Introduction to Objects
For increased flexibility and web interface ease-of-use, the system uses named objects, which are reusable configurations that associate a name with a value. When you want to use that value, use the named object instead. The system supports object use in various places in the web interface, including many policies and rules, event searches, reports, dashboards, and so on. The system provides many predefined objects that represent frequently used configurations.
Use the object manager to create and manage objects. Many configurations that use objects also allow you to create objects on the fly, as needed. You can also use the object manager to:
-
View the policies, settings, and other objects where a network, port, VLAN, or URL object is used; see Viewing Objects and Their Usage.
-
Group objects to reference multiple objects with a single configuration; see Object Groups.
-
Override object values for selected devices; see Object Overrides.
After you edit an object used in an active policy, you must redeploy the changed configuration for your changes to take effect. You cannot delete an object that is in use by an active policy.
 Note |
An object is configured on a managed device if, and only if, the object is used in a policy that is assigned to that device. If you remove an object from all policies assigned to a given device, the object is also removed from the device configuration on the next deployment, and subsequent changes to the object are not reflected in the device configuration. |
Object Types
The following table lists the objects you can create in the system, and indicates whether each object type can be grouped or configured to allow overrides.
|
Object Type |
Groupable? |
Allows Overrides? |
|---|---|---|
|
Network |
yes |
yes |
|
Port |
yes |
yes |
|
Interface:
|
no |
no |
|
Tunnel Zone |
no |
no |
|
Application Filter |
no |
no |
|
VLAN Tag |
yes |
yes |
|
External Attribute: Security Group Tag (SGT) and Dynamic Object |
no |
no |
|
URL |
yes |
yes |
|
Geolocation |
no |
no |
|
Time Range |
no |
no |
|
Variable Set |
no |
no |
|
Security Intelligence: Network, DNS, and URL lists and feeds |
no |
no |
|
Sinkhole |
no |
no |
|
File List |
no |
no |
|
Cipher Suite List |
no |
no |
|
Distinguished Name |
yes |
no |
|
Public Key Infrastructure (PKI):
|
yes |
no |
| Key Chain | no | yes |
|
DNS Server Group |
no |
no |
|
SLA Monitor |
no |
no |
|
Prefix List: IPv4 and IPv6 |
no |
yes |
|
Route Map |
no |
yes |
|
Access List: Standard and Extended |
no |
yes |
|
AS Path |
no |
yes |
|
Community List |
no |
yes |
|
Policy List |
no |
yes |
|
FlexConfig: Text and FlexConfig objects |
no |
yes |
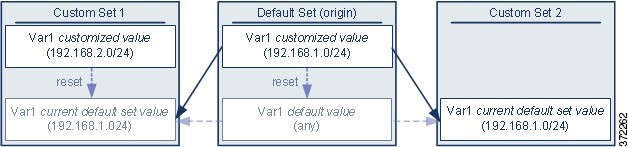
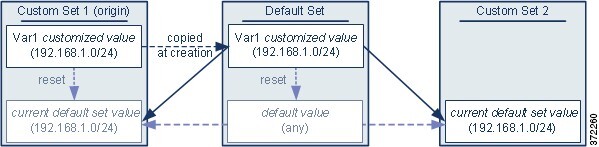
Objects and Multitenancy
In a multidomain deployment, you can create objects in Global and descendant domains with the exception of Security Group Tag (SGT) objects, which you can create only in the Global domain. The system displays objects created in the current domain, which you can edit. It also displays objects created in ancestor domains, which you cannot edit, with the exception of security zones and interface groups.
 Note |
Because security zones and interface groups are tied to device interfaces, which you configure at the leaf level, administrators in descendant domains can view and edit and groups created in ancestor domains. Subdomain users can add and delete interfaces from ancestor zones and groups, but cannot delete or rename the zones/groups. |
Object names must be unique within the domain hierarchy. The system may identify a conflict with the name of an object you cannot view in your current domain.
For objects that support grouping, you can group objects in the current domain with objects inherited from ancestor domains.
Object overrides allow you to define device-specific or domain-specific values for certain types of object, including network, port, VLAN tag, and URL. In a multidomain deployment, you can define a default value for an object in an ancestor domain, but allow administrators in descendant domains to add override values for that object.
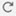









 ) button provided against the
) button provided against the  . By default, the weak-crypto option is disabled.
. By default, the weak-crypto option is disabled.

 Feedback
Feedback