- Information About the ASA CX Module
- Licensing Requirements for the ASA CX Module
- Prerequisites
- Guidelines and Limitations
- Default Settings
- Configuring the ASA CX Module
- Task Flow for the ASA CX Module
- Connecting the ASA CX Management Interface
- (ASA 5512-X through ASA 5555-X; May Be Required) Installing the Software Module
- (ASA 5585-X) Changing the ASA CX Management IP Address
- Configuring Basic ASA CX Settings at the ASA CX CLI
- Configuring the Security Policy on the ASA CX Module Using PRSM
- (Optional) Configuring the Authentication Proxy Port
- Redirecting Traffic to the ASA CX Module
ASA CX Module
This chapter describes how to configure the ASA CX module that runs on the ASA.
Information About the ASA CX Module
The ASA CX module lets you enforce security based on the full context of a situation. This context includes the identity of the user (who), the application or website that the user is trying to access (what), the origin of the access attempt (where), the time of the attempted access (when), and the properties of the device used for the access (how). With the ASA CX module, you can extract the full context of a flow and enforce granular policies such as permitting access to Facebook but denying access to games on Facebook, or permitting finance employees access to a sensitive enterprise database but denying the same access to other employees.
- How the ASA CX Module Works with the ASA
- Monitor-Only Mode
- Information About ASA CX Management
- Information About Authentication Proxy
- Information About VPN and the ASA CX Module
- Compatibility with ASA Features
How the ASA CX Module Works with the ASA
The ASA CX module runs a separate application from the ASA. The ASA CX module includes external management interface(s) so you can connect to the ASA CX module directly. Any data interfaces on the ASA CX module are used for ASA traffic only.
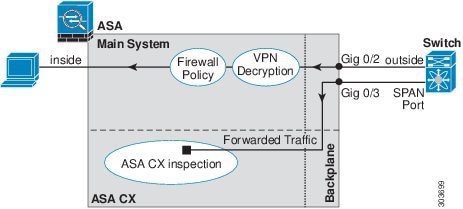
Traffic goes through the firewall checks before being forwarded to the ASA CX module. When you identify traffic for ASA CX inspection on the ASA, traffic flows through the ASA and the ASA CX module as follows:
2.![]() Incoming VPN traffic is decrypted.
Incoming VPN traffic is decrypted.
3.![]() Firewall policies are applied.
Firewall policies are applied.
4.![]() Traffic is sent to the ASA CX module.
Traffic is sent to the ASA CX module.
5.![]() The ASA CX module applies its security policy to the traffic, and takes appropriate actions.
The ASA CX module applies its security policy to the traffic, and takes appropriate actions.
6.![]() Valid traffic is sent back to the ASA; the ASA CX module might block some traffic according to its security policy, and that traffic is not passed on.
Valid traffic is sent back to the ASA; the ASA CX module might block some traffic according to its security policy, and that traffic is not passed on.
7.![]() Outgoing VPN traffic is encrypted.
Outgoing VPN traffic is encrypted.
Figure 27-1 shows the traffic flow when using the ASA CX module. In this example, the ASA CX module automatically blocks traffic that is not allowed for a certain application. All other traffic is forwarded through the ASA.
Figure 27-1 ASA CX Module Traffic Flow in the ASA


Note![]() If you have a connection between hosts on two ASA interfaces, and the ASA CX service policy is only configured for one of the interfaces, then all traffic between these hosts is sent to the ASA CX module, including traffic originating on the non-ASA CX interface (because the feature is bidirectional). However, the ASA only performs the authentication proxy on the interface to which the service policy is applied, because authentication proxy is applied only to ingress traffic (see Information About Authentication Proxy).
If you have a connection between hosts on two ASA interfaces, and the ASA CX service policy is only configured for one of the interfaces, then all traffic between these hosts is sent to the ASA CX module, including traffic originating on the non-ASA CX interface (because the feature is bidirectional). However, the ASA only performs the authentication proxy on the interface to which the service policy is applied, because authentication proxy is applied only to ingress traffic (see Information About Authentication Proxy).
Monitor-Only Mode
For demonstration purposes, you can configure a service policy or a traffic-forwarding interface in monitor-only mode.
For guidelines and limitations for monitor-only mode, see Guidelines and Limitations.
Service Policy in Monitor-Only Mode
For testing and demonstration purposes, you can configure the ASA to send a duplicate stream of read-only traffic to the ASA CX module, so you can see how the module inspects the traffic without affecting the ASA traffic flow. In this mode, the ASA CX module inspects the traffic as usual, makes policy decisions, and generates events. However, because the packets are read-only copies, the module actions do not affect the actual traffic. Instead, the module drops the copies after inspection. Figure 27-2 shows the ASA CX module in monitor-only mode.
Figure 27-2 ASA CX Monitor-Only Mode

Traffic-Forwarding Interface in Monitor-Only Mode
You can alternatively configure ASA interfaces to be traffic-forwarding interfaces, where all traffic received is forwarded directly to the ASA CX module without any ASA processing. For testing and demonstration purposes, traffic-forwarding removes the extra complication of ASA processing. Traffic-forwarding is only supported in monitor-only mode, so the ASA CX module drops the traffic after inspecting it. Figure 27-3 shows the ASA GigabitEthernet 0/3 interface configured for traffic-forwarding. That interface is connected to a switch SPAN port so the ASA CX module can inspect all of the network traffic.
Figure 27-3 ASA CX Traffic-Forwarding
Information About ASA CX Management
Initial Configuration
For initial configuration, you must use the CLI on the ASA CX module to run the setup command and configure other optional settings.
To access the CLI, you can use the following methods:
–![]() ASA CX console port—The ASA CX console port is a separate external console port.
ASA CX console port—The ASA CX console port is a separate external console port.
–![]() ASA CX Management 1/0 interface using SSH—You can connect to the default IP address (192.168.8.8), or you can use ASDM to change the management IP address and then connect using SSH. The ASA CX management interface is a separate external Gigabit Ethernet interface.
ASA CX Management 1/0 interface using SSH—You can connect to the default IP address (192.168.8.8), or you can use ASDM to change the management IP address and then connect using SSH. The ASA CX management interface is a separate external Gigabit Ethernet interface.

Note![]() You cannot access the ASA CX hardware module CLI over the ASA backplane using the session command.
You cannot access the ASA CX hardware module CLI over the ASA backplane using the session command.
–![]() ASA session over the backplane—If you have CLI access to the ASA, then you can session to the module and access the module CLI.
ASA session over the backplane—If you have CLI access to the ASA, then you can session to the module and access the module CLI.
–![]() ASA CX Management 0/0 interface using SSH—You can connect to the default IP address (192.168.1.2), or you can use ASDM to change the management IP address and then connect using SSH. These models run the ASA CX module as a software module. The ASA CX management interface shares the Management 0/0 interface with the ASA. Separate MAC addresses and IP addresses are supported for the ASA and ASA CX module. You must perform configuration of the ASA CX IP address within the ASA CX operating system (using the CLI or ASDM). However, physical characteristics (such as enabling the interface) are configured on the ASA. You can remove the ASA interface configuration (specifically the interface name) to dedicate this interface as an ASA CX-only interface. This interface is management-only.
ASA CX Management 0/0 interface using SSH—You can connect to the default IP address (192.168.1.2), or you can use ASDM to change the management IP address and then connect using SSH. These models run the ASA CX module as a software module. The ASA CX management interface shares the Management 0/0 interface with the ASA. Separate MAC addresses and IP addresses are supported for the ASA and ASA CX module. You must perform configuration of the ASA CX IP address within the ASA CX operating system (using the CLI or ASDM). However, physical characteristics (such as enabling the interface) are configured on the ASA. You can remove the ASA interface configuration (specifically the interface name) to dedicate this interface as an ASA CX-only interface. This interface is management-only.
Policy Configuration and Management
After you perform initial configuration, configure the ASA CX policy using Cisco Prime Security Manager (PRSM). Then configure the ASA policy for sending traffic to the ASA CX module using ASDM or the ASA CLI.

Note![]() When using PRSM in multiple device mode, you can configure the ASA policy for sending traffic to the ASA CX module within PRSM, instead of using ASDM or the ASA CLI. Using PRSM lets you consolodate management to a single management system. However, PRSM has some limitations when configuring the ASA service policy; see the ASA CX user guide for more information.
When using PRSM in multiple device mode, you can configure the ASA policy for sending traffic to the ASA CX module within PRSM, instead of using ASDM or the ASA CLI. Using PRSM lets you consolodate management to a single management system. However, PRSM has some limitations when configuring the ASA service policy; see the ASA CX user guide for more information.
Information About Authentication Proxy
When the ASA CX needs to authenticate an HTTP user (to take advantage of identity policies), you must configure the ASA to act as an authentication proxy: the ASA CX module redirects authentication requests to the ASA interface IP address/proxy port. By default, the port is 885 (user configurable). Configure this feature as part of the service policy to divert traffic from the ASA to the ASA CX module. If you do not enable the authentication proxy, only passive authentication is available.

Note![]() If you have a connection between hosts on two ASA interfaces, and the ASA CX service policy is only configured for one of the interfaces, then all traffic between these hosts is sent to the ASA CX module, including traffic orginiating on the non-ASA CX interface (the feature is bidirectional). However, the ASA only performs the authentication proxy on the interface to which the service policy is applied, because this feature is ingress-only.
If you have a connection between hosts on two ASA interfaces, and the ASA CX service policy is only configured for one of the interfaces, then all traffic between these hosts is sent to the ASA CX module, including traffic orginiating on the non-ASA CX interface (the feature is bidirectional). However, the ASA only performs the authentication proxy on the interface to which the service policy is applied, because this feature is ingress-only.
Information About VPN and the ASA CX Module
The ASA includes VPN client and user authentication metadata from the Cisco AnyConnect client when forwarding traffic to the ASA CX module, which allows the ASA CX module to include this information as part of its policy lookup criteria. The VPN metadata is sent only at VPN tunnel establishment time along with a type-length-value (TLV) containing the session ID. The ASA CX module caches the VPN metadata for each session. Each tunneled connection sends the session ID so the ASA CX module can look up that session’s metadata.
Compatibility with ASA Features
The ASA includes many advanced application inspection features, including HTTP inspection. However, the ASA CX module provides more advanced HTTP inspection than the ASA provides, as well as additional features for other applications, including monitoring and controlling application usage.
To take full advantage of the ASA CX module features, see the following guidelines for traffic that you send to the ASA CX module:
- Do not configure ASA inspection on HTTP traffic.
- Do not configure Cloud Web Security (ScanSafe) inspection. If you configure both the ASA CX action and Cloud Web Security inspection for the same traffic, the ASA only performs the ASA CX action.
- Other application inspections on the ASA are compatible with the ASA CX module, including the default inspections.
- Do not enable the Mobile User Security (MUS) server; it is not compatible with the ASA CX module.
- Do not enable ASA clustering; it is not compatible with the ASA CX module.
- If you enable failover, when the ASA fails over, any existing ASA CX flows are transferred to the new ASA, but the traffic is allowed through the ASA without being acted upon by the ASA CX module. Only new flows recieved by the new ASA are acted upon by the ASA CX module.
- (9.1(1) and earlier) Does not support NAT 64. In 9.1(2) and later, NAT 64 is supported.
Licensing Requirements for the ASA CX Module
|
|
|
|---|---|
The ASA CX module and PRSM require additional licenses. See the ASA CX documentation for more information.
Prerequisites
To use PRSM to configure the ASA, you need to install a certificate on the ASA for secure communications. By default, the ASA generates a self-signed certificate. However, this certificate can cause browser prompts asking you to verify the certificate because the publisher is unknown. To avoid these browser prompts, you can instead install a certificate from a known certificate authority (CA). If you request a certificate from a CA, be sure the certificate type is both a server authentication certificate and a client authentication certificate. See the general operations configuration guide for more information.
Guidelines and Limitations
(9.1(2) and earlier) Supported in single context mode only. Does not support multiple context mode.
(9.1(3) and later) Supported in multiple context mode. See the following guidelines:
- The ASA CX module itself (configured in PRSM) is a single context mode device; the context-specific traffic coming from the ASA is checked against the common ASA CX policy.
- For ASA CX module support, you cannot use the same IP addresses in multiple contexts; each context must include unique networks.
Supported in routed and transparent firewall mode. Traffic-forwarding interfaces are only supported in transparent mode.
Does not support failover directly; when the ASA fails over, any existing ASA CX flows are transferred to the new ASA, but the traffic is allowed through the ASA without being inspected by the ASA CX.
- Supports IPv6.
- (9.1(1) and earlier) Does not support NAT 64. In 9.1(2) and later, NAT 64 is supported.
- Supported only on the ASA 5585-X and 5512-X through ASA 5555-X. See the Cisco ASA Compatibility Matrix for more information:
http://www.cisco.com/en/US/docs/security/asa/compatibility/asamatrx.html
- For the 5512-X through ASA 5555-X, you must install a Cisco solid state drive (SSD). For more information, see the ASA 5500-X hardware guide.
- You cannot configure both monitor-only mode and normal inline mode at the same time on the ASA. Only one type of security policy is allowed. In multiple context mode, you cannot configure monitor-only mode for some contexts, and regular inline mode for others.
- The following features are not supported in monitor-only mode:
- The ASA CX does not perform packet buffering in monitor-only mode, and events will be generated on a best-effort basis. For example, some events, such as ones with long URLs spanning packet boundaries, may be impacted by the lack of buffering.
- Be sure to configure both the ASA policy and the ASA CX to have matching modes: both in monitor-only mode, or both in normal inline mode.
Additional guidelines for traffic-forwarding interfaces:
- The ASA must be in transparent mode.
- You can configure up to 4 interfaces as traffic-forwarding interfaces. Other ASA interfaces can be used as normal.
- Traffic-forwarding interfaces must be physical interfaces, not VLANs or BVIs. The physical interface also cannot have any VLANs associated with it.
- Traffic-forwarding interfaces cannot be used for ASA traffic; you cannot name them or configure them for ASA features, including failover or management-only.
- You cannot configure both a traffic-forwarding interface and a service policy for ASA CX traffic.
Additional Guidelines and Limitations
- See Compatibility with ASA Features.
- You cannot change the software type installed on the hardware module; if you purchase an ASA CX module, you cannot later install other software on it.
Default Settings
Table 27-1 lists the default settings for the ASA CX module.
|
|
|
|---|---|
ASA 5585-X: Management 1/0 192.168.8.8/24 ASA 5512-X through ASA 5555-X: Management 0/0 192.168.1.2/24 |
|
Configuring the ASA CX Module
This section describes how to configure the ASA CX module.
- Task Flow for the ASA CX Module
- Connecting the ASA CX Management Interface
- (ASA 5585-X) Changing the ASA CX Management IP Address
- (ASA 5512-X through ASA 5555-X; May Be Required) Installing the Software Module
- Configuring Basic ASA CX Settings at the ASA CX CLI
- Configuring the Security Policy on the ASA CX Module Using PRSM
- Redirecting Traffic to the ASA CX Module
Task Flow for the ASA CX Module
Configuring the ASA CX module is a process that includes configuration of the ASA CX security policy on the ASA CX module and then configuration of the ASA to send traffic to the ASA CX module. To configure the ASA CX module, perform the following steps:
Step 1![]() Cable the ASA CX management interfaces interface. See Connecting the ASA CX Management Interface.
Cable the ASA CX management interfaces interface. See Connecting the ASA CX Management Interface.
Step 2![]() (ASA 5512-X through ASA 5555-X; May be required) Install the software module. See (ASA 5512-X through ASA 5555-X; May Be Required) Installing the Software Module.
(ASA 5512-X through ASA 5555-X; May be required) Install the software module. See (ASA 5512-X through ASA 5555-X; May Be Required) Installing the Software Module.
Step 3![]() (ASA 5585-X) Configure the ASA CX module management IP address for initial SSH access. See (ASA 5585-X) Changing the ASA CX Management IP Address.
(ASA 5585-X) Configure the ASA CX module management IP address for initial SSH access. See (ASA 5585-X) Changing the ASA CX Management IP Address.
Step 4![]() On the ASA CX module, configure basic settings. You must use the CLI to configure these settings. See Configuring Basic ASA CX Settings at the ASA CX CLI.
On the ASA CX module, configure basic settings. You must use the CLI to configure these settings. See Configuring Basic ASA CX Settings at the ASA CX CLI.
Step 5![]() On the ASA CX module, configure the security policy using PRSM. See Configuring the Security Policy on the ASA CX Module Using PRSM.
On the ASA CX module, configure the security policy using PRSM. See Configuring the Security Policy on the ASA CX Module Using PRSM.
Step 6![]() (Optional) On the ASA, configure the authentication proxy port. See (Optional) Configuring the Authentication Proxy Port.
(Optional) On the ASA, configure the authentication proxy port. See (Optional) Configuring the Authentication Proxy Port.
Step 7![]() On the ASA, identify traffic to divert to the ASA CX module. See Redirecting Traffic to the ASA CX Module.
On the ASA, identify traffic to divert to the ASA CX module. See Redirecting Traffic to the ASA CX Module.

Note![]() When using PRSM in multiple device mode, you can configure the ASA policy for sending traffic to the ASA CX module within PRSM, instead of using ASDM or the ASA CLI. However, PRSM has some limitations when configuring the ASA service policy; see the ASA CX user guide for more information.
When using PRSM in multiple device mode, you can configure the ASA policy for sending traffic to the ASA CX module within PRSM, instead of using ASDM or the ASA CLI. However, PRSM has some limitations when configuring the ASA service policy; see the ASA CX user guide for more information.
Connecting the ASA CX Management Interface
In addition to providing management access to the ASA CX module, the ASA CX management interface needs access to an HTTP proxy server or a DNS server and the Internet for signature updates and more. This section describes recommended network configurations. Your network may differ.
ASA 5585-X (Hardware Module)
The ASA CX module includes a separate management interface from the ASA. For initial setup, you can connect with SSH to the ASA CX Management 1/0 interface using the default IP address (192.168.8.8/24). If you cannot use the default IP address, you can either use the console port or use ASDM to change the management IP address so you can use SSH.

If you have an inside router, you can route between the management network, which can include both the ASA Management 0/0 and ASA CX Management 1/0 interfaces, and the ASA inside network for Internet access. Be sure to also add a route on the ASA to reach the Management network through the inside router.

If you do not have an inside router
If you have only one inside network, then you cannot also have a separate management network, which would require an inside router to route between the networks. In this case, you can manage the ASA from the inside interface instead of the Management 0/0 interface. Because the ASA CX module is a separate device from the ASA, you can configure the ASA CX Management 1/0 address to be on the same network as the inside interface.

ASA 5512-X through ASA 5555-X (Software Module)
These models run the ASA CX module as a software module, and the ASA CX management interface shares the Management 0/0 interface with the ASA.
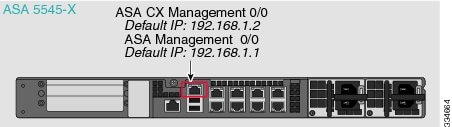
If you have an inside router, you can route between the Management 0/0 network, which includes both the ASA and ASA CX management IP addresses, and the inside network for Internet access. Be sure to also add a route on the ASA to reach the Management network through the inside router.

If you do not have an inside router
If you have only one inside network, then you cannot also have a separate management network. In this case, you can manage the ASA from the inside interface instead of the Management 0/0 interface. If you remove the ASA-configured name from the Management 0/0 interface, you can still configure the ASA CX IP address for that interface. Because the ASA CX module is essentially a separate device from the ASA, you can configure the ASA CX management address to be on the same network as the inside interface.


Note![]() You must remove the ASA-configured name for Management 0/0; if it is configured on the ASA, then the ASA CX address must be on the same network as the ASA, and that excludes any networks already configured on other ASA interfaces. If the name is not configured, then the ASA CX address can be on any network, for example, the ASA inside network.
You must remove the ASA-configured name for Management 0/0; if it is configured on the ASA, then the ASA CX address must be on the same network as the ASA, and that excludes any networks already configured on other ASA interfaces. If the name is not configured, then the ASA CX address can be on any network, for example, the ASA inside network.
What to Do Next
- Configure the ASA CX management IP address. See (ASA 5585-X) Changing the ASA CX Management IP Address.
(ASA 5512-X through ASA 5555-X; May Be Required) Installing the Software Module
If you purchase the ASA with the ASA CX module, the module software and required solid state drive(s) (SSDs) come pre-installed and ready to go. If you want to add the ASA CX to an existing ASA, or need to replace the SSD, you need to install the ASA CX boot software and partition the SSD according to this procedure. To physically install the SSD, see the ASA hardware guide.

Note![]() For the ASA 5585-X hardware module, you must install or upgrade your image from within the ASA CX module. See the ASA CX module documentation for more information.
For the ASA 5585-X hardware module, you must install or upgrade your image from within the ASA CX module. See the ASA CX module documentation for more information.
Prerequisites
Detailed Steps
Step 1![]() Download the ASA CX boot software from Cisco.com to your computer. If you have a Cisco.com login, you can obtain the boot software from the following website:
Download the ASA CX boot software from Cisco.com to your computer. If you have a Cisco.com login, you can obtain the boot software from the following website:
http://www.cisco.com/cisco/software/release.html?mdfid=284325223&softwareid=284399946
The boot software lets you set basic ASA CX network configuration, partition the SSD, and download the larger system software from a server of your choice to the SSD.
Step 2![]() Download the ASA CX system software from Cisco.com to an HTTP, HTTPS, or FTP server accessible from the ASA CX management interface. If you have a Cisco.com login, you can obtain the boot software from the following website:
Download the ASA CX system software from Cisco.com to an HTTP, HTTPS, or FTP server accessible from the ASA CX management interface. If you have a Cisco.com login, you can obtain the boot software from the following website:
http://www.cisco.com/cisco/software/release.html?mdfid=284325223&softwareid=284399946
Step 3![]() In ASDM, choose Tools > File Management, and then choose File Transfer > Between Local PC and Flash. Transfer the boot software to disk0 on the ASA. Do not transfer the system
In ASDM, choose Tools > File Management, and then choose File Transfer > Between Local PC and Flash. Transfer the boot software to disk0 on the ASA. Do not transfer the system![]() software; it is downloaded later to the SSD.
software; it is downloaded later to the SSD.
Step 4![]() Connect to the ASA CLI, and enter privileged EXEC mode. See “Getting Started” chapter in the general operations configuration guide to access the ASA CLI.
Connect to the ASA CLI, and enter privileged EXEC mode. See “Getting Started” chapter in the general operations configuration guide to access the ASA CLI.
Step 5![]() If you are replacing the IPS module with the ASA CX module, shut down and uninstall the IPS module, and then reload the ASA:
If you are replacing the IPS module with the ASA CX module, shut down and uninstall the IPS module, and then reload the ASA:
After the ASA reloads, reconnect to the ASA CLI.
Step 6![]() Set the ASA CX module boot image location in ASA disk0 by entering the following command:
Set the ASA CX module boot image location in ASA disk0 by entering the following command:
Step 7![]() Load the ASA CX boot image by entering the following command:
Load the ASA CX boot image by entering the following command:
Step 8![]() Wait approximately 5 minutes for the ASA CX module to boot up, and then open a console session to the now-running ASA CX boot image. The default username is admin and the default password is Admin123.
Wait approximately 5 minutes for the ASA CX module to boot up, and then open a console session to the now-running ASA CX boot image. The default username is admin and the default password is Admin123.
Step 10![]() Perform the basic network setup using the setup command according to the Configuring Basic ASA CX Settings at the ASA CX CLI (do not exit the ASA CX CLI), and then return to this procedure to install the software image.
Perform the basic network setup using the setup command according to the Configuring Basic ASA CX Settings at the ASA CX CLI (do not exit the ASA CX CLI), and then return to this procedure to install the software image.
Step 11![]() Install the system software from the server:
Install the system software from the server:
The following command installs the asacx-sys-9.1.1.pkg system software.
Step 12![]() Press Enter to reboot the ASA CX module. Rebooting the module closes the console session. Allow 10 or more minutes for application component installation and for the ASA CX services to start.
Press Enter to reboot the ASA CX module. Rebooting the module closes the console session. Allow 10 or more minutes for application component installation and for the ASA CX services to start.
(ASA 5585-X) Changing the ASA CX Management IP Address
If you cannot use the default management IP address (192.168.8.8), then you can set the management IP address from the ASA. After you set the management IP address, you can access the ASA CX module using SSH to perform initial setup.

Note![]() For a software module, you can access the ASA CX CLI to perform setup by sessioning from the ASA CLI; you can then set the ASA CX management IP address as part of setup. See Configuring Basic ASA CX Settings at the ASA CX CLI.
For a software module, you can access the ASA CX CLI to perform setup by sessioning from the ASA CLI; you can then set the ASA CX management IP address as part of setup. See Configuring Basic ASA CX Settings at the ASA CX CLI.
Guidelines
In multiple context mode, perform this procedure in the system execution space.
Detailed Steps
Step 1![]() In the System, choose Tools > Command Line Interface.
In the System, choose Tools > Command Line Interface.
Step 2![]() Enter the following command:
Enter the following command:
|
|
|
|---|---|
session 1 do setup host ip ip_address / mask , gateway_ip |
Step 1![]() In ASDM, choose Wizards > Startup Wizard.
In ASDM, choose Wizards > Startup Wizard.
Step 2![]() Click Next to advance through the initial screens until you reach the ASA CX Basic Configuration screen.
Click Next to advance through the initial screens until you reach the ASA CX Basic Configuration screen.

Step 3![]() Enter the new management IP address, subnet mask, and default gateway.
Enter the new management IP address, subnet mask, and default gateway.
Step 4![]() (Optional) Change the Auth Proxy Port. You can set this later if desired. See (Optional) Configuring the Authentication Proxy Port for more information.
(Optional) Change the Auth Proxy Port. You can set this later if desired. See (Optional) Configuring the Authentication Proxy Port for more information.
Step 5![]() Click Finish to skip the remaining screens, or click Next to advance through the remaining screens and complete the wizard.
Click Finish to skip the remaining screens, or click Next to advance through the remaining screens and complete the wizard.
Configuring Basic ASA CX Settings at the ASA CX CLI
You must configure basic network settings and other parameters on the ASA CX module before you can configure your security policy.
Detailed Steps
Step 1![]() Do one of the following:
Do one of the following:
- (All models) Use SSH to connect to the ASA CX management IP address.
- (ASA 5512-X through ASA 5555-X) Open a console session to the module from the ASA CLI (see the “Getting Started” chapter in the general operations configuration guide to access the ASA CLI). In multiple context mode, session from the system execution space.
Step 2![]() Log in with the username admin and the password Admin123. You will change the password as part of this procedure.
Log in with the username admin and the password Admin123. You will change the password as part of this procedure.
Step 3![]() Enter the following command:
Enter the following command:
You are prompted through the setup wizard. The following example shows a typical path through the wizard; if you enter Y instead of N at a prompt, you will be able to configure some additional settings. This example shows how to configure both IPv4 and IPv6 static addresses. You can configure IPv6 stateless auto configuration by answering N when asked if you want to configure a static IPv6 address.
Step 4![]() After you complete the final prompt, you are presented with a summary of the settings. Look over the summary to verify that the values are correct, and enter Y to apply your changed configuration. Enter N to cancel your changes.
After you complete the final prompt, you are presented with a summary of the settings. Look over the summary to verify that the values are correct, and enter Y to apply your changed configuration. Enter N to cancel your changes.

Note![]() If you change the host name, the prompt does not show the new name until you log out and log back in.
If you change the host name, the prompt does not show the new name until you log out and log back in.
Step 5![]() If you do not use NTP, configure the time settings. The default time zone is the UTC time zone. Use the show time command to see the current settings. You can use the following commands to change time settings:
If you do not use NTP, configure the time settings. The default time zone is the UTC time zone. Use the show time command to see the current settings. You can use the following commands to change time settings:
Step 6![]() Change the admin password by entering the following command:
Change the admin password by entering the following command:
Step 7![]() Enter the exit command to log out.
Enter the exit command to log out.
Configuring the Security Policy on the ASA CX Module Using PRSM
This section describes how to launch PRSM to configure the ASA CX module application. For details on using PRSM to configure your ASA CX security policy, see the ASA CX user guide.
Detailed Steps
You can launch PRSM from your web browser, or you can launch it from ASDM.
Where the ASA CX management IP address is the one you set in the Configuring Basic ASA CX Settings at the ASA CX CLI.
- Launch PRSM from ASDM by choosing Home > ASA CX Status, and clicking the Connect to the ASA CX application link.

What to Do Next
- (Optional) Configure the authentication proxy port. See (Optional) Configuring the Authentication Proxy Port.
- Redirect traffic to the ASA CX module. See Redirecting Traffic to the ASA CX Module.
(Optional) Configuring the Authentication Proxy Port
The default authentication port is 885. To change the authentication proxy port, perform the following steps. For more information about the authentication proxy, see Information About Authentication Proxy.

Note![]() (Single mode) You can also set the port as part of the ASDM startup wizard. See (ASA 5585-X) Changing the ASA CX Management IP Address.
(Single mode) You can also set the port as part of the ASDM startup wizard. See (ASA 5585-X) Changing the ASA CX Management IP Address.
Guidelines
In multiple context mode, perform this procedure within each security context.
Detailed Steps
Step 1![]() In ASDM, choose Configuration > Firewall > Advanced > ASA CX Auth Proxy.
In ASDM, choose Configuration > Firewall > Advanced > ASA CX Auth Proxy.

Step 2![]() Enter a port greater than 1024. The default is 885.
Enter a port greater than 1024. The default is 885.
Redirecting Traffic to the ASA CX Module
You can redirect traffic to the ASA CX module by creating a service policy that identifies specific traffic. For demonstration purposes only, you can also enable monitor-only mode for the service policy, which forwards a copy of traffic to the ASA CX module, while the original traffic remains unaffected.
Another option for demonstration purposes is to configure a traffic-forwarding interface instead of a service policy in monitor-only mode. The traffic-forwarding interface sends all traffic directly to the ASA CX module, bypassing the ASA.
Creating the ASA CX Service Policy
This section identifies traffic to redirect from the ASA to the ASA CX module. Configure this policy on the ASA. If you want to use a traffic-forwarding interface for demonstration purposes, skip this procedure and see Configuring Traffic-Forwarding Interfaces (Monitor-Only Mode) instead.

Note![]() When using PRSM in multiple device mode, you can configure the ASA policy for sending traffic to the ASA CX module within PRSM, instead of using ASDM or the ASA CLI. However, PRSM has some limitations when configuring the ASA service policy; see the ASA CX user guide for more information.
When using PRSM in multiple device mode, you can configure the ASA policy for sending traffic to the ASA CX module within PRSM, instead of using ASDM or the ASA CLI. However, PRSM has some limitations when configuring the ASA service policy; see the ASA CX user guide for more information.
Prerequisites
- If you enable the authentication proxy on the ASA using this procedure, be sure to also configure a directory realm for authentication on the ASA CX module. See the ASA CX user guide for more information.
- If you have an active service policy redirecting traffic to an IPS module (that you replaced with the ASA CX), you must remove that policy before you configure the ASA CX service policy.
- Be sure to configure both the ASA policy and the ASA CX to have matching modes: both in monitor-only mode, or both in normal inline mode.
- In multiple context mode, perform this procedure within each security context.
Detailed Steps
Step 1![]() Choose Configuration > Firewall > Service Policy Rules.
Choose Configuration > Firewall > Service Policy Rules.

Step 2![]() Choose Add > Add Service Policy Rule. The Add Service Policy Rule Wizard - Service Policy dialog box appears.
Choose Add > Add Service Policy Rule. The Add Service Policy Rule Wizard - Service Policy dialog box appears.
Step 3![]() Complete the Service Policy dialog box as desired. See the ASDM online help for more information about these screens.
Complete the Service Policy dialog box as desired. See the ASDM online help for more information about these screens.
Step 4![]() Click Next. The Add Service Policy Rule Wizard - Traffic Classification Criteria dialog box appears.
Click Next. The Add Service Policy Rule Wizard - Traffic Classification Criteria dialog box appears.
Step 5![]() Complete the Traffic Classification Criteria dialog box as desired. See the ASDM online help for more information about these screens.
Complete the Traffic Classification Criteria dialog box as desired. See the ASDM online help for more information about these screens.
Step 6![]() Click Next to show the Add Service Policy Rule Wizard - Rule Actions dialog box.
Click Next to show the Add Service Policy Rule Wizard - Rule Actions dialog box.
Step 7![]() Click the ASA CX Inspection tab.
Click the ASA CX Inspection tab.

Step 8![]() Check the Enable ASA CX for this traffic flow check box.
Check the Enable ASA CX for this traffic flow check box.
Step 9![]() In the If ASA CX Card Fails area, click one of the following:
In the If ASA CX Card Fails area, click one of the following:
Step 10![]() (Optional) To enable the authentication proxy, which is required for active authentication, check the Enable Auth Proxy check box. This option is not available in monitor-only mode.
(Optional) To enable the authentication proxy, which is required for active authentication, check the Enable Auth Proxy check box. This option is not available in monitor-only mode.
Step 11![]() (Optional) For demonstration purposes only, check the Monitor-only check box to send a read-only copy of traffic to the ASA CX module. See Monitor-Only Mode for more information.
(Optional) For demonstration purposes only, check the Monitor-only check box to send a read-only copy of traffic to the ASA CX module. See Monitor-Only Mode for more information.

Note![]() You must configure all classes and policies to be either in monitor-only mode, or in normal inline mode; you cannot mix both modes on the same ASA.
You must configure all classes and policies to be either in monitor-only mode, or in normal inline mode; you cannot mix both modes on the same ASA.
Step 12![]() Click OK and then Apply.
Click OK and then Apply.
Step 13![]() Repeat this procedure to configure additional traffic flows as desired.
Repeat this procedure to configure additional traffic flows as desired.
Configuring Traffic-Forwarding Interfaces (Monitor-Only Mode)
This section configures traffic-forwarding interfaces, where all traffic is forwarded directly to the ASA CX module. This method is for demonstration purposes only. For a normal ASA CX service policy, see Creating the ASA CX Service Policy.
For more information see Monitor-Only Mode. See also the Guidelines and Limitations for guidelines and limitations specific to traffic-forwarding interfaces.
You can only configure this feature at the CLI; you can use the Command Line Interface tool.
Prerequisites
Detailed Steps
Step 1![]() Choose Tools > Command Line Interface.
Choose Tools > Command Line Interface.
Step 2![]() Click the Multiple Line radio button.
Click the Multiple Line radio button.
Step 3![]() Enter the following commands:
Enter the following commands:
Step 4![]() Repeat for any additional interfaces.
Repeat for any additional interfaces.
Examples
The following example makes GigabitEthernet 0/5 a traffic-forwarding interface:

Managing the ASA CX Module
This section includes procedures that help you manage the module.
- Resetting the Password
- Reloading or Resetting the Module
- Shutting Down the Module
- (ASA 5512-X through ASA 5555-X) Uninstalling a Software Module Image
- (ASA 5512-X through ASA 5555-X) Sessioning to the Module From the ASA
Resetting the Password
You can reset the module password to the default. For the user admin, the default password is Admin123. After resetting the password, you should change it to a unique value using the module application.
Resetting the module password causes the module to reboot. Services are not available while the module is rebooting.
If you cannot connect to ASDM with the new password, restart ASDM and try to log in again. If you defined a new password and still have an existing password in ASDM that is different from the new password, clear the password cache by choosing File > Clear ASDM Password Cache, then restart ASDM and try to log in again.
To reset the module password to the default of Admin123, perform the following steps.
Guidelines
In multiple context mode, perform this procedure in the system execution space.
Detailed Steps
Step 1![]() From the ASDM menu bar, choose Tools > ASA CX Password Reset.
From the ASDM menu bar, choose Tools > ASA CX Password Reset.
The Password Reset confirmation dialog box appears.

Step 2![]() Click OK to reset the password to the default Admin123.
Click OK to reset the password to the default Admin123.
A dialog box displays the success or failure of the password reset.
Step 3![]() Click Close to close the dialog box.
Click Close to close the dialog box.
Reloading or Resetting the Module
To reload or reset the module, enter one of the following commands at the ASA CLI.
Guidelines
In multiple context mode, perform this procedure in the system execution space.
Detailed Steps
Shutting Down the Module
Shutting down the module software prepares the module to be safely powered off without losing configuration data. Note : If you reload the ASA, the module is not automatically shut down, so we recommend shutting down the module before reloading the ASA. To gracefully shut down the module, perform the following steps at the ASA CLI.
Guidelines
In multiple context mode, perform this procedure in the system execution space.
Detailed Steps
|
|
|
|---|---|
For a hardware module (ASA 5585-X): For a software module (ASA 5512-X through ASA 5555-X): |
(ASA 5512-X through ASA 5555-X) Uninstalling a Software Module Image
To uninstall a software module image and associated configuration, perform the following steps.
Guidelines
In multiple context mode, perform this procedure in the system execution space.
Detailed Steps
(ASA 5512-X through ASA 5555-X) Sessioning to the Module From the ASA
To access the ASA CX software module CLI from the ASA, you can session from the ASA. You can either session to the module (using Telnet) or create a virtual console session. A console session might be useful if the control plane is down and you cannot establish a Telnet session.
You may need to access the CLI if you are using multiple context mode and you need to set basic network settings using the CLI, or for troubleshooting.
Guidelines
In multiple context mode, perform this procedure in the system execution space.
Detailed Steps
Monitoring the ASA CX Module
Use Tools > Command Line Interface to use monitoring commands.
- Showing Module Status
- Showing Module Statistics
- Monitoring Module Connections
- Capturing Module Traffic
- Problems with the Authentication Proxy

Note![]() For ASA CX-related syslog messages, see the syslog messages guide. ASA CX syslog messages start with message number 429001.
For ASA CX-related syslog messages, see the syslog messages guide. ASA CX syslog messages start with message number 429001.
Showing Module Status
See the ASA CX Status Tab in the general operations configuration guide.
Showing Module Statistics
To show module statistics, enter the following command:
|
|
|
|---|---|
Displays the ASA CX statistics and status per service policy. |
Examples
The following is sample output from the show service-policy command showing the ASA CX policy and the current statistics as well as the module status when the authentication proxy is disabled:
The following is sample output from the show service-policy command showing the ASA CX policy and the current statistics as well as the module status when the authentication proxy is enabled; in this case, the proxied counters also increment:
Monitoring Module Connections
To show connections through the ASA CX module, enter one of the following commands:
Examples
The following is sample output from the show asp table classify domain cxsc command:
The following is sample output from the show asp table classify domain cxsc-auth-proxy command. For the first rule in the output, the destination “port=2000” is the auth-proxy port configured by the cxsc auth-proxy port 2000 command, and the destination “ip/id=192.168.0.100” is the ASA interface IP address.
The following is sample output from the show asp drop command. This output is just an example and lists all the possible reasons for a dropped frame or flow from the ASA CX module:
The following is sample output from the show asp event dp-cp cxsc-msg command:
The following is sample output from the show conn detail command:
Capturing Module Traffic
To configure and view packet captures for the ASA CX module, enter one of the following commands:
|
|
|
|---|---|
Captures packets between ASA CX module and the ASA on the backplane. |
|

Note![]() Captured packets contain an additional AFBP header that your PCAP viewer might not understand; be sure to use the appropriate plugin to view these packets.
Captured packets contain an additional AFBP header that your PCAP viewer might not understand; be sure to use the appropriate plugin to view these packets.
Troubleshooting the ASA CX Module
Problems with the Authentication Proxy
If you are having a problem using the authentication proxy feature, follow these steps to troubleshoot your configuration and connections:
- On the ASA, check the output of the show asp table classify domain cxsc-auth-proxy command and make sure there are rules installed and that they are correct.
- In PRSM, ensure the directory realm is created with the correct credentials and test the connection to make sure you can reach the authentication server; also ensure that a policy object or objects are configured for authentication.
2.![]() Check the output of the show service-policy cxsc command to see if any packets were proxied.
Check the output of the show service-policy cxsc command to see if any packets were proxied.
3.![]() Perform a packet capture on the backplane, and check to see if traffic is being redirected on the correct configured port. See Capturing Module Traffic. You can check the configured port using the show running-config cxsc command or the show asp table classify domain cxsc-auth-proxy command.
Perform a packet capture on the backplane, and check to see if traffic is being redirected on the correct configured port. See Capturing Module Traffic. You can check the configured port using the show running-config cxsc command or the show asp table classify domain cxsc-auth-proxy command.

Note![]() If you have a connection between hosts on two ASA interfaces, and the ASA CX service policy is only configured for one of the interfaces, then all traffic between these hosts is sent to the ASA CX module, including traffic orginiating on the non-ASA CX interface (the feature is bidirectional). However, the ASA only performs the authentication proxy on the interface to which the service policy is applied, because this feature is ingress-only.
If you have a connection between hosts on two ASA interfaces, and the ASA CX service policy is only configured for one of the interfaces, then all traffic between these hosts is sent to the ASA CX module, including traffic orginiating on the non-ASA CX interface (the feature is bidirectional). However, the ASA only performs the authentication proxy on the interface to which the service policy is applied, because this feature is ingress-only.
Example 27-1 Make sure port 2000 is used consistently:
1.![]() Check the authentication proxy port:
Check the authentication proxy port:
2.![]() Check the authentication proxy rules:
Check the authentication proxy rules:
3.![]() In the packet captures, the redirect request should be going to destination port 2000.
In the packet captures, the redirect request should be going to destination port 2000.
Feature History for the ASA CX Module
Table 27-2 lists each feature change and the platform release in which it was implemented. ASDM is backwards-compatible with multiple platform releases, so the specific ASDM release in which support was added is not listed.
 Feedback
Feedback