|
Password for admin user.
|
Whatever you entered.
|
Explicit.
|
|
Management IP address.
|
Obtained through DHCP.
Threat Defense Virtual: 192.168.45.45
Firepower 4100/9300: The management IP address you set when you deployed the logical device.
|
Default.
|
|
Management gateway.
|
The data interfaces on the device. Typically the
outside interface becomes the route to the Internet. The management
gateway works for from-the-device traffic only. If the device receives a default
gateway from the DHCP server, then that gateway is
used.
Firepower 4100/9300: The gateway IP address you set when you deployed the logical device.
ISA 3000: 192.168.45.1
Threat Defense Virtual: 192.168.45.1
|
Default.
|
|
DNS servers for the management interface.
|
The OpenDNS public DNS servers, IPv4:
208.67.220.220, 208.67.222.222; IPv6: 2620:119:35::35, or
whatever you entered. DNS servers obtained from DHCP are never
used.
Firepower 4100/9300: The DNS servers you set when you deployed the logical device.
|
Explicit.
|
|
Management hostname.
|
firepower or whatever you entered.
Firepower 4100/9300: The hostname you set when you deployed the logical device.
|
Explicit.
|
|
Management access through data interfaces.
|
A data interface management access list rule allows HTTPS access through the inside
interface. SSH connections are not allowed. Both IPv4 and IPv6
connections are allowed.
Firepower 4100/9300: No data interfaces have default management access rules.
ISA 3000: No data interfaces have default management access rules.
Threat Defense Virtual: No data interfaces have default management access rules.
|
Implied.
|
|
System time.
|
The time zone and NTP servers you selected.
Firepower 4100/9300: System time is inherited from the chassis.
ISA 3000: Cisco NTP servers: 0.sourcefire.pool.ntp.org, 1.sourcefire.pool.ntp.org, 2.sourcefire.pool.ntp.org.
|
Explicit.
|
|
Smart license.
|
Either registered with a base license, or the evaluation period activated, whichever you selected.
Subscription licenses are not enabled. Go to the smart licensing page to enable them.
|
Explicit.
|
|
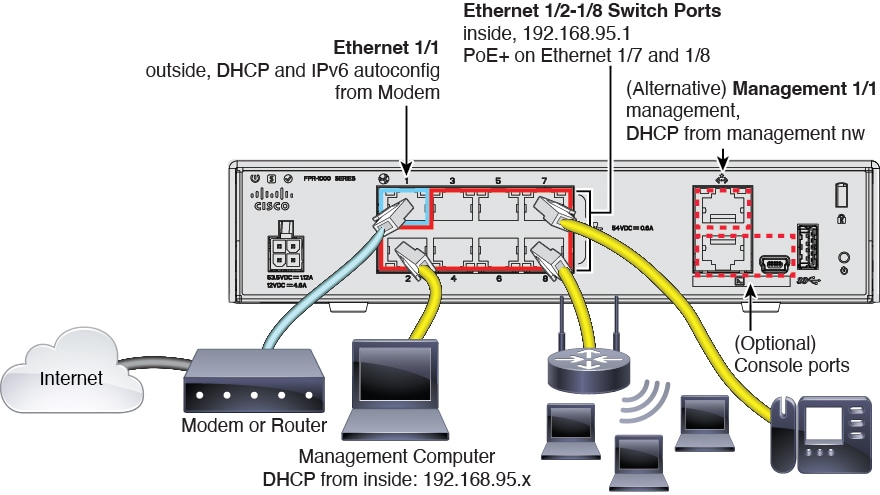
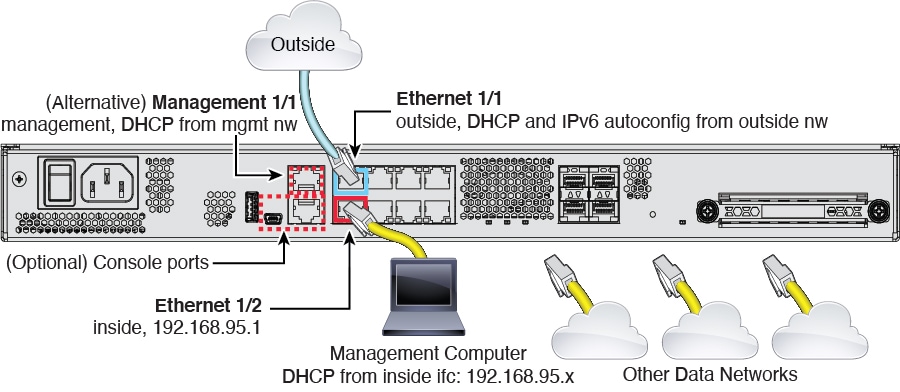
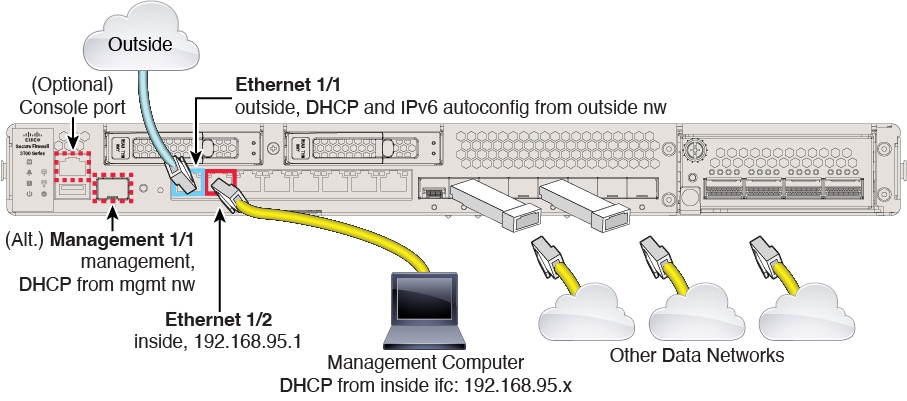
Inside interface IP address.
|
192.168.95.1/24
Firepower 4100/9300: Data interfaces are not pre-configured.
ISA 3000: None. You must set the BVI1 IP address manually.
Threat Defense Virtual: 192.168.45.1/24
|
Default.
|
|
DHCP server for inside clients.
|
Running on the inside interface with
the address pool 192.168.95.5 - 192.168.95.254.
Firepower 4100/9300: No DHCP server enabled.
ISA 3000: No DHCP server enabled.
Threat Defense Virtual: The address pool on the inside interface is 192.168.45.46 - 192.168.45.254.
|
Default.
|
|
DHCP auto-configuration for inside clients. (Auto-configuration supplies clients with addresses for WINS and DNS servers.)
|
Enabled on outside interface if you use DHCP to obtain the outside interface IPv4 address.
If you use static addressing, DHCP auto-configuration is disabled.
|
Explicit, but indirectly.
|
|
Data interface configuration.
|
-
Firepower 1010 and Secure Firewall 1210/1220—The outside interface, Ethernet1/1, is a physical firewall interface. All other interfaces are switch ports that are enabled
and part of VLAN1, the inside interface. You can plug end points or switches into these ports and obtain addresses from the
DHCP server for the inside interface.
-
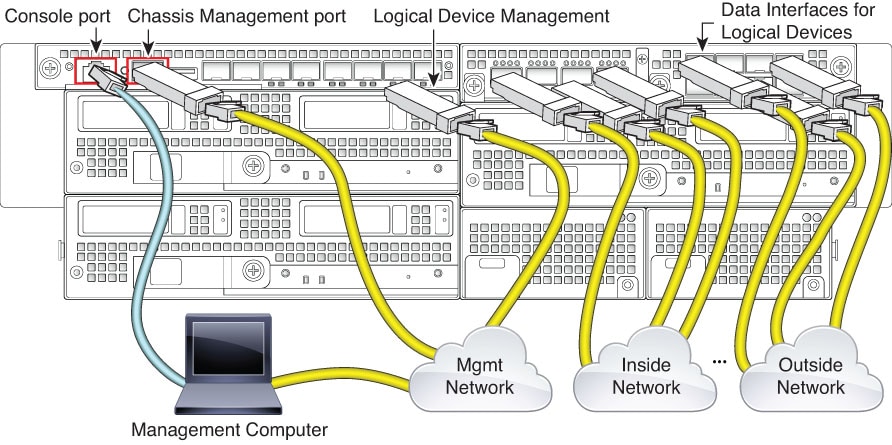
Firepower 4100/9300—All data inetrfaces are disabled.
-
ISA 3000—All data interfaces are enabled and part of the same bridge group, BVI1. GigabitEthernet1/1 and 1/3 are outside interfaces,
and GigabitEthernet1/2 and 1/4 are inside interfaces. GigabitEthernet1/1 (outside1) and 1/2 (inside1), and GigabitEthernet1/3
(outside2) and 1/4 (inside2) (non-fiber models only) are configured as Hardware Bypass pairs.
-
All other models—The outside and inside interfaces are the only ones configured and enabled. All other data interfaces are
disabled.
|
Default.
|
|
Outside physical interface and IP address.
|
The default outside port based on the device model. See Default Configuration Prior to Initial Setup.
The IP address is obtained by DHCP and IPv6
autoconfiguration, or it is a static address as entered
(IPv4, IPv6, or both).
Firepower 4100/9300: Data interfaces are not pre-configured.
ISA 3000: None. You must set the BVI1 IP address manually.
|
Interface is Default.
Addressing is Explicit.
|
|
Static routes.
|
If you configure a static IPv4 or IPv6 address for the outside interface, a static default route is configured for IPv4/IPv6
as appropriate, pointing to the gateway you defined for that address type. If you select DHCP, the default route is obtained
from the DHCP server.
Network objects are also created for the gateway and the "any" address, that is, 0.0.0.0/0 for IPv4, ::/0 for IPv6.
|
Implied.
|
|
Security zones.
|
inside_zone, containing the inside interfaces. For the Firepower 4100/9300, you need to add interfaces manually to this security zone.
outside_zone, containing the outside interfaces. For the Firepower 4100/9300, you need to add interfaces manually to this zone.
(You can edit these zones to add other interfaces, or create your own zones.)
|
Implied.
|
|
Access control policy.
|
A rule trusting all traffic from the inside_zone to the outside_zone. This allows without inspection all traffic from users
inside your network to get outside, and all return traffic for those connections.
The default action for any other traffic is to block it. This prevents any traffic initiated from outside to enter your network.
Firepower 4100/9300: There are no pre-configured access rules.
ISA 3000: A rule trusting all traffic from the inside_zone to the outside_zone, and a rule trusting all traffic from the outside_zone
to the inside_zone. Traffic is not blocked. The device also has rules trusting all traffic between the interfaces in the inside_zone
and in the outside_zone. This allows without inspection all traffic between users on the inside, and between users on the
outside.
|
Implied.
|
|
NAT
|
An interface dynamic PAT rule translates the source address for any IPv4 traffic destined to the outside interface to a unique port on the outside interface's IP address.
There are additional hidden PAT rules to enable HTTPS access through the inside interfaces, and routing through the data interfaces
for the management address. These do not appear in the NAT table, but you will see them if you use the show nat command in the CLI.
Firepower 4100/9300: NAT is not pre-configured.
ISA 3000: NAT is not pre-configured.
|
Implied.
|







 Feedback
Feedback