Secure Firewall Threat Intelligence Director Overview
The Secure Firewall threat intelligence director operationalizes threat intelligence data, helping you aggregate intelligence data, configure defensive actions, and analyze threats in your environment. This feature is intended to supplement other Firepower functionality, offering an additional line of defense against threats.
When configured on your hosting platform, threat intelligence director ingests data from threat intelligence sources and publishes the data to all configured managed devices (elements.) For more information about the hosting platforms and elements supported in this release, see Platform, Element, and License Requirements.
Sources contain indicators, which contain observables. An indicator conveys all of the characteristics associated with a threat, and individual observables represent individual characteristics (e.g. a SHA-256 value) associated with the threat. Simple indicators contain a single observable, and complex indicators contain two or more observables.
Observables and the AND/OR operators between them form an indicator's pattern, as illustrated in the following examples.
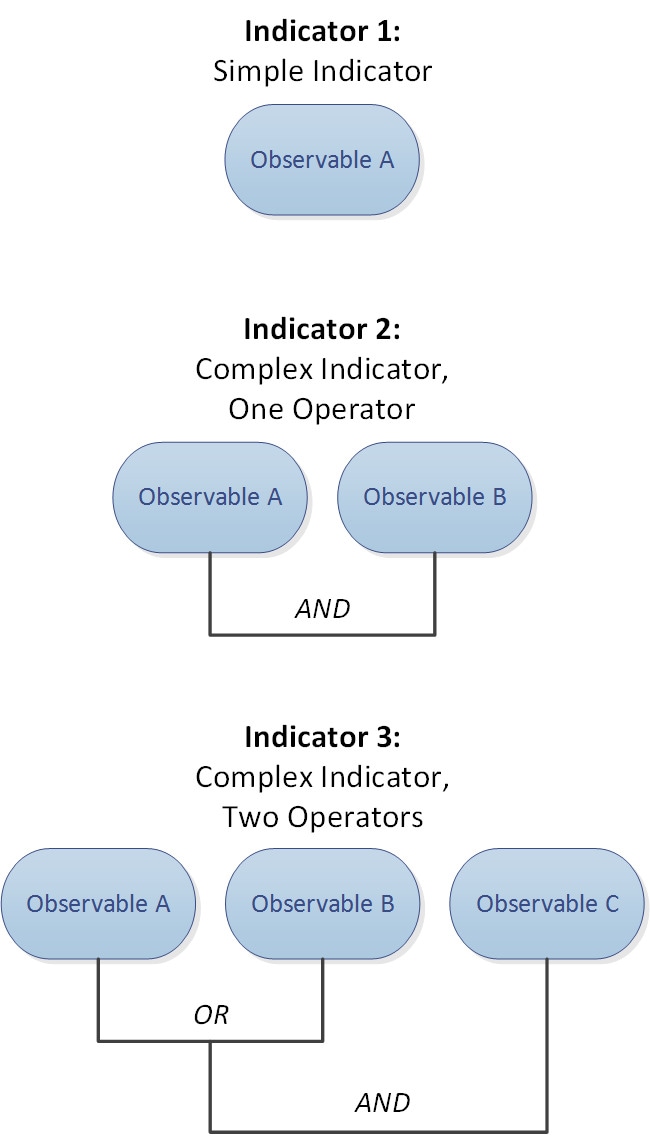
After the observables are published to the elements, the elements monitor traffic and report observations to the management center when the system identifies observables in traffic.
The management center collects observations from all elements, evaluates the observations against threat intelligence director indicators, and generates or updates incidents associated with the observable's parent indicator(s).
An incident is fully realized when an indicator's pattern is fulfilled. An incident is partially realized if traffic matches one or more observables in the indicator but not the entire pattern. For more information, see Observation and Incident Generation.
The following diagram shows data flow in a sample system configuration.
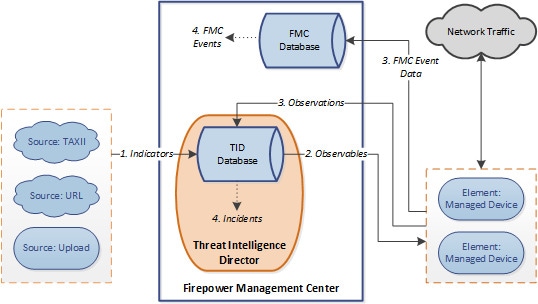
When a threat intelligence director incident is fully or partially realized, the system takes the configured action (monitor, block, partially block, or no action). For details, see Factors That Affect the Action Taken.
Threat Intelligence Director and Security Intelligence
As part of your access control policy, Security Intelligence uses reputation intelligence to quickly block connections to or from IP addresses, URLs, and domains. Security Intelligence uniquely provides access to industry-leading threat intelligence from Talos Intelligence Group. For more information on Security Intelligence, see About Security Intelligence.
Threat Intelligence Director enhances the system's ability to block connections based on security intelligence from third-party sources as follows:
-
Threat Intelligence Director supports additional traffic filtering criteria—Security Intelligence allows you to filter traffic based on IP address, URL, and (if DNS policy is enabled) domain name. Threat Intelligence Director also supports filtering by these criteria and adds support for filtering on SHA-256 hash values.
-
Threat Intelligence Director supports additional intelligence ingestion methods—With both Security Intelligence and threat intelligence director, you can import threat intelligence into the system by either manually uploading flat files or configuring the system to retrieve flat files from a third-party host. Threat Intelligence Director provides increased flexibility in managing those flat files. In addition, threat intelligence director can retrieve and ingest intelligence provided in Structured Threat Information eXpression (STIX™) format.
-
Threat Intelligence Director provides granular control of filtering actions—With Security Intelligence, you can specify filtering criteria by network, URL, or DNS object. Security Intelligence objects, especially list and feeds, can contain multiple IP addresses, URLs, or DNS domain names, but you can only block or not block based on entire objects, not based on individual components of an object. With threat intelligence director, you can configure filtering actions for individual criteria (that is, simple indicators or individual observables).
-
Threat Intelligence Director configuration changes do not require redeployment—After you modify Security Intelligence settings in the access control policy, you must redeploy the changed configuration to managed devices. With threat intelligence director, after initial deployment of the access control policy to the managed devices, you can configure sources, indicators, and observables without redeploying, and the system automatically publishes new threat intelligence director data to the elements.
For information about what the system does when either Security Intelligence or threat intelligence director could handle a particular incident, see Threat Intelligence Director-Management Center Action Prioritization.
Performance Impact of Threat Intelligence Director
Secure Firewall Management Center
In some cases, you may notice the following:
-
The system may experience minor performance issues while ingesting particularly large STIX sources, and ingestion may take longer than expected to finish.
-
The system may take up to 15 minutes to publish new or modified threat intelligence director data down to elements.
Managed Device
There is no exceptional performance impact. Threat Intelligence Director impacts performance identically to the Secure Firewall Management Center Security Intelligence feature.

 )
) )
) )
) )
) )
) )
) )
) )
)


 Feedback
Feedback