Gateway VPN Basics
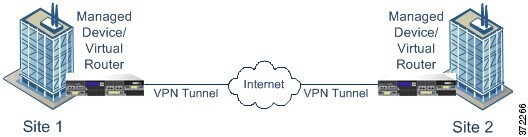
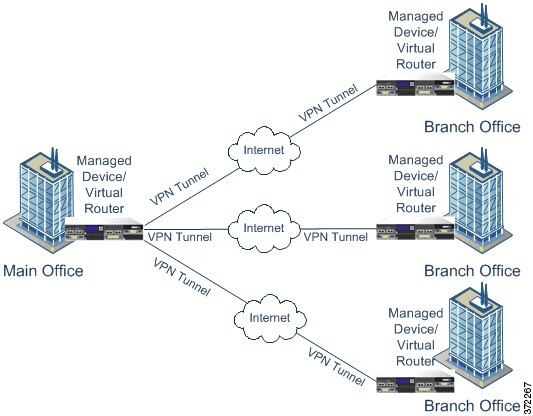
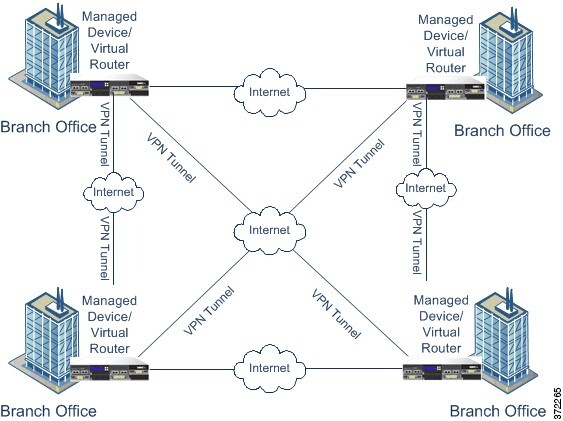
A virtual private network (VPN) is a network connection that establishes a secure tunnel between endpoints via a public source, such as the internet or other network. You can configure the Firepower System to build secure VPN tunnels between the virtual routers of Firepower managed devices. The system builds tunnels using the Internet Protocol Security (IPsec) protocol suite.
After the VPN connection is established, the hosts behind the local gateway can connect to the hosts behind the remote gateway through the secure VPN tunnel. A connection consists of the IP addresses and host names of the two gateways, the subnets behind them, and the shared secrets for the two gateways to authenticate to each other.
The VPN endpoints authenticate to each other with either the Internet Key Exchange (IKE) version 1 or version 2 protocol to create a security association for the tunnel. The system uses either the IPsec authentication header (AH) protocol or the IPsec encapsulating security payload (ESP) protocol to authenticate the data entering the tunnel. The ESP protocol encrypts the data as well as providing the same functionality as AH.
If you have access control policies in your deployment, the system does not send VPN traffic until it has passed through access control. In addition, the system does not send tunnel traffic to the public source when the tunnel is down.
To configure and deploy VPN for Firepower, you must have a VPN license enabled on each of your target managed devices. Additionally, VPN features are only available on 7000 and 8000 Series devices.
IPsec
The IPsec protocol suite defines how IP packets across a VPN tunnel are hashed, encrypted, and encapsulated in the ESP or AH security protocol. The Firepower System uses the hash algorithm and encryption key of the Security Association (SA), which becomes established between the two gateways by the Internet Key Exchange (IKE) protocol.
Security associations (SA) establish shared security attributes between two devices and allow VPN endpoints to support secure communication. An SA allows two VPN endpoints to handle the parameters for how the VPN tunnel is secured between them.
The system uses the Internet Security Association and Key Management Protocol (ISAKMP) during the initial phase of negotiating the IPsec connection to establish the VPN between endpoints and the authenticated key exchange. The IKE protocol resides within ISAKMP.
The AH security protocol provides protection for packet headers and data, but it cannot encrypt them. ESP provides encryption and protection for packets, but it cannot secure the outermost IP header. In many cases, this protection is not required, and most VPN deployments use ESP more frequently than AH because of its encryption capabilities. Since VPN only operates in tunnel mode, the system encrypts and authenticates the entire packet from Layer 3 and up in the ESP protocol. ESP in tunnel mode encrypts the data as well as providing the latter’s encryption capabilities.
IKE
The Firepower System uses the IKE protocol to mutually authenticate the two gateways against each other as well as to negotiate the SA for the tunnel. The process consists of two phases.
IKE phase 1 establishes a secure authenticated communication channel by using the Diffie-Hellman key exchange to generate a pre-shared key to encrypt further IKE communications. This negotiation results in a bidirectional ISAKMP security association. The system allows you to perform the authentication using a pre-shared key. Phase 1 operates in main mode, which seeks to protect all data during the negotiation, while also protecting the identity of the peers.
During IKE phase 2, the IKE peers use the secure channel established in phase 1 to negotiate security associations on behalf of IPsec. The negotiation results in a minimum of two unidirectional security associations, one inbound and one outbound.


 )
) Feedback
Feedback