About Traffic Zones
This section describes how you should use traffic zones in your network.
Non-Zoned Behavior
The Adaptive Security Algorithm takes into consideration the state of a packet when deciding to permit or deny the traffic. One of the enforced parameters for the flow is that traffic enters and exits the same interface. Any traffic for an existing flow that enters a different interface is dropped by the ASA.
Traffic zones let you group multiple interfaces together so that traffic entering or exiting any interface in the zone fulfills the Adaptive Security Algorithm security checks.
Why Use Zones?
You can use zones to accommodate several routing scenarios.
Asymmetric Routing
In the following scenario, a connection was established between an inside host and an outside host through ISP 1 on the Outside1 interface. Due to asymmetric routing on the destination network, return traffic arrived from ISP 2 on the Outside2 interface.
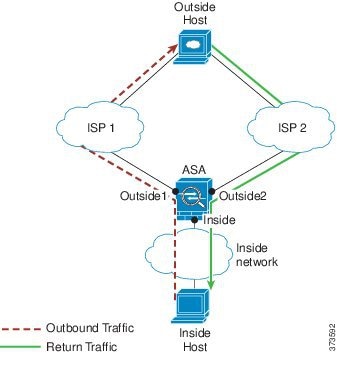
Non-Zoned Problem: The ASA maintains the connection tables on a per-interface basis. When the returning traffic arrives at Outside2, it will not match the connection table and will be dropped. For an ASA cluster, asymmetric routing when the cluster has multiple adjacencies to the same router can lead to unacceptible traffic loss.
Zoned Solution: The ASA maintains connection tables on a per-zone basis. If you group Outside1 and Outside2 into a zone, then when the returning traffic arrives at Outside2, it will match the per-zone connection table, and the connection will be allowed.
Lost Route
In the following scenario, a connection was established between an inside host and an outside host through ISP 1 on the Outside1 interface. Due to a lost or moved route between Outside1 and ISP 1, traffic needs to take a different route through ISP 2.
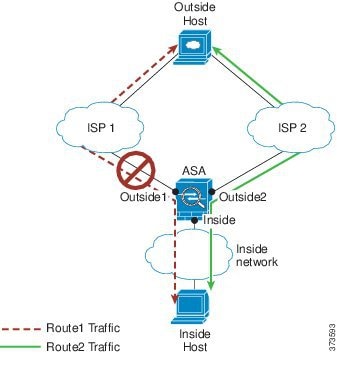
Non-Zoned Problem: The connection between the inside and outside host will be deleted; a new connection must be established using a new next-best route. For UDP, the new route will be used after a single packet drop, but for TCP, a new connection has to be reestablished.
Zoned Solution: The ASA detects the lost route and switches the flow to the new path through ISP 2. Traffic will be seamlessly forwarded without any packet drops.
Load Balancing
In the following scenario, a connection was established between an inside host and an outside host through ISP 1 on the Outside1 interface. A second connection was established through an equal cost route through ISP 2 on Outside2.
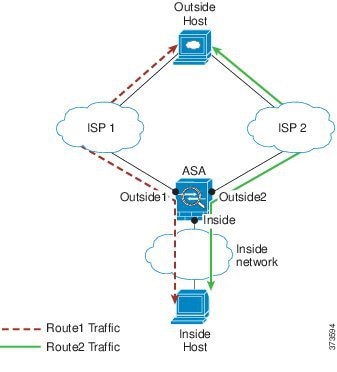
Non-Zoned Problem: Load-balancing across interfaces is not possible; you can only load-balance with equal cost routes on one interface.
Zoned Solution: The ASA load-balances connections across up to eight equal cost routes on all the interfaces in the zone.
Per-Zone Connection and Routing Tables
The ASA maintains a per-zone connection table so that traffic can arrive on any of the zone interfaces. The ASA also maintains a per-zone routing table for ECMP support.
ECMP Routing
The ASA supports Equal-Cost Multi-Path (ECMP) routing.
Non-Zoned ECMP Support
Without zones, you can have up to 8 equal cost static or dynamic routes per interface. For example, you can configure three default routes on the outside interface that specify different gateways:
route outside 0 0 10.1.1.2
route outside 0 0 10.1.1.3
route outside 0 0 10.1.1.4
In this case, traffic is load-balanced on the outside interface between 10.1.1.2, 10.1.1.3, and 10.1.1.4. Traffic is distributed among the specified gateways based on an algorithm that hashes the source and destination IP addresses, incoming interface, protocol, source and destination ports.
ECMP is not supported across multiple interfaces, so you cannot define a route to the same destination on a different interface. The following route is disallowed when configured with any of the routes above:
route outside2 0 0 10.2.1.1
Zoned ECMP Support
With zones, you can have up to 8 equal cost static or dynamic routes across up to 8 interfaces within a zone. For example, you can configure three default routes across three interfaces in the zone:
route outside1 0 0 10.1.1.2
route outside2 0 0 10.2.1.2
route outside3 0 0 10.3.1.2
Similarly, your dynamic routing protocol can automatically configure equal cost routes. The ASA load-balances traffic across the interfaces with a more robust load balancing mechanism.
When a route is lost, the ASA seamlessly moves the flow to a different route.
How Connections Are Load-Balanced
The ASA load balances connections across equal cost routes using a hash made from the packet 6-tuple (source and destination IP address, source and destination port, protocol, and ingress interface). Unless the route is lost, a connection will stay on the chosen interface for its duration.
Packets within a connection are not load-balanced across routes; a connection uses a single route unless that route is lost.
The ASA does not consider the interface bandwidth or other parameters when load balancing. You should make sure all interfaces within the same zone have the same characteristics such as MTU, bandwidth, and so on.
The load-balancing algorithm is not user configurable.
Falling Back to a Route in Another Zone
When a route is lost on an interface, if there are no other routes available within the zone, then the ASA will use a route from a different interface/zone. If this backup route is used, then you may experience packet drops as with non-zoned routing support.
Interface-Based Security Policy
Zones allow traffic to and from any interface in the zone, but the security policy itself (access rules, NAT, and so on) is still applied per interface, not per zone. If you configure the same security policy for all interfaces within the zone, then you can successfully implement ECMP and load balancing for that traffic. For more information about required parallel interface configuration, see Prerequisites for Traffic Zones.
Supported Services for Traffic Zones
The following services are supported with zones:
-
Access Rules
-
NAT
-
Service Rules, except for QoS traffic policing.
-
Routing
You can also configure to- and from-the-box services listed in To- and From-the-Box Traffic, although full zoned support is not available.
Do not configure other services (such as VPN or Botnet Traffic Filter) for interfaces in a traffic zone; they may not function or scale as expected.
 Note |
For detailed information about how to configure the security policy, see Prerequisites for Traffic Zones. |
Security Levels
The first interface that you add to a zone determines the security level of the zone. All additional interfaces must have the same security level. To change the security level for interfaces in a zone, you must remove all but one interface, and then change the security levels, and re-add the interfaces.
Primary and Current Interface for the Flow
Each connection flow is built based on the initial ingress and egress interfaces. These interfaces are the primary interfaces.
If a new egress interface is used because of route changes or asymmetric routing, then the new interfaces are the current interfaces.
Joining or Leaving a Zone
When you assign an interface to a zone, any connections on that interface are deleted. The connections must be reestablished.
If you remove an interface from a zone, any connections that have the interface as the primary interface are deleted. The connections must be reestablished. If the interface is the current interface, the ASA moves the connections back to the primary interface. The zone route table is also refreshed.
Intra-Zone Traffic
To allow traffic to enter one interface and exit another in the same zone, enable Configuration > Device Setup > Interface Settings > Interfaces > Enable traffic between two or more hosts connected to the same interface, which allows traffic to enter and exit the same interface, as well as Configuration > Device Setup > Interface Settings > Interfaces > Enable traffic between two or more interfaces which are configured with same security level, which allows traffic between same-security interfaces. Otherwise, a flow cannot be routed between two interfaces in the same zone.
To- and From-the-Box Traffic
-
You cannot add management-only or management-access interfaces to a zone.
-
For management traffic on regular interfaces in a zone, only asymmetric routing on existing flows is supported; there is no ECMP support.
-
You can configure a management service on only one zone interface, but to take advantage of asymmetric routing support, you need to configure it on all interfaces. Even when the configurations are parallel on all interfaces, ECMP is not supported.
-
The ASA supports the following to- and from-the-box services in a zone:
-
Telnet
-
SSH
-
HTTPS
-
SNMP
-
Syslog
-
Overlapping IP Addresses Within a Zone
For non-zoned interfaces, the ASA supports overlapping IP address networks on interfaces so long as you configure NAT properly. However, overlapping networks are not supported on interfaces in the same zone.

 Feedback
Feedback