The following is a sample of the summary that is displayed.
"id": "00505691-15DC-0ed3-0000-004294988561",
"name": "_Intrusion_Policy_1",
"type": "IntrusionPolicy",
"syncStatus": {
"source": {
"id": "bdce2d6a-1ebe-11ee-8e88-220032eb1fb5",
"type": "IntrusionPolicy"
},
"status": "WARN",
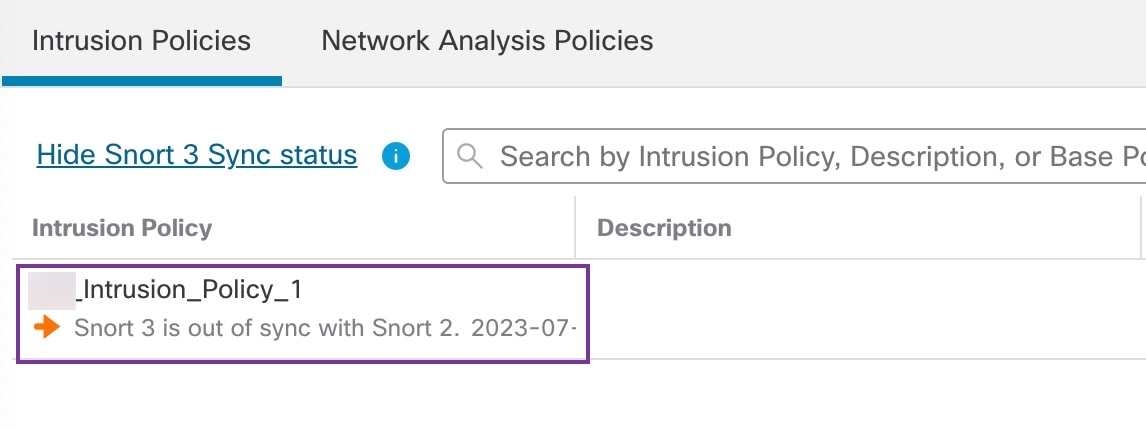
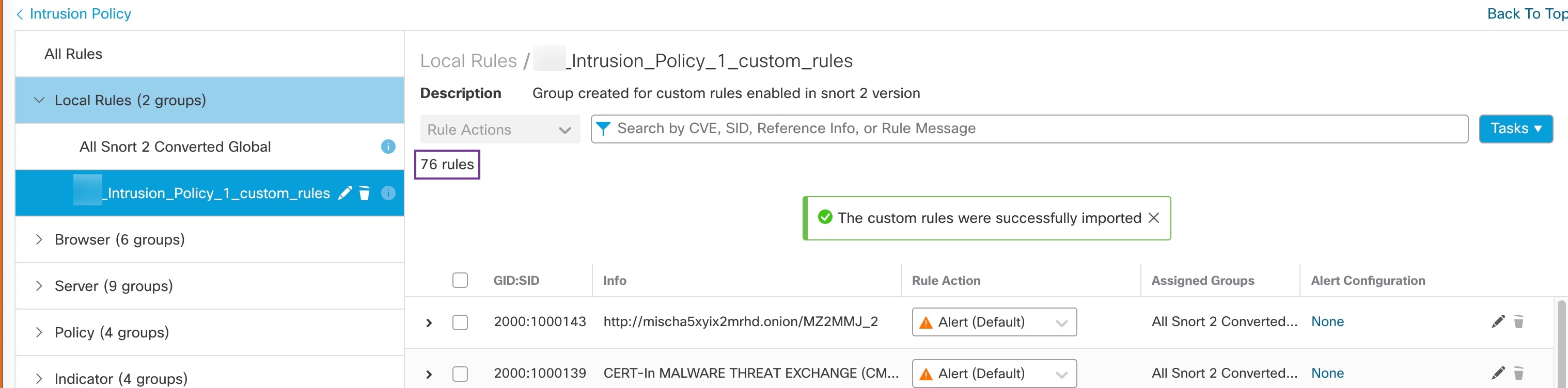
"description": "Migration is partially successful. Some of the rules are not copied to Snort3.",
"timestamp": 1690883954814,
"lastUser": {
"name": "admin"
},
"details": [
{
"type": "Summary",
"status": "INFO",
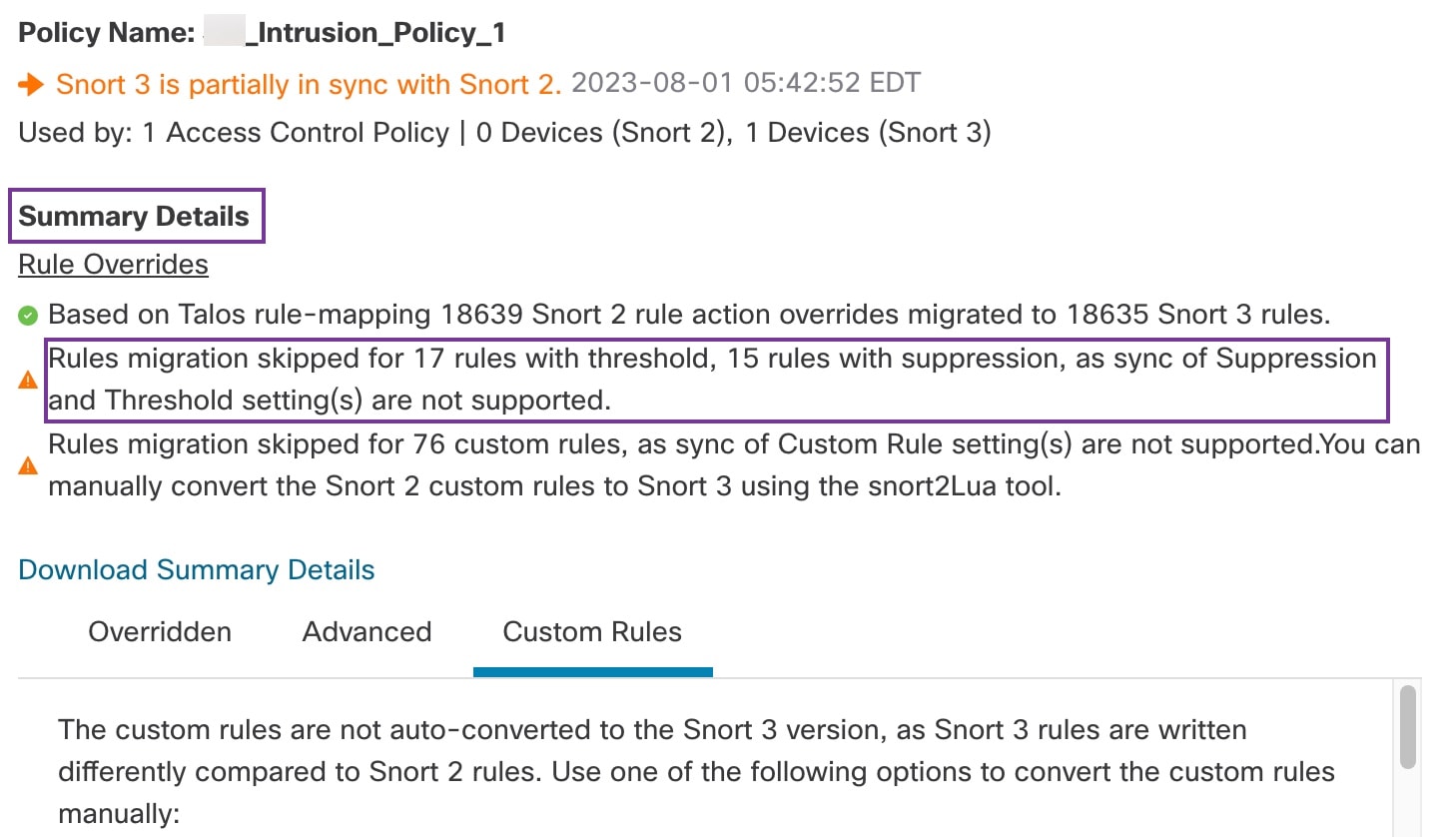
"description": "Based on Talos rule-mapping 18639 Snort 2 rule action overrides migrated to 18635 Snort 3 rules."
},
{
"id": "1:1000156=alert,1:1000114=alert,1:1000160=alert,1:1000135=alert,1:1000115=alert,1:1000118=alert,
1:1000092=alert,1:1000139=alert,1:1000123=alert,1:1000159=alert,1:1000149=disabled,1:1000167=alert,
1:1000133=alert,1:1000095=alert,1:1000143=alert,1:1000106=alert,1:1000153=alert,1:1000097=alert,1:1000141=alert,
1:1000148=alert,1:1000090=alert,1:1000119=alert,1:1000112=alert,1:1000138=alert,1:1000128=alert,1:1000132=alert,
1:1000134=alert,1:1000145=disabled,1:1000110=disabled,1:1000107=alert,1:1000163=alert,1:1000124=alert,1:1000125=alert,
1:1000094=alert,1:1000113=disabled,1:1000147=alert,1:1000161=alert,1:1000105=disabled,1:1000140=alert,1:1000111=alert,
1:1000102=alert,1:1000129=disabled,1:1000108=alert,1:1000144=disabled,1:1000088=alert,1:1000091=alert,1:1000131=alert,
1:1000157=alert,1:1000120=alert,1:1000126=alert,1:1000165=alert,1:1000146=alert,1:1000162=alert,1:1000116=alert,1:1000142=alert,
1:1000170=disabled,1:1000169=alert,1:1000104=alert,1:1000099=disabled,1:1000171=alert,1:1000093=alert,1:1000087=alert,1:1000100=alert,
1:1000137=alert,1:1000158=alert,1:1000103=alert,1:1000098=alert,1:1000127=disabled,1:1000130=alert,1:1000164=alert,1:1000089=alert,
1:1000109=alert,1:1000136=alert,1:1000117=alert,1:1000166=alert,1:1000168=alert",
"type": "PolicyInfo",
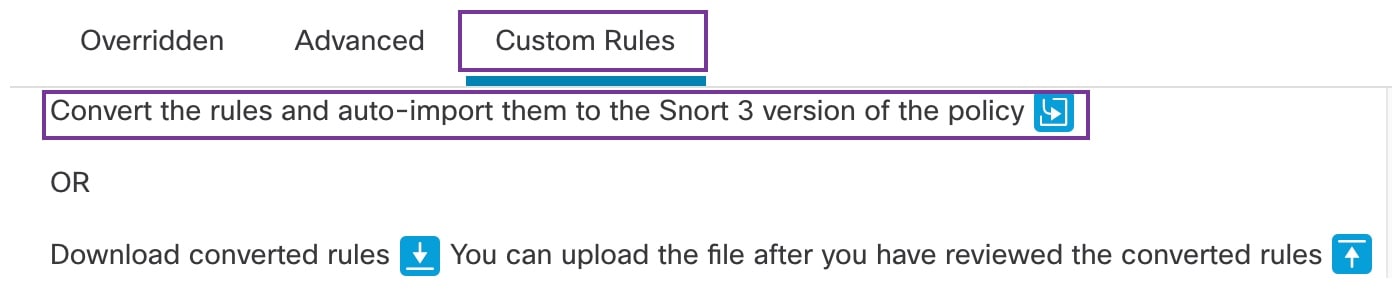
"description": "Corresponding Snort 2 policy overridden custom (local) rules."
},
{
"type": "AssignedDevices",
"status": "INFO",
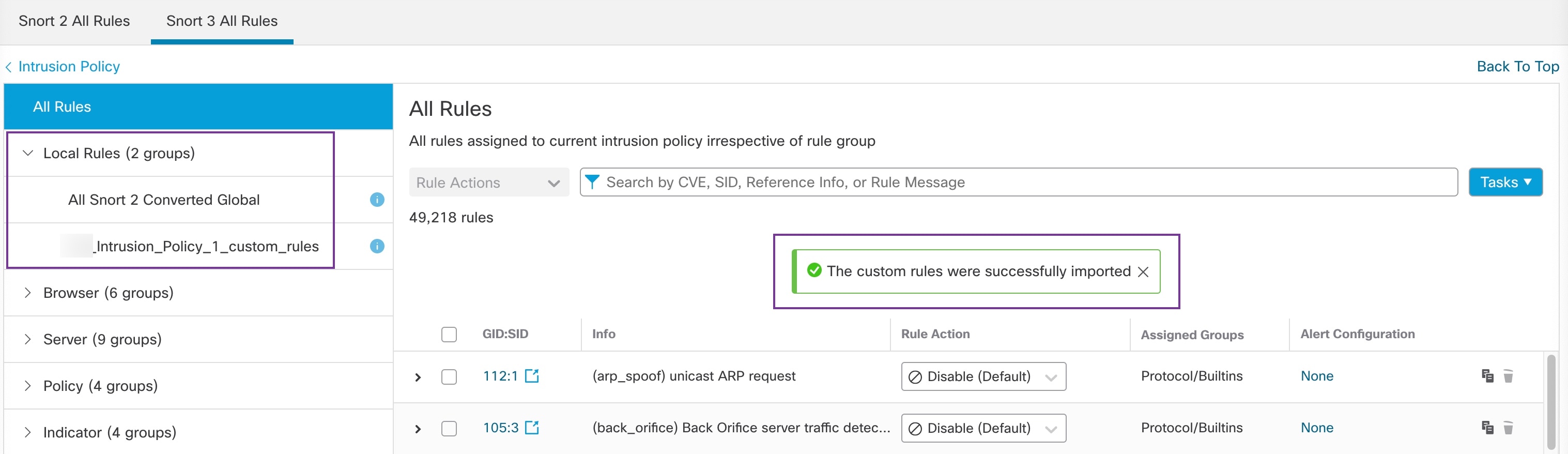
"description": "Snort3:0 , Snort2:0"
},
{
"id": "122:6",
"type": "Threshold",
"status": "ERROR",
"description": "PSNG_TCP_FILTERED_DECOY_PORTSCAN"
},
{
"id": "122:15",
"type": "Threshold",
"status": "ERROR",
"description": "PSNG_IP_PORTSWEEP_FILTERED"
},
{
"id": "122:1",
"type": "Threshold",
"status": "ERROR",
"description": "PSNG_TCP_PORTSCAN"
},








 )
) )
) Feedback
Feedback