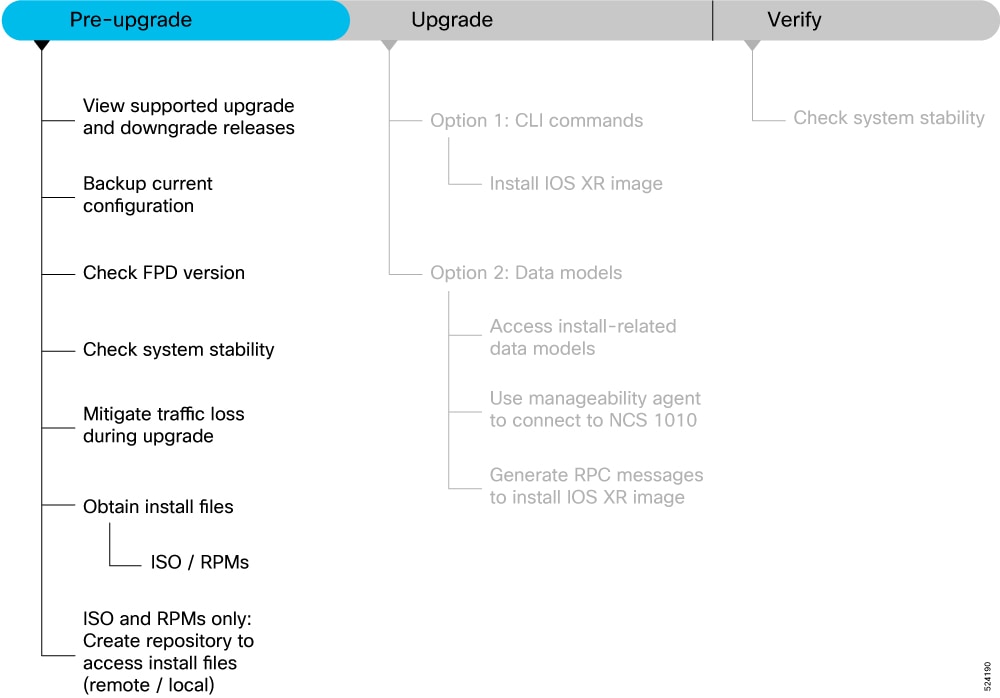
Plan the Software Upgrade
Before you upgrade the software version, prepare NCS 1010 to ensure that the upgrade process is seamless.
Pre-upgrade workflow image for NCS 1010
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
NCS 1010 comes preinstalled with IOS XR software. You can upgrade NCS 1010 by installing a new version of the software. We recommend that you keep the software up-to-date to ensure that NCS 1010 works with the latest features and bug fixes.
During an upgrade:
The newer software replaces the currently active software on NCS 1010.
Packages (RPMs) that have the same name and version in the current and target release versions are not removed or reinstalled.
This section contains the following topics:
Before you upgrade the software version, prepare NCS 1010 to ensure that the upgrade process is seamless.
Pre-upgrade workflow image for NCS 1010

The following table lists the upgrade and downgrade paths supported for Cisco NCS 1010.
|
Upgrade Path |
Downgrade Path |
||
|---|---|---|---|
|
Source Release |
Destination Release |
Source Release |
Destination Release |
|
R24.3.1 |
R24.3.1 |
|
|
Example: |
The ability to recover from a disaster is an essential part of any system maintenance plan. We recommend you backup the configurations in a secure remote location and verify that the transfer is a success, both before and after upgrade.
|
Step 1 |
Create a backup of the running configuration to one of the following locations based on your requirement:
|
|
Step 2 |
Verify that the configuration is backed up. |
A Field Programmable Device (FPD) refers to any programmable hardware device on a chassis, which includes a Field Programmable Gate Array (FPGA). NCS 1010 uses several FPDs that are necessary for chassis, route processor, line cards, and power modules to function properly. Before upgrading the software, check whether the latest FPDs are available on NCS 1010.
 Note |
FPD auto-upgrade is enabled by default on NCS 1010. |
From Release 7.10.1, you can perform FPD upgrade for the breakout and multiplexer/demultiplexer modules. For the breakout modules, you can perform the FPD upgrade in both direct and indirect connections. You can upgrade all the passive modules at once or selectively upgrade the necessary modules as needed.
 Note |
If the FPD in a given SSD is not supported by the current IOS XR software release, the status is displayed as NOT READY . The status will change once FPD support for these SSDs is enabled in future releases. |
|
Location |
FPDs |
|---|---|
|
RP |
|
|
PM0 and PM1 |
|
|
LC |
|
|
Rack |
|
|
Breakout module |
|
|
Multiplexer and demultiplexer modules |
|
Golden FPDs serve as backup FPDs for the primary FPDs. For example, BIOS-Golden is the backup Golden FPD for the BIOS primary FPD. If a primary FPD is corrupted, NCS 1010 boots with the corresponding Golden FPD. The Golden FPDs cannot be upgraded.
Check FPD Version
There are multiple types of FPDs for each type of module. The show hw-module fpd command provides information about each FPD.
RP/0/RP0/CPU0:ios#show hw-module fpd
Fri Feb 17 11:43:28.878 UTC
Auto-upgrade:Enabled
Attribute codes: B golden, P protect, S secure, A Anti Theft aware
FPD Versions
==============
Location Card type HWver FPD device ATR Status Running Programd Reload Loc
-------------------------------------------------------------------------------------------------
0/RP0/CPU0 NCS1010-CTLR-B-K9 1.0 ADMConfig CURRENT 2.30 2.30 NOT REQ
0/RP0/CPU0 NCS1010-CTLR-B-K9 1.0 BIOS S CURRENT 4.40 4.40 0/RP0
0/RP0/CPU0 NCS1010-CTLR-B-K9 1.0 BIOS-Golden BS CURRENT 4.40 0/RP0
0/RP0/CPU0 NCS1010-CTLR-B-K9 1.0 CpuFpga S CURRENT 1.11 1.11 0/RP0
0/RP0/CPU0 NCS1010-CTLR-B-K9 1.0 CpuFpgaGolden BS CURRENT 1.01 0/RP0
0/RP0/CPU0 NCS1010-CTLR-B-K9 1.0 SsdIntelS4510 S CURRENT 11.32 11.32 0/RP0
0/RP0/CPU0 NCS1010-CTLR-B-K9 1.0 TamFw S CURRENT 6.13 6.13 0/RP0
0/RP0/CPU0 NCS1010-CTLR-B-K9 1.0 TamFwGolden BS CURRENT 6.11 0/RP0
0/PM0 NCS1010-AC-PSU 0.0 AP-PriMCU CURRENT 1.03 1.03 NOT REQ
0/PM0 NCS1010-AC-PSU 0.0 AP-SecMCU CURRENT 2.01 2.01 NOT REQ
0/PM1 NCS1010-AC-PSU 0.0 AP-PriMCU CURRENT 1.03 1.03 NOT REQ
0/PM1 NCS1010-AC-PSU 0.0 AP-SecMCU NEED UPGD 1.06 1.06 NOT REQ
0/0/NXR0 NCS1K-E-OLT-R-C 1.0 OLT S CURRENT 1.16 1.16 NOT REQ
0/0/NXR0 NCS1K-E-OLT-R-C 1.0 Raman-1 S CURRENT 1.04 1.04 NOT REQ
0/Rack NCS1010-SA 0.1 EITU-ADMConfig CURRENT 1.04 1.04 NOT REQ
0/Rack NCS1010-SA 0.1 IoFpga S CURRENT 1.12 NOT REQ
0/Rack NCS1010-SA 0.1 IoFpgaGolden BS NEED UPGD 1.12 0.08 NOT REQ
0/Rack NCS1010-SA 0.1 SsdIntelS4510 S CURRENT 11.32 11.32 0/Rack
0/1 NCS1K-MD-32E-C 0.1 MD-32-NEO S CURRENT 2.02 2.02 NOT REQ
0/2 NCS1K-MD-32O-C 10.2 MD-32-ACC S CURRENT 2.18 2.18 NOT REQ
0/3/0 NCS1K-BRK-8 1.0 BRK-8 S CURRENT 2.08 2.08 NOT REQ
0/3/3 NCS1K-BRK-24 1.0 BRK-24 S CURRENT 2.08 2.08 NOT REQ
If the status of any FPD is NEED UPGD, then the upgrade is required for that FPD. In this example, AP-SecMCU and IoFpgaGolden FPD devices need an upgrade. You must ensure that FPDs are upgraded before upgrading NCS 1010.
The following table lists the NCS 1010 FPDs that are distributed across route processor (RP), power modules (PM), line cards (LC), and Rack.
The following table describes the significant fields in the output of the show hw-module fpd command.
|
Field |
Description |
|---|---|
|
Location |
Location of the FPD. |
|
Card type |
PID of the modules such as chassis, card, CPU, and PSU. |
|
HWver |
Hardware version where the FPD resides. |
|
FPD device |
Name of the FPD. |
|
ATR |
Attribute codes. The possible values are:
The attribute code of the primary FPDs is S and the Golden FPDs is BS. |
|
Status |
Status of the FPD. See Table 3. |
|
Running |
FPD image version that has been activated and currently running in the FPD device. |
|
Programd |
FPD image version that has been programmed into the FPD device, but might not be activated. |
|
Reload Loc |
Indicates whether reload of the location is required or not. |
The following table describes the possible values of the Status field in the output of the show hw-module fpd command.
|
FPD Status |
Description |
|---|---|
|
NOT READY |
The driver that owns the FPD device has not initialized the FPD client to handle this device. |
|
CURRENT |
FPD version is up to date and upgrade is not required. |
|
NEED UPGD |
Upgrade is required for this FPD. Check the output of the show fpd package command to determine the recommended FPD version. |
|
UPGD PREP |
FPD is preparing for upgrade. |
|
IN QUEUE |
Upgrade of this FPD is in queue. |
|
UPGD SKIP |
FPD upgrade is not required. For example,
|
|
UPGRADING |
FPD upgrade started and the driver did not report the upgrade progress information yet. |
|
%UPGD |
Percentage of FPD upgrade completion. |
|
RLOAD REQ |
FPD upgrade is successfully completed and the FPD must be reloaded for the new version to take effect. |
|
UPGD FAIL |
FPD upgrade has failed. Check the syslog for failure reason. It could be a timeout or a failure that is reported by the driver. |
|
UPGD DONE |
FPD upgrade is successfully completed. |
The show fpd package command is used to determine the FPDs that are supported with the current software release and the minimum hardware requirements for each FPD.
The following table describes the fields in the output of the show fpd package command.
|
Field |
Description |
|---|---|
|
Card Type |
PID of the modules such as chassis, card, CPU, and PSU. |
|
FPD Description |
Description of the FPD. |
|
Req Reload |
Determines whether reload is required to activate the FPD image. |
|
SW Ver |
Recommended FPD software version for the associated module running the current Cisco IOS XR Software. |
|
Min Req SW Ver |
Minimum required FPD software version to operate the module. |
|
Min Req Board Ver |
Minimum required hardware version for the associated FPD. A minimum hardware requirement of version 0.0 indicates that all the hardware can support this FPD version. |
The automatic FPD upgrade upgrades the FPD version of all the modules to the latest version. When automatic FPD upgrade is enabled, all the FPDs (except the Golden FPDs) that are in NEED UPGD status are upgraded to CURRENT status during the software upgrade.
In NCS 1010, automatic FPD upgrade is enabled by default.
|
Use the following commands to disable automatic FPD upgrade. Example: |
Use the following procedure to upgrade the FPDs manually.
 Note |
The Golden FPDs cannot be upgraded using the CLI. |
|
Step 1 |
Use the show hw-module fpd command to display information about the current FPD version. You can use this command to determine if you must upgrade the FPD. |
||
|
Step 2 |
Use the show alarms brief system active command to display the active alarms. |
||
|
Step 3 |
Use the upgrade hw-module location [location-id] fpd [fpd name] command to upgrade a specific FPD. After upgrading the FPD, the user must wait for upgrade completion. The progress of the FPD upgrade can be monitored using the show hw-module fpd command. Example:
|
||
|
Step 4 |
Use the reload location location-id to reload the FPDs belonging to a specific location with the new version. The Reload Loc field in the output of show hw-module fpd command indicates whether the reload is required or not. Example: |
||
|
Step 5 |
(Optional) Use the upgrade hw-module location all fpd all command to upgrade all the FPDs at once. |
||
|
Step 6 |
(Optional) Use the upgrade hw-module [location [location-id | all]] fpd [fpd name] | all] command to upgrade a specific FPD, all the FPDs, or the FPDs belonging to a specific location. Example:
|
YANG is a data modeling language that helps to create configurations, retrieve operational data and execute actions. NCS 1010 acts on the data definition when these operations are requested using NETCONF RPCs. The data model handles the following types of requirements on NCS 1010 for FPD:
| Operational Data | Native Data Model |
|---|---|
| Auto Upgrade: Enabling or disabling of automatic upgrade of FPD | Cisco-IOS-XR-fpd-infra-cfg.yang |
|
Auto Reload: Enabling or disabling of automatic reload of FPD |
Cisco-IOS-XR-fpd-infra-cfg.yang |
System stability checks are essential to measure the efficiency and ability of an upgrade to function over an extended period.
At the EXEC prompt, execute the following commands to assess basic system stability checks before and after the software upgrade.
|
Command |
Reason |
Workaround |
|---|---|---|
|
|
Verify that all nodes are in |
NA |
|
Or
Or
|
Verify that all necessary interfaces are |
NA |
|
|
Verify that the proper set of packages are active |
NA |
|
|
Verify that the proper set of committed packages are same as active |
Execute ‘install commit’ command |
|
|
Verify/fix configuration file system |
NA |
|
|
Ensure all the FPD versions status are CURRENT |
Execute |
|
|
Display the current state of the disk storage media |
To free up space, remove older .iso image files and bug fix .tar files. |
|
|
Display the current state of the root filesystem (rootfs). By default, the following files are stored in rootfs :
|
The installation is blocked if it utilizes more than 92% of the disk space on the rootfs . To avoid this, we recommend maintaining:
To free up space in rootfs :
|
|
|
Show chassis inventory information |
NA |
|
|
Capture show logging to check for any errors |
NA |
You can obtain the install files based on one of the following options that is best suited to your network:
Golden ISO: You can build a customized golden ISO (GISO) image with the base ISO and the required RPMs to automatically upgrade the software.
Base ISO and Optional RPMs: You can upgrade the software through the standard method where you install the ISO followed by the required RPMs.
Standard ISO and RPMs
|
Step 1 |
Access the Cisco Software Download page. For optimum website experience, we recommend any of the following browsers: Google Chrome, Mozilla Firefox or Internet Explorer. |
|
Step 2 |
Click Browse All and navigate to NCS 1010 using . |
|
Step 3 |
Select the Software Type: IOS XR Software or IOS XR Software Maintenance Upgrades (SMU). |
|
Step 4 |
From the left pane, select the release. For the selected release, the Software Download page displays the downloadable files. For more information, see Install ISO and RPMs. |
|
Step 5 |
Use your Cisco login credentials to download the files. |
This section provides information about the processes involved in upgrading the IOS XR software on NCS 1010
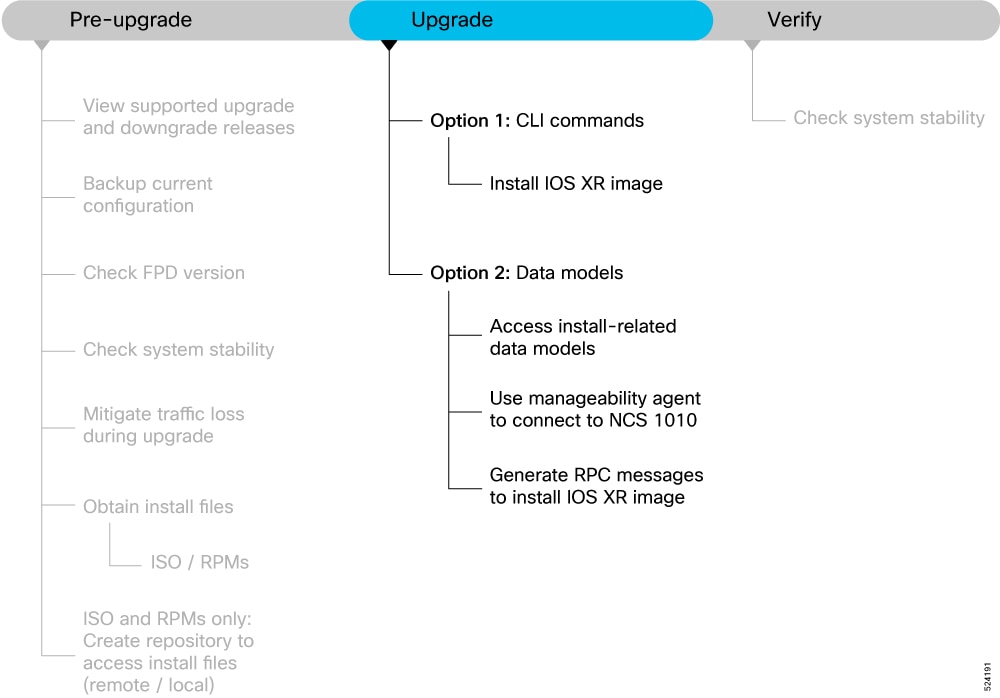
The Cisco IOS XR software can be upgraded using one of these methods:
Upgrade NCS 1010 Using CLI Commands
Upgrade NCS 1010 Using YANG Data Models
There are two options to upgrade your Cisco IOS XR software using the Command Line Interface (CLI):
Base ISO and optional RPMs
Golden ISO (GISO)
|
Step 1 |
Copy the ISO image to be installed either on the NCS 1010 hard disk or on a network server to which NCS 1010 has access. Example: |
||
|
Step 2 |
To verify data integrity, verify the md5 checksum of the copied file with the original MD5 values on CCO. Example: |
||
|
Step 3 |
Install the base image to upgrade the system.
|
||
|
Step 4 |
After the base image is upgraded, install the additional packages. For more information, see Install Additional RPMs and Bug Fixes. If a system fails to boot successfully, or reboots unexpectedly when the package is undergoing a version change, the system is automatically recovered to its old software state.
|
Golden ISO (GISO) upgrades NCS 1010 to a version that has a predefined list of bug fixes (sometimes also called software maintenance updates) with a single operation.
To update the system to the same release version with a different set of bug fixes:
Create a GISO with the base version and all the bug fixes you require
Use the install replace or install package replace commands to install the GISO.
The GISO can include bridging bug fixes for multiple source releases, and installs only the specific bridging bug fixes required for the target release.
The bridging bug fix RPMs can be used in the following scenarios:
To resolve a bug that might stop upgrade.
To meet the prerequisite requirements of a new release version that were not met by the earlier version.
 Note |
The install replace command is supported only with GISO, but not with .rpm packages directly. |
|
Step 1 |
Copy the GISO image file to the /harddisk: of NCS 1010. Example: |
||
|
Step 2 |
Install the GISO.
|
Data models are a programmatic way of configuring and collecting operational data of a network device. They replace the process of manual configuration and can be used to automate configuration tasks across heterogeneous devices in a network.
|
Step 1 |
Navigate to the directory in the release image where the YANG data models are available. Example: |
||||||||||||||||||
|
Step 2 |
View the list of install-related data models on NCS 1010. Example:The following table describes the function of the install-related data models:
You can also access the supported data models to install Cisco IOS XR software from the Github repository. |
Use a manageability agent like NETCONF or gRPC to connect and communicate with NCS 1010. You can send Remote Procedure Calls (RPC) requests to configure or retrieve operational data from NCS 1010. NCS 1010 processes the request and responds to the request through an RPC response. You use the RPCs to send requests to install the software by populating the relevant parameters of a container and leaf in the data model. For more information about understanding the data model structure and using data models, see the Cisco NCS 1010 Data Models Configuration Guide .
Not all software versions are supported as the target upgrade software version. You must review the supported upgrade and downgrade paths, hardware or software limitations, and bridging SMUs required for the version. For more information about checking the release support between the current and target versions, see View Supported Upgrade and Downgrade Releases.
|
Step 1 |
Use the |
|
Step 2 |
Configure the values of the |
|
Step 3 |
Send |
|
Step 4 |
Apply the changes to activate the ISO on NCS 1010 using RPCs by using the Example:View the RPC response received from NCS 1010. In the response, NCS 1010 sends an ID indicating that the changes are applied successfully. |
|
Step 5 |
Verify that the software upgrade is successful. Use the Example:View the RPC response received from NCS 1010. The state of the install operation in the RPC response indicates that the software and the RPMs are upgraded successfully. |
This section provides information about the processes involved in verifying the upgraded software on your NCS 1010.
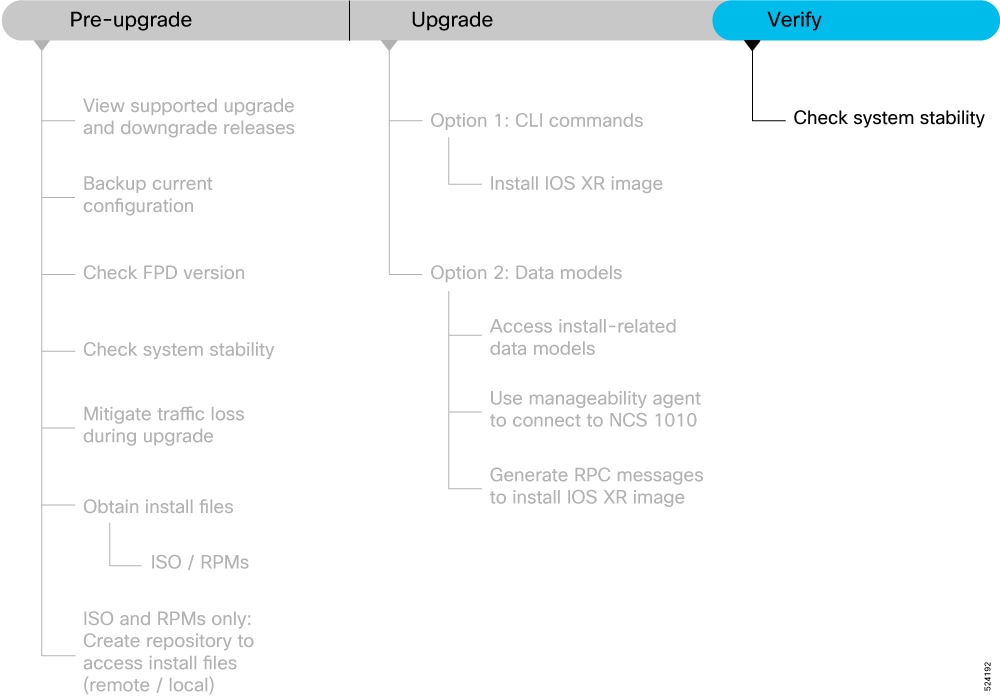
This section contains the following topics:
System stability checks are essential to measure the efficiency and ability of an upgrade to function over an extended period.
At the EXEC prompt, execute the following commands to assess basic system stability checks before and after the software upgrade.
|
Command |
Reason |
Workaround |
|---|---|---|
|
show platform |
Verify that all nodes are in |
NA |
|
show redundancy |
Verify that a standby RP is available, and the system is in |
NA |
|
show install active summary |
Verify that the proper set of packages are active |
NA |
|
show install committed summary |
Verify that the proper set of committed packages are same as active |
Execute ‘install commit’ command |
|
clear configuration inconsistency |
Verify/fix configuration file system |
NA |
|
show hw-module fpd |
Ensure all the FPD versions status are CURRENT |
Execute |
|
show media |
Display the current state of the disk storage media |
To free up space, remove older .iso image files and bug fix .tar files. |
|
show inventory |
Show chassis inventory information |
NA |