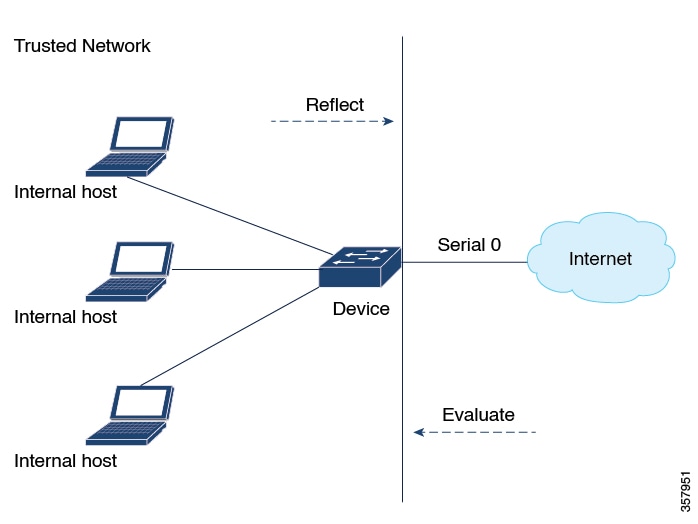
This example shows configuration of reflexive access lists for an external interface.
This configuration example permits both inbound and outbound TCP traffic at interface GigabitEthernet 1, but only if the
first packet in a given session originated from inside your network. Interface GigabitEthernet 1 connects to the internet.
This command defines the interface where session-filtering configuration is to be applied:
interface GigabitEthernet 1
description Access to the Internet via this interface
This command applies access lists to an interface, for inbound traffic and outbound traffic.
ip access-group inboundfilters in
ip access-group outboundfilters out
This command defines an outbound access list. This is the access list that evaluates all outbound traffic on interface GigabitEthernet
1.
ip access-list extended outboundfilters
This command defines a reflexive access list called tcptraffic. This entry permits all outbound TCP traffic and creates a
new access list named tcptraffic. Also, when an outbound TCP packet is the first in a new session, a corresponding temporary
entry is automatically created in the reflexive access list tcptraffic.
permit tcp any any reflect tcptraffic
This command defines an inbound access list. This is the access list that evaluates all inbound traffic on interface GigabitEthernet
1.
ip access-list extended inboundfilters
This command defines inbound access list entries. This example shows that EIGRP is permitted on the interface. Also, no ICMP
traffic is permitted. The last entry points to the reflexive access list. If a packet doesn’t match the first two entries,
the packet is evaluated against all the entries in the reflexive access list called tcptraffic.
permit eigrp any any
deny icmp any any
evaluate tcptraffic
This command defines the global idle timeout value for all reflexive access lists. In this example, when the reflexive access
list tcptraffic was defined, no timeout was specified, so tcptraffic uses the global timeout. Therefore, if for 120 seconds
there’s no TCP traffic that is part of an established session, the corresponding reflexive access list entry will be removed.
ip reflexive-list timeout 120
The example configuration looks as follows:
interface GigabitEthernet 1
description Access to the Internet via this interface
ip access-group inboundfilters in
ip access-group outboundfilters out
!
ip reflexive-list timeout 120
!
ip access-list extended outboundfilters
permit tcp any any reflect tcptraffic
!
ip access-list extended inboundfilters
permit eigrp any any
deny icmp any any
evaluate tcptraffic
In this configuration, before any TCP sessions are initiated, the show
access-list command displays the following:
Extended IP access list inboundfilters
permit eigrp any any
deny icmp any any
evaluate tcptraffic
Extended IP access list outboundfilters
permit tcp any any reflect tcptraffic
The reflexive access list doesn’t appear in this output. This is because before any TCP sessions are initiated, no traffic
has triggered the reflexive access list, and the list is empty, that is, it has no entries. When empty, reflexive access lists
do not show up in the show
access-list output.
After a Telnet connection is initiated from within your network to a destination outside of your network, the show
access-list command displays the following:
Extended IP access list inboundfilters
permit eigrp any any
deny icmp any any
evaluate tcptraffic
Extended IP access list outboundfilters
permit tcp any any reflect tcptraffic
Reflexive IP access list tcptraffic
permit tcp host 172.19.99.67 eq telnet host 192.168.60.185 eq 11005 (5 matches) (time
left 115 seconds)
The reflexive access list tcptraffic now appears, and displays the temporary entry generated when the Telnet session is initiated
with an outbound packet.

 Feedback
Feedback