Restrictions for IPsec
General Restrictions for IPsec
-
Crypto maps are not supported.
-
Only tunnel mode is supported.
-
Volume-based rekeying is not supported.
-
IPsec tunnels are not supported on an MPLS cloud.
-
IPsec tunnels are not supported on vrf lite.
-
A maximum of 128 source IPv4 addresses can be used as a tunnel source IP address (loopback address).
-
A maximum of 128 source IPv6 addresses can be used as a tunnel source IP address (loopback address).
-
The maximum number of IPsec IPv4 Static Virtual Tunnel Interfaces (SVTIs) supported is 480. The maximum number of IPsec IPv6 SVTIs supported is 240. This is a unidimensional scale number. If you enable other features which share the same resource, the scale number will be reduced.
-
IPv4 tunnel mode and IPv6-overlay-IPv4 do not allow IPv6 addresses.
-
IPv6 tunnel mode and IPv4-overlay-IPv6 do not allow IPv4 addresses.
-
OSPFv3 authentication is not supported with IPsec.
-
Only Internet Key Exchange Version 2 (IKEv2) is supported in IPsec.
-
IPsec supports only the following transform-sets:
esp-aes esp-sha-hmac (with throughput up to 15 Gbps)
esp-gcm, esp-gcm 256 (with throughput up to 100 Gbps)
 Note |
The PHY layer adds an additional 34-38 bytes to the IPsec overhead of egressing packets. This may cause the egressing packets to exceed the MTU configured on the underlay interface, and they will be dropped. You can resolve this by increasing the MTU value of the underlay interface by 38 bytes. |
Restrictions for IPsec Virtual Tunnel Interfaces
-
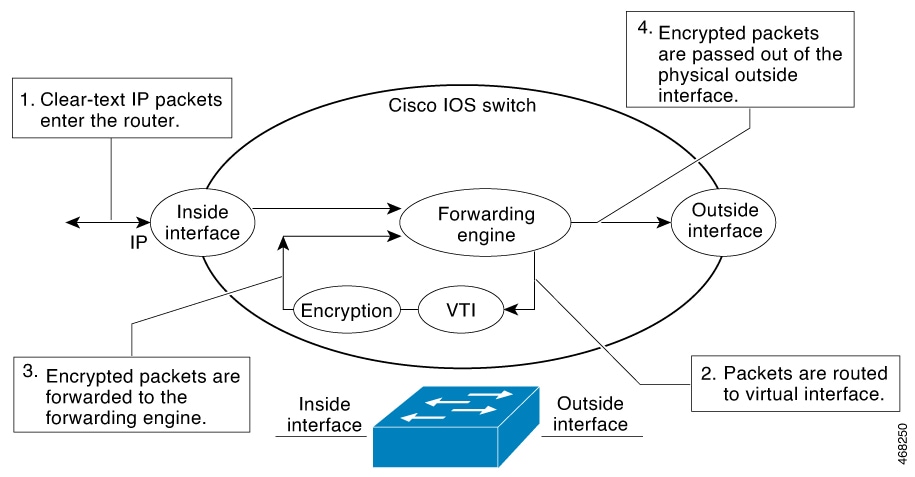
Fragmentation of encrypted packets and reassembling of encrypted fragments is not supported. SVTI's MTU needs to be set smaller than physical interface. Fragmentation can be done before encryption or after decryption.
-
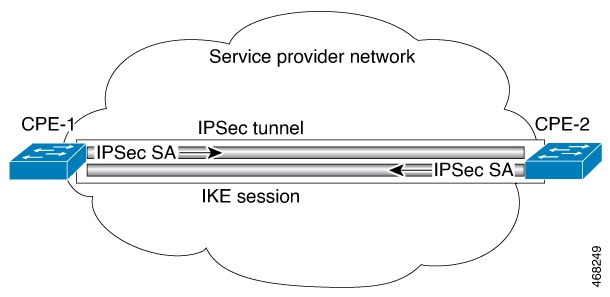
The Internet Key Exchange (IKE) security association (SA) is bound to the VTI.
-
By default, Static VTIs (SVTIs) support only a single IPSec SA that is attached to the virtual tunnel interface. The traffic selector for the IPsec SA is always “IP any any” or "IPv6 any any".
-
VTIs do not support traffic selector narrowing down.
-
SVTIs support only the “IP any any” proxy.
-
IPsec stateful failover is not supported with IPSec VTIs.
-
Do not configure the shared keyword when using the tunnel mode ipsec ipv4 command for IPsec IPv4 mode.
-
The traceroute function with crypto offload on VTIs is not supported.
-
Mixed mode is not supported with tunnel mode auto . Mixed mode is not supported with tunnel protection ipsec [shared] .
-
Tunnel source cannot be a subinterface.
Restrictions for IPsec Dead Peer Detection Periodic Message Option
Using periodic Dead Peer Detection (DPD) potentially allows the device to detect an unresponsive IKE peer with faster response time when compared to on-demand DPD. However, use of periodic DPD incurs extra overhead. When communicating to large numbers of IKE peers, with more than 10 crypto sessions, you should consider using on-demand DPD instead.




 Feedback
Feedback