About MITRE ATT&CK Framework
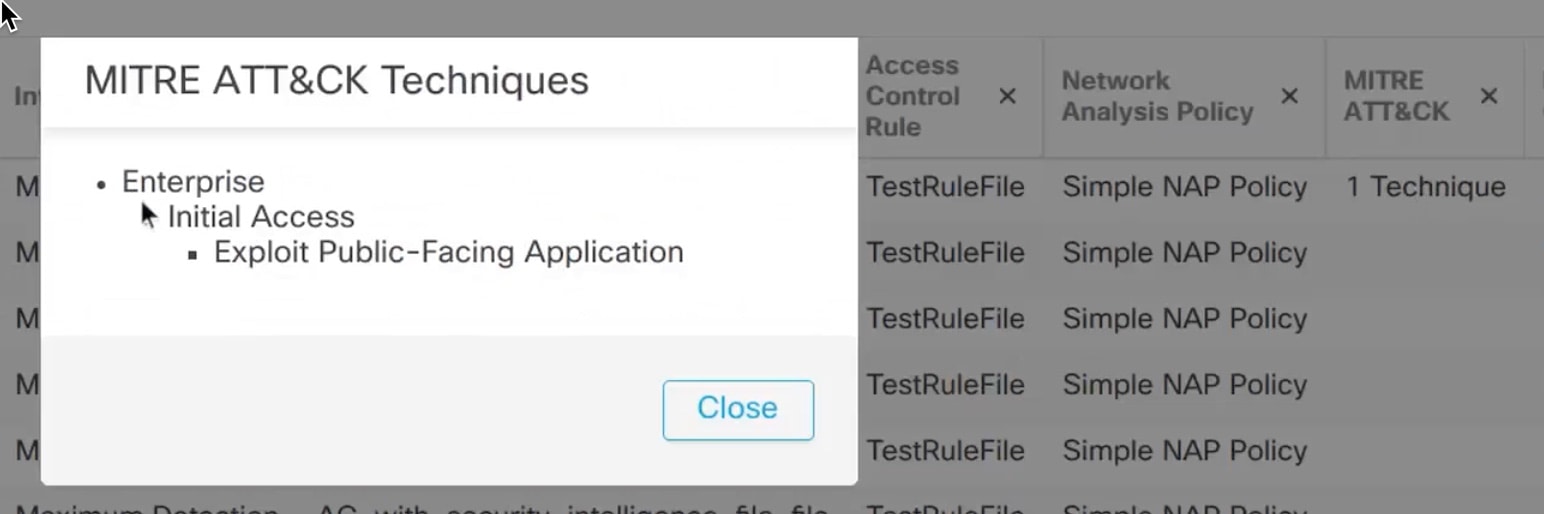
The MITRE ATT&CK Framework is a comprehensive knowledge base that outlines the tactics, techniques, and procedures (TTPs) used by threat actors to compromise systems. It organizes these TTPs into matrices for different operating systems and platforms, mapping each attack stage (tactics) to specific methods (techniques). Each technique includes information about execution, procedures, defenses, detections, and real-world examples.
 Note |
See https://attack.mitre.org for additional information about MITRE ATT&CK. |
The management center uses the MITRE ATT&CK Framework to enhance threat detection and response, incorporating the following capabilities:
-
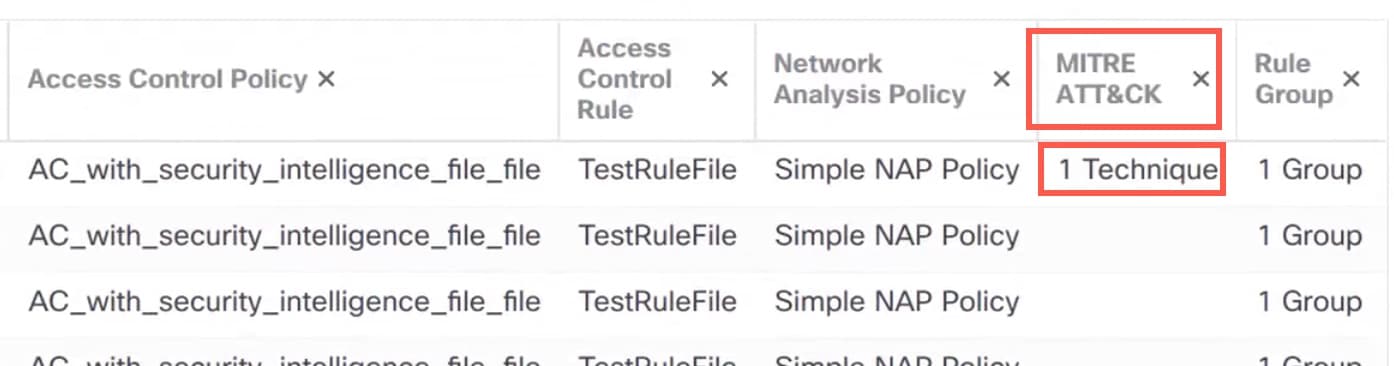
Intrusion events include TTPs, allowing administrators to manage traffic with greater granularity by grouping rules according to vulnerability type, target system, or threat category.
-
Select malware events use TTPs, enhancing the ability to detect and respond to threats.
-
Unified and Classic Event Viewers display tactics, techniques, attack lifecycle graphs, and contextual enrichments from the Talos taxonomy. These enrichments include MITRE tags and a hierarchical view of associated tactics, techniques, and sub-techniques. You can also filter events using MITRE identifiers.

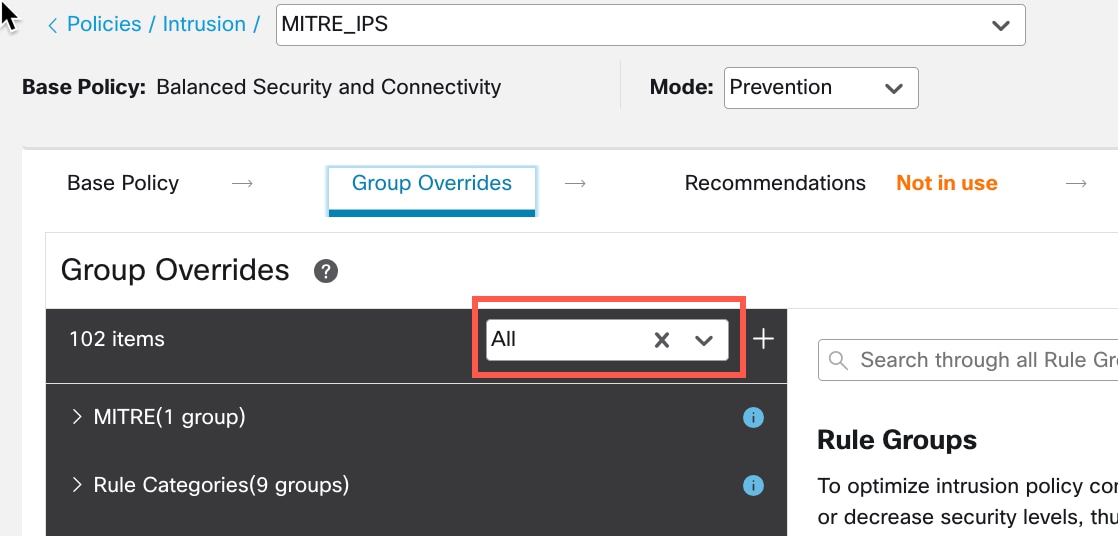
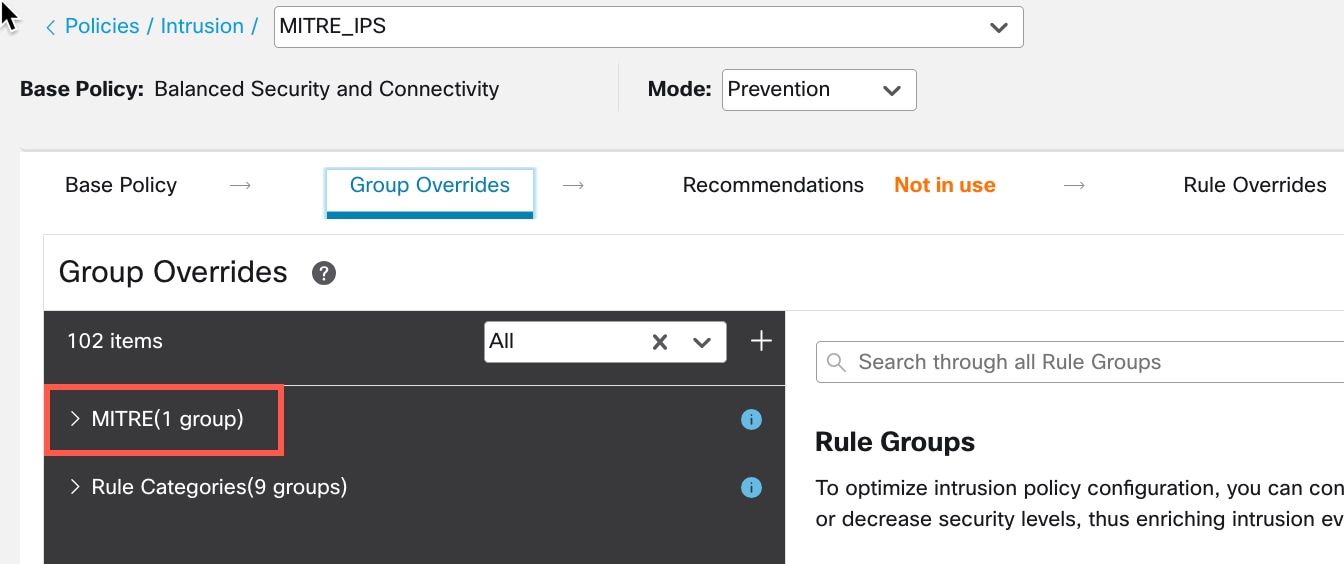
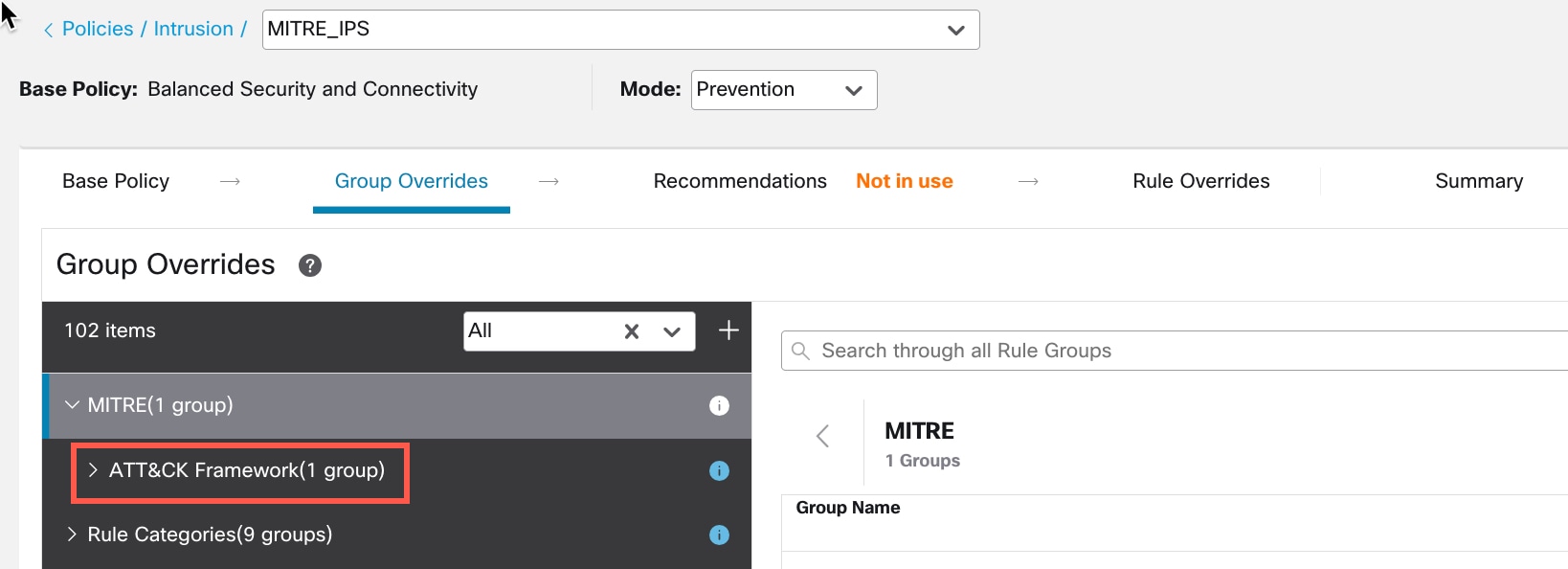

 ) icon next to the Security Level of the rule group to make bulk changes to the security level of all the associated rule groups under the
) icon next to the Security Level of the rule group to make bulk changes to the security level of all the associated rule groups under the 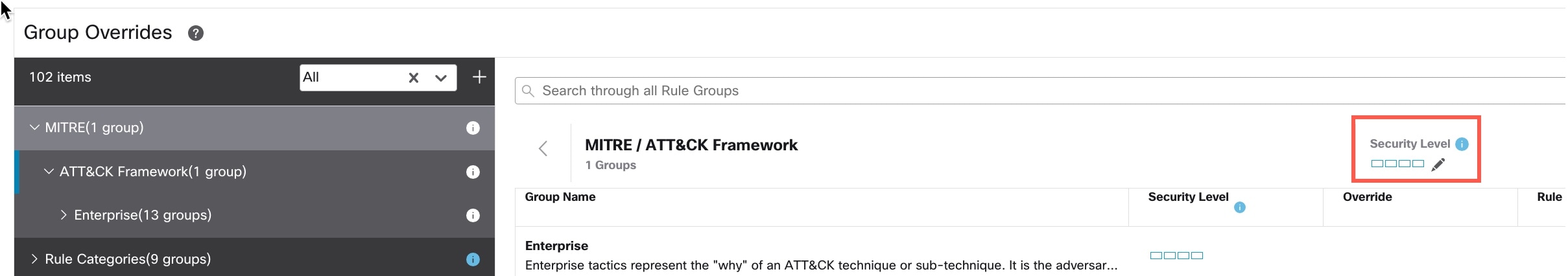







 Feedback
Feedback