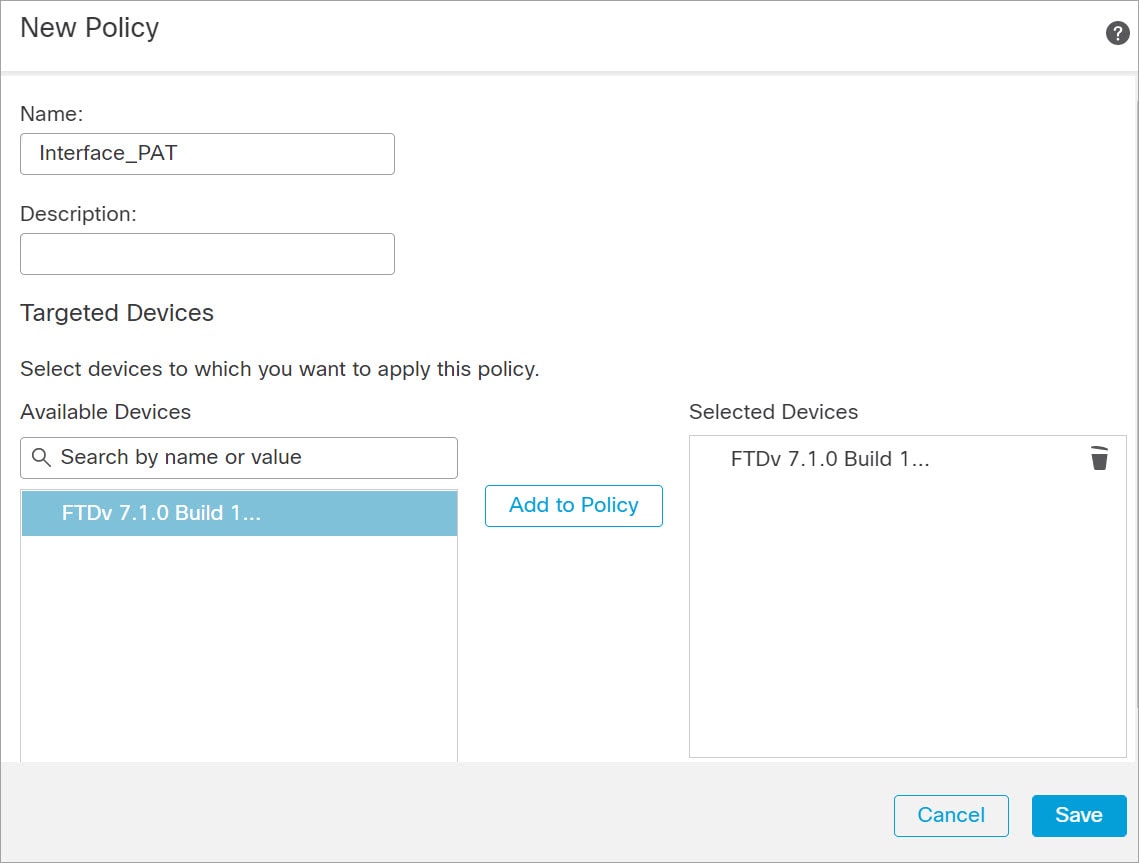
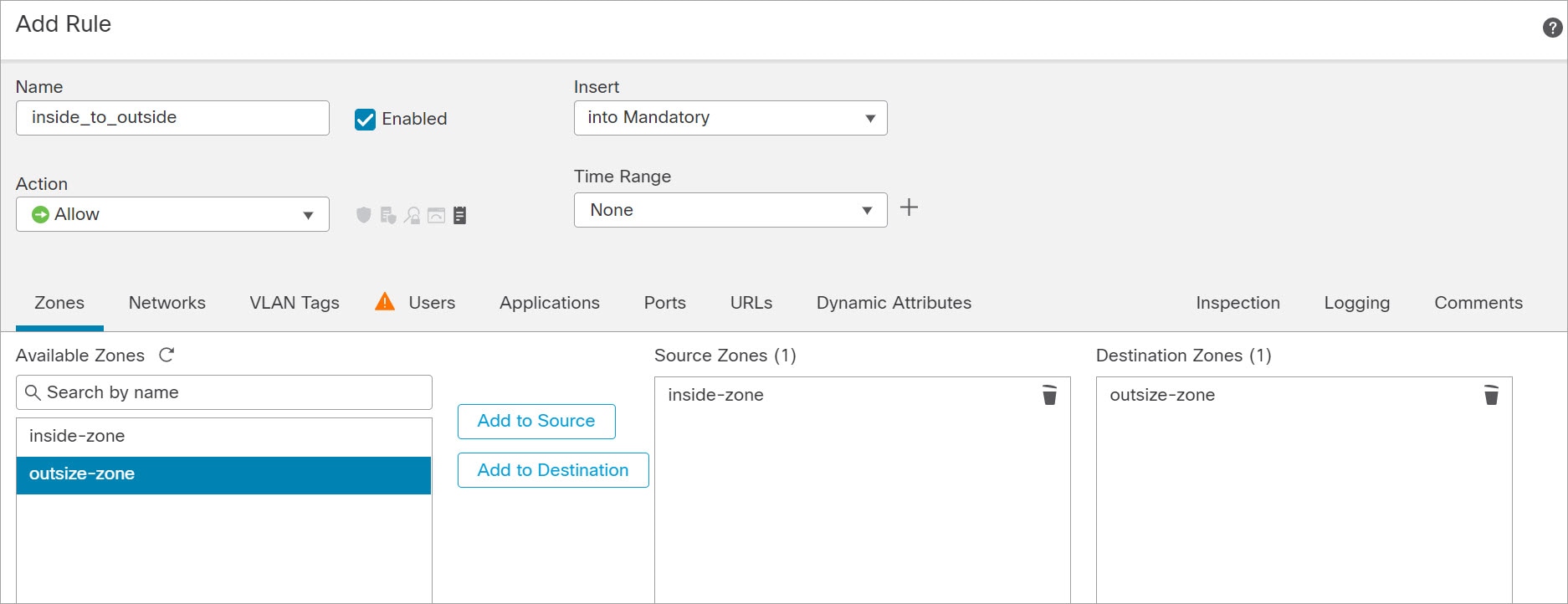
About Secure Firewall Threat Defense Virtual with the Secure Firewall Management Center
The Secure Firewall Threat Defense Virtual is the virtualized component of the Cisco NGFW solution. The threat defense virtual provides next-generation firewall services, including stateful firewalling, routing, VPN, Next-Generation Intrusion Prevention System (NGIPS), Application Visibility and Control (AVC), URL filtering, and malware defense.
You can manage the threat defense virtual using the management center , a full-featured, multidevice manager on a separate server. The threat defense virtual registers and communicates with the management center on the Management interface that you allocated to the threat defense virtual machine.
The threat defense virtual registers and communicates with the management center on the Management interface that you allocated to the threat defense virtual machine.
For troubleshooting purposes, you can access the threat defense CLI using SSH on the Management interface, or you can connect to the threat defense from the management center CLI.
This guide describes how to deploy a standalone threat defense virtual device managed with the management center. For detailed configuration information on the management center, see the Management Center Administration Guide and Management Center Device Configuration Guide.
For information about installing the management center, see the Cisco Firepower Management Center 1600, 2600, and 4600 Hardware Installation Guide or Management Center Virtual Getting Started Guide.














 )
)





 Feedback
Feedback