Inspection for Management Application Protocols
This chapter describes how to configure application layer protocol inspection. Inspection engines are required for services that embed IP addressing information in the user data packet or that open secondary channels on dynamically assigned ports. These protocols require the ASA to do a deep packet inspection instead of passing the packet through the fast path. As a result, inspection engines can affect overall throughput.
Several common inspection engines are enabled on the ASA by default, but you might need to enable others depending on your network.
DCERPC Inspection
This section describes the DCERPC inspection engine. This section includes the following topics:
DCERPC Overview
DCERPC is a protocol widely used by Microsoft distributed client and server applications that allows software clients to execute programs on a server remotely.
This typically involves a client querying a server called the Endpoint Mapper listening on a well known port number for the dynamically allocated network information of a required service. The client then sets up a secondary connection to the server instance providing the service. The security appliance allows the appropriate port number and network address and also applies NAT, if needed, for the secondary connection.
DCERPC inspect maps inspect for native TCP communication between the EPM and client on well known TCP port 135. Map and lookup operations of the EPM are supported for clients. Client and server can be located in any security zone. The embedded server IP address and Port number are received from the applicable EPM response messages. Since a client may attempt multiple connections to the server port returned by EPM, multiple use of pinholes are allowed, which have user configurable timeouts.

Note![]() DCERPC inspection only supports communication between the EPM and clients to open pinholes through theASA. Clients using RPC communication that does not use the EPM is not supported with DCERPC inspection.
DCERPC inspection only supports communication between the EPM and clients to open pinholes through theASA. Clients using RPC communication that does not use the EPM is not supported with DCERPC inspection.
Select DCERPC Map
Add/Edit Service Policy Rule Wizard > Rule Actions > Protocol Inspection Tab >Select DCERPC Map
The Select DCERPC Map dialog box lets you select or create a new DCERPC map. A DCERPC map lets you change the configuration values used for DCERPC application inspection. The Select DCERPC Map table provides a list of previously configured maps that you can select for application inspection.
DCERPC Inspect Map
Configuration > Global Objects > Inspect Maps > DCERPC
The DCERPC pane lets you view previously configured DCERPC application inspection maps. A DCERPC map lets you change the default configuration values used for DCERPC application inspection.
DCERPC is a protocol widely used by Microsoft distributed client and server applications that allows software clients to execute programs on a server remotely.
This typically involves a client querying a server called the Endpoint Mapper (EPM) listening on a well known port number for the dynamically allocated network information of a required service. The client then sets up a secondary connection to the server instance providing the service. The security appliance allows the appropriate port number and network address and also applies NAT, if needed, for the secondary connection.
DCERPC inspect maps inspect for native TCP communication between the EPM and client on well known TCP port 135. Map and lookup operations of the EPM are supported for clients. Client and server can be located in any security zone. The embedded server IP address and Port number are received from the applicable EPM response messages. Because a client may attempt multiple connections to the server port returned by EPM, multiple use of pinholes are allowed, which have user configurable timeouts.
- DCERPC Inspect Maps—Table that lists the defined DCERPC inspect maps.
- Add—Configures a new DCERPC inspect map. To edit a DCERPC inspect map, choose the DCERPC entry in the DCERPC Inspect Maps table and click Customize.
- Delete—Deletes the inspect map selected in the DCERPC Inspect Maps table.
- Security Level—Select the security level (high, medium, or low).
Endpoint mapper service: not enforced
Endpoint mapper service lookup: enabled
Endpoint mapper service lookup timeout: 00:05:00
Endpoint mapper service: not enforced
Endpoint mapper service lookup: disabled.
Endpoint mapper service: enforced
Endpoint mapper service lookup: disabled
–![]() Customize—Opens the Add/Edit DCERPC Policy Map dialog box for additional settings.
Customize—Opens the Add/Edit DCERPC Policy Map dialog box for additional settings.
–![]() Default Level—Sets the security level back to the default level of Medium.
Default Level—Sets the security level back to the default level of Medium.
Add/Edit DCERPC Policy Map
Configuration > Global Objects > Inspect Maps > DCERPC > DCERPC Inspect Map > Basic/Advanced View
The Add/Edit DCERPC Policy Map pane lets you configure the security level and parameters for DCERPC application inspection maps.
- Name—When adding a DCERPC map, enter the name of the DCERPC map. When editing a DCERPC map, the name of the previously configured DCERPC map is shown.
- Description—Enter the description of the DCERPC map, up to 200 characters in length.
- Security Level—Select the security level (high, medium, or low).
Endpoint mapper service: not enforced
Endpoint mapper service lookup: enabled
Endpoint mapper service lookup timeout: 00:05:00
Endpoint mapper service: not enforced
Endpoint mapper service lookup: disabled.
Endpoint mapper service: enforced
Endpoint mapper service lookup: disabled
–![]() Default Level—Sets the security level back to the default level of Medium.
Default Level—Sets the security level back to the default level of Medium.
–![]() Pinhole Timeout—Sets the pinhole timeout. Because a client may use the server information returned by the endpoint mapper for multiple connections, the timeout value is configurable based on the client application environment. Range is from 0:0:1 to 1193:0:0. Default is 2 minutes.
Pinhole Timeout—Sets the pinhole timeout. Because a client may use the server information returned by the endpoint mapper for multiple connections, the timeout value is configurable based on the client application environment. Range is from 0:0:1 to 1193:0:0. Default is 2 minutes.
–![]() Enforce endpoint-mapper service—Enforces endpoint mapper service during binding.
Enforce endpoint-mapper service—Enforces endpoint mapper service during binding.
–![]() Enable endpoint-mapper service lookup—Enables the lookup operation of the endpoint mapper service. If disabled, the pinhole timeout is used.
Enable endpoint-mapper service lookup—Enables the lookup operation of the endpoint mapper service. If disabled, the pinhole timeout is used.
Enforce Service Lookup Timeout—Enforces the service lookup timeout specified.
Service Lookup Timeout—Sets the timeout for pinholes from lookup operation.
GTP Inspection
This section describes the GTP inspection engine. This section includes the following topics:
- GTP Inspection Overview
- Select GTP Map
- GTP Inspect Map
- IMSI Prefix Filtering
- Add/Edit GTP Policy Map (Security Level)
- Add/Edit GTP Policy Map (Details)
- Add/Edit GTP Map

Note![]() GTP inspection requires a special license.
GTP inspection requires a special license.
GTP Inspection Overview
GPRS provides uninterrupted connectivity for mobile subscribers between GSM networks and corporate networks or the Internet. The GGSN is the interface between the GPRS wireless data network and other networks. The SGSN performs mobility, data session management, and data compression (See Figure 12-1).
Figure 12-1 GPRS Tunneling Protocol
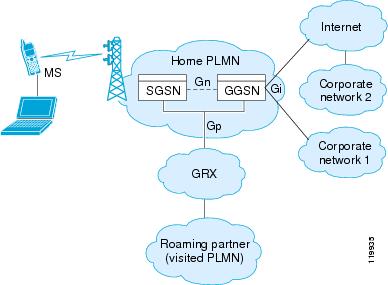
The UMTS is the commercial convergence of fixed-line telephony, mobile, Internet and computer technology. UTRAN is the networking protocol used for implementing wireless networks in this system. GTP allows multi-protocol packets to be tunneled through a UMTS/GPRS backbone between a GGSN, an SGSN and the UTRAN.
GTP does not include any inherent security or encryption of user data, but using GTP with the ASA helps protect your network against these risks.
The SGSN is logically connected to a GGSN using GTP. GTP allows multiprotocol packets to be tunneled through the GPRS backbone between GSNs. GTP provides a tunnel control and management protocol that allows the SGSN to provide GPRS network access for a mobile station by creating, modifying, and deleting tunnels. GTP uses a tunneling mechanism to provide a service for carrying user data packets.

Note![]() When using GTP with failover, if a GTP connection is established and the active unit fails before data is transmitted over the tunnel, the GTP data connection (with a “j” flag set) is not replicated to the standby unit. This occurs because the active unit does not replicate embryonic connections to the standby unit.
When using GTP with failover, if a GTP connection is established and the active unit fails before data is transmitted over the tunnel, the GTP data connection (with a “j” flag set) is not replicated to the standby unit. This occurs because the active unit does not replicate embryonic connections to the standby unit.
Select GTP Map
Add/Edit Service Policy Rule Wizard > Rule Actions > Protocol Inspection Tab >Select GTP Map
The Select GTP Map dialog box lets you select or create a new GTP map. A GTP map lets you change the configuration values used for GTP application inspection. The Select GTP Map table provides a list of previously configured maps that you can select for application inspection.

Note![]() GTP inspection requires a special license. If you try to enable GTP application inspection on a ASA without the required license, the ASA displays an error message.
GTP inspection requires a special license. If you try to enable GTP application inspection on a ASA without the required license, the ASA displays an error message.
GTP Inspect Map
Configuration > Global Objects > Inspect Maps > GTP
The GTP pane lets you view previously configured GTP application inspection maps. A GTP map lets you change the default configuration values used for GTP application inspection.
GTP is a relatively new protocol designed to provide security for wireless connections to TCP/IP networks, such as the Internet. You can use a GTP map to control timeout values, message sizes, tunnel counts, and GTP versions traversing the security appliance.

Note![]() GTP inspection is not available without a special license.
GTP inspection is not available without a special license.
- GTP Inspect Maps—Table that lists the defined GTP inspect maps.
- Add—Configures a new GTP inspect map. To edit a GTP inspect map, choose the GTP entry in the GTP Inspect Maps table and click Customize.
- Delete—Deletes the inspect map selected in the GTP Inspect Maps table.
- Security Level—Security level low only.
–![]() Maximum Number of Tunnels: 500
Maximum Number of Tunnels: 500
–![]() Pdp-Context timeout: 00:30:00
Pdp-Context timeout: 00:30:00
–![]() Signaling timeout: 00:30:00.
Signaling timeout: 00:30:00.
IMSI Prefix Filtering
Configuration > Global Objects > Inspect Maps > GTP > IMSI Prefix Filtering
The IMSI Prefix tab lets you define the IMSI prefix to allow within GTP requests.
- Mobile Country Code—Defines the non-zero, three-digit value identifying the mobile country code. One or two-digit entries will be prepended by 0 to create a three-digit value.
- Mobile Network Code—Defines the two or three-digit value identifying the network code.
- Add—Add the specified country code and network code to the IMSI Prefix table.
- Delete—Deletes the specified country code and network code from the IMSI Prefix table.
Add/Edit GTP Policy Map (Security Level)
Configuration > Global Objects > Inspect Maps > GTP > GTP Inspect Map > Basic View
The Add/Edit GTP Policy Map pane lets you configure the security level and additional settings for GTP application inspection maps.
- Name—When adding a GTP map, enter the name of the GTP map. When editing a GTP map, the name of the previously configured GTP map is shown.
- Description—Enter the description of the GTP map, up to 200 characters in length.
- Security Level—Security level low only.
Maximum Number of Tunnels: 500
T3-response timeout: 00:00:20.
Drop and log unknown message IDs.
–![]() IMSI Prefix Filtering—Opens the IMSI Prefix Filtering dialog box to configure IMSI prefix filters.
IMSI Prefix Filtering—Opens the IMSI Prefix Filtering dialog box to configure IMSI prefix filters.
–![]() Default Level—Sets the security level back to the default.
Default Level—Sets the security level back to the default.
Add/Edit GTP Policy Map (Details)
Configuration > Global Objects > Inspect Maps > GTP > GTP Inspect Map > Advanced View
The Add/Edit GTP Policy Map pane lets you configure the security level and additional settings for GTP application inspection maps.
- Name—When adding a GTP map, enter the name of the GTP map. When editing a GTP map, the name of the previously configured GTP map is shown.
- Description—Enter the description of the GTP map, up to 200 characters in length.
- Security Level—Shows the security level and IMSI prefix filtering settings to configure.
- Permit Parameters—Tab that lets you configure the permit parameters for the GTP inspect map.
From object group—Specify an object group or use the browse button to open the Add Network Object Group dialog box.
To object group—Specify an object group or use the browse button to open the Add Network Object Group dialog box.
–![]() Add—Add the specified country code and network code to the IMSI Prefix table.
Add—Add the specified country code and network code to the IMSI Prefix table.
–![]() Delete—Deletes the specified country code and network code from the IMSI Prefix table.
Delete—Deletes the specified country code and network code from the IMSI Prefix table.
–![]() Permit Errors—Lets any packets that are invalid or that encountered an error during inspection to be sent through the ASA instead of being dropped. By default, all invalid packets or packets that failed during parsing are dropped.
Permit Errors—Lets any packets that are invalid or that encountered an error during inspection to be sent through the ASA instead of being dropped. By default, all invalid packets or packets that failed during parsing are dropped.
–![]() Maximum Number of Requests—Lets you change the default for the maximum request queue size allowed. The default for the maximum request queue size is 200. Specifies the maximum number of GTP requests that will be queued waiting for a response. The permitted range is from 1 to 9999999.
Maximum Number of Requests—Lets you change the default for the maximum request queue size allowed. The default for the maximum request queue size is 200. Specifies the maximum number of GTP requests that will be queued waiting for a response. The permitted range is from 1 to 9999999.
–![]() Maximum Number of Tunnels—Lets you change the default for the maximum number of tunnels allowed. The default tunnel limit is 500. Specifies the maximum number of tunnels allowed. The permitted range is from 1 to 9999999 for the global overall tunnel limit.
Maximum Number of Tunnels—Lets you change the default for the maximum number of tunnels allowed. The default tunnel limit is 500. Specifies the maximum number of tunnels allowed. The permitted range is from 1 to 9999999 for the global overall tunnel limit.
GSN timeout—Lets you change the default for the maximum period of inactivity before a GSN is removed. The default is 30 minutes. Timeout is in the format hh:mm:ss, where hh specifies the hour, mm specifies the minutes, and ss specifies the seconds. A value 0 means never tear down.
PDP-Context timeout—Lets you change the default for the maximum period of inactivity before receiving the PDP Context for a GTP session. The default is 30 minutes. Timeout is in the format hh:mm:ss, where hh specifies the hour, mm specifies the minutes, and ss specifies the seconds. A value 0 means never tear down.
Request Queue—Lets you change the default for the maximum period of inactivity before receiving the GTP message during a GTP session. The default is 1 minute. Timeout is in the format hh:mm:ss, where hh specifies the hour, mm specifies the minutes, and ss specifies the seconds. A value 0 means never tear down.
Signaling—Lets you change the default for the maximum period of inactivity before a GTP signaling is removed. The default is 30 minutes. Timeout is in the format hh:mm:ss, where hh specifies the hour, mm specifies the minutes, and ss specifies the seconds. A value 0 means never tear down.
Tunnel—Lets you change the default for the maximum period of inactivity for the GTP tunnel. The default is 1 hour. Timeout is in the format hh:mm:ss, where hh specifies the hour, mm specifies the minutes, and ss specifies the seconds. A value 0 means never tear down Request timeout—Specifies the GTP Request idle timeout.
T3-Response timeout—Specifies the maximum wait time for a response before removing the connection.
- IMSI Prefix Filtering—Tab that lets you configure the IMSI prefix filtering for the GTP inspect map.
–![]() Mobile Country Code—Defines the non-zero, three-digit value identifying the mobile country code. One or two-digit entries will be prepended by 0 to create a three-digit value.
Mobile Country Code—Defines the non-zero, three-digit value identifying the mobile country code. One or two-digit entries will be prepended by 0 to create a three-digit value.
–![]() Mobile Network Code—Defines the two or three-digit value identifying the network code.
Mobile Network Code—Defines the two or three-digit value identifying the network code.
–![]() Add—Add the specified country code and network code to the IMSI Prefix table.
Add—Add the specified country code and network code to the IMSI Prefix table.
–![]() Delete—Deletes the specified country code and network code from the IMSI Prefix table.
Delete—Deletes the specified country code and network code from the IMSI Prefix table.
–![]() Match Type—Shows the match type, which can be a positive or negative match.
Match Type—Shows the match type, which can be a positive or negative match.
–![]() Criterion—Shows the criterion of the GTP inspection.
Criterion—Shows the criterion of the GTP inspection.
–![]() Value—Shows the value to match in the GTP inspection.
Value—Shows the value to match in the GTP inspection.
–![]() Action—Shows the action if the match condition is met.
Action—Shows the action if the match condition is met.
–![]() Add—Opens the Add GTP Inspect dialog box to add an GTP inspection.
Add—Opens the Add GTP Inspect dialog box to add an GTP inspection.
–![]() Edit—Opens the Edit GTP Inspect dialog box to edit an GTP inspection.
Edit—Opens the Edit GTP Inspect dialog box to edit an GTP inspection.
–![]() Delete—Deletes an GTP inspection.
Delete—Deletes an GTP inspection.
Add/Edit GTP Map
Configuration > Global Objects > Inspect Maps > GTP > GTP Inspect Map > Add/Edit GTP Map
The Add/Edit GTP Inspect dialog box lets you define the match criterion and value for the GTP inspect map.
For example, if No Match is selected on the string “example.com,” then any traffic that contains “example.com” is excluded from the class map.
–![]() Access Point Name—Match on access point name.
Access Point Name—Match on access point name.
–![]() Message ID—Match on the message ID.
Message ID—Match on the message ID.
–![]() Message Length—Match on the message length
Message Length—Match on the message length
–![]() Version—Match on the version.
Version—Match on the version.
- Access Point Name Criterion Values—Specifies an access point name to be matched. By default, all messages with valid APNs are inspected, and any APN is allowed.
–![]() Regular Expression—Lists the defined regular expressions to match.
Regular Expression—Lists the defined regular expressions to match.
–![]() Manage—Opens the Manage Regular Expressions dialog box, which lets you configure regular expressions.
Manage—Opens the Manage Regular Expressions dialog box, which lets you configure regular expressions.
–![]() Regular Expression Class—Lists the defined regular expression classes to match.
Regular Expression Class—Lists the defined regular expression classes to match.
–![]() Manage—Opens the Manage Regular Expression Class dialog box, which lets you configure regular expression class maps.
Manage—Opens the Manage Regular Expression Class dialog box, which lets you configure regular expression class maps.
- Message ID Criterion Values—Specifies the numeric identifier for the message that you want to match. The valid range is 1 to 255. By default, all valid message IDs are allowed.
–![]() Value—Specifies whether value is an exact match or a range.
Value—Specifies whether value is an exact match or a range.
Range—Enter a range of values.
–![]() Action—Drop packet or limit rate (pps).
Action—Drop packet or limit rate (pps).
- Message Length Criterion Values—Lets you change the default for the maximum message length for the UDP payload that is allowed.
–![]() Minimum value—Specifies the minimum number of bytes in the UDP payload. The range is from 1 to 65536.
Minimum value—Specifies the minimum number of bytes in the UDP payload. The range is from 1 to 65536.
–![]() Maximum value—Specifies the maximum number of bytes in the UDP payload. The range is from 1 to 65536.
Maximum value—Specifies the maximum number of bytes in the UDP payload. The range is from 1 to 65536.
- Version Criterion Values—Specifies the GTP version for messages that you want to match. The valid range is 0-255. Use 0 to identify Version 0 and 1 to identify Version 1. Version 0 of GTP uses port 3386, while Version 1 uses port 2123. By default all GTP versions are allowed.
–![]() Value—Specifies whether value is an exact match or a range.
Value—Specifies whether value is an exact match or a range.
RADIUS Accounting Inspection
This section describes the RADIUS Accounting inspection engine. This section includes the following topics:
- RADIUS Accounting Inspection Overview
- Select RADIUS Accounting Map
- Add RADIUS Accounting Policy Map
- RADIUS Inspect Map
- RADIUS Inspect Map Host
- RADIUS Inspect Map Other
RADIUS Accounting Inspection Overview
One of the well known problems is the over-billing attack in GPRS networks. The over-billing attack can cause consumers anger and frustration by being billed for services that they have not used. In this case, a malicious attacker sets up a connection to a server and obtains an IP address from the SGSN. When the attacker ends the call, the malicious server will still send packets to it, which gets dropped by the GGSN, but the connection from the server remains active. The IP address assigned to the malicious attacker gets released and reassigned to a legitimate user who will then get billed for services that the attacker will use.
RADIUS accounting inspection prevents this type of attack by ensuring the traffic seen by the GGSN is legitimate. With the RADIUS accounting feature properly configured, the security appliance tears down a connection based on matching the Framed IP attribute in the Radius Accounting Request Start message with the Radius Accounting Request Stop message. When the Stop message is seen with the matching IP address in the Framed IP attribute, the security appliance looks for all connections with the source matching the IP address.
You have the option to configure a secret pre-shared key with the RADIUS server so the security appliance can validate the message. If the shared secret is not configured, the security appliance does not need to validate the source of the message and will only check that the source IP address is one of the configured addresses allowed to send the RADIUS messages.

Note![]() When using RADIUS accounting inspection with GPRS enabled, the ASA checks for the 3GPP-Session-Stop-Indicator in the Accounting Request STOP messages to properly handle secondary PDP contexts. Specifically, the ASA requires that the Accounting Request STOP messages include the 3GPP-SGSN-Address attribute before it will terminate the user sessions and all associated connections. Some third-party GGSNs might not send this attribute by default.
When using RADIUS accounting inspection with GPRS enabled, the ASA checks for the 3GPP-Session-Stop-Indicator in the Accounting Request STOP messages to properly handle secondary PDP contexts. Specifically, the ASA requires that the Accounting Request STOP messages include the 3GPP-SGSN-Address attribute before it will terminate the user sessions and all associated connections. Some third-party GGSNs might not send this attribute by default.
Select RADIUS Accounting Map
The Select RADIUS Accounting Map dialog box lets you select a defined RADIUS accounting map or define a new one.
Add RADIUS Accounting Policy Map
The Add RADIUS Accounting Policy Map dialog box lets you add the basic settings for the RADIUS accounting map.
- Name—Enter the name of the previously configured RADIUS accounting map.
- Description—Enter the description of the RADIUS accounting map, up to 100 characters in length.
- Host Parameters tab:
–![]() Host IP Address—Specify the IP address of the host that is sending the RADIUS messages.
Host IP Address—Specify the IP address of the host that is sending the RADIUS messages.
–![]() Key: (optional)—Specify the key.
Key: (optional)—Specify the key.
–![]() Add—Adds the host entry to the Host table.
Add—Adds the host entry to the Host table.
–![]() Delete—Deletes the host entry from the Host table.
Delete—Deletes the host entry from the Host table.
–![]() Attribute Number—Specify the attribute number to validate when an Accounting Start is received.
Attribute Number—Specify the attribute number to validate when an Accounting Start is received.
–![]() Add—Adds the entry to the Attribute table.
Add—Adds the entry to the Attribute table.
–![]() Delete—Deletes the entry from the Attribute table.
Delete—Deletes the entry from the Attribute table.
–![]() Send response to the originator of the RADIUS message—Sends a message back to the host from which the RADIUS message was sent.
Send response to the originator of the RADIUS message—Sends a message back to the host from which the RADIUS message was sent.
–![]() Enforce timeout—Enables the timeout for users.
Enforce timeout—Enables the timeout for users.
–![]() Users Timeout—Timeout for the users in the database (hh:mm:ss).
Users Timeout—Timeout for the users in the database (hh:mm:ss).
RADIUS Inspect Map
The RADIUS pane lets you view previously configured RADIUS application inspection maps. A RADIUS map lets you change the default configuration values used for RADIUS application inspection. You can use a RADIUS map to protect against an overbilling attack.
- Name—Enter the name of the inspect map, up to 40 characters in length.
- Description—Enter the description of the inspect map, up to 200 characters in length.
- RADIUS Inspect Maps—Table that lists the defined RADIUS inspect maps. The defined inspect maps are also listed in the RADIUS area of the Inspect Maps tree.
- Add—Adds the new RADIUS inspect map to the defined list in the RADIUS Inspect Maps table and to the RADIUS area of the Inspect Maps tree. To configure the new RADIUS map, select the RADIUS entry in Inspect Maps tree.
- Delete—Deletes the application inspection map selected in the RADIUS Inspect Maps table and from the RADIUS area of the Inspect Maps tree.
RADIUS Inspect Map Host
The RADIUS Inspect Map Host Parameters pane lets you configure the host parameter settings for the inspect map.
- Name—Shows the name of the previously configured RADIUS accounting map.
- Description—Enter the description of the RADIUS accounting map, up to 200 characters in length.
- Host Parameters—Lets you configure host parameters.
–![]() Host IP Address—Specify the IP address of the host that is sending the RADIUS messages.
Host IP Address—Specify the IP address of the host that is sending the RADIUS messages.
RADIUS Inspect Map Other
The RADIUS Inspect Map Other Parameters pane lets you configure additional parameter settings for the inspect map.
- Name—Shows the name of the previously configured RADIUS accounting map.
- Description—Enter the description of the RADIUS accounting map, up to 200 characters in length.
- Other Parameters—Lets you configure additional parameters.
–![]() Send response to the originator of the RADIUS message—Sends a message back to the host from which the RADIUS message was sent.
Send response to the originator of the RADIUS message—Sends a message back to the host from which the RADIUS message was sent.
–![]() Enforce timeout—Enables the timeout for users.
Enforce timeout—Enables the timeout for users.
Users Timeout—Timeout for the users in the database (hh:mm:ss).
–![]() Enable detection of GPRS accounting—Enables detection of GPRS accounting. This option is only available when GTP/GPRS license is enabled.
Enable detection of GPRS accounting—Enables detection of GPRS accounting. This option is only available when GTP/GPRS license is enabled.
–![]() Validate Attribute—Attribute information.
Validate Attribute—Attribute information.
Attribute Number—Specify the attribute number to validate when an Accounting Start is received.
RSH Inspection
RSH inspection is enabled by default. The RSH protocol uses a TCP connection from the RSH client to the RSH server on TCP port 514. The client and server negotiate the TCP port number where the client listens for the STDERR output stream. RSH inspection supports NAT of the negotiated port number if necessary.
SNMP Inspection
This section describes the SNMP inspection engine. This section includes the following topics:
SNMP Inspection Overview
SNMP application inspection lets you restrict SNMP traffic to a specific version of SNMP. Earlier versions of SNMP are less secure; therefore, denying certain SNMP versions may be required by your security policy. The ASA can deny SNMP versions 1, 2, 2c, or 3. You control the versions permitted by creating an SNMP map.
You then apply the SNMP map when you enable SNMP inspection according to the Configuring Application Layer Protocol Inspection.
Select SNMP Map
Add/Edit Service Policy Rule Wizard > Rule Actions > Protocol Inspection Tab > Select SNMP Map
The Select SNMP Map dialog box lets you select or create a new SNMP map. An SNMP map lets you change the configuration values used for SNMP application inspection. The Select SNMP Map table provides a list of previously configured maps that you can select for application inspection.
SNMP Inspect Map
Configuration > Global Objects > Inspect Maps > SNMP
The SNMP pane lets you view previously configured SNMP application inspection maps. An SNMP map lets you change the default configuration values used for SNMP application inspection.
- Map Name—Lists previously configured application inspection maps. Select a map and click Edit to view or change an existing map.
- Add—Configures a new SNMP inspect map.
- Edit—Edits the selected SNMP entry in the SNMP Inspect Maps table.
- Delete—Deletes the inspect map selected in the SNMP Inspect Maps table.
Add/Edit SNMP Map
Configuration > Global Objects > Inspect Maps > SNMP > Add/Edit SNMP Map (You can get to this dialog box through various paths.)
The Add/Edit SNMP Map dialog box lets you create a new SNMP map for controlling SNMP application inspection.
- SNMP Map Name—Defines the name of the application inspection map.
- SNMP version 1—Enables application inspection for SNMP version 1.
- SNMP version 2 (party based)—Enables application inspection for SNMP version 2.
- SNMP version 2c (community based)—Enables application inspection for SNMP version 2c.
- SNMP version 3—Enables application inspection for SNMP version 3.
XDMCP Inspection
XDMCP inspection is enabled by default; however, the XDMCP inspection engine is dependent upon proper configuration of the established command.
XDMCP is a protocol that uses UDP port 177 to negotiate X sessions, which use TCP when established.
For successful negotiation and start of an XWindows session, the ASA must allow the TCP back connection from the Xhosted computer. To permit the back connection, use the established command on the ASA. Once XDMCP negotiates the port to send the display, The established command is consulted to verify if this back connection should be permitted.
During the XWindows session, the manager talks to the display Xserver on the well-known port 6000 | n. Each display has a separate connection to the Xserver, as a result of the following terminal setting.
where n is the display number.
When XDMCP is used, the display is negotiated using IP addresses, which the ASA can NAT if needed. XDCMP inspection does not support PAT.
 Feedback
Feedback