Introduction to Access Control
Access control is a hierarchical policy-based feature that allows you to specify, inspect, and log (non-fast-pathed) network traffic.
Each managed device can be targeted by one access control policy. The data that the policy’s target devices collect about your network traffic can be used to filter and control that traffic based on:
-
simple, easily determined transport and network layer characteristics: source and destination, port, protocol, and so on
-
the latest contextual information on the traffic, including characteristics such as reputation, risk, business relevance, application used, or URL visited
-
realm, user, user group, or ISE attribute
-
characteristics of encrypted traffic; you can also decrypt this traffic for further analysis
-
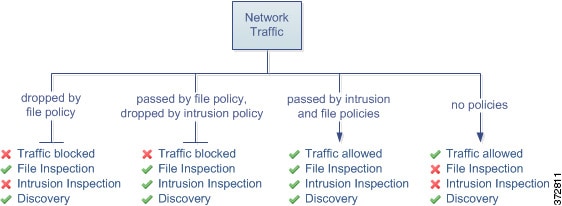
whether unencrypted or decrypted traffic contains a prohibited file, detected malware, or intrusion attempt
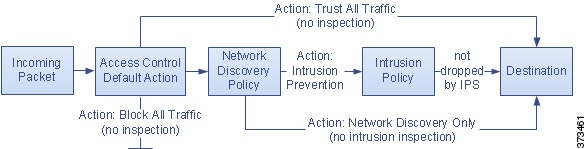
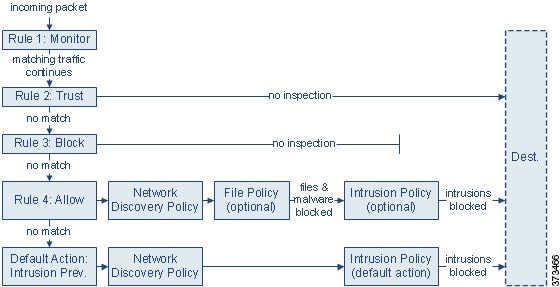
Each type of traffic inspection and control occurs where it makes the most sense for maximum flexibility and performance. For example, reputation-based blocking uses simple source and destination data, so it can block prohibited traffic early in the process. In contrast, detecting and blocking intrusions and exploits is a last-line defense.




 Feedback
Feedback