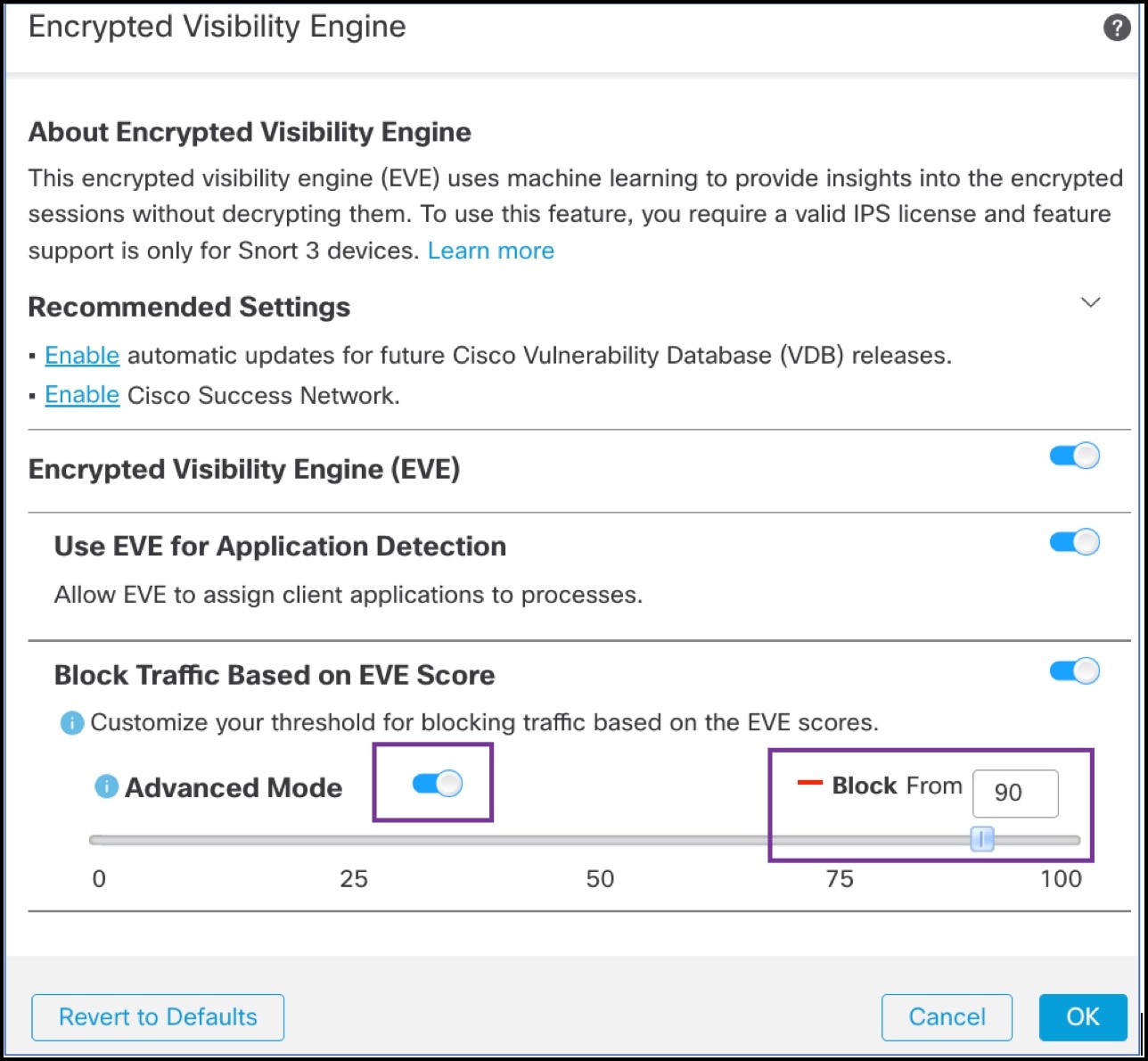
About Encrypted Visibility Engine
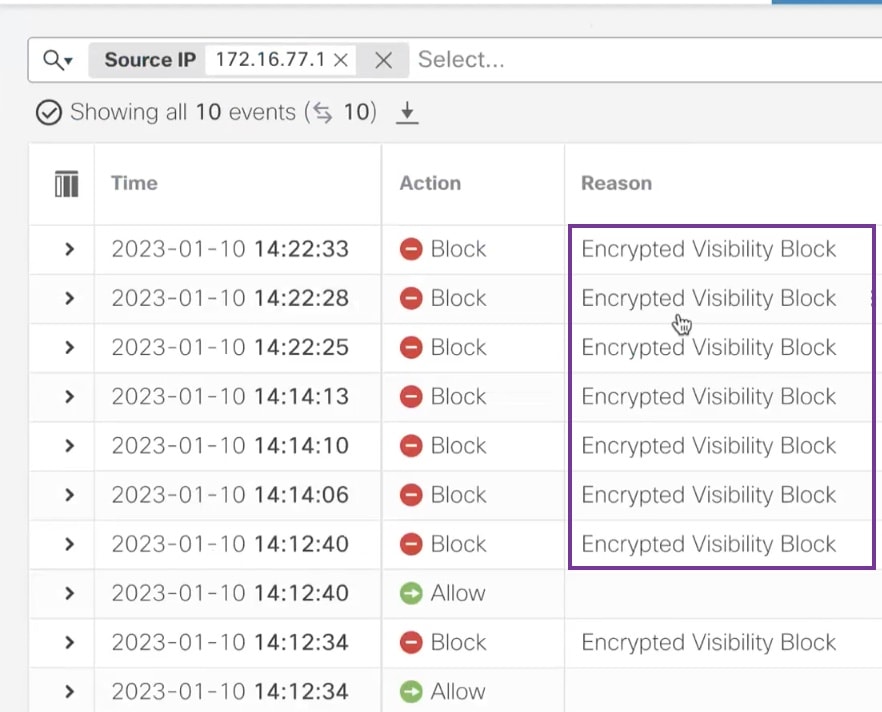
You can use the Encrypted Visibility Engine (EVE) to identify client applications and processes using Transport Layer Security (TLS) encryption. EVE provides more visibility into the encrypted sessions without decryption. Based on EVE’s findings, administrators can enforce policy actions on the traffic within their environments. You can also use the EVE to identify and stop malware.
 ) next to the access control policy you want to edit.
) next to the access control policy you want to edit.




 Feedback
Feedback