End-to-End Procedure
See the following tasks to deploy and configure the ASA on your chassis.

|
|
Cisco Commerce Workspace |
Chassis Manager: Register the Chassis with the Licensing Server: Obtain feature licenses. |
|
|
Smart Software Manager |
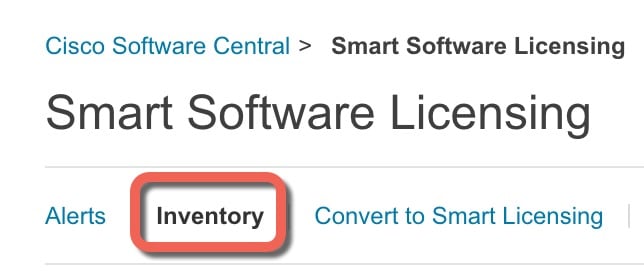
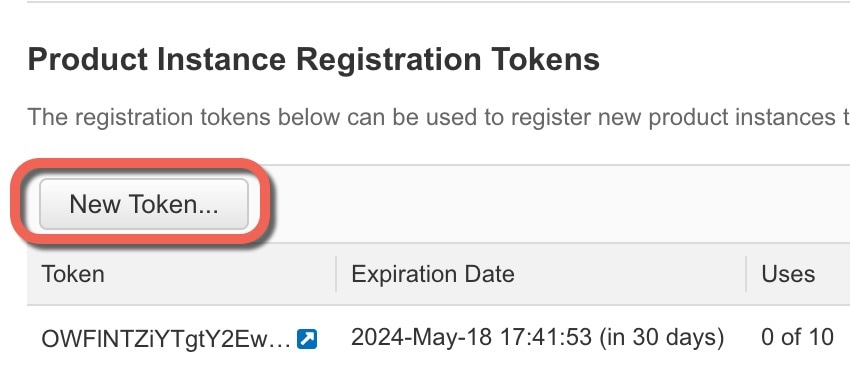
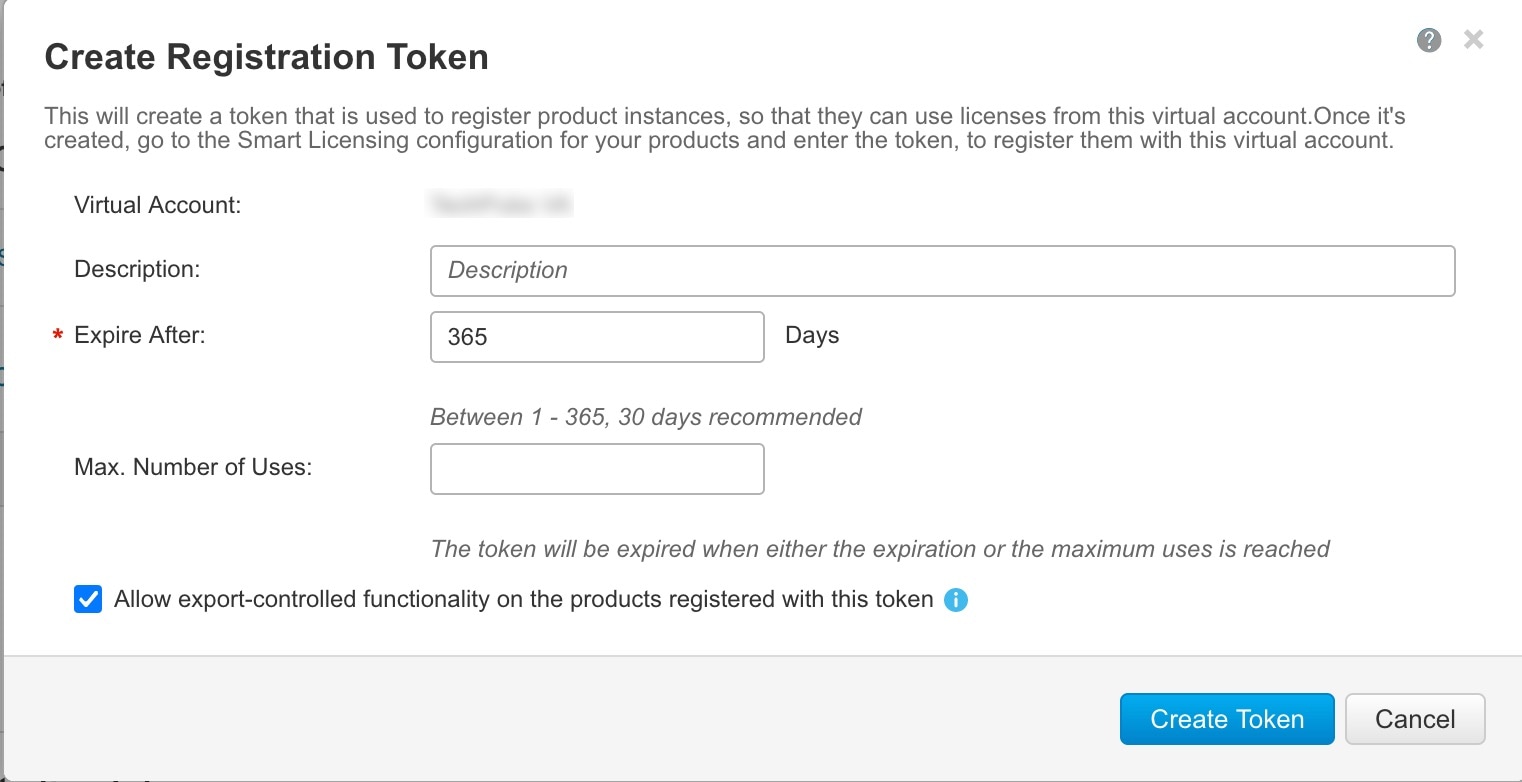
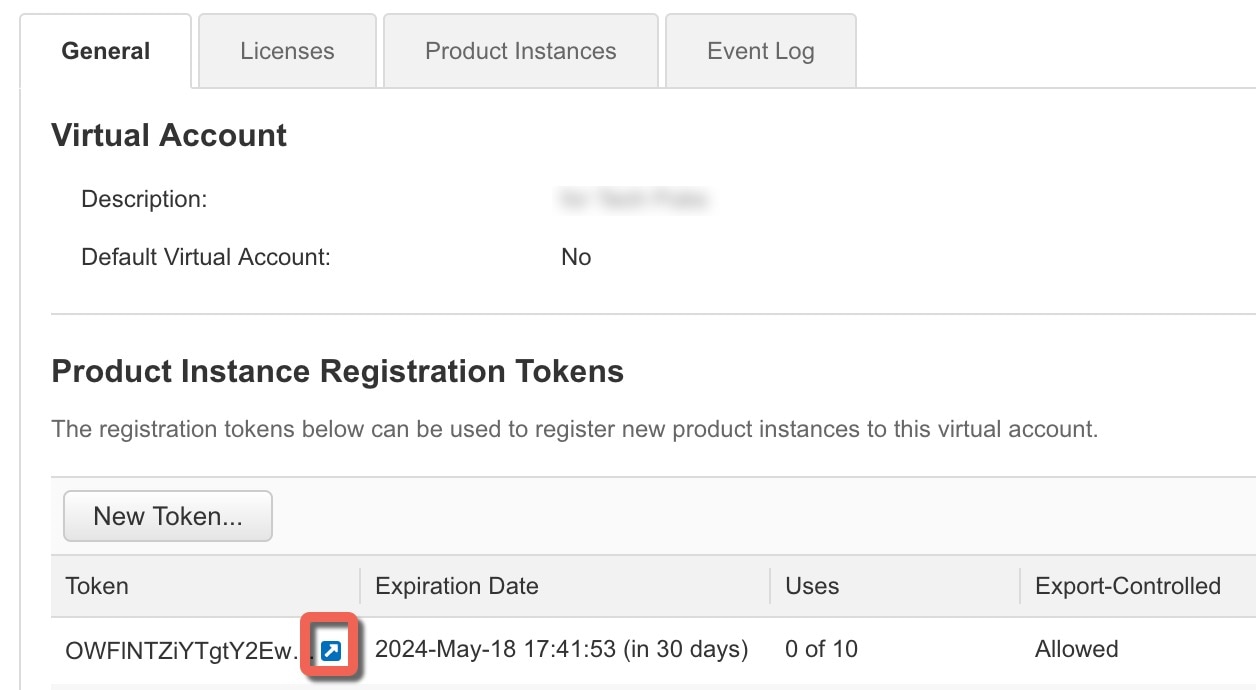
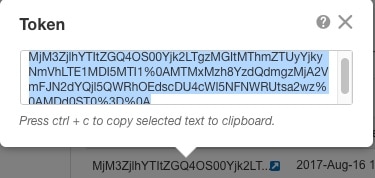
Chassis Manager: Register the Chassis with the Licensing Server: Generate a license token for the chassis. |
|
|
Chassis Manager |
Chassis Manager: Register the Chassis with the Licensing Server: Register the chassis with the Smart Licensing server. |
|
|
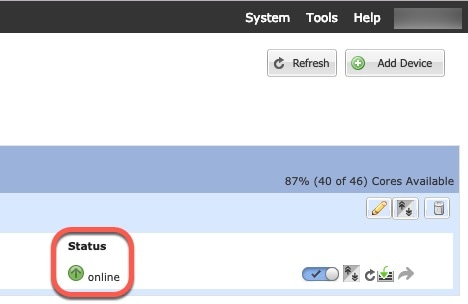
Chassis Manager |
|
|
|
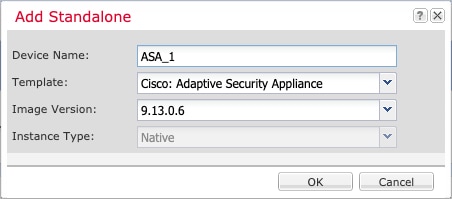
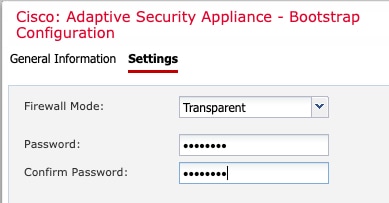
ASDM |
|
|
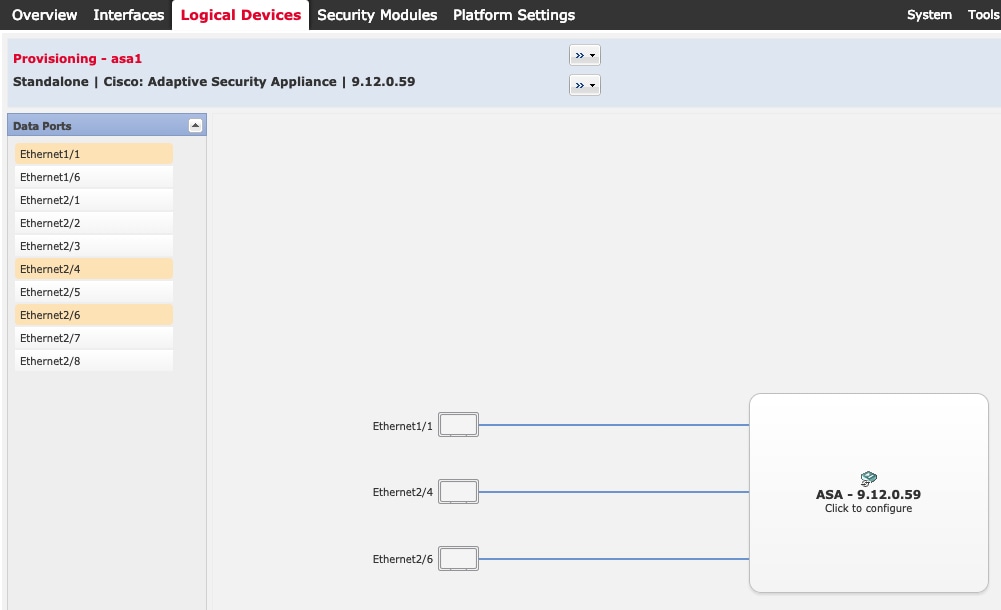
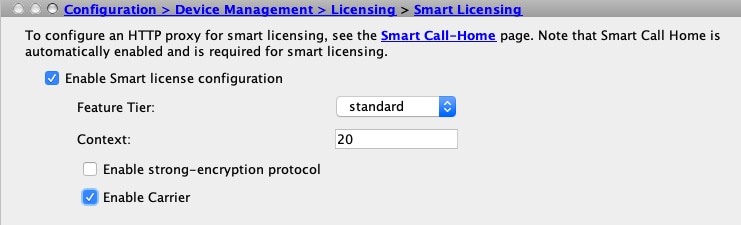
ASDM |
||
|
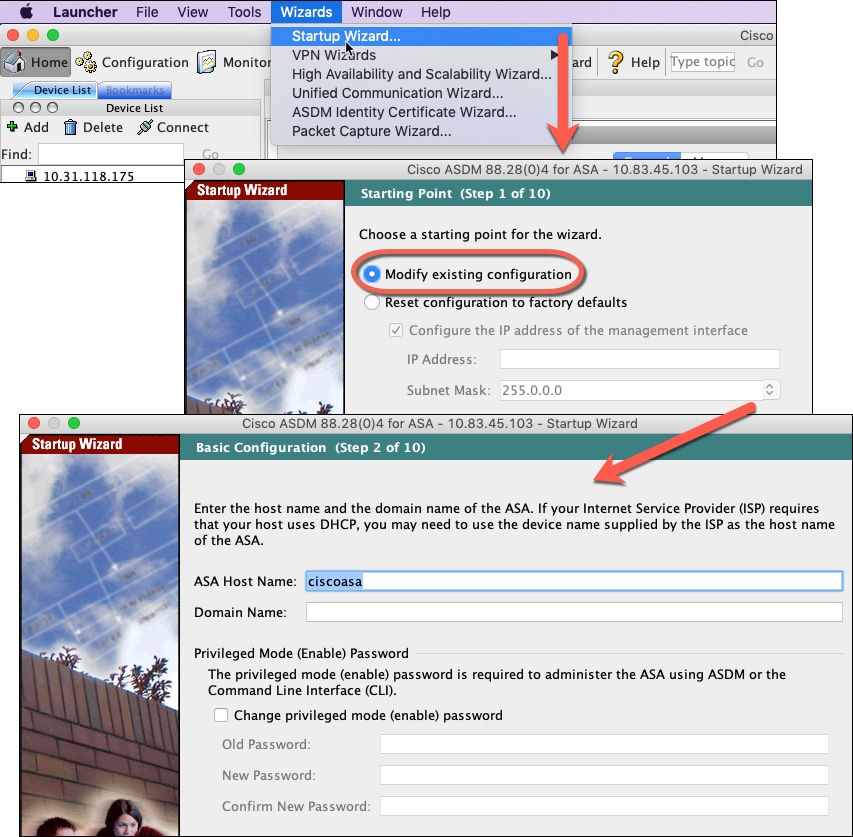
ASDM |




 Feedback
Feedback