Feature Information for Zone-Based Policy Firewalls
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.|
Feature Name |
Releases |
Feature Information |
|---|---|---|
| Zone-Based Firewall Reclassification | Cisco IOS XE Bengaluru 17.6.1 |
The Zone-Based Firewall reclassification feature is introduced. This feature enforces changes, if any, to a policy configuration on the existing sessions. |
|
Smart Licensing support for Zone-Based Firewall on ASR1000 |
Cisco IOS XE Denali 16.3.1 |
The following command was modified: show license all . |
|
Out-of-Order Packet Handling in Zone-Based Policy Firewall |
Cisco IOS XE Release 3.5S |
The Out-of-Order Packet Handling feature allows OoO packets to pass through the router and reach their destination if a session does not require DPI. All Layer 4 traffic with OoO packets are allowed to pass through to their destination. However, if a session requires Layer 7 inspection, the OoO packets are still dropped. |
|
IOS-XE ZBFW Interop with Crypto VPN |
Cisco IOS XE Release 3.17S |
The IOS-XE ZBFW Interop with Crypto VPN feature supports the enabling of zone-based firewall under FlexVPN DVTI. |
|
Zone-Based Firewall Support of Multipath TCP |
Cisco IOS XE Release 3.13S |
Multipoint TCP seamlessly works with zone-based firewall Layer 4 inspection. Multipoint TCP does not work with application layer gateways (ALGs) and application inspection and control (AIC). |
|
Firewall—NetMeeting Directory (LDAP) ALG Support |
Cisco IOS XE Release 3.1S |
LDAP is an application protocol that is used for querying and updating information stored on directory servers. The Firewall—Netmeeting (LDAP) Directory ALG Support feature enables Cisco firewalls to support Layer 4 LDAP inspection by default. The following command was introduced: match protocol . |
|
Debuggability Enhancement in Zone-Based Firewall (Phase-II) |
Cisco IOS XE Release 3.10S |
The Debuggability Enhancement Zone-Based Firewall feature provides severity levels for debug logs. |
|
Zone-Based Firewall—Default Zone |
Cisco IOS Release 2.6 |
The Zone-Based Firewall— Default Zone feature introduces a default zone that enables a firewall policy to be configured on a zone pair that consist of a zone and a default zone. Any interface without explicit zone membership belongs to the default zone. |
|
Zone-Based Policy Firewalls |
Cisco IOS Release 2.1 |
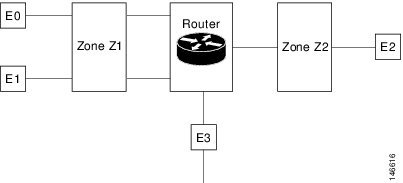
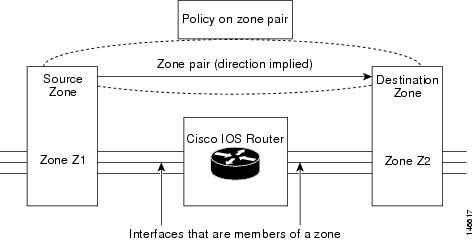
The Zone-Based Policy Firewall feature provides a Cisco IOS XE software unidirectional firewall policy between groups of interfaces known as zones. |



 Feedback
Feedback