Enable the threat
defense interfaces, assign them to security zones, and set the IP addresses. Typically, you must configure at least a minimum of
two interfaces to have a
system that passes meaningful traffic. Normally, you would have an outside interface
that faces the upstream router or internet, and one or more inside interfaces for
your organization’s networks. Some of these interfaces might be “demilitarized
zones” (DMZs), where you place publically-accessible assets such as your web
server.
A typical edge-routing situation is to obtain the outside interface address through
DHCP from your ISP, while you define static addresses on the inside interfaces.
The following example configures a routed mode inside interface with a static address
and a routed mode outside interface using DHCP.
|
Step 1
|
Choose , and click the Edit ( ) for the firewall. ) for the firewall.
|
|
Step 2
|
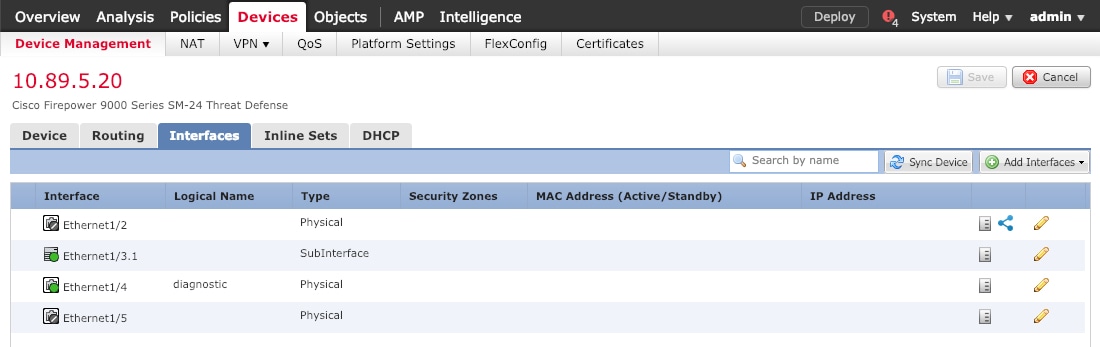
Click Interfaces.
|
|
Step 3
|
Click Edit ( ) for the interface that you want to use for inside. ) for the interface that you want to use for inside.
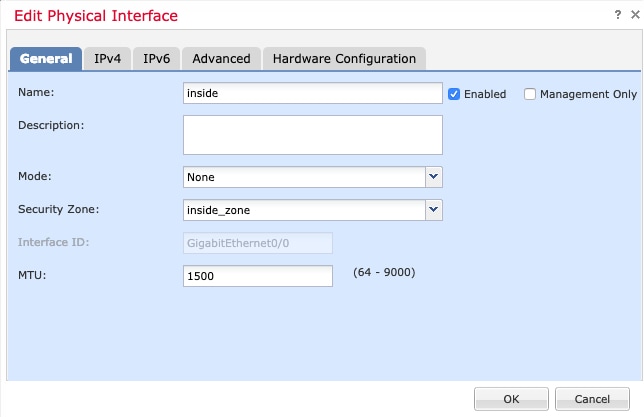
The General tab appears.
-
Enter a Name up to 48 characters in length.
For example, name the interface inside.
-
Check the Enabled check
box.
-
Leave the Mode set to
None.
-
From the Security Zone drop-down list, choose an
existing inside security zone or add a new one by clicking
New.
For example, add a zone called inside_zone.
Each interface must be assigned to a security zone and/or interface
group. An interface can belong to only one security zone, but can
also belong to multiple interface groups. You apply your security
policy based on zones or groups. For example, you can assign the
inside interface to the inside zone; and the outside interface to
the outside zone. Then you can configure your access control policy
to enable traffic to go from inside to outside, but not from outside
to inside. Most policies only support security zones; you can use
zones or interface groups in NAT policies, prefilter policies, and
QoS policies.
-
Click the IPv4 and/or
IPv6 tab.
-
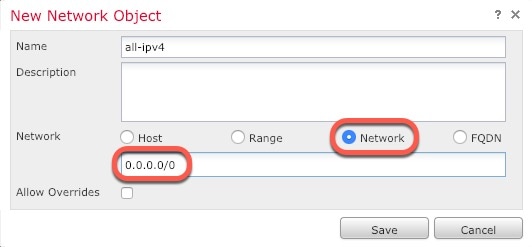
IPv4—Choose Use Static
IP from the drop-down list, and enter an IP
address and subnet mask in slash notation.
For
example, enter
192.168.1.1/24 
-
IPv6—Check the
Autoconfiguration check box for
stateless autoconfiguration.
-
Click OK.
|
|
Step 4
|
Click the Edit ( ) for the interface that you want to use for outside. ) for the interface that you want to use for outside.
The General tab appears.

|
Note
|
If you pre-configured this interface for manager access, then the
interface will already be named, enabled, and addressed. You should not
alter any of these basic settings because doing so will disrupt the management center management connection. You can still configure the Security Zone on
this screen for through traffic policies.
|
-
Enter a Name up to 48 characters in length.
For example, name the interface outside.
-
Check the Enabled check
box.
-
Leave the Mode set to
None.
-
From the Security Zone drop-down list, choose an
existing outside security zone or add a new one by clicking
New.
For example, add a zone called
outside_zone.
-
Click the IPv4 and/or
IPv6 tab.
-
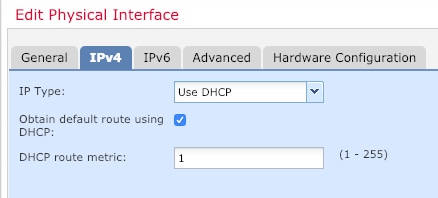
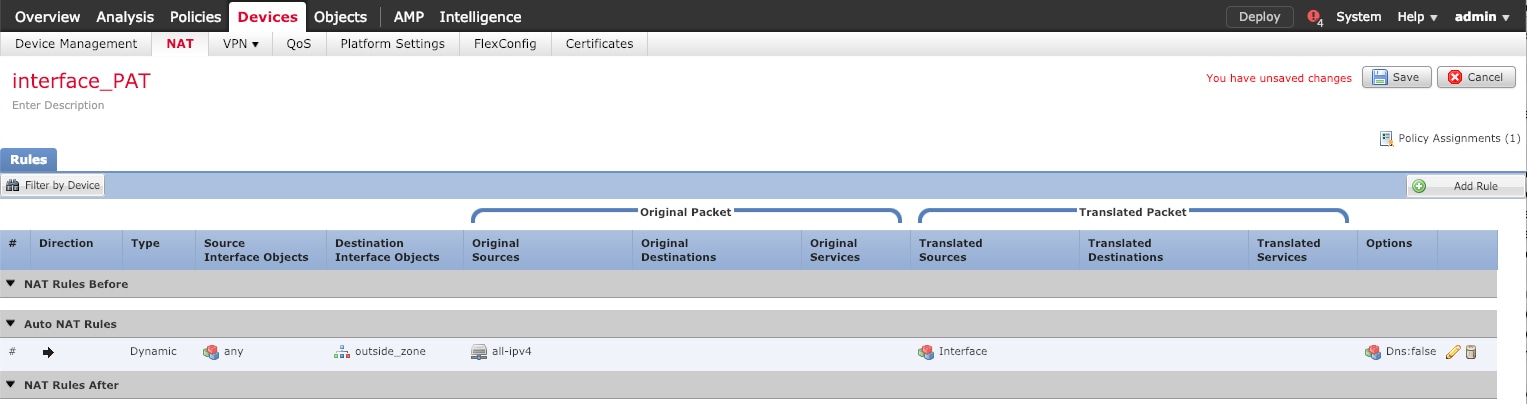
IPv4—Choose Use
DHCP, and configure the following optional
parameters:
-
Obtain default route using
DHCP—Obtains the default route from
the DHCP server.
-
DHCP route metric—Assigns an
administrative distance to the learned route,
between 1 and 255. The default administrative
distance for the learned routes is 1.
-
IPv6—Check the
Autoconfiguration check box for
stateless autoconfiguration.
-
Click OK.
|
|
Step 5
|
Click Save.
|


 )
)




 )
)
 Feedback
Feedback