14
Cybersecurity in ASEAN: An Urgent Call to Action
or overestimate their cybersecurity requirements in the absence of a strong vision for cyber risk
management. A structured approach optimizes finite resources to deliver exceptional protection
appropriate to the risk they represent if the assets are strategically prioritized and apportioned.
Otherwise, as is often the case, there is little thought given to how systems are designed or
deployed, and the entire organization must undergo costly remediation to protect select assets.
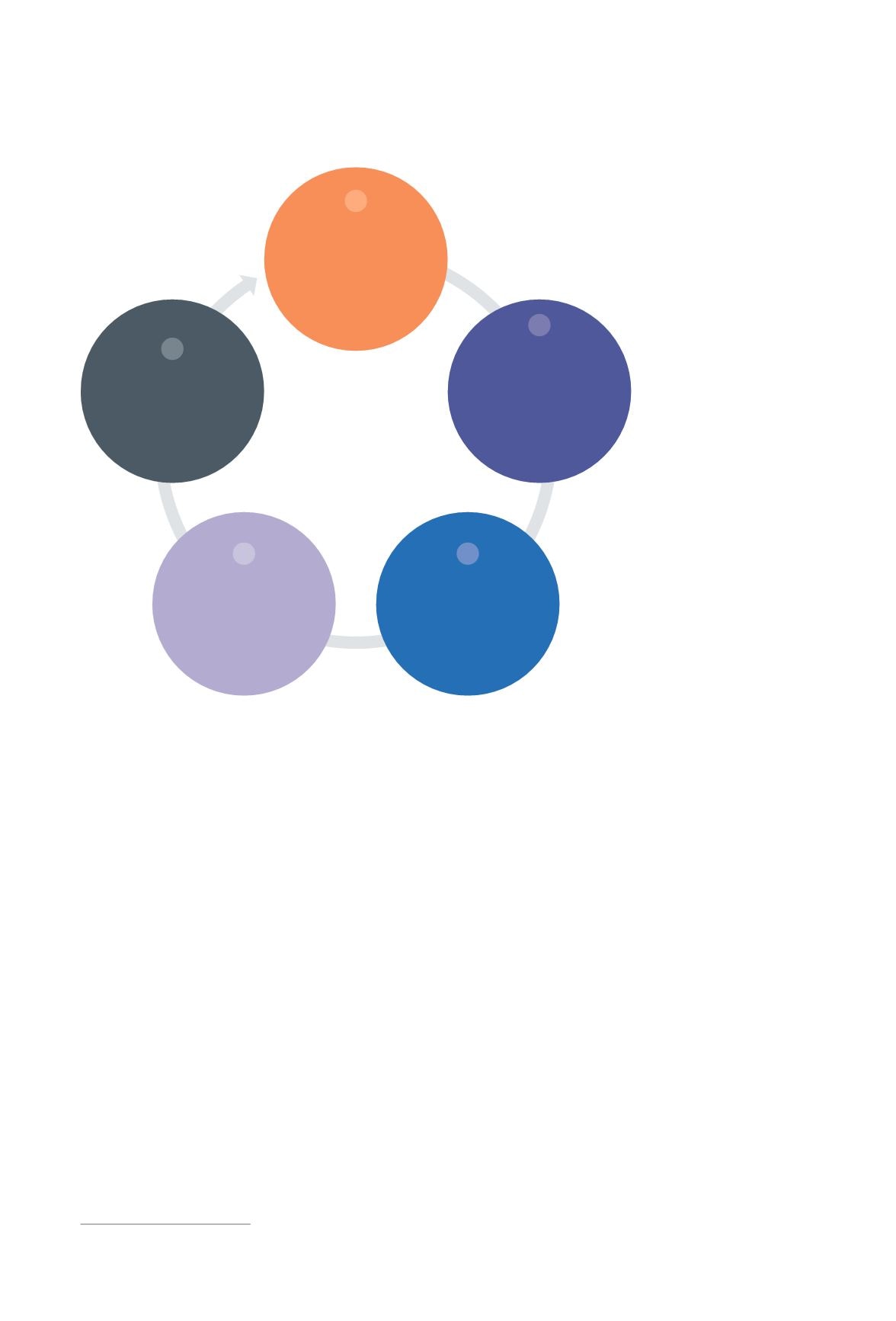
The National Institute of Standards and Technology (NIST) framework
16
recommends five
functional capabilities for achieving comprehensive, cybersecurity defense: identify, protect,
detect, respond, and recover. While businesses in the region are largely focused on the identify,
protect, and detect functions of the cybersecurity life cycle, we are seeing the need for greater
awareness and investment around recover and respond (see figure 10).
“There is a lot of movement in the recovery and respond
parts of the life cycle but still a lot of emphasis on protect.”
—global director of cybersecurity solutions, global energymanagement
and automation company
Note: NIST is National Institute of Standards and Technology.
Sources: National Institute of Standards and Technology; A.T. Kearney analysis
Figure
NIST Framework for Improving Critical Infrastructure Cybersecurity
Identify
Asset management,
business environment,
governance, risk
assessment, risk
management
1
Protect
Access control, awareness
training, data security,
information protection
processes and
procedures, protective
technology
2
Recover
Recovery planning,
improvements,
communications
5
Detect
Anomalies and events,
continuous security
monitoring, detection
processes
3
Respond
Response planning,
communications,
analysis, mitigation,
improvements
4
16
The
NIST Framework for Improving Critical Infrastructure Cybersecurityis a set of industry standards and best practices to help
organizations manage cybersecurity risks.