- Information About the ASA IPS Module
- Licensing Requirements for the ASA IPS module
- Guidelines and Limitations
- Default Settings
- Configuring the ASA IPS module
- Task Flow for the ASA IPS Module
- Connecting the ASA IPS Management Interface
- Sessioning to the Module from the ASA (May Be Required)
- (ASA 5512-X through ASA 5555-X) Booting the Software Module
- Configuring Basic IPS Module Network Settings
- Configuring the Security Policy on the ASA IPS Module
- Assigning Virtual Sensors to a Security Context (ASA 5512-X and Higher)
- Diverting Traffic to the ASA IPS module
- Managing the ASA IPS module
- Monitoring the ASA IPS module
- Feature History for the ASA IPS module
ASA IPS Module
This chapter describes how to configure the ASA IPS module. The ASA IPS module might be a hardware module or a software module, depending on your ASA model. For a list of supported ASA IPS modules per ASA model, see the Cisco ASA Compatibility Matrix :
http://www.cisco.com/en/US/docs/security/asa/compatibility/asamatrx.html
Information About the ASA IPS Module
The ASA IPS module runs advanced IPS software that provides proactive, full-featured intrusion prevention services to stop malicious traffic, including worms and network viruses, before they can affect your network. This section includes the following topics:
- How the ASA IPS Module Works with the ASA
- Operating Modes
- Using Virtual Sensors (ASA 5512-X and Higher)
- Information About Management Access
How the ASA IPS Module Works with the ASA
The ASA IPS module runs a separate application from the ASA. The ASA IPS module might include an external management interface so you can connect to the ASA IPS module directly; if it does not have a management interface, you can connect to the ASA IPS module through the ASA interface. The ASA IPS SSP on the ASA 5585-X includes data interfaces; these interfaces provide additional port-density for the ASA. However, the overall through-put of the ASA is not increased.
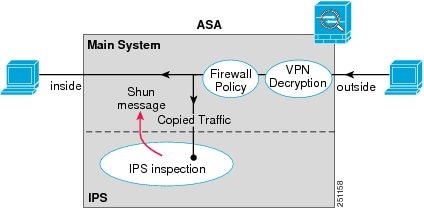
Traffic goes through the firewall checks before being forwarded to the ASA IPS module. When you identify traffic for IPS inspection on the ASA, traffic flows through the ASA and the ASA IPS module as follows. Note : This example is for “inline mode.” See Operating Modes for information about “promiscuous mode,” where the ASA only sends a copy of the traffic to the ASA IPS module.
2.![]() Incoming VPN traffic is decrypted.
Incoming VPN traffic is decrypted.
3.![]() Firewall policies are applied.
Firewall policies are applied.
4.![]() Traffic is sent to the ASA IPS module.
Traffic is sent to the ASA IPS module.
5.![]() The ASA IPS module applies its security policy to the traffic, and takes appropriate actions.
The ASA IPS module applies its security policy to the traffic, and takes appropriate actions.
6.![]() Valid traffic is sent back to the ASA; the ASA IPS module might block some traffic according to its security policy, and that traffic is not passed on.
Valid traffic is sent back to the ASA; the ASA IPS module might block some traffic according to its security policy, and that traffic is not passed on.
7.![]() Outgoing VPN traffic is encrypted.
Outgoing VPN traffic is encrypted.
Figure 28-1 shows the traffic flow when running the ASA IPS module in inline mode. In this example, the ASA IPS module automatically blocks traffic that it identified as an attack. All other traffic is forwarded through the ASA.
Figure 28-1 ASA IPS module Traffic Flow in the ASA: Inline Mode

Operating Modes
You can send traffic to the ASA IPS module using one of the following modes:
- Inline mode—This mode places the ASA IPS module directly in the traffic flow (see Figure 28-1). No traffic that you identified for IPS inspection can continue through the ASA without first passing through, and being inspected by, the ASA IPS module. This mode is the most secure because every packet that you identify for inspection is analyzed before being allowed through. Also, the ASA IPS module can implement a blocking policy on a packet-by-packet basis. This mode, however, can affect throughput.
- Promiscuous mode—This mode sends a duplicate stream of traffic to the ASA IPS module. This mode is less secure, but has little impact on traffic throughput. Unlike inline mode, in promiscuous mode the ASA IPS module can only block traffic by instructing the ASA to shun the traffic or by resetting a connection on the ASA. Also, while the ASA IPS module is analyzing the traffic, a small amount of traffic might pass through the ASA before the ASA IPS module can shun it. Figure 28-2 shows the ASA IPS module in promiscuous mode. In this example, the ASA IPS module sends a shun message to the ASA for traffic it identified as a threat.
Figure 28-2 ASA IPS module Traffic Flow in the ASA: Promiscuous Mode
Using Virtual Sensors (ASA 5512-X and Higher)
The ASA IPS module running IPS software Version 6.0 and later can run multiple virtual sensors, which means you can configure multiple security policies on the ASA IPS module. You can assign each ASA security context or single mode ASA to one or more virtual sensors, or you can assign multiple security contexts to the same virtual sensor. See the IPS documentation for more information about virtual sensors, including the maximum number of sensors supported.
Figure 28-3 shows one security context paired with one virtual sensor (in inline mode), while two security contexts share the same virtual sensor.
Figure 28-3 Security Contexts and Virtual Sensors
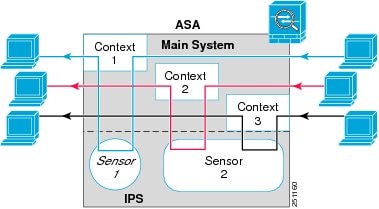
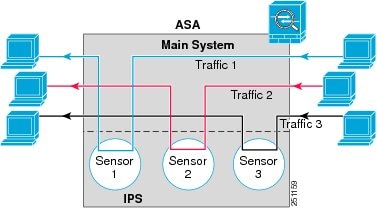
Figure 28-4 shows a single mode ASA paired with multiple virtual sensors (in inline mode); each defined traffic flow goes to a different sensor.
Figure 28-4 Single Mode ASA with Multiple Virtual Sensors
Information About Management Access
You can manage the IPS application using the following methods:
- Sessioning to the module from the ASA—If you have CLI access to the ASA, then you can session to the module and access the module CLI. See Sessioning to the Module from the ASA (May Be Required).
- Connecting to the IPS management interface using ASDM or SSH—After you launch ASDM from the ASA, your management station connects to the module management interface to configure the IPS application. For SSH, you can access the module CLI directly on the module management interface. (Telnet access requires additional configuration in the module application). The module management interface can also be used for sending syslog messages or allowing updates for the module application, such as signature database updates.
See the following information about the management interface:
–![]() ASA 5585-X—The IPS management interface is a separate external Gigabit Ethernet interface.
ASA 5585-X—The IPS management interface is a separate external Gigabit Ethernet interface.
–![]() ASA 5512-X, ASA 5515-X, ASA 5525-X, ASA 5545-X, ASA 5555-X—These models run the ASA IPS module as a software module. The IPS management interface shares the Management 0/0 interface with the ASA. Separate MAC addresses and IP addresses are supported for the ASA and ASA IPS module. You must perform configuration of the IPS IP address within the IPS operating system (using the CLI or ASDM). However, physical characteristics (such as enabling the interface) are configured on the ASA. You can remove the ASA interface configuration (specifically the interface name) to dedicate this interface as an IPS-only interface. This interface is management-only.
ASA 5512-X, ASA 5515-X, ASA 5525-X, ASA 5545-X, ASA 5555-X—These models run the ASA IPS module as a software module. The IPS management interface shares the Management 0/0 interface with the ASA. Separate MAC addresses and IP addresses are supported for the ASA and ASA IPS module. You must perform configuration of the IPS IP address within the IPS operating system (using the CLI or ASDM). However, physical characteristics (such as enabling the interface) are configured on the ASA. You can remove the ASA interface configuration (specifically the interface name) to dedicate this interface as an IPS-only interface. This interface is management-only.
–![]() ASA 5505—You can use an ASA VLAN to allow access to an internal management IP address over the backplane.
ASA 5505—You can use an ASA VLAN to allow access to an internal management IP address over the backplane.
Licensing Requirements for the ASA IPS module
The following table shows the licensing requirements for this feature:
Guidelines and Limitations
This section includes the guidelines and limitations for this feature.
The ASA 5505 does not support multiple context mode, so multiple context features, such as virtual sensors, are not supported on the AIP SSC.
Supported in routed and transparent firewall mode.
http://www.cisco.com/en/US/docs/security/asa/compatibility/asamatrx.html
- The ASA 5505 does not support multiple context mode, so multiple context features, such as virtual sensors, are not supported on the AIP SSC.
- The ASA IPS module for the ASA 5512-X and higher supports higher performance requirements, while the ASA IPS module for the ASA 5505 is designed for a small office installation. The following features are not supported for the ASA 5505:
–![]() Unretirement of default retired signatures
Unretirement of default retired signatures
–![]() ASA 5512-X through ASA 5555-X—See http://www.cisco.com/en/US/prod/collateral/vpndevc/ps6032/ps6094/ps6120/qa_c67-700608.html
ASA 5512-X through ASA 5555-X—See http://www.cisco.com/en/US/prod/collateral/vpndevc/ps6032/ps6094/ps6120/qa_c67-700608.html
–![]() ASA 5585-X—See http://www.cisco.com/en/US/prod/collateral/vpndevc/ps6032/ps6094/ps6120/qa_c67-617018.html
ASA 5585-X—See http://www.cisco.com/en/US/prod/collateral/vpndevc/ps6032/ps6094/ps6120/qa_c67-617018.html
–![]() ASA 5505—See http://www.cisco.com/en/US/prod/collateral/vpndevc/ps6032/ps6094/ps6120/product_data_sheet0900aecd802930c5.html
ASA 5505—See http://www.cisco.com/en/US/prod/collateral/vpndevc/ps6032/ps6094/ps6120/product_data_sheet0900aecd802930c5.html
Default Settings
Table 28-1 lists the default settings for the ASA IPS module.
|
|
|
|---|---|

Note![]() The default management IP address on the ASA is 192.168.1.1/24.
The default management IP address on the ASA is 192.168.1.1/24.
Configuring the ASA IPS module
This section describes how to configure the ASA IPS module and includes the following topics:
- Task Flow for the ASA IPS Module
- Connecting the ASA IPS Management Interface
- Sessioning to the Module from the ASA (May Be Required)
- Configuring Basic IPS Module Network Settings
- (ASA 5512-X through ASA 5555-X) Booting the Software Module
- Configuring the Security Policy on the ASA IPS Module
- Assigning Virtual Sensors to a Security Context (ASA 5512-X and Higher)
- Diverting Traffic to the ASA IPS module
Task Flow for the ASA IPS Module
Configuring the ASA IPS module is a process that includes configuration of the IPS security policy on the ASA IPS module and then configuration of the ASA to send traffic to the ASA IPS module. To configure the ASA IPS module, perform the following steps:
Step 1![]() Cable the ASA IPS management interface. See Connecting the ASA IPS Management Interface.
Cable the ASA IPS management interface. See Connecting the ASA IPS Management Interface.
Step 2![]() Session to the module. Access the IPS CLI over the backplane. For ASDM users, you may need to session to the module to boot the IPS software if it is not running. See Sessioning to the Module from the ASA (May Be Required).
Session to the module. Access the IPS CLI over the backplane. For ASDM users, you may need to session to the module to boot the IPS software if it is not running. See Sessioning to the Module from the ASA (May Be Required).
Step 3![]() (ASA 5512-X through ASA 5555-X; may be required) Install the software module. See (ASA 5512-X through ASA 5555-X) Booting the Software Module.
(ASA 5512-X through ASA 5555-X; may be required) Install the software module. See (ASA 5512-X through ASA 5555-X) Booting the Software Module.
Step 4![]() Depending on your ASA model:
Depending on your ASA model:
- (ASA 5512-X and higher) Configure basic network settings for the IPS module. See (ASA 5512-X and Higher) Configuring Basic Network Settings.
- (ASA 5505) Configure the management VLAN and IP address for the IPS module. See (ASA 5505) Configuring Basic Network Settings.
Step 5![]() On the module, configure the inspection and protection policy, which determines how to inspect traffic and what to do when an intrusion is detected. See Configuring the Security Policy on the ASA IPS Module.
On the module, configure the inspection and protection policy, which determines how to inspect traffic and what to do when an intrusion is detected. See Configuring the Security Policy on the ASA IPS Module.
Step 6![]() (ASA 5512-X and higher, optional) On the ASA in multiple context mode, specify which IPS virtual sensors are available for each context (if you configured virtual sensors). See Assigning Virtual Sensors to a Security Context (ASA 5512-X and Higher).
(ASA 5512-X and higher, optional) On the ASA in multiple context mode, specify which IPS virtual sensors are available for each context (if you configured virtual sensors). See Assigning Virtual Sensors to a Security Context (ASA 5512-X and Higher).
Step 7![]() On the ASA, identify traffic to divert to the ASA IPS module. See Diverting Traffic to the ASA IPS module.
On the ASA, identify traffic to divert to the ASA IPS module. See Diverting Traffic to the ASA IPS module.
Connecting the ASA IPS Management Interface
In addition to providing management access to the IPS module, the IPS management interface needs access to an HTTP proxy server or a DNS server and the Internet so it can download global correlation, signature updates, and license requests. This section describes recommended network configurations. Your network may differ.
ASA 5585-X (Hardware Module)
The IPS module includes a separate management interface from the ASA.
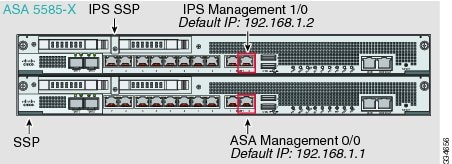
If you have an inside router, you can route between the management network, which can include both the ASA Management 0/0 and IPS Management 1/0 interfaces, and the ASA inside network. Be sure to also add a route on the ASA to reach the Management network through the inside router.
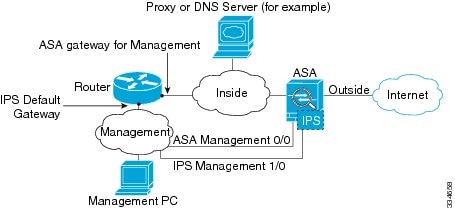
If you do not have an inside router
If you have only one inside network, then you cannot also have a separate management network, which would require an inside router to route between the networks. In this case, you can manage the ASA from the inside interface instead of the Management 0/0 interface. Because the IPS module is a separate device from the ASA, you can configure the IPS Management 1/0 address to be on the same network as the inside interface.

ASA 5512-X through ASA 5555-X (Software Module)
These models run the IPS module as a software module, and the IPS management interface shares the Management 0/0 interface with the ASA.

If you have an inside router, you can route between the Management 0/0 network, which includes both the ASA and IPS management IP addresses, and the inside network. Be sure to also add a route on the ASA to reach the Management network through the inside router.

If you do not have an inside router
If you have only one inside network, then you cannot also have a separate management network. In this case, you can manage the ASA from the inside interface instead of the Management 0/0 interface. If you remove the ASA-configured name from the Management 0/0 interface, you can still configure the IPS IP address for that interface. Because the IPS module is essentially a separate device from the ASA, you can configure the IPS management address to be on the same network as the inside interface.


Note![]() You must remove the ASA-configured name for Management 0/0; if it is configured on the ASA, then the IPS address must be on the same network as the ASA, and that excludes any networks already configured on other ASA interfaces. If the name is not configured, then the IPS address can be on any network, for example, the ASA inside network.
You must remove the ASA-configured name for Management 0/0; if it is configured on the ASA, then the IPS address must be on the same network as the ASA, and that excludes any networks already configured on other ASA interfaces. If the name is not configured, then the IPS address can be on any network, for example, the ASA inside network.
ASA 5505
The ASA 5505 does not have a dedicated management interface. You must use an ASA VLAN to access an internal management IP address over the backplane. Connect the management PC to one of the following ports: Ethernet 0/1 through 0/7, which are assigned to VLAN 1.
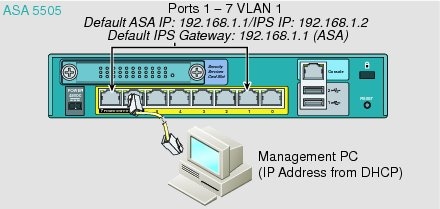
What to Do Next
- (ASA 5512-X and higher) Configure basic network settings. See (ASA 5512-X and Higher) Configuring Basic Network Settings.
- (ASA 5505) Configure management interface settings. See (ASA 5505) Configuring Basic Network Settings.
Sessioning to the Module from the ASA (May Be Required)
To access the IPS module CLI from the ASA, you can session from the ASA. For software modules, you can either session to the module (using Telnet) or create a virtual console session. A console session might be useful if the control plane is down and you cannot establish a Telnet session.
You may need to access the CLI if you are using multiple context mode and you need to set basic network settings using the CLI, or for troubleshooting.
Detailed Steps
(ASA 5512-X through ASA 5555-X) Booting the Software Module
Your ASA typically ships with IPS module software present on Disk0. If the module is not running, or if you are adding the IPS module to an existing ASA, you must boot the module software. If you are unsure if the module is running, you will not see the IPS Basic Configuration screen when you run the Startup Wizard (see Configuring Basic IPS Module Network Settings).
Detailed Steps
Step 1![]() Do one of the following:
Do one of the following:
For example, look for a filename like IPS-SSP_5512-K9-sys-1.1-a-7.1-4-E4.aip. Note the filename; you will need this filename later in the procedure.
http://www.cisco.com/cisco/software/navigator.html?mdfid=282164240
Choose Tools > File Management, then choose File Transfer > Between Local PC and Flash to upload the new image to disk0. Note the filename; you will need this filename later in the procedure.
Step 2![]() Choose Tools > Command Line Interface.
Choose Tools > Command Line Interface.
Step 3![]() To set the IPS module software location in disk0, enter the following command and then click Send :
To set the IPS module software location in disk0, enter the following command and then click Send :
For example, using the filename in the example in Step 1, enter:
Step 4![]() To install and load the IPS module software, enter the following command and then click Send :
To install and load the IPS module software, enter the following command and then click Send :
Step 5![]() To check the progress of the image transfer and module restart process, enter the following command and then click Send :
To check the progress of the image transfer and module restart process, enter the following command and then click Send :
The Status field in the output indicates the operational status of the module. A module operating normally shows a status of “Up.” While the ASA transfers an application image to the module, the Status field in the output reads “Recover.” When the ASA completes the image transfer and restarts the module, the newly transferred image is running.
Configuring Basic IPS Module Network Settings
(ASA 5512-X and Higher) Configuring Basic Network Settings
In single context mode, you can use the Startup Wizard in ASDM to configure basic IPS network configuration. These settings are saved to the IPS configuration, not the ASA configuration.
In multiple context mode, session to the module from the ASA and configure basic settings using the setup command.

Note![]() (ASA 5512-X through ASA 5555-X) If you do not see the IPS Basic Configuration screen in your wizard, then the IPS module is not running. See (ASA 5512-X through ASA 5555-X) Booting the Software Module, and then repeat this procedure after you install the module.
(ASA 5512-X through ASA 5555-X) If you do not see the IPS Basic Configuration screen in your wizard, then the IPS module is not running. See (ASA 5512-X through ASA 5555-X) Booting the Software Module, and then repeat this procedure after you install the module.
Detailed Steps—Single Mode
Step 1![]() Choose Wizards > Startup Wizard.
Choose Wizards > Startup Wizard.
Step 2![]() Click Next to advance through the initial screens until you reach the IPS Basic Configuration screen.
Click Next to advance through the initial screens until you reach the IPS Basic Configuration screen.
Step 3![]() In the Network Settings area, configure the following:
In the Network Settings area, configure the following:
- IP Address—The management IP address. By default, the address is 192.168.1.2.
- Subnet Mask—The subnet mask for the management IP address.
- Gateway—The IP address of the upstream router. The IP address of the next hop router. See Connecting the ASA IPS Management Interface to understand the requirements for your network. The default setting of the ASA management IP address will not work.
- HTTP Proxy Server—(Optional) The HTTP proxy server address. You can use a proxy server to download global correlation updates and other information instead of downloading over the Internet.
- HTTP Proxy Port—(Optional) The HTTP proxy server port.
- DNS Primary—(Optional) The primary DNS server address. If you are using a DNS server, you must configure at least one DNS server and it must be reachable for global correlation updates to be successful.
For global correlation to function, you must have either a DNS server or an HTTP proxy server configured at all times. DNS resolution is supported only for accessing the global correlation update server.
Step 4![]() In the Management Access List area, enter an IP address and subnet mask for any hosts that are allowed to access the IPS management interface, and click Add. You can add multiple IP addresses.
In the Management Access List area, enter an IP address and subnet mask for any hosts that are allowed to access the IPS management interface, and click Add. You can add multiple IP addresses.
Step 5![]() In the Cisco Account Password area, set the password for the username cisco and confirm it. The username cisco and this password are used for Telnet sessions from hosts specified by the management ACL and when accessing the IPS module from ASDM (Configuration > IPS). By default, the password is cisco.
In the Cisco Account Password area, set the password for the username cisco and confirm it. The username cisco and this password are used for Telnet sessions from hosts specified by the management ACL and when accessing the IPS module from ASDM (Configuration > IPS). By default, the password is cisco.
Step 6![]() In the Network Participation area, which you use to have the IPS module participate in SensorBase data sharing, click Full, Partial, or Off.
In the Network Participation area, which you use to have the IPS module participate in SensorBase data sharing, click Full, Partial, or Off.
Detailed Steps—Multiple Mode Using the CLI
|
|
|
|
|---|---|---|
Session to the IPS module according to the Sessioning to the Module from the ASA (May Be Required). |
||
|
|
Runs the setup utility for initial configuration of the ASA IPS module. You are prompted for basic settings. For the default gateway, specify the IP address of the upstream router. See Connecting the ASA IPS Management Interface to understand the requirements for your network. The default setting of the ASA management IP address will not work. |
(ASA 5505) Configuring Basic Network Settings
An ASA IPS module on the ASA 5505 does not have any external interfaces. You can configure a VLAN to allow access to an internal IPS management IP address over the backplane. By default, VLAN 1 is enabled for IPS management. You can only assign one VLAN as the management VLAN. This section describes how to change the management VLAN and IP address if you do not want to use the default, and how to set other required network parameters.

Note![]() Perform this configuration on the ASA 5505, not on the ASA IPS module.
Perform this configuration on the ASA 5505, not on the ASA IPS module.
Prerequisites
When you change the IPS VLAN and management address from the default, be sure to also configure the matching ASA VLAN and switch port(s) according to the procedures listed in the general operations configuration guide. You must define and configure the VLAN for the ASA so the IPS management interface is accessible on the network.
Restrictions
Do not configure NAT for the management address if you intend to access it using ASDM. For initial setup with ASDM, you need to access the real address. After initial setup (where you set the password on the ASA IPS module), you can configure NAT and supply ASDM with the translated address for accessing the ASA IPS module.
Detailed Steps
Step 1![]() In ASDM, choose Configuration > Device Setup > SSC Setup.
In ASDM, choose Configuration > Device Setup > SSC Setup.

Note![]() The following settings are written to the ASA IPS module application configuration, not the ASA configuration.
The following settings are written to the ASA IPS module application configuration, not the ASA configuration.
Step 2![]() In the Management Interface area, set the following:
In the Management Interface area, set the following:
a.![]() Choose the Interface VLAN from the drop-down list.
Choose the Interface VLAN from the drop-down list.
This setting allows you to manage the ASA IPS module using this VLAN.
b.![]() Enter the IPS management IP address. Make sure this address is on the same subnet as the ASA VLAN IP address. For example, if you assigned 10.1.1.1 to the VLAN for the ASA, then assign another address on that network, such as 10.1.1.2, for the IPS management address. By default, the address is 192.168.1.2
Enter the IPS management IP address. Make sure this address is on the same subnet as the ASA VLAN IP address. For example, if you assigned 10.1.1.1 to the VLAN for the ASA, then assign another address on that network, such as 10.1.1.2, for the IPS management address. By default, the address is 192.168.1.2
c.![]() Choose the subnet mask from the drop-down list.
Choose the subnet mask from the drop-down list.
d.![]() Enter the default gateway IP address.
Enter the default gateway IP address.
Set the gateway to be the ASA IP address for the management VLAN. By default, this IP address is 192.168.1.1.
Step 3![]() In the Management Access List area, enter the following:
In the Management Access List area, enter the following:
a.![]() Enter the IP address for the management host network.
Enter the IP address for the management host network.
b.![]() Choose the subnet mask from the drop-down list.
Choose the subnet mask from the drop-down list.
c.![]() Click Add to add these settings to the Allowed Hosts/Networks list.
Click Add to add these settings to the Allowed Hosts/Networks list.
Step 4![]() In the IPS Password area, do the following:
In the IPS Password area, do the following:
a.![]() Enter the current password. The default password is cisco.
Enter the current password. The default password is cisco.
b.![]() Enter the new password, and confirm the change.
Enter the new password, and confirm the change.
Step 5![]() Click Apply to save the settings to the running configuration.
Click Apply to save the settings to the running configuration.
Step 6![]() To launch the IPS Startup Wizard, click the Configure the IPS SSC module link.
To launch the IPS Startup Wizard, click the Configure the IPS SSC module link.
Configuring the Security Policy on the ASA IPS Module
This section describes how to configure the ASA IPS module application.
Detailed Steps
Step 1![]() Connect to ASDM using the ASA management IP address.
Connect to ASDM using the ASA management IP address.
Step 2![]() To access the IPS Device Manager (IDM) from ASDM, click Configuration > IPS.
To access the IPS Device Manager (IDM) from ASDM, click Configuration > IPS.
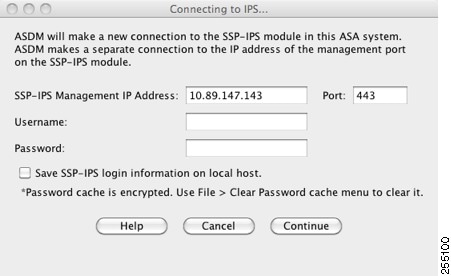
Step 3![]() Enter the IP address, username and password that you set in the Configuring Basic IPS Module Network Settings, as well as the port. The default IP address and port is 192.168.1.2:443. The default username and password is cisco and cisco.
Enter the IP address, username and password that you set in the Configuring Basic IPS Module Network Settings, as well as the port. The default IP address and port is 192.168.1.2:443. The default username and password is cisco and cisco.
If the password to access IDM is lost, you can reset the password using ASDM. See Resetting the Password, for more information.
Step 4![]() To save the login information on your local PC, check the Save IPS login information on local host check box.
To save the login information on your local PC, check the Save IPS login information on local host check box.
The Startup Wizard pane appears.

Step 6![]() Click Launch Startup Wizard. Complete the screens as prompted. For more information, see the IDM online help.
Click Launch Startup Wizard. Complete the screens as prompted. For more information, see the IDM online help.

(ASA 5512-X and higher) If you configure virtual sensors, you identify one of the sensors as the default. If the ASA series does not specify a virtual sensor name in its configuration, the default sensor is used.
What to Do Next
- For the ASA in multiple context mode, see Assigning Virtual Sensors to a Security Context (ASA 5512-X and Higher).
- For the ASA in single context mode, see Diverting Traffic to the ASA IPS module.
Assigning Virtual Sensors to a Security Context (ASA 5512-X and Higher)
If the ASA is in multiple context mode, then you can assign one or more IPS virtual sensors to each context. Then, when you configure the context to send traffic to the ASA IPS module, you can specify a sensor that is assigned to the context; you cannot specify a sensor that you did not assign to the context. If you do not assign any sensors to a context, then the default sensor configured on the ASA IPS module is used. You can assign the same sensor to multiple contexts.

Note![]() You do not need to be in multiple context mode to use virtual sensors; you can be in single mode and use different sensors for different traffic flows.
You do not need to be in multiple context mode to use virtual sensors; you can be in single mode and use different sensors for different traffic flows.
Prerequisites
For more information about configuring contexts, see the general operations configuration guide.
Detailed Steps
Step 1![]() In the ASDM Device List pane, double-click System under the active device IP address.
In the ASDM Device List pane, double-click System under the active device IP address.
Step 2![]() On the Context Management > Security Contexts pane, choose a context that you want to configure, and click Edit.
On the Context Management > Security Contexts pane, choose a context that you want to configure, and click Edit.
The Edit Context dialog box appears. For more information about configuring contexts, see the general operations configuration guide.
Step 3![]() In the IPS Sensor Allocation area, click Add.
In the IPS Sensor Allocation area, click Add.
The IPS Sensor Selection dialog box appears.
Step 4![]() From the Sensor Name drop-down list, choose a sensor name from those configured on the ASA IPS module.
From the Sensor Name drop-down list, choose a sensor name from those configured on the ASA IPS module.
Step 5![]() (Optional) To assign a mapped name to the sensor, enter a value in the Mapped Sensor Name field.
(Optional) To assign a mapped name to the sensor, enter a value in the Mapped Sensor Name field.
This sensor name can be used within the context instead of the actual sensor name. If you do not specify a mapped name, the sensor name is used within the context. For security purposes, you might not want the context administrator to know which sensors are being used by the context. Or you might want to genericize the context configuration. For example, if you want all contexts to use sensors called “sensor1” and “sensor2,” then you can map the “highsec” and “lowsec” sensors to sensor1 and sensor2 in context A, but map the “medsec” and “lowsec” sensors to sensor1 and sensor2 in context B.
Step 6![]() Click OK to return to the Edit Context dialog box.
Click OK to return to the Edit Context dialog box.
Step 7![]() (Optional) To set one sensor as the default sensor for this context, from the Default Sensor drop-down list, choose a sensor name.
(Optional) To set one sensor as the default sensor for this context, from the Default Sensor drop-down list, choose a sensor name.
If you do not specify a sensor name when you configure IPS within the context configuration, the context uses this default sensor. You can only configure one default sensor per context. If you do not specify a sensor as the default, and the context configuration does not include a sensor name, then traffic uses the default sensor on the ASA IPS module.
Step 8![]() Repeat this procedure for each security context.
Repeat this procedure for each security context.
Step 9![]() Change to each context to configure the IPS security policy as described in Diverting Traffic to the ASA IPS module.
Change to each context to configure the IPS security policy as described in Diverting Traffic to the ASA IPS module.
What to Do Next
Change to each context to configure the IPS security policy as described in Diverting Traffic to the ASA IPS module.
Diverting Traffic to the ASA IPS module
This section identifies traffic to divert from the ASA to the ASA IPS module.
Prerequisites
In multiple context mode, perform these steps in each context execution space. To change to a context, in the Configuration > Device List pane, double-click the context name under the active device IP address.
Detailed Steps
Step 1![]() Choose Configuration > Firewall > Service Policy Rules.
Choose Configuration > Firewall > Service Policy Rules.

Step 2![]() Choose Add > Add Service Policy Rule. The Add Service Policy Rule Wizard - Service Policy dialog box appears.
Choose Add > Add Service Policy Rule. The Add Service Policy Rule Wizard - Service Policy dialog box appears.
Step 3![]() Complete the Service Policy dialog box as desired. See the ASDM online help for more information about these screens.
Complete the Service Policy dialog box as desired. See the ASDM online help for more information about these screens.
Step 4![]() Click Next. The Add Service Policy Rule Wizard - Traffic Classification Criteria dialog box appears.
Click Next. The Add Service Policy Rule Wizard - Traffic Classification Criteria dialog box appears.
Step 5![]() Complete the Traffic Classification Criteria dialog box as desired. See the ASDM online help for more information about these screens.
Complete the Traffic Classification Criteria dialog box as desired. See the ASDM online help for more information about these screens.
Step 6![]() Click Next to show the Add Service Policy Rule Wizard - Rule Actions dialog box.
Click Next to show the Add Service Policy Rule Wizard - Rule Actions dialog box.
Step 7![]() Click the Intrusion Prevention tab.
Click the Intrusion Prevention tab.

Step 8![]() Check the Enable IPS for this traffic flow check box.
Check the Enable IPS for this traffic flow check box.
Step 9![]() In the Mode area, click Inline Mode or Promiscuous Mode. See Operating Modes for more information.
In the Mode area, click Inline Mode or Promiscuous Mode. See Operating Modes for more information.
Step 10![]() In the If IPS Card Fails area, click Permit traffic or Close traffic. The Close traffic option sets the ASA to block all traffic if the ASA IPS module is unavailable. The Permit traffic option sets the ASA to allow all traffic through, uninspected, if the ASA IPS module is unavailable. For information about the IPS Sensor Selection area, see the ASDM online help.
In the If IPS Card Fails area, click Permit traffic or Close traffic. The Close traffic option sets the ASA to block all traffic if the ASA IPS module is unavailable. The Permit traffic option sets the ASA to allow all traffic through, uninspected, if the ASA IPS module is unavailable. For information about the IPS Sensor Selection area, see the ASDM online help.
Step 11![]() (ASA 5512-X and higher) From the IPS Sensor to use drop-down list, choose a virtual sensor name.
(ASA 5512-X and higher) From the IPS Sensor to use drop-down list, choose a virtual sensor name.
If you use virtual sensors, you can specify a sensor name using this option. If you use multiple context mode on the ASA, you can only specify sensors that you assigned to the context (see Assigning Virtual Sensors to a Security Context (ASA 5512-X and Higher)). If you do not specify a sensor name, then the traffic uses the default sensor. In multiple context mode, you can specify a default sensor for the context. In single mode or if you do not specify a default sensor in multiple mode, the traffic uses the default sensor that is set on the ASA IPS module.
Step 12![]() Click OK and then Apply.
Click OK and then Apply.
Step 13![]() Repeat this procedure to configure additional traffic flows as desired.
Repeat this procedure to configure additional traffic flows as desired.
Managing the ASA IPS module
This section includes procedures that help you recover or troubleshoot the module and includes the following topics:
- Installing and Booting an Image on the Module
- Shutting Down the Module
- Uninstalling a Software Module Image
- Resetting the Password
- Reloading or Resetting the Module
Installing and Booting an Image on the Module
If the module suffers a failure, and the module application image cannot run, you can reinstall a new image on the module from a TFTP server (for a hardware module), or from the local disk (software module).

Note![]() Do not use the upgrade command within the module software to install the image.
Do not use the upgrade command within the module software to install the image.
Prerequisites

Note![]() This process can take approximately 15 minutes to complete, depending on your network and the size of the image.
This process can take approximately 15 minutes to complete, depending on your network and the size of the image.

Note![]() Before you download the IPS software to disk0, make sure at least 50% of the flash memory is free. When you install IPS, IPS reserves 50% of the internal flash memory for its file system.
Before you download the IPS software to disk0, make sure at least 50% of the flash memory is free. When you install IPS, IPS reserves 50% of the internal flash memory for its file system.
Detailed Steps
Shutting Down the Module
Shutting down the module software prepares the module to be safely powered off without losing configuration data. Note : If you reload the ASA, the module is not automatically shut down, so we recommend shutting down the module before reloading the ASA. To gracefully shut down the module, perform the following steps at the ASA CLI.
Detailed Steps
|
|
|
|---|---|
For a hardware module (for example, the ASA 5585-X): For a software module (for example, the ASA 5545-X): |
Uninstalling a Software Module Image
To uninstall a software module image and associated configuration, perform the following steps.
Detailed Steps
Resetting the Password
You can reset the module password to the default. For the user cisco, the default password is cisco. After resetting the password, you should change it to a unique value using the module application.
Resetting the module password causes the module to reboot. Services are not available while the module is rebooting.
If you cannot connect to ASDM with the new password, restart ASDM and try to log in again. If you defined a new password and still have an existing password in ASDM that is different from the new password, clear the password cache by choosing File > Clear ASDM Password Cache, then restart ASDM and try to log in again.
To reset the module password to the default of cisco, perform the following steps.
Detailed Steps
Step 1![]() From the ASDM menu bar, choose Tools > module Password Reset.
From the ASDM menu bar, choose Tools > module Password Reset.
The Password Reset confirmation dialog box appears.
Step 2![]() Click OK to reset the password to the default.
Click OK to reset the password to the default.
A dialog box displays the success or failure of the password reset.
Step 3![]() Click Close to close the dialog box.
Click Close to close the dialog box.
Reloading or Resetting the Module
To reload or reset the module, enter one of the following commands at the ASA CLI.
Detailed Steps
Monitoring the ASA IPS module
See the Intrusion Prevention Tab in the general operations configuration guide.
Feature History for the ASA IPS module
Table 28-2 lists each feature change and the platform release in which it was implemented. ASDM is backwards-compatible with multiple platform releases, so the specific ASDM release in which support was added is not listed.
 Feedback
Feedback