URL Filtering Overview
Use the URL filtering feature to control the websites that users on your network can access:
-
Category and reputation-based URL filtering—With a URL Filtering license, you can control access to websites based on the URL’s general classification (category) and risk level (reputation). This is the recommended option.
-
Manual URL filtering—With any license, you can manually specify individual URLs, groups of URLs, and URL lists and feeds to achieve granular, custom control over web traffic. For more information, see Manual URL Filtering.
See also Blocking Traffic with Security Intelligence, a similar but different feature for blocking malicious URLs, domains, and IP addresses.
About URL Filtering with Category and Reputation
With a URL Filtering license, you can control access to websites based on the category and reputation of requested URLs:
-
Category—A general classification for the URL. For example, ebay.com belongs to the Auctions category, and monster.com belongs to the Job Search category.
A URL can belong to more than one category.
-
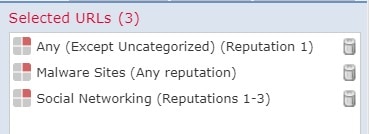
Reputation—How likely the URL is to be used for purposes that might be against your organization’s security policy. Reputations range from High Risk (level 1) to Well Known (level 5).
Benefits of Category and Reputation-Based URL Filtering
URL categories and reputations help you quickly configure URL filtering. For example, you can use access control to block high-risk URLs in the Hacking category. Or, you can use QoS to rate limit traffic from sites in the Streaming Media category. There are also categories for types of threats, such as a Spyware and Adware category.
Using category and reputation data simplifies policy creation and administration. It grants you assurance that the system controls web traffic as expected. Because Cisco continually updates its threat intelligence with new URLs, as well as new categories and risks for existing URLs, the system uses up-to-date information to filter requested URLs. Sites that (for example) represent security threats, or that serve undesirable content, may appear and disappear faster than you can update and deploy new policies.
Some examples of how the system can adapt include:
-
If an access control rule blocks all gaming sites, as new domains get registered and classified as Games, the system can block those sites automatically. Similarly, if a QoS rule rate limits all streaming media sites, the system can automatically limit traffic to new Streaming Media sites.
-
If an access control rule blocks all malware sites and a shopping page gets infected with malware, the system can recategorize the URL from Shopping to Malware Sites and block that site.
-
If an access control rule blocks high-risk social networking sites and somebody posts a link on their profile page that contains links to malicious payloads, the system can change the reputation of that page from Benign Sites to High Risk and block it.



 Feedback
Feedback