|
SecureX ribbon
|
7.0
|
Any
|
The SecureX ribbon pivots into SecureX for instant visibility into the threat landscape across your Cisco security products.
To display the SecureX ribbon in FMC, see the Firepower and SecureX Integration Guide at https://cisco.com/go/firepower-securex-documentation.
New/Modified screens: New page: System > SecureX
|
|
Send all connection events to the Cisco cloud
|
7.0
|
Any
|
You can now send all connection events to the Cisco cloud, rather than just sending high-priority connection events.
New/Modified screens: New option on the System > Integration > Cloud Services page
|
|
Cross-launch to view data in Secure Network
Analytics
|
6.7
|
Any
|
This feature introduces a quick way to create multiple entries for your Secure Network
Analytics appliance on the Analysis > Contextual Cross-Launch page.
These entries allow you to right-click a relevant event to cross-launch Secure Network
Analytics and display information related to the data point from which you cross-launched.
New menu item: System > Logging > Security Analytics and Logging
New page to configure sending events to Secure Network
Analytics.
|
|
Contextual cross-launch from additional field types
|
6.7
|
Any
|
You can now cross-launch into an external application using the following additional types of event data:
New menu options: Contextual-cross launch options are now available when right-clicking the above data types for events in
Dashboard widgets and event tables on pages under the Analysis menu.
Supported platforms: Firepower Management Center
|
|
Integration with IBM QRadar
|
6.0 and later
|
Any
|
IBM QRadar users can use a new Firepower-specific app to analyze their event data.
Available functionality is affected by your Firepower version.
See Event Analysis in IBM QRadar.
|
|
Enhancements to integration with Cisco Threat
Response
|
6.5
|
Any
|
Modified screens: New options on System > Integration > Cloud Services.
Supported Platforms: All devices supported in this release, either via direct integration or syslog.
|
|
Syslog
|
6.5
|
Any
|
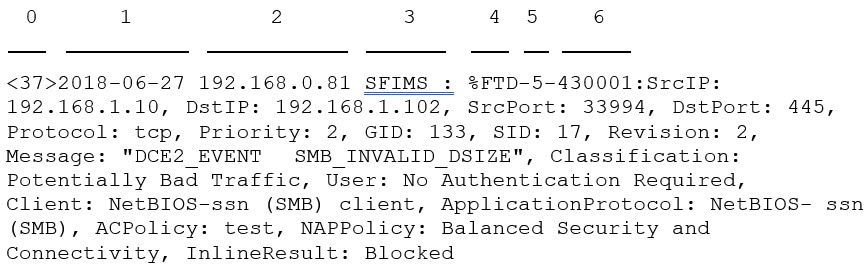
The AccessControlRuleName field is now available in intrusion event syslog messages.
|
|
Integration with Cisco Security Packet
Analyzer
|
6.5
|
Any
|
Support for this feature was removed.
|
|
Integration with Cisco Threat
Response
|
6.3 (via syslog, using a proxy collector)
6.4 (direct)
|
Any
|
Integrate Firepower intrusion event data with data from other sources for a unified view of threats on your network using
the powerful analysis tools in Cisco Threat
Response.
Modified screens (version 6.4): New options on System > Integration > Cloud Services.
Supported Platforms: Firepower Threat
Defense devices running version 6.3 (via syslog) or 6.4.
|
|
Syslog support for File and Malware events
|
6.4
|
Any
|
Fully-qualified file and malware event data can now be sent from managed devices via syslog.
Modified screens: Policies > Access Control > Access Control > Logging.
Supported Platforms: All managed devices running version 6.4.
|
|
Integration with Splunk
|
Supports all 6.x versions
|
Any
|
Splunk users can use a new, separate Splunk app, Cisco Secure Firewall (f.k.a. Firepower) app for Splunk, to analyze events.
Available functionality is affected by your Firepower version.
See Event Analysis in Splunk.
|
|
Integration with Cisco Security Packet
Analyzer
|
6.3
|
Any
|
Feature introduced: Instantly query Cisco Security Packet
Analyzer for packets related to an event, then click to examine the results in Cisco Security Packet
Analyzer or download them for analysis in another external tool.
New screens:
New menu options: Query Packet Analyzer menu item when right-clicking on an event on Dashboard pages and event tables on pages under the Analysis menu.
Supported platforms: Firepower Management Center
|
|
Contextual cross-launch
|
6.3
|
Any
|
Feature introduced: Right-click an event to look up related information in predefined or custom URL-based external resources.
New screens:
New menu options: Multiple options when right-clicking on an event on Dashboard pages and event tables on pages under the
Analysis menu.
Supported platforms: Firepower Management Center
|
|
Syslog messages for connection and intrusion events
|
6.3
|
Any
|
Ability to send fully-qualified connection and intrusion events to external storage and tools via syslog, using new unified
and simplified configurations. Message headers are now standardized and include event type identifiers, and messages are smaller
because fields with unknown and empty values are omitted.
Supported Platforms:
-
All new functionality: FTD devices running version 6.3.
-
Some new functionality: Non-FTD devices running version 6.3.
-
Less new functionality: All devices running versions older than 6.3.
For more information, see the topics under About Sending Syslog Messages for Security Events and subtopics.
|
|
eStreamer
|
6.3
|
Any
|
Moved eStreamer content from the Host Identity Sources chapter to this chapter and added a summary comparing eStreamer to
syslog.
|
 )
)
 )
) )
) )
)
 )
) )
) )
) Feedback
Feedback