Information About IPv6 Client Address Learning
Client Address Learning is configured on device to learn the IPv4 and IPv6 address of wireless client, and the client's transition state maintained by the device on association and timeout.
There are three ways for an IPv6 client to acquire IPv6 addresses:
-
Stateless Address Auto-Configuration (SLAAC)
-
Stateful DHCPv6
-
Static Configuration
In all of these methods, the IPv6 client always sends a neighbor solicitation Duplicate Address Detection (DAD) request to ensure that there is no duplicate IP address on the network. The device snoops on the Neighbor Discovery Protocol (NDP) and DHCPv6 packets of the client to learn about its client IP addresses.
Address Assignment Using SLAAC
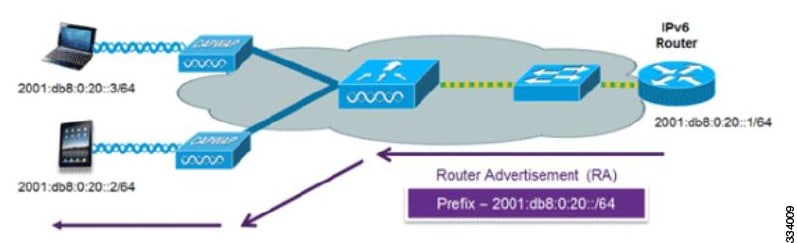
The most common method for IPv6 client address assignment is SLAAC, which provides simple plug-and-play connectivity, where clients self-assign an address based on the IPv6 prefix.
SLAAC is configured as follows:
-
A host sends a Router Solicitation message.
-
The host waits for a Router Advertisement message.
-
The host take the first 64 bits of the IPv6 prefix from the Router Advertisement message and combines it with the 64 bit EUI-64 address (in the case of Ethernet, this is created from the MAC address) to create a global unicast message. The host also uses the source IP address, in the IP header, of the Router Advertisement message, as its default gateway.
-
Duplicate Address Detection is performed by the IPv6 clients to ensure that random addresses that are picked do not collide with other clients.
 Note |
The last 64 bits of the IPv6 address can be learned by using one of the following algorithms:
|
The following Cisco IOS configuration commands from a Cisco-capable IPv6 router are used to enable SLAAC addressing and router advertisements:
ipv6 unicast-routing
interface Vlan20
description IPv6-SLAAC
ip address 192.168.20.1 255.255.255.0
ipv6 address FE80:DB8:0:20::1 linklocal
ipv6 address 2001:DB8:0:20::1/64
ipv6 enable
endStateful DHCPv6 Address Assignment
The use of DHCPv6 is not required for IPv6 client connectivity if SLAAC is already deployed. There are two modes of operation for DHCPv6, that is, Stateless and Stateful.
The DHCPv6 Stateless mode is used to provide clients with additional network information that is not available in the router advertisement, but not an IPv6 address, becuase this is already provided by SLAAC. This information includes the DNS domain name, DNS servers, and other DHCP vendor-specific options.

The following interface configuration is for a Cisco IOS IPv6 router implementing stateless DHCPv6 with SLAAC enabled:
ipv6 unicast-routing
ipv6 dhcp pool IPV6_DHCPPOOL
address prefix 2001:db8:5:10::/64
domain-name cisco.com
dns-server 2001:db8:6:6::1
interface Vlan20
description IPv6-DHCP-Stateless
ip address 192.168.20.1 255.255.255.0
ipv6 nd other-config-flag
ipv6 dhcp server IPV6_DHCPPOOL
ipv6 address 2001:DB8:0:20::1/64
endRouter Solicitation
A Router Solicitation message is issued by a host controller to facilitate local routers to transmit a Router Advertisement from which the controller can obtain information about local routing, or perform stateless auto configuration. Router Advertisements are transmitted periodically and the host prompts with an immediate Router Advertisement using a Router Solicitation such as - when it boots or following a restart operation.
Router Advertisement
A Router Advertisement message is issued periodically by a router or in response to a Router Solicitation message from a host. The information contained in these messages is used by a host to perform stateless auto configuration and to modify its routing table.
Neighbor Discovery
IPv6 Neighbor Discovery is a set of messages and processes that determine relationships between neighboring nodes. Neighbor Discovery replaces the Address Resolution Protocol (ARP), Internet Control Message Protocol (ICMP) Router Discovery, and ICMP Redirect used in IPv4.
IPv6 Neighbor Discovery inspection analyzes neighbor discovery messages in order to build a trusted binding table database, and IPv6 Neighbor Discovery packets that do not comply, are dropped. The neighbor binding table in the tracks each IPv6 address and its associated MAC address. Clients are removed from the table according to neighbor-binding timers.
Neighbor Discovery Suppression
The IPv6 addresses of wireless clients are cached by a device once the wireless client is in RUN state. When the device receives an NS multicast, it looks into the IPv6 addresses cached. If the target address is known to the device and belongs to one of its wireless clients, the device converts the NS from multicast to unicast and forward it to the wireless client. If the target address is not present in the cache, then device interprets that the Multicast NS is for a wired entity and forward it towards the wired side and not to the wireless client.
The same behavior is seen for ARP request in case of IPv4 address, where the device maintains IPv4 address of the wireless client in the cache.
When neither of the configuration is enabled, and when the device receives Non-DAD or DAD NS multicast looking for an IPv6 address, and if the target address is known to the device and belongs to one of its clients, the device will convert the multicast NS to unicast NS, with the destination MAC address, replaced with client's MAC and forward the unicast packet towards client.
When full-proxy is enabled, and when the device receives Non-DAD or DAD NS multicast, looking for an IPv6 address, and if the target address is known to the device and belongs to one of its clients, the device will reply with an NA message on behalf of the client.
You can use the ipv6 nd proxy command to enable or disable DAD or full proxy.
When the device receives an DAD-NS multicast looking for an IPv6 address, and if the target address is known to the device and belongs to one of its clients, the device will reply with an NA message on behalf of the client.
When the device receives Non-DAD NS multicast looking for an IPv6 address, and if the target address is known to the device and belongs to one of its clients, the device will convert the multicast NS to unicast NS, with the destination MAC address, replaced with client's MAC and forward the unicast packet towards client.
If the device does not have the IPv6 address of a wireless client, the device does not respond with NA; instead, it forwards the NS packet to the wired side. Reason for forwarding to Wired Side is due to the assumption that all wireless client IPv6 address and the its mapped MAC address should be available in the controller and if an IPv6 address required in the NS is not available, then that address is not a wireless client address, so forwarded to wired side.
Router Advertisement Guard
The RA Guard feature increases the security of the IPv6 network by dropping router advertisements coming from wireless clients. Without this feature, misconfigured or malicious IPv6 clients could announce themselves as a router for the network, often with a high priority, which could take precedence over legitimate IPv6 routers. By default, RA guard is always enabled on the controller.
-
Port on which the frame is received
-
IPv6 source address
-
Prefix list
-
Trusted or Untrusted ports for receiving the router advertisement guard messages
-
Trusted/Untrusted IPv6 source addresses of the router advertisement sender
-
Trusted/Untrusted Prefix list and Prefix ranges
-
Router preference
Router Advertisement Throttling
RA throttling allows the controller to enforce limits to the RA packets headed toward the wireless network. By enabling RA throttling, routers that send multiple RA packets can be trimmed to a minimum frequency that will still maintain an IPv6 client connectivity. If a client sends an RS packet, an RA is sent back to the client. This RA is allowed through the controller and unicast to the client. This process ensures that the new clients or roaming clients are not affected by the RA throttling.
 Feedback
Feedback