Information About Application Hosting
A hosted application is a software as a service solution, and it can be run remotely using commands. Application hosting gives administrators a platform for leveraging their own tools and utilities.
This module describes the Application Hosting feature and how to enable it.
Need for Application Hosting
The move to virtual environments has given rise to the need to build applications that are reusable, portable, and scalable. Application hosting gives administrators a platform for leveraging their own tools and utilities. An application, hosted on a network device, can serve a variety of purposes. This ranges from automation, configuration management monitoring, and integration with existing tool chains.
Cisco devices support third-party off-the-shelf applications built using Linux tool chains. Users can run custom applications cross-compiled with the software development kit that Cisco provides.
IOx Overview
IOx is a Cisco-developed end-to-end application framework that provides application hosting capabilities for different application types on Cisco network platforms.
IOx architecture for the IR1101 is different compared to other Cisco platforms that use the hypervisor approach. In other platforms, IOx runs as a virtual machine. IOx is running as a process on the IR1101.
Cisco Application Hosting Overview
The IR1101 enables the user to deploy the application using the app-hosting CLIs. These app-hosting CLIs are not available on the other older platforms. There are additional ways to deploy the applications using the Local Manager and Fog Director.
Application hosting provides the following services:
-
Launches designated applications in containers.
-
Checks available resources (memory, CPU, and storage), and allocates and manages them.
-
Provides support for console logging.
-
Provides access to services via REST APIs.
-
Provides a CLI endpoint.
-
Provides an application hosting infrastructure referred to as Cisco Application Framework (CAF).
-
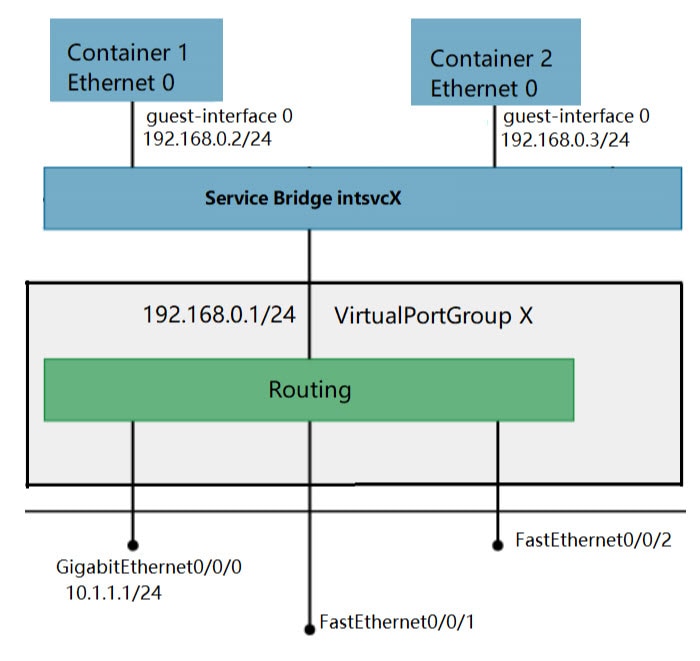
Helps in the setup of platform-specific networking (packet-path) via VirtualPortGroup and management interfaces
The container is referred to as the virtualization environment provided to run the guest application on the host operating system. The Cisco IOS-XE virtualization services provide manageability and networking models for running guest applications. The virtualization infrastructure allows the administrator to define a logical interface that specifies the connectivity between the host and the guest. IOx maps the logical interface into the Virtual Network Interface Card (vNIC) that the guest application uses.
Applications to be deployed in the containers are packaged as TAR files. The configuration that is specific to these applications is also packaged as part of the TAR file.
The management interface on the device connects the application hosting network to the IOS management interface. The Layer 3 interface of the application receives the Layer 2 bridged traffic from the IOS management interface. The management interface connects through the management bridge to the container/application interface. The IP address of the application must be on the same subnet as the management interface IP address.
IOXMAN
IOXMAN is a process that establishes a tracing infrastructure to provide logging or tracing services for guest applications, except Libvirt, that emulates serial devices. IOXMAN is based on the lifecycle of the guest application to enable and disable the tracing service, to send logging data to IOS syslog, to save tracing data to IOx tracelog, and to maintain IOx tracelog for each guest application.
GPS access to IOx Apps
Previously, when a modem has GPS enabled, the NMEA stream was not forwarded to IOx. This release allows the NMEA stream to be forwarded to IOx from the ngiolite module. There are two steps to enable this.
-
Create a tunnel between Linux and IOx
-
Forward all NMEA messages over the tunnel to IOx.
The system code checks for the presence of the tunnel, and if it is not present, data cannot be sent to IOx.
To support this feature there will be two new tunnels created for two cellular modems on the IR1101 and IR1800. Two tunnels are created by default and whichever modem has the GPS/NMEA enabled, the NMEA stream will be sent over the corresponding tunnel as follows:
Modem0:
[Linux] /dev/ttyTun5 and /dev/ttyTun6 [IOx]. Soft link to /dev/ttyTun5 will be created named /dev/ttyTunNMEA0, soft link to /dev/ttyTun6 will be created named /dev/ttyNMEA0 which can be accessed from IOx.
Modem1:
[Linux] /dev/ttyTun7 and /dev/ttyTun8 [IOx]. Soft link to /dev/ttyTun7 will be created named /dev/ttyTunNMEA1, soft link to /dev/ttyTun8 will be created named /dev/ttyNMEA1 which can be accessed from IOx.
The following command shows the state of the GPS:
IR1101#show app-hosting list
App id State
---------------------------------------------------------
gps RUNNINGGuest Shell as IOx Container APP
The Guest Shell is a virtualized Linux-based environment, designed to run custom Linux applications, including Python for automated control and management of Cisco devices. Using the Guest Shell, the user can also install, update, and operate third-party Linux applications and access the IOS CLI.
The Guest Shell environment is intended for tools, Linux utilities, and manageability rather than networking.
Guest Shell shares the kernel with the host (router) system. Users can access the Linux shell of Guest Shell and update scripts and software packages in the container rootfs. However, users within the Guest Shell cannot modify the host file system and processes.
The Guest Shell container is managed using IOx. IOx is Cisco's Application Hosting Infrastructure for Cisco IOS XE devices. IOx enables hosting of applications and services developed by Cisco, partners, and third-party developers in network edge devices, seamlessly across diverse and disparate hardware platforms.
The Guest Shell is typically bundled with the system image and can be installed using the guestshell enable Cisco IOS command. However, this approach leads to an increase of roughly 75MB in the size of the image. This is a problem for some users who have limited bandwidth, or download images through LTE.
With these users in mind, guestshell will be made available as a single tar file which can then be downloaded and installed on the system like any other IOX application. As a result, there won't be any increase in the size of the universal release image.
 Note |
Day 0 guestshell provisioning will not work with this approach. |
By default, Guest Shell allows applications to access the management network via the management interface. For platforms like the IR1101, which don't have a dedicated management port, a VirtualPortGroup can be associated with Guest Shell in the IOS configuration.
Sample guestshell configuration can be found here.
To install guestshell on the device, copy the tar file to the router and run the following command:
app-hosting install appid guestshell package <path to tar file>
Use the following command to check the status:
show app-hosting list
Once guestshell has been deployed successfully, standard guestshell commands such as guestshell enable , guestshell run bash , and guestshell run python3 should work.
The following resource talks about running python scripts using guestshell:
 Note |
Only python3 is supported in 17.5.1. |
Important - Before You Install
Before attempting to install Guest shell on your device, please verify that the device has IOx container keys programmed on it by running the following command:
Router#show software authenticity keys | i Name
Product Name : SFP-VADSL2-I
Product Name : SFP-VADSL2-I
Product Name : IR1101
Product Name : IR1101
Product Name : Cisco Services Containers
Product Name : Cisco Services ContainersThe output should contain one or more lines with the Product Name “Cisco Services Containers”. If the device doesn’t have container keys programmed on it, then you won’t be able to install guest shell.
You will see an error like the following:
*Aug 26 15:47:21.484: %IOSXE-3-PLATFORM: R0/0: IOx: App signature verification failed with non-zero exit code
*Aug 26 15:47:21.588: %IM-6-INSTALL_MSG: R0/0: ioxman: app-hosting: Install failed: App package signature (package.sign)
verification failed for package manifest file package.mf. Re-sign the application and then deploy again.There is no software based mechanism to install container keys on the device. The keys have to be programmed at the manufacturing facility. IR1100 devices shipped after January 1, 2020, should have the container keys programmed.
The guest shell tar file is published along with the IOS-XE image for a given release. More information can be found here:https://developer.cisco.com/docs/iox/#!iox-resource-downloads/downloads

 Feedback
Feedback