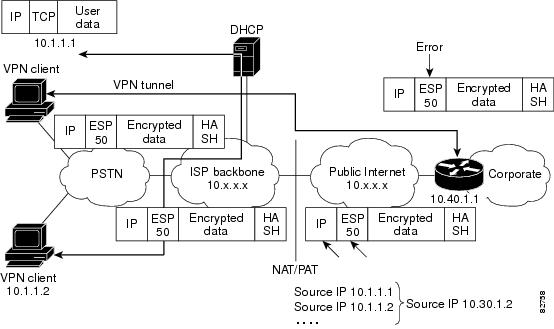
Restrictions for IPsec NAT-Traversal
-
When using a static NAT policy to change both source IP address and source port, you need to set NAT rules for both port 500 and port 4500. When NAT is detected IPsec traffic is shifted to port 4500. If there is no NAT rule for port 4500, traffic will not reach tunnel destination and IPsec NAT-Traversal will remain down.
-
Dynamic NAT policy for changing IP address is not supported for IPsec NAT-Traversal.
-
IPsec NAT-Traversal is not supported for IPv6 traffic.
-
IPsec NAT-Traversal does not work when an IP address is translated to the IP address of an existing subnet in the topology.
-
IPSEC and NAT are not supported on the same device.
-
When making changes to the IPsec NAT-Traversal keepalive timer, you first need to remove the tunnel mode and tunnel protection configurations from the SVTI. Then, you need to reconfigure the tunnel mode and tunnel protection along with the changes to the IPsec NAT-Traversal keepalive timer.
-
Traffic through an IPsec tunnel will not work when IPsec NAT-Traversal sessions and other IPsec sessions have the same tunnel destination.
-
IPsec NAT-Traversal will not work when MACsec is enabled on the underlay interfaces.
-
All the limitations that apply to IPsec also apply to IPsec NAT-Traversal.



 Feedback
Feedback