About Licenses
Cisco Smart Licensing is a flexible licensing model that provides you with an easier, faster, and more consistent way to purchase and manage software across the Cisco portfolio and across your organization. And it’s secure—you control what users can access. With Smart Licensing you get:
-
Easy Activation: Smart Licensing establishes a pool of software licenses that can be used across the entire organization—no more PAKs (Product Activation Keys).
-
Unified Management: My Cisco Entitlements (MCE) provides a complete view into all of your Cisco products and services in an easy-to-use portal, so you always know what you have and what you are using.
-
License Flexibility: Your software is not node-locked to your hardware, so you can easily use and transfer licenses as needed.
To use Smart Licensing, you must first set up a Smart Account on Cisco Software Central (software.cisco.com).
For a more detailed overview on Cisco Licensing, go to cisco.com/go/licensingguide
Smart Software Manager and Accounts
When you purchase one or more licenses, you manage them in the Smart Software Manager: https://software.cisco.com/#module/SmartLicensing. The Smart Software Manager lets you create a primary account for your organization. If you do not yet have an account, click the link to set up a new account. The Smart Software Manager lets you create a primary account for your organization.
By default, your licenses are assigned to the Default Virtual Account under your primary account. As the account administrator, you can create additional virtual accounts; for example, for regions, departments, or subsidiaries. Multiple virtual accounts help you manage large numbers of licenses and devices.
You manage licenses by virtual account. Only that virtual account’s devices can use the licenses assigned to the account. If you need additional licenses, you can transfer an unused license from another virtual account. You can also transfer devices between virtual accounts.
Licensing Options for Air-Gapped Deployments
The following table compares the available licensing options for environments without internet access. Your sales representative may have additional advice for your specific situation.
|
Smart Software Manager On-Prem |
Specific License Reservation |
|---|---|
|
Scalable for a large number of products |
Best for a small number of devices |
|
Automated licensing management, usage and asset management visibility |
Limited usage and asset management visibility |
|
No incremental operational costs to add devices |
Linear operational costs over time to add devices |
|
Flexible, easier to use, less overhead |
Significant administrative and manual overhead for moves, adds, and changes |
|
Out-of-compliance status is allowed initially and at various expiration states |
Out-of-compliance status impacts system functioning |
|
For more information, see Register the FMC with the Smart Software Manager On-Prem |
For more information, see Configure Specific License Reservation (SLR) |
How Licensing Works for the Management Center and Devices
The FMC registers with the Smart Software Manager, and then assigns licenses for each managed device. Devices do not register directly with the Smart Software Manager.
A physical FMC does not require a license for its own use. The FMCv does require a platform license.
Periodic Communication with the Smart Software Manager
In order to maintain your product license entitlement, your product must communicate periodically with the Smart Software Manager.
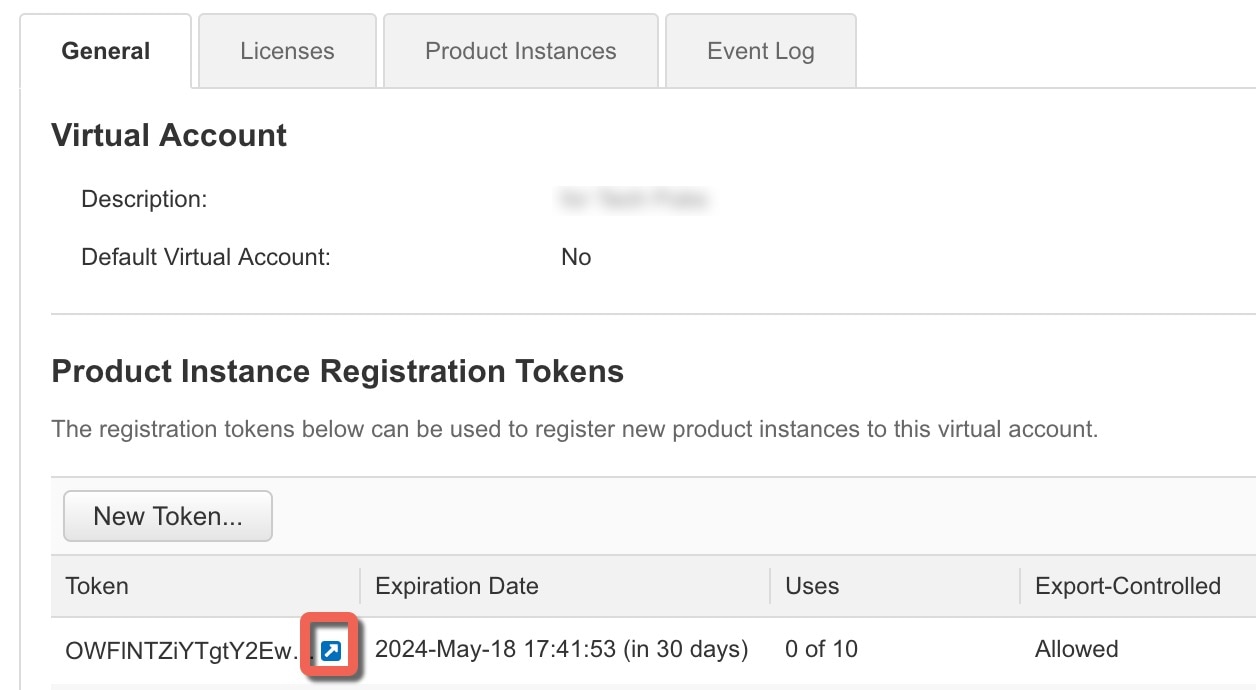
You use a Product Instance Registration Token to register the FMC with the Smart Software Manager. The Smart Software Manager issues an ID certificate for communication between the FMC and the Smart Software Manager. This certificate is valid for one year, although it will be renewed every six months. If an ID certificate expires (after a year with no communication), the FMC may be removed from your account.
The FMC communicates with the Smart Software Manager on a periodic basis. If you make changes in the Smart Software Manager, you can refresh the authorization on the FMC so the changes immediately take effect. You also can wait for the FMC to communicate as scheduled.
Your FMC must either have direct internet access to the Smart Software Manager, or use one of the options described in Licensing Options for Air-Gapped Deployments. In non-airgapped deployments, normal license communication occurs every 30 days, but with the grace period, your FMC will operate for up to 90 days without contacting the Smart Software Manager. Ensure that the FMC contacts the Smart Software Manager before 90 days have passed, or else the FMC will revert to an unregistered state.
Evaluation Mode
Before the FMC registers with the Smart Software Manager, it operates for 90 days in evaluation mode. You can assign feature licenses to managed devices, and they will remain in compliance for the duration of evaluation mode. When this period ends, the FMC becomes unregistered.
If you register the FMC with the Smart Software Manager, the evaluation mode ends. If you later deregister the FMC, you cannot resume evaluation mode, even if you did not initially use all 90 days.
For more information about the unregistered state, see Unregistered State.
 Note |
You cannot receive an evaluation license for Strong Encryption (3DES/AES); you must register with the Smart Software Manager to receive the export-compliance token that enables the Strong Encryption (3DES/AES) license. |
Out-of-Compliance State
The FMC can become out of compliance in the following situations:
-
Over-utilization—When the managed devices or the FMCv uses unavailable licenses.
-
License expiration—When a managed device term-based license expires.
In an out-of-compliance state, see the following effects:
-
FMCv platform license—Operation is not affected.
-
All managed device licenses—Operation is not affected.
After you resolve the licensing problem, the FMC will show that it is now in compliance after its regularly scheduled authorization
with the Smart Software Manager. To force an authorization, click
Re-Authorize on the System ( ) page.
) page.
Unregistered State
The FMC can become unregistered in the following situations:
-
Evaluation mode expiration—Evaluation mode expires after 90 days.
-
Manual deregistration of the FMC
-
Lack of communication with the Smart Software Manager—The FMC does not communicate with the Smart Software Manager for 1 year. Note: After 90 days, the FMC authorization expires, but it can successfully resume communication within one year to automatically re-authorize. After a year, the ID certificate expires, and the FMC is removed from your account so you will have to manually re-register the FMC.
In an unregistered state, the FMC cannot deploy any configuration changes to devices for features that require licenses.
End-User License Agreement
The Cisco end-user license agreement (EULA) and any applicable supplemental agreement (SEULA) that governs your use of this product are available from http://www.cisco.com/go/softwareterms.
License Types and Restrictions
This section describes the types of licenses available.
|
License You Assign |
Subscription You Purchase |
Duration |
Granted Capabilities |
||
|---|---|---|---|---|---|
|
Base |
Based on license type |
Perpetual or Subscription
|
Except for Specific License Reservation and the Secure Firewall 3100, Base perpetual licenses are automatically assigned with all FTDs. User and application control Switching and routing NAT For details, see Base Licenses. |
||
|
Threat |
|
Subscription |
Intrusion detection and prevention File control Security Intelligence filtering For details, see Threat Licenses |
||
|
Malware |
|
Subscription |
Malware defense Secure Malware Analytics File storage For details, see Malware Licenses and License Requirements for File and Malware Policies in the Firepower Management Center Device Configuration Guide. |
||
|
URL Filtering |
|
Subscription |
Category and reputation-based URL filtering For details, see URL Filtering Licenses. |
||
|
FMCv |
Based on license type |
|
The platform license determines the number of devices the FMCv can manage. For details, see FMCv Licenses. |
||
|
Export-Controlled Features |
No subscription required |
Perpetual |
Features that are subject to national security, foreign policy, and anti-terrorism laws and regulations; see Licensing for Export-Controlled Functionality. |
||
|
Remote Access VPN:
|
Based on license type |
Subscription or perpetual |
Remote access VPN configuration. Your account must allow export-controlled functionality to configure remote access VPN. You select whether you meet export requirements when you register the device. The FTD can use any valid AnyConnect Client license. The available features do not differ based on license type. For more information, see AnyConnect Client Licenses and VPN Licensing in the Firepower Management Center Device Configuration Guide. |
 Note |
Subscription licenses are term-based licenses. |
FMCv Licenses
The FMCv requires a platform license that correlates with the number of devices it can manage.
The FMCv supports Smart Licensing.
In regular Smart Licensing, these licenses are perpetual.
In Specific License Reservation (SLR), these licenses are subscription-based.
 Note |
For the add-on license requirements of your new devices on FMCv, it is recommended to migrate to a higher FMCv model that supports additional devices. |
Base Licenses
The Base license allows you to:
-
Configure your devices to perform switching and routing (including DHCP relay and NAT)
-
Configure devices as a high availability pair
-
Configure clustering
-
Implement user and application control by adding user and application conditions to access control rules
-
Update the Vulnerability database (VDB) and geolocation database (GeoDB).
-
Download intrusion rules such as SRU/LSP. However, you cannot deploy access control policy or rules that have intrusion policy to the device unless Threat license is enabled.
Secure Firewall 3100
You obtain a Base license when you purchase the Secure Firewall 3100.
Other Models
Except in deployments using Specific License Reservation, a Base license is automatically added to your account when you register a device to the FMC. For Specific License Reservation, you need to add the Base license to your account.
Malware Licenses
A Malware license lets you perform AMP for Networks and Secure Malware Analytics. With this feature, you can use devices to detect and block malware in files transmitted over your network. To support this feature license, you can purchase the Malware (AMP) service subscription as a stand-alone subscription or in combination with Threat (TM) or Threat and URL Filtering (TMC) subscriptions. Threat license is a prerequisite for a Malware license.
 Note |
Managed devices with Malware licenses enabled periodically attempt to connect to the Secure Malware Analytics Cloud even if you have not configured dynamic analysis. Because of this, the device’s Interface Traffic dashboard widget shows transmitted traffic; this is expected behavior. |
You configure AMP for Networks as part of a file policy, which you then associate with one or more access control rules. File policies can detect your users uploading or downloading files of specific types over specific application protocols. AMP for Networks allows you to use local malware analysis and file preclassification to inspect a restricted set of those file types for malware. You can also download and submit specific file types to the Secure Malware Analytics Cloud for dynamic and Spero analysis to determine whether they contain malware. For these files, you can view the network file trajectory, which details the path the file has taken through your network. The Malware license also allows you to add specific files to a file list and enable the file list within a file policy, allowing those files to be automatically allowed or blocked on detection.
Note that a Malware license is required only if you deploy AMP for Networks and Secure Malware Analytics. Without a Malware license, the FMC can receive AMP for Endpoints malware events and indications of compromise (IOC) from the Secure Malware Analytics Cloud.
See also important information at License Requirements for File and Malware Policies in the Firepower Management Center Device Configuration Guide.
When you disable this license:
-
The system stops querying the Secure Malware Analytics Cloud, and also stops acknowledging retrospective events sent from the Secure Malware Analytics Cloud.
-
You cannot re-deploy existing access control policies if they include AMP for Networks configurations.
-
For a very brief time after a Malware license is disabled, the system can use existing cached file dispositions. After the time window expires, the system assigns a disposition of
Unavailableto those files.
If the license expires, your entitlement for the above capabilities ceases and the FMC moves to the out-of-compliance state.
Threat Licenses
A Threat license allows you to perform intrusion detection and prevention, file control, and Security Intelligence filtering:
-
Intrusion detection and prevention allows you to analyze network traffic for intrusions and exploits and, optionally, drop offending packets.
-
File control allows you to detect and, optionally, block users from uploading (sending) or downloading (receiving) files of specific types over specific application protocols. AMP for Networks, which requires a Malware license, allows you to inspect and block a restricted set of those file types based on their dispositions.
-
Security Intelligence filtering allows you to block —deny traffic to and from—specific IP addresses, URLs, and DNS domain names, before the traffic is subjected to analysis by access control rules. Dynamic feeds allow you to immediately block connections based on the latest intelligence. Optionally, you can use a “monitor-only” setting for Security Intelligence filtering.
You can purchase a Threat license as a stand-alone subscription (T) or in combination with URL Filtering (TC), Malware (TM), or both (TMC).
When you disable this license:
-
The FMC stops acknowledging intrusion and file events from the affected devices. As a consequence, correlation rules that use those events as a trigger criteria stop firing.
-
The FMC does not contact the internet for either Cisco-provided or third-party Security Intelligence information.
-
You cannot re-deploy existing intrusion policies until you re-enable Threat.
If the license expires, your entitlement for the above capabilities ceases and the FMC moves to the out-of-compliance state.
URL Filtering Licenses
The URL Filtering license allows you to write access control rules that determine the traffic that can traverse your network based on URLs requested by monitored hosts, correlated with information about those URLs. To support this feature license, you can purchase the URL Filtering service subscription as a stand-alone subscription or in combination with Threat (TC) or Threat and Malware (TMC) subscriptions. Threat license is a prerequisite for this license.
 Tip |
Without a URL Filtering license, you can specify individual URLs or groups of URLs to allow or block. This option gives you granular, custom control over web traffic, but does not allow you to use URL category and reputation data to filter network traffic. |
Although you can add category and reputation-based URL conditions to access control rules without a URL Filtering license, the FMC will not download URL information. You cannot deploy the access control policy until you first add a URL Filtering license to the FMC, then enable it on the devices targeted by the policy.
When you disable this license:
-
You may lose access to URL filtering.
-
Access control rules with URL conditions immediately stop filtering URLs.
-
Your FMC can no longer download updates to URL data.
-
You cannot re-deploy existing access control policies if they include rules with category and reputation-based URL conditions.
If the license expires, your entitlement for the above capabilities ceases and the FMC moves to the out-of-compliance state.
AnyConnect Client Licenses
You can configure remote access VPN using the AnyConnect Client and standards-based IPSec/IKEv2.
To enable remote access VPN, you must purchase and enable one of the following licenses: AnyConnect Plus, AnyConnect Apex, or AnyConnect VPN Only. You can select AnyConnect Plus and AnyConnect Apex if you have both licenses and you want to use them both. The AnyConnect VPN Onlylicense cannot be used with Apex or Plus. The AnyConnect Client license must be shared with the Smart Account. For more instructions, see http://www.cisco.com/c/dam/en/us/products/collateral/security/anyconnect-og.pdf.
You cannot deploy the remote access VPN configuration to the device if the specified device does not have the entitlement for a minimum of one of the specified AnyConnect Client license types. If the registered license moves out of compliance or entitlements expire, the system displays licensing alerts and health events.
While using remote access VPN, your Smart Account must have the export controlled features (strong encryption) enabled. The FTD requires strong encryption (which is higher than DES) for successfully establishing remote access VPN connections with AnyConnect Clients.
You cannot deploy remote access VPN if the following are true:
-
Smart Licensing on the FMC is running in evaluation mode.
-
Your Smart Account is not configured to use export-controlled features (strong encryption).
Licensing for Export-Controlled Functionality
Features that require export-controlled functionality
Certain software features are subject to national security, foreign policy, and anti-terrorism laws and regulations. These export-controlled features include:
-
Security certifications compliance
-
Remote access VPN
-
Site-to-site VPN with strong encryption
-
SSH platform policy with strong encryption
-
SSL policy with strong encryption
-
Functionality such as SNMPv3 with strong encryption
How to determine whether export-controlled functionality is currently enabled for your system
To determine whether export-controlled functionality is currently enabled for your system: Go to System > Licenses > Smart Licenses and see if Export-Controlled Features displays Enabled.
About enabling export-controlled functionality
If Export-Controlled Features shows Disabled and you want to use features that require strong encryption, there are two ways to enable strong cryptographic features. Your organization may be eligible for one or the other (or neither), but not both.
-
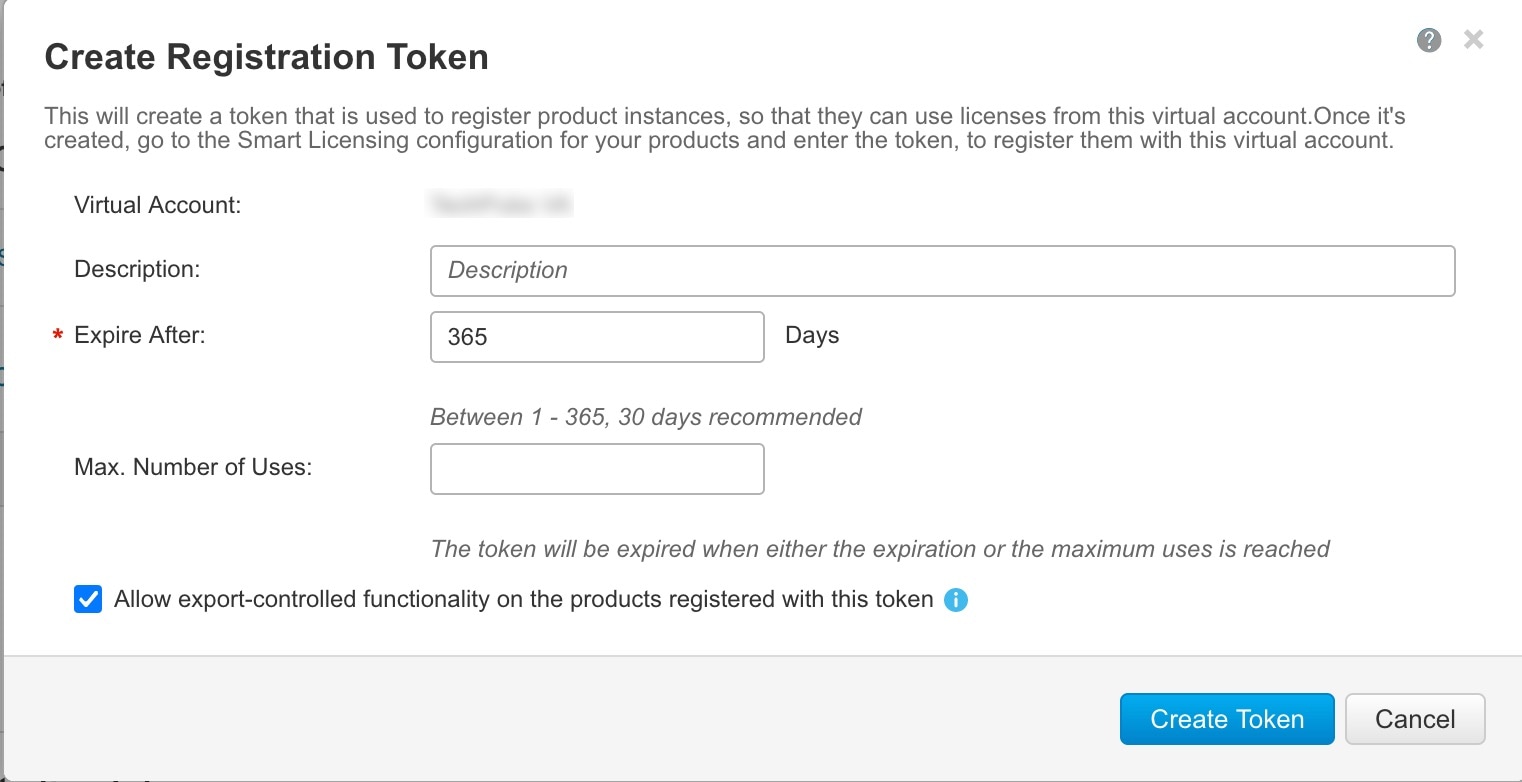
If there is no option to enable export-controlled functionality when you generate a new Product Instance Registration Token in the Smart Software Manager, contact your account representative.
When approved by Cisco, you can manually add a strong encryption license to your account so you can use export-controlled features. For more information, see Enable the Export Control Feature for Accounts Without Global Permission
-
If the option “Allow export-controlled functionality on the products registered with this token” appears when you generate a new Product Instance Registration Token in the Smart Software Manager, make sure you check it before generating the token.
If you did not enable export-controlled functionality for the Product Instance Registration Token that you used to register the FMC, then you must deregister and then re-register the FMC using a new Product Instance Registration Token with export-controlled functionality enabled.
If you registered devices to the FMC in evaluation mode or before you enabled strong encryption on the FMC, reboot each managed device to make strong encryption available. In a high availability deployment, the active and standby devices must be rebooted together to avoid an Active-Active condition.
The entitlement is perpetual and does not require a subscription.
More Information
For general information about export controls, see https://www.cisco.com/c/en/us/about/legal/global-export-trade.html.
FTDv Licenses
This section describes the performance-tiered license entitlements available for the FTDv.
Any FTDv license can be used on any supported FTDv vCPU/memory configuration. This allows FTDv customers to run on a wide variety of VM resource footprints. This also increases the number of supported AWS and Azure instances types. When configuring the FTDv VM, the maximum supported number of cores (vCPUs) is 16 ; and the maximum supported memory is 32 GB RAM .
Performance Tiers for FTDv Smart Licensing
Session limits for RA VPNs are determined by the installed FTDv platform entitlement tier, and enforced via a rate limiter. The following table summarizes the session limits based on the entitlement tier and rate limiter.
|
Performance Tier |
Device Specifications (Core/RAM) |
Rate Limit |
RA VPN Session Limit |
|---|---|---|---|
|
FTDv5, 100Mbps |
4 core/8 GB |
100Mbps |
50 |
|
FTDv10, 1Gbps |
4 core/8 GB |
1Gbps |
250 |
|
FTDv20, 3Gbps |
4 core/8 GB |
3Gbps |
250 |
|
FTDv30, 5Gbps |
8 core/16 GB |
5Gbps |
250 |
|
FTDv50, 10Gbps |
12 core/24 GB |
10Gbps |
750 |
|
FTDv100, 16Gbps |
16 core/32 GB |
16Gbps |
10,000 |
FTDv Performance Tier Licensing Guidelines and Limitations
Please keep the following guidelines and limitations in mind when licensing your FTDv device.
-
The FTDv supports performance-tiered licensing that provides different throughput levels and VPN connection limits based on deployment requirements.
-
Any FTDv license can be used on any supported FTDv core/memory configuration. This allows the FTDv customers to run on a wide variety of VM resource footprints.
-
You can select a performance tier when you deploy the FTDv, whether your device is in evaluation mode or is already registered with Cisco Smart Software Manager.

Note
Make sure your Smart Licensing account contains the available licenses you need. It’s important to choose the tier that matches the license you have in your account. If you are upgrading your FTDv to Version 7.0, you can choose FTDv - Variable to maintain your current license compliance. Your FTDv continues to perform with session limits based on your device capabilities (number of cores/RAM).
-
The default performance tier is FTDv50 when deploying a new FTDv device, or when provisioning the FTDv using the REST API.
-
Base licenses are subscription-based and mapped to performance tiers. Your virtual account needs to have the Base license entitlements for the FTDv devices, as well as for Threat, Malware, and URL Filtering licenses.
-
Each HA peer consumes one entitlement, and the entitlements on each HA peer must match, including Base license.
-
A change in performance tier for an HA pair should be applied to the primary peer.
-
Universal PLR licensing is applied to each device in an HA pair separately. The secondary device will not automatically mirror the performance tier of the primary device. It must be updated manually.
License PIDs
FMCv PIDs
-
VMware:
-
SF-FMC-VMW-2-K9—2 devices
-
SF-FMC-VMW-10-K9—10 devices
-
SF-FMC-VMW-K9—25 devices
-
SF-FMC-VMW-300-K9—300 devices
-
-
KVM:
-
SF-FMC-KVM-2-K9—2 devices
-
SF-FMC-KVM-10-K9—10 devices
-
SF-FMC-KVM-K9—25 devices
-
-
PAK-based VMware:
-
FS-VMW-2-SW-K9—2 devices
-
FS-VMW-10-SW-K9—10 devices
-
FS-VMW-SW-K9—25 devices
-
FTDv PIDs
When you order FTDV-SEC-SUB, you must choose a Base license and optional feature licenses (12 month term):
-
Base license:
-
FTD-V-5S-BSE-K9
-
FTD-V-10S-BSE-K9
-
FTD-V-20S-BSE-K9
-
FTD-V-30S-BSE-K9
-
FTD-V-50S-BSE-K9
-
FTD-V-100S-BSE-K9
-
-
Threat, Malware, and URL license combination:
-
FTD-V-5S-TMC
-
FTD-V-10S-TMC
-
FTD-V-20S-TMC
-
FTD-V-30S-TMC
-
FTD-V-50S-TMC
-
FTD-V-100S-TMC
-
-
RA VPN—See the Cisco Secure Client Ordering Guide.
Firepower 1010 PIDs
-
Threat, Malware, and URL license combination:
-
L-FPR1010T-TMC=
When you add the above PID to your order, you can then choose a term-based subscription corresponding with one of the following PIDs:
-
L-FPR1010T-TMC-1Y
-
L-FPR1010T-TMC-3Y
-
L-FPR1010T-TMC-5Y
-
-
RA VPN—See the Cisco Secure Client Ordering Guide.
Firepower 1100 PIDs
-
Threat, Malware, and URL license combination:
-
L-FPR1120T-TMC=
-
L-FPR1140T-TMC=
-
L-FPR1150T-TMC=
When you add one of the above PIDs to your order, you can then choose a term-based subscription corresponding with one of the following PIDs:
-
L-FPR1120T-TMC-1Y
-
L-FPR1120T-TMC-3Y
-
L-FPR1120T-TMC-5Y
-
L-FPR1140T-TMC-1Y
-
L-FPR1140T-TMC-3Y
-
L-FPR1140T-TMC-5Y
-
L-FPR1150T-TMC-1Y
-
L-FPR1150T-TMC-3Y
-
L-FPR1150T-TMC-5Y
-
-
RA VPN—See the Cisco Secure Client Ordering Guide.
Firepower 2100 PIDs
-
Threat, Malware, and URL license combination:
-
L-FPR2110T-TMC=
-
L-FPR2120T-TMC=
-
L-FPR2130T-TMC=
-
L-FPR2140T-TMC=
When you add one of the above PIDs to your order, you can then choose a term-based subscription corresponding with one of the following PIDs:
-
L-FPR2110T-TMC-1Y
-
L-FPR2110T-TMC-3Y
-
L-FPR2110T-TMC-5Y
-
L-FPR2120T-TMC-1Y
-
L-FPR2120T-TMC-3Y
-
L-FPR2120T-TMC-5Y
-
L-FPR2130T-TMC-1Y
-
L-FPR2130T-TMC-3Y
-
L-FPR2130T-TMC-5Y
-
L-FPR2140T-TMC-1Y
-
L-FPR2140T-TMC-3Y
-
L-FPR2140T-TMC-5Y
-
-
RA VPN—See the Cisco Secure Client Ordering Guide.
Secure Firewall 3100 PIDs
-
Base license:
-
L-FPR3110-BSE=
-
L-FPR3120-BSE=
-
L-FPR3130-BSE=
-
L-FPR3140-BSE=
-
-
Threat, Malware, and URL license combination:
-
L-FPR3110T-TMC=
-
L-FPR3120T-TMC=
-
L-FPR3130T-TMC=
-
L-FPR3140T-TMC=
When you add one of the above PIDs to your order, you can then choose a term-based subscription corresponding with one of the following PIDs:
-
L-FPR3110T-TMC-1Y
-
L-FPR3110T-TMC-3Y
-
L-FPR3110T-TMC-5Y
-
L-FPR3120T-TMC-1Y
-
L-FPR3120T-TMC-3Y
-
L-FPR3120T-TMC-5Y
-
L-FPR3130T-TMC-1Y
-
L-FPR3130T-TMC-3Y
-
L-FPR3130T-TMC-5Y
-
L-FPR3140T-TMC-1Y
-
L-FPR3140T-TMC-3Y
-
L-FPR3140T-TMC-5Y
-
-
RA VPN—See the Cisco Secure Client Ordering Guide.
Firepower 4100 PIDs
-
Threat, Malware, and URL license combination:
-
L-FPR4110T-TMC=
-
L-FPR4112T-TMC=
-
L-FPR4115T-TMC=
-
L-FPR4120T-TMC=
-
L-FPR4125T-TMC=
-
L-FPR4140T-TMC=
-
L-FPR4145T-TMC=
-
L-FPR4150T-TMC=
When you add one of the above PIDs to your order, you can then choose a term-based subscription corresponding with one of the following PIDs:
-
L-FPR4110T-TMC-1Y
-
L-FPR4110T-TMC-3Y
-
L-FPR4110T-TMC-5Y
-
L-FPR4112T-TMC-1Y
-
L-FPR4112T-TMC-3Y
-
L-FPR4112T-TMC-5Y
-
L-FPR4115T-TMC-1Y
-
L-FPR4115T-TMC-3Y
-
L-FPR4115T-TMC-5Y
-
L-FPR4120T-TMC-1Y
-
L-FPR4120T-TMC-3Y
-
L-FPR4120T-TMC-5Y
-
L-FPR4125T-TMC-1Y
-
L-FPR4125T-TMC-3Y
-
L-FPR4125T-TMC-5Y
-
L-FPR4140T-TMC-1Y
-
L-FPR4140T-TMC-3Y
-
L-FPR4140T-TMC-5Y
-
L-FPR4145T-TMC-1Y
-
L-FPR4145T-TMC-3Y
-
L-FPR4145T-TMC-5Y
-
L-FPR4150T-TMC-1Y
-
L-FPR4150T-TMC-3Y
-
L-FPR4150T-TMC-5Y
-
-
RA VPN—See the Cisco Secure Client Ordering Guide.
Firepower 9300 PIDs
-
Threat, Malware, and URL license combination:
-
L-FPR9K-24T-TMC=
-
L-FPR9K-36T-TMC=
-
L-FPR9K-40T-TMC=
-
L-FPR9K-44T-TMC=
-
L-FPR9K-48T-TMC=
-
L-FPR9K-56T-TMC=
When you add one of the above PIDs to your order, you can then choose a term-based subscription corresponding with one of the following PIDs:
-
L-FPR9K-24T-TMC-1Y
-
L-FPR9K-24T-TMC-3Y
-
L-FPR9K-24T-TMC-5Y
-
L-FPR9K-36T-TMC-1Y
-
L-FPR9K-36T-TMC-3Y
-
L-FPR9K-36T-TMC-5Y
-
L-FPR9K-40T-TMC-1Y
-
L-FPR9K-40T-TMC-3Y
-
L-FPR9K-40T-TMC-5Y
-
L-FPR9K-44T-TMC-1Y
-
L-FPR9K-44T-TMC-3Y
-
L-FPR9K-44T-TMC-5Y
-
L-FPR9K-48T-TMC-1Y
-
L-FPR9K-48T-TMC-3Y
-
L-FPR9K-48T-TMC-5Y
-
L-FPR9K-56T-TMC-1Y
-
L-FPR9K-56T-TMC-3Y
-
L-FPR9K-56T-TMC-5Y
-
-
RA VPN—See the Cisco AnyConnect Ordering Guide.
ISA 3000 PIDs
-
Threat, Malware, and URL license combination:
-
L-ISA3000T-TMC=
When you add the above PID to your order, you can then choose a term-based subscription corresponding with one of the following PIDs:
-
L-ISA3000T-TMC-1Y
-
L-ISA3000T-TMC-3Y
-
L-ISA3000T-TMC-5Y
-
-
RA VPN—See the Cisco AnyConnect Ordering Guide.

 )
) )
) )
) )
) )
)

 Feedback
Feedback