9
Cybersecurity in ASEAN: An Urgent Call to Action
Quantifying the value-at-risk from cybercrime is challenging, and organizations around the
world lack competencies in this area. One of the biggest challenges is understanding the nature
of the threat to high-value assets and appropriately prioritizing and focusing mitigating
resources. No organization can afford to use every defense mechanism in its arsenal, nor is it
practical. However, resources must be allocated according to the magnitude of the threat and
the value-at-risk.
Based on a sector-wide perspective, most ASEAN countries are at risk of cyberattacks because
of the significant contribution of information and communications technology (ICT) in the
sectors that are most at risk. The IBM X-Force Threat Intelligence Index has cited the following as
the most cyberattacked sectors in recent years: healthcare, manufacturing, financial services,
government, transportation, and retail.
13
Across the ASEAN-6, these sectors account for the
majority of GDP contribution (on average of 70 percent). In the case of Singapore, the share of
these sectors is even higher at 94 percent of GDP.
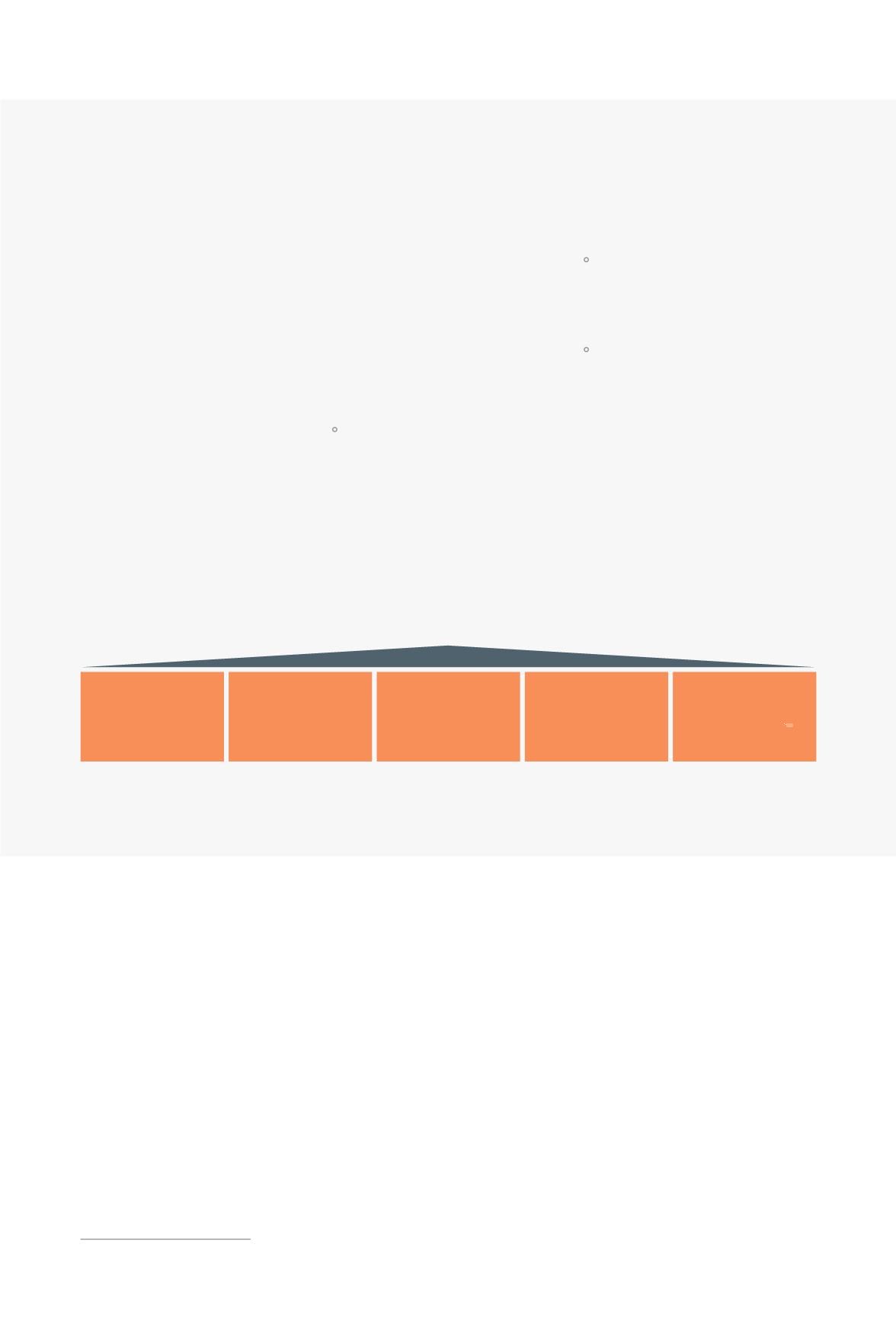
The EUApproach toCybersecurity
TheEuropeanUnion (EU)
developeda region-widecyberse-
curitystrategy in2013 to“enhance
theEU’soverall performance”
and to“safeguardanonline
environment providing thehighest
possible freedomandsecurity for
thebenefit of everyone.”Thiswas
augmentedby theCybersecurity
Packageannounced in2017. The
figurebelowhighlights thepillars
of EU’scybersecuritystrategy
(see figure).
Facing similar complexities as
ASEAN, such as fragmented
regulation, the EU also saw the
need for a unifying framework,
giving rise to the Directive on
Security of Network and
Information Systems (NIS
Directive) as part of its overall
cybersecurity strategy, which
entered into force inAugust 2016.
Member states were given 21
months to adopt the directive
into their national legislation.
Some crucial elements of the
directive include:
• A requirement formember
states tobe appropriately
equipped, such as having a
national CSIRT and a national
NISbody. TheCSIRTswould
forma collaborativeCSIRT
network that would cooperate
on incidents and share
risk-related information.
• Acooperationgroup involving
all member states, allowing for
strategic cooperation and
information sharing
• Securitymeasures across
critical information infra-
structure sectors and key digital
service providers, such as the
mandatory reporting of serious
incidents by organizations to
the national authorities
Sources:
Joint Communication to the European Parliament and The Council,
The European Economic and Social Committee,
the Committee of the Regions, Cybersecurity Strategy of the European Union; A.T. Kearney analysis
Achieving
cyber resilience
Drastically
reducing
cybercrime
Developing
cyber defence
policy and
capabilities
Developing
industrial and
technological
resources
Establishing
a cyberspace
policy promoting
core EU values
1 2
3
4
5
Figure
Cybersecurity Strategy of the European Union
13
“ Monitored security is superior security ,”
IBM X-Force Threat Intelligence Index 2017