15
Cybersecurity in ASEAN: An Urgent Call to Action
In addition, our interviews reveal that most small and medium-size enterprises
17
(SMEs)
generally do not see cybersecurity as a top priority. Although these firms are not usually the
main target, many cyber criminals leverage supply chain linkages or shared data to infiltrate
partnerships smaller companies have established with larger organizations. Verizon’s 2017 Data
Breach Investigations Report shows that large companies are attacked more frequently than
small companies, but small companies have a significantly higher breach-to-incident ratio: 1:1.4
for small companies compared to 1:80 for large companies. Because SMEs account for between
88 to 99 percent of the region’s establishments and between 52 to 97 percent of all jobs,
18
their
susceptibility to breaches is a major cause for concern.
1.5Multiple vendor relationships andproduct deployments result
in operational complexity
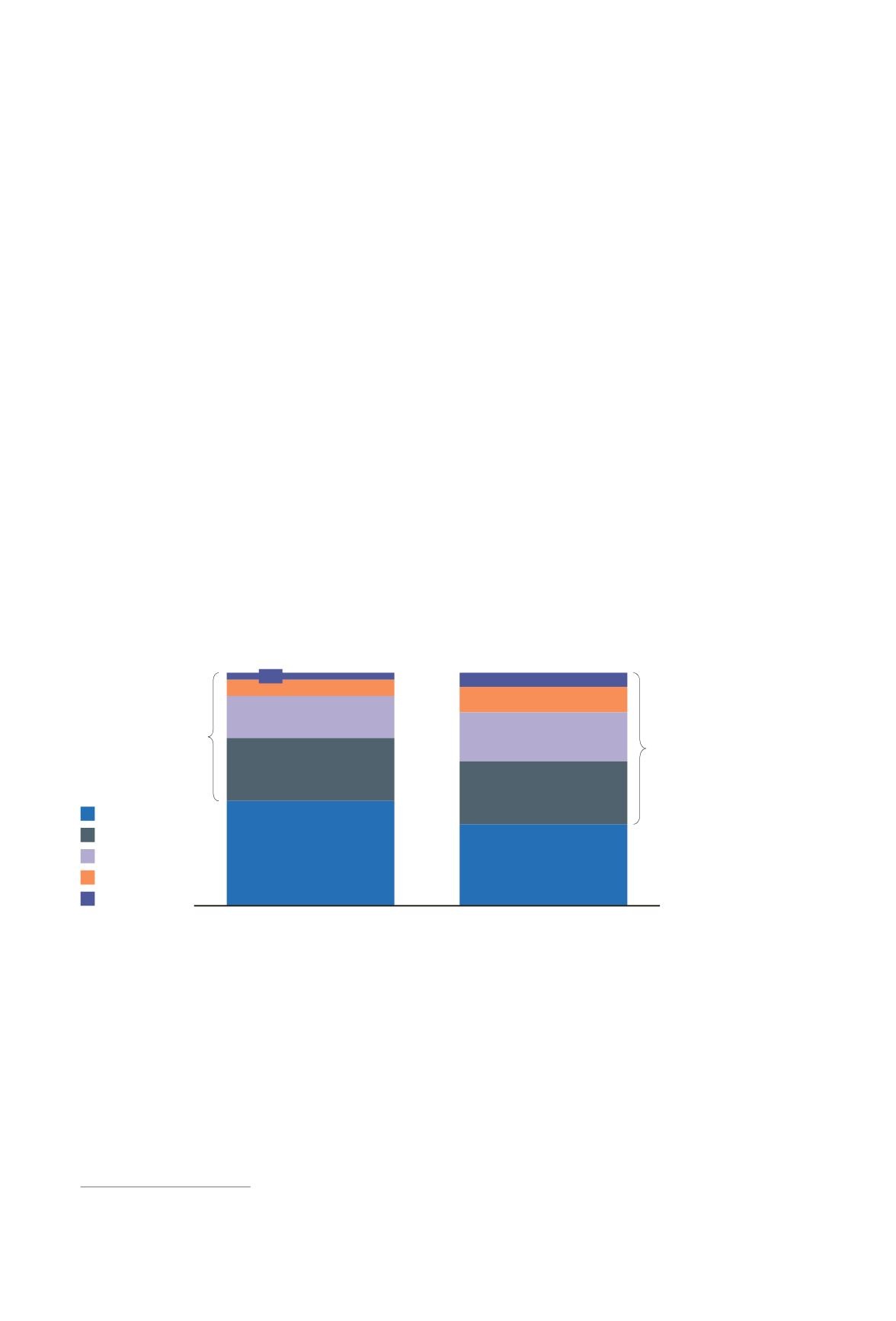
Given the breadth of the security product landscape and the level of fragmentation of vendor
solutions, best of breed has emerged as a preferred vendor selection model. Cisco’s Annual
Cybersecurity Report 2017 has highlighted the complexity of the cybersecurity landscape in
terms of end-user reliance on multiple vendors and products. More than a quarter of companies
in the sample use more than 10 vendors, and 36 percent deploy more than 10 cybersecurity
solutions (see figure 11).
Sources: Cisco
Annual Cybersecurity Report; A.T. Kearney analysis
Figure
Number of security vendors and products used by organizations
–
–
–
–
More than
Security products
Security vendors
% of
organizations
use more than ive
security vendors
% of organizations
use more than ive
security products
or solutions
%
%
%
%
%
%
%
%
%
%
A complicated vendor landscape with security products that do not work well together can
lengthen the time to identify and contain a breach, thereby increasing vulnerability.
In the ASEAN region, data published by the Ponemon Institute suggests that it takes on average
184 days to identify a data breach and close to 65 days to contain it (see figure 12 on page 16).
Cyber dwell time, defined as the number of days a threat actor remains undetected within a
given environment until remediation, is reported to be 65 percent higher in the Asia Pacific
17
Using the Malaysian definition: establishments with fewer than 200 employees in manufacturing or 75 employees in services
and other areas
18
ASEAN Economic Community, Small and Medium Enterprises Overview