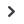
16
Cybersecurity in ASEAN: An Urgent Call to Action
region as compared to the Americas.
19
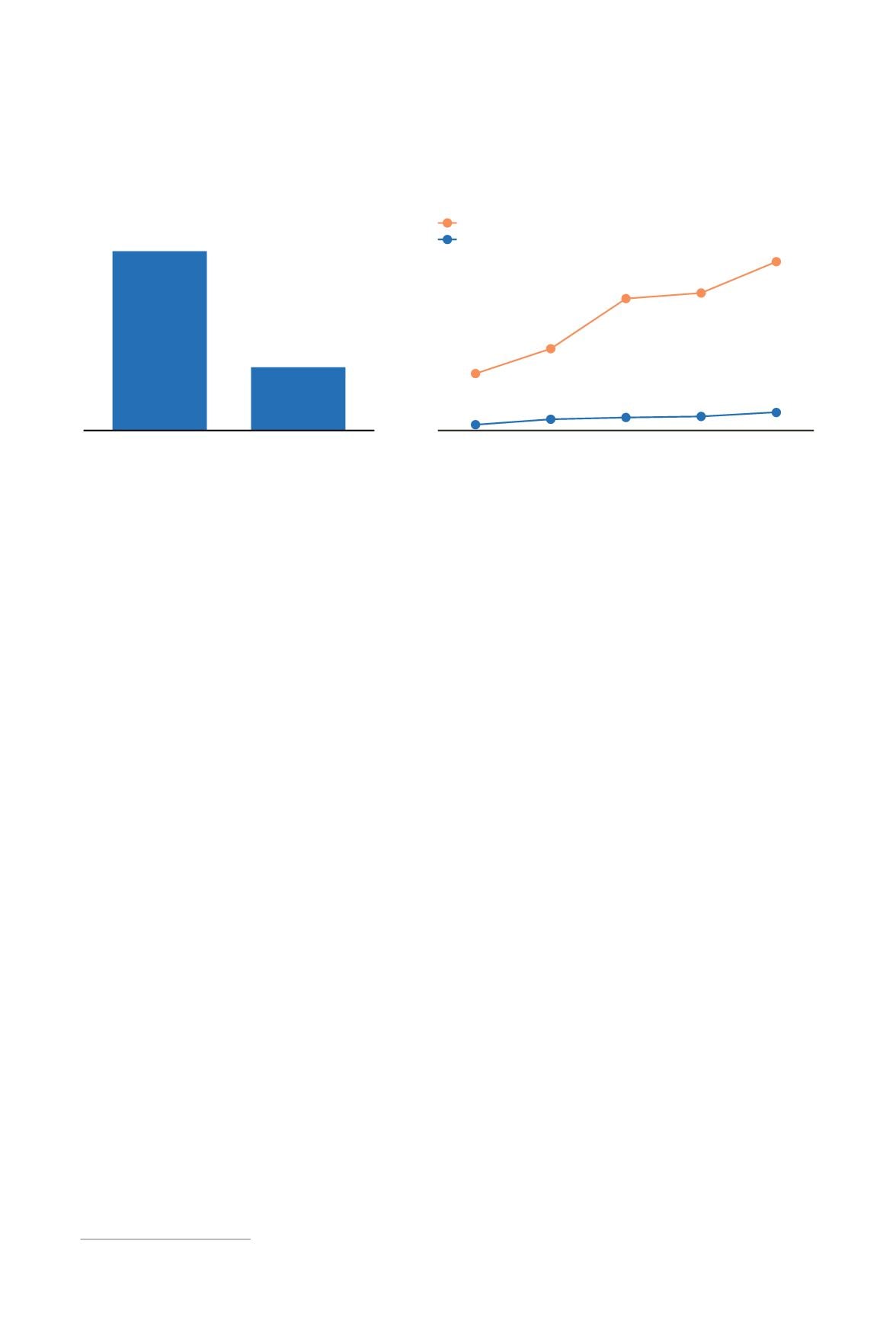
These metrics can have a significant impact on the
financial outcome of a breach as detailed in figure 12. Executives recognize this as an opportunity
to trim their security product portfolio to drive ease of management, enhance interoperability,
and improve operational effectiveness.
“You cannot be married to a single vendor. We are vendor
agnostic. We test many different platforms, most of which
are in the top percentile, then we decide. We recommend
that the vendor base should not exceed five.”
—global energymanagement and automation company
When mapping their cybersecurity portfolios, organizations can benefit from a cyber defense
matrix (see figure 13 on page 17).
Mapping asset classes against the NIST framework will help identify gaps in the portfolio and
could help trim the security and vendor portfolio by identifying duplication and focusing
attention on fewer, more comprehensive providers.
Enterprises can benefit from a platform that is simple, open, and automated—enabling better
integration between products from the same vendor and the ability to share data with other
third-party technologies. Security product integration frameworks (SPIF) facilitate the
sharing of security-related metadata, help standalone security products and services to
interoperate effectively, and ultimately improve the efficacy of enterprises’ unique security
architectures. SPIFs enable pre-integration of standalone third-party security products,
eventually enabling enterprises to construct a customized, more effective enterprise security
solution architecture.
Sources: Ponemon Institute, European Political Strategy Centre; A.T. Kearney analysis
Figure
Costs escalate the longer a cyberattack remains uncontained
Mean time
to contain
Mean time
to identify
Time to identify and contain a data
breach in ASEAN
days
Financial impact of cybersecurity breaches
detection time, thousand
More than
a week
Several
days
A day
A few
hours
Almost
instant
,
Larger businesses
Small and medium-size enterprises
19
M-Trends 2017: Trends from the Year’s Breaches and Cyber Attacks
, M-Trends Reports